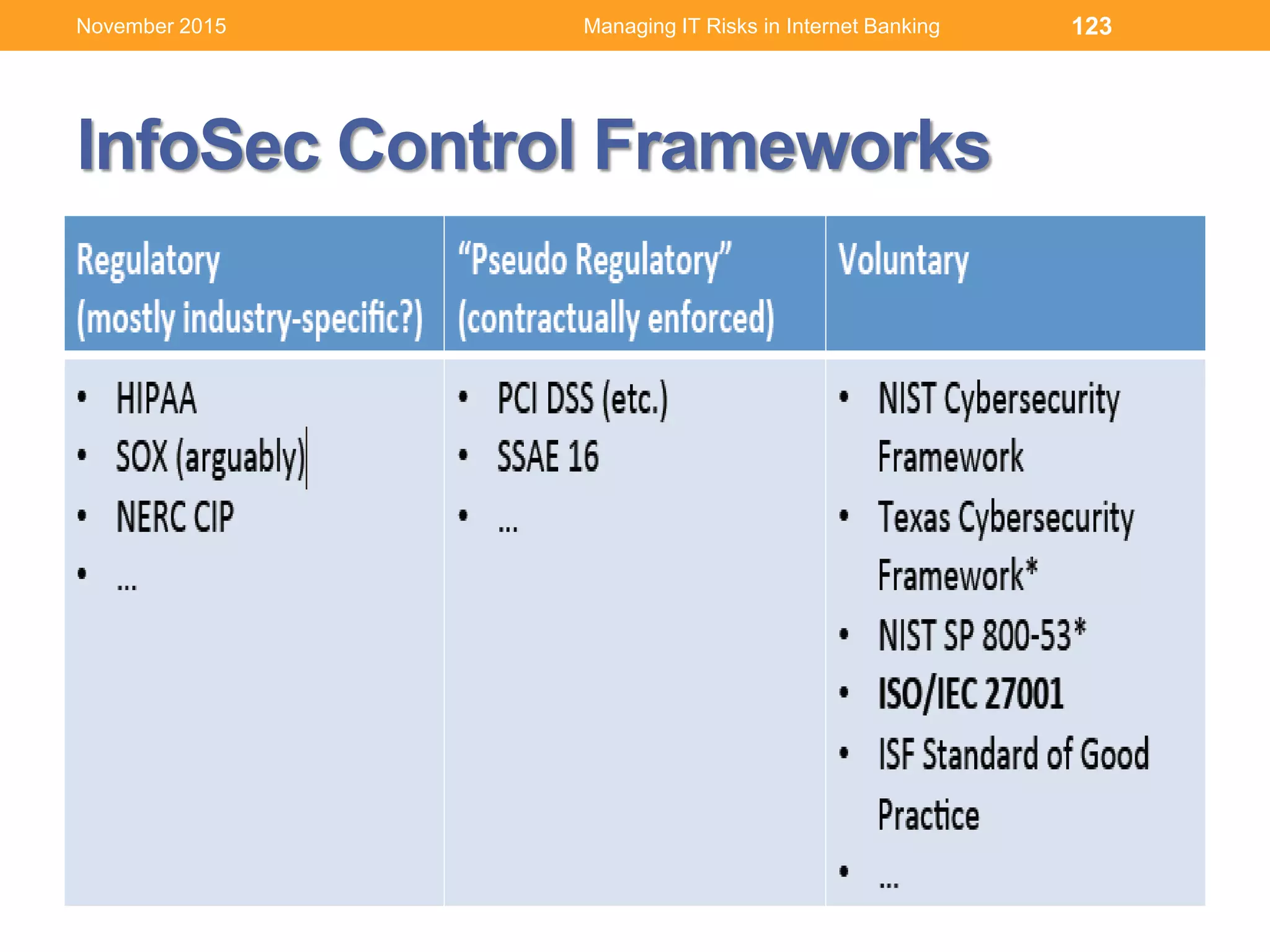
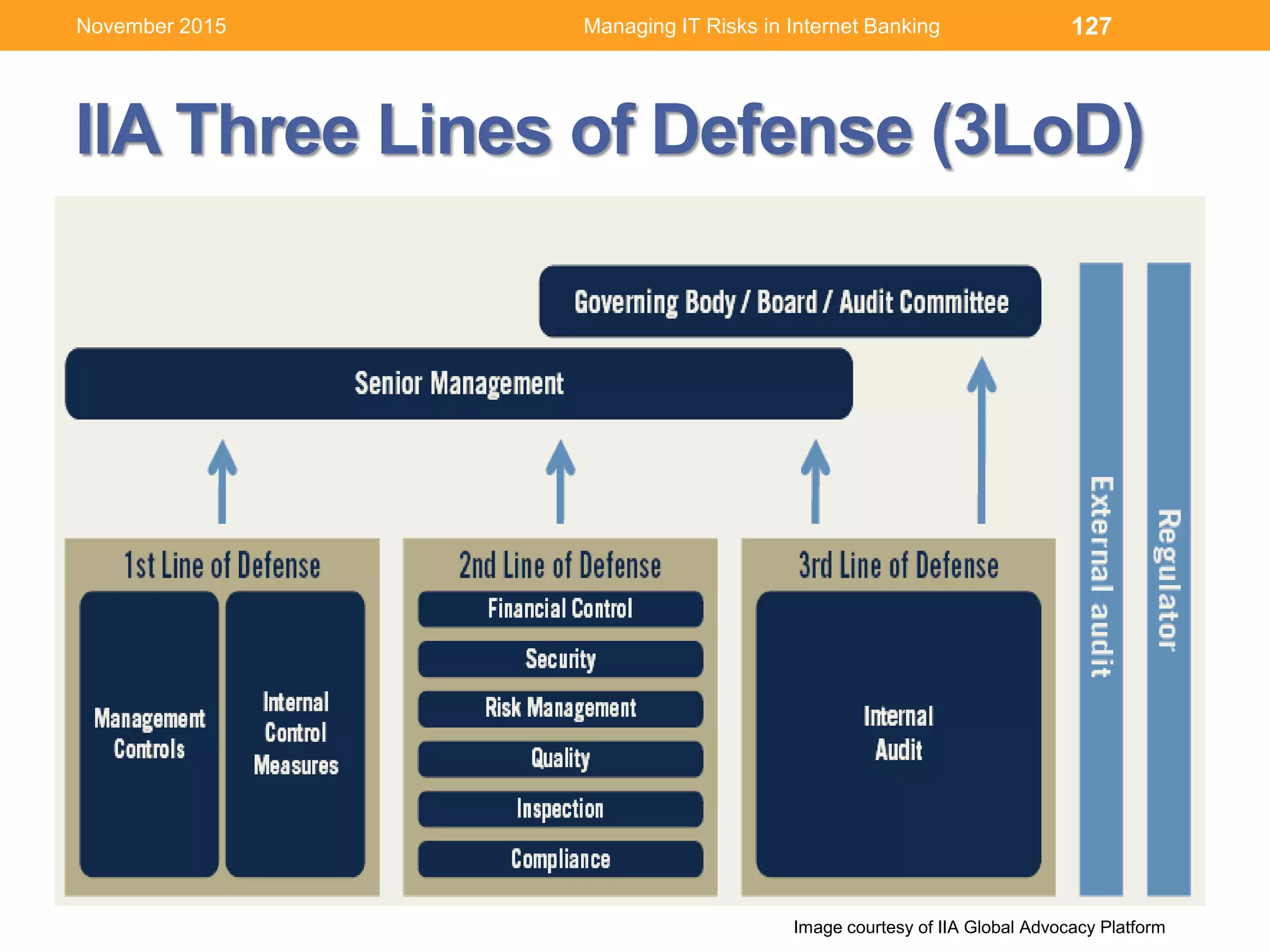
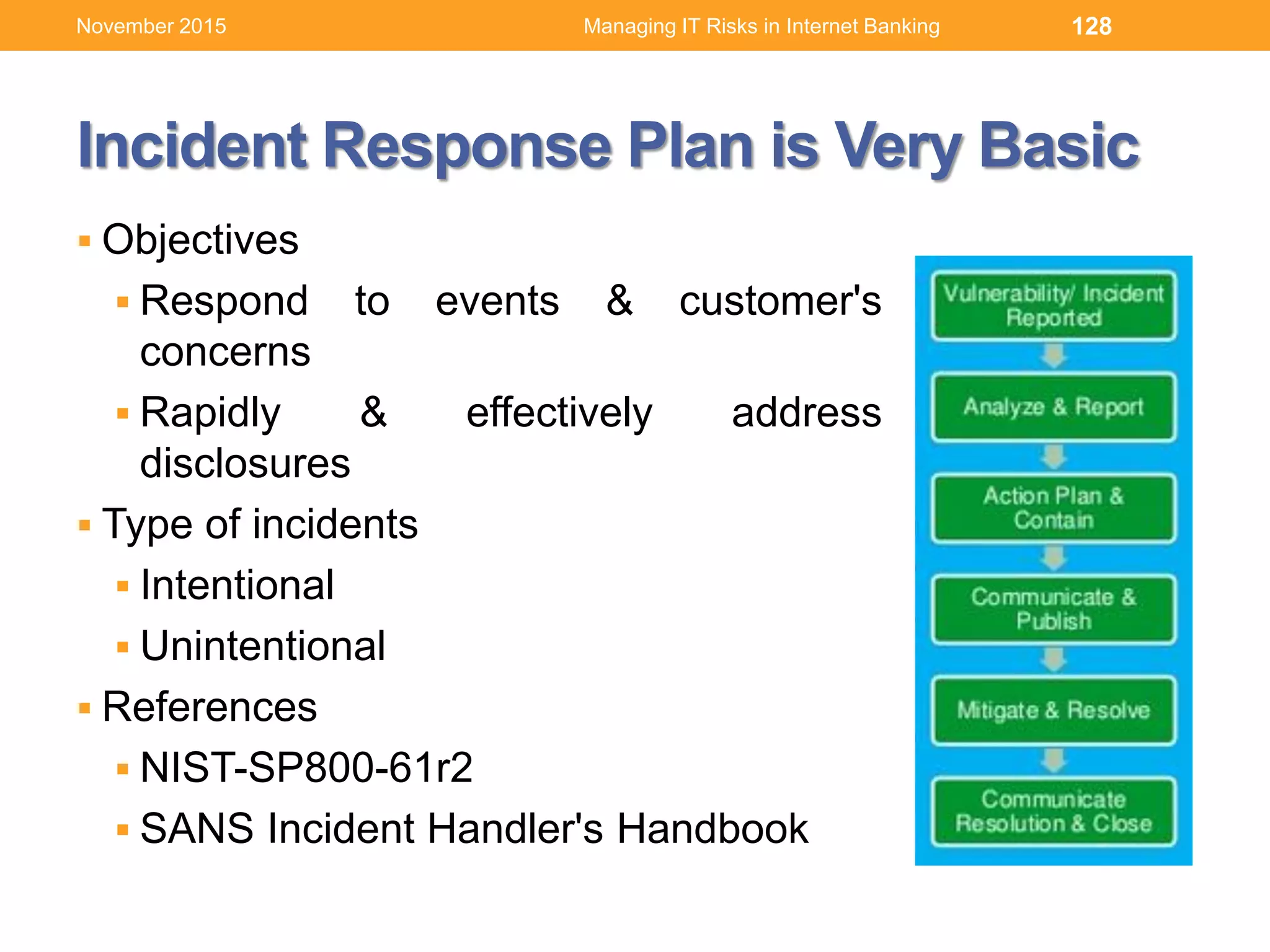
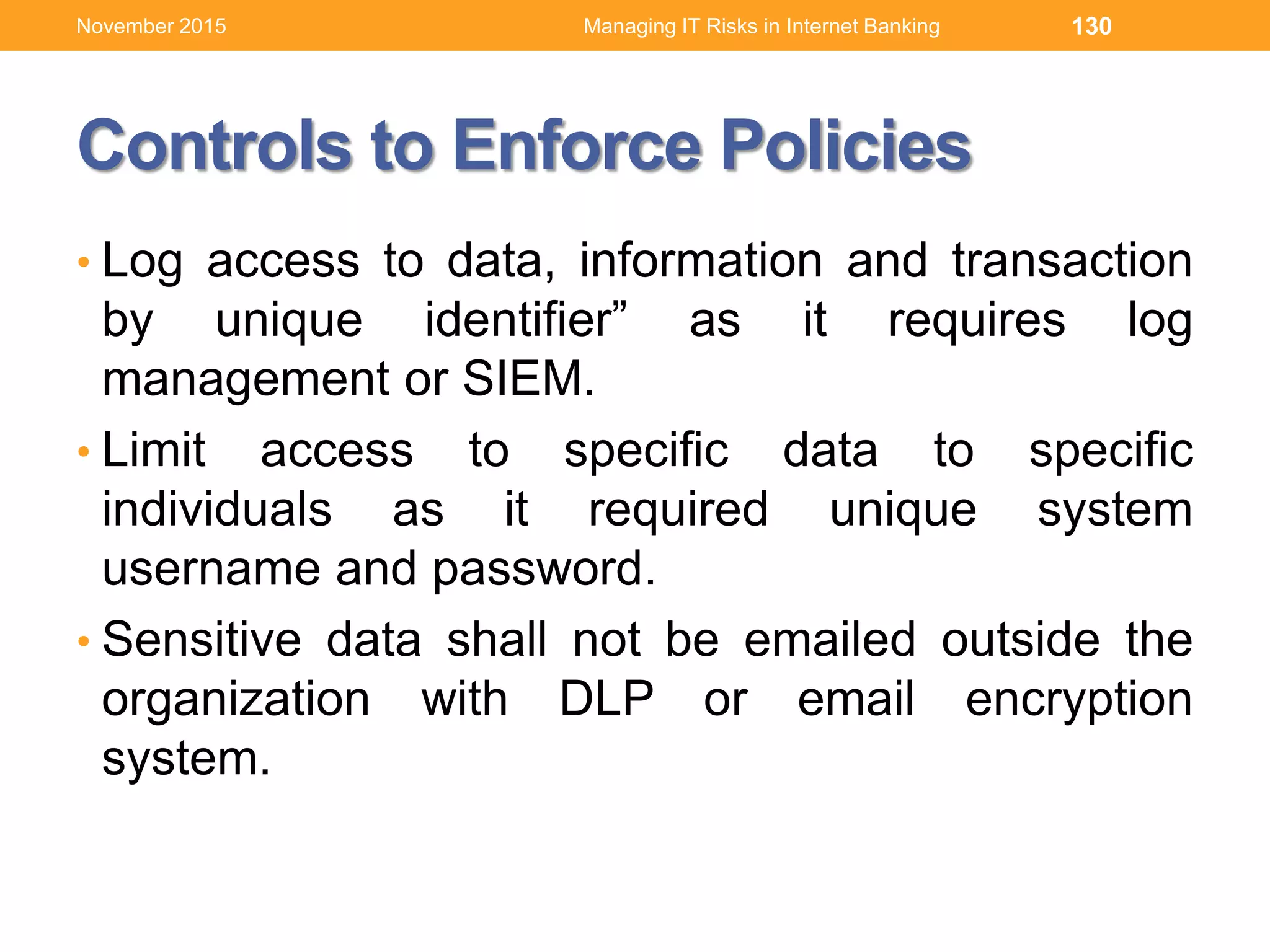
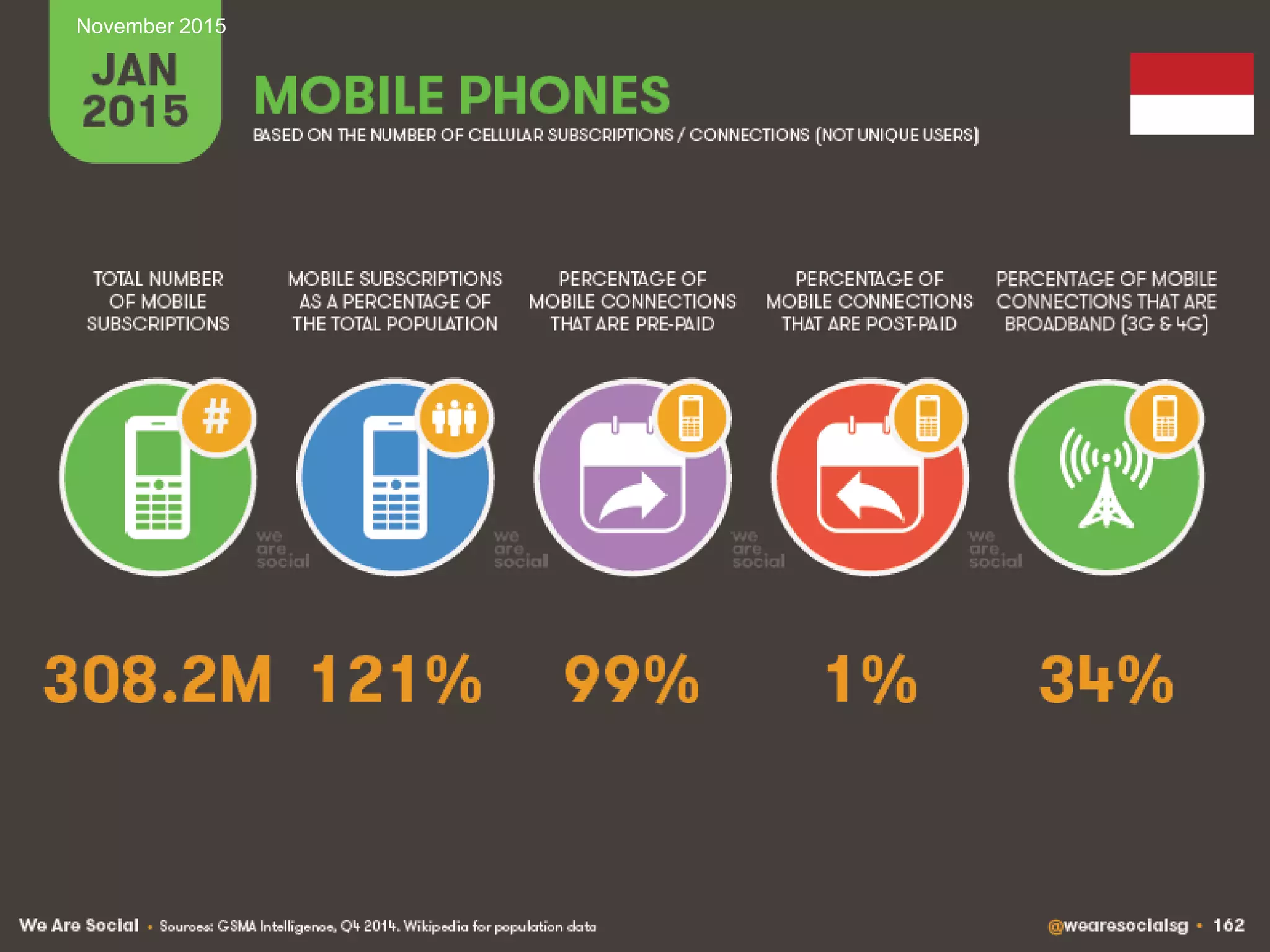
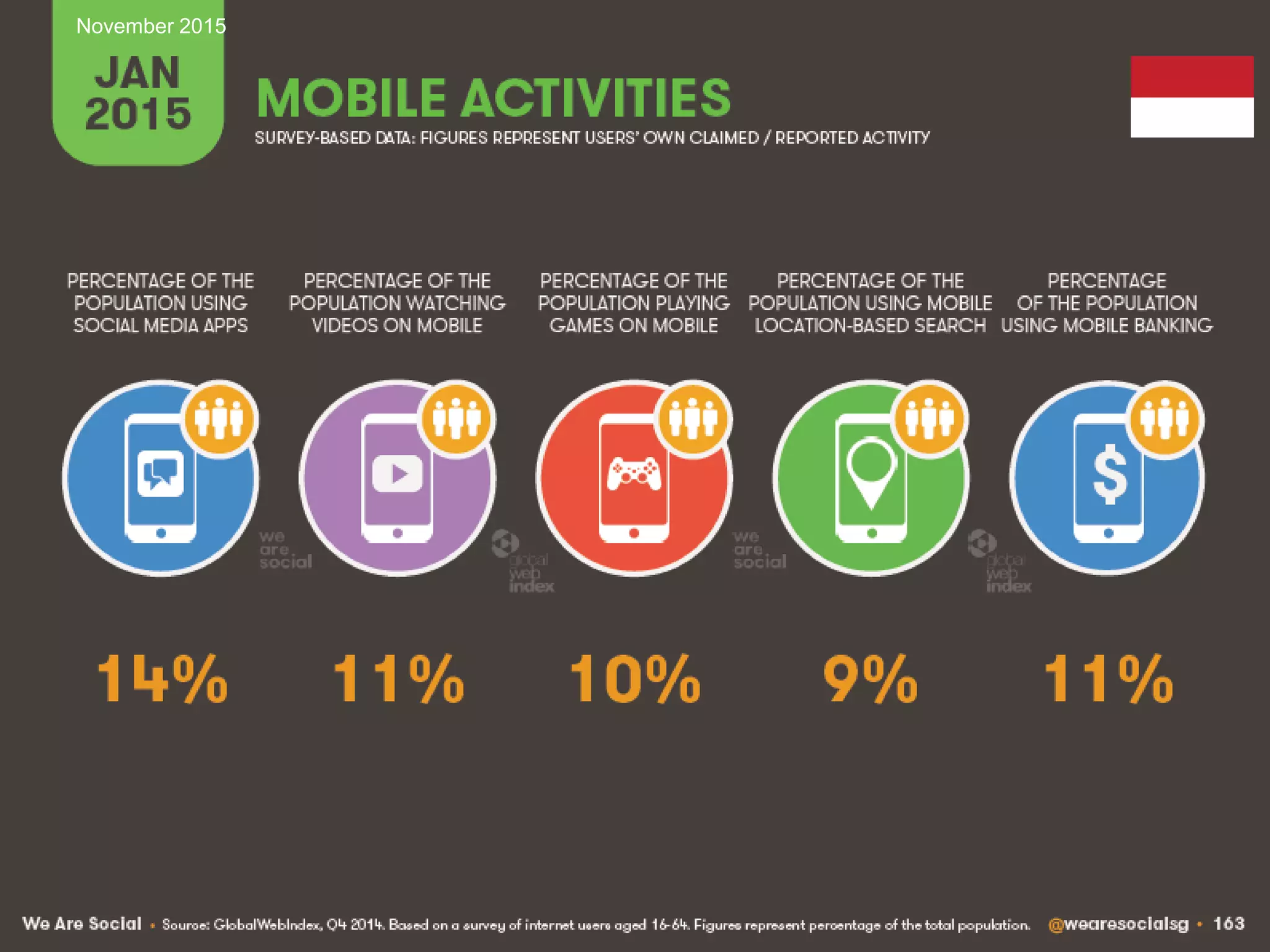
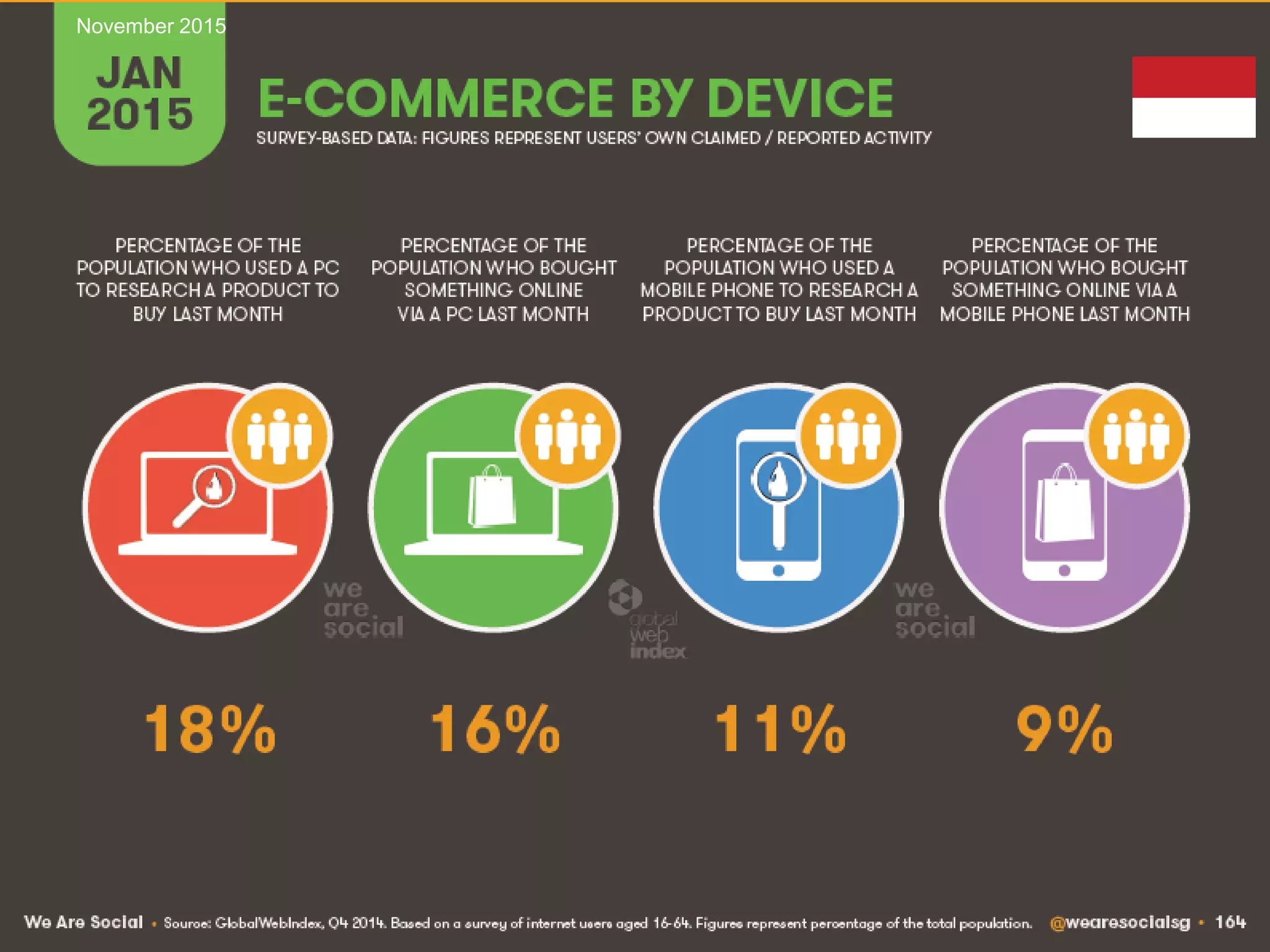
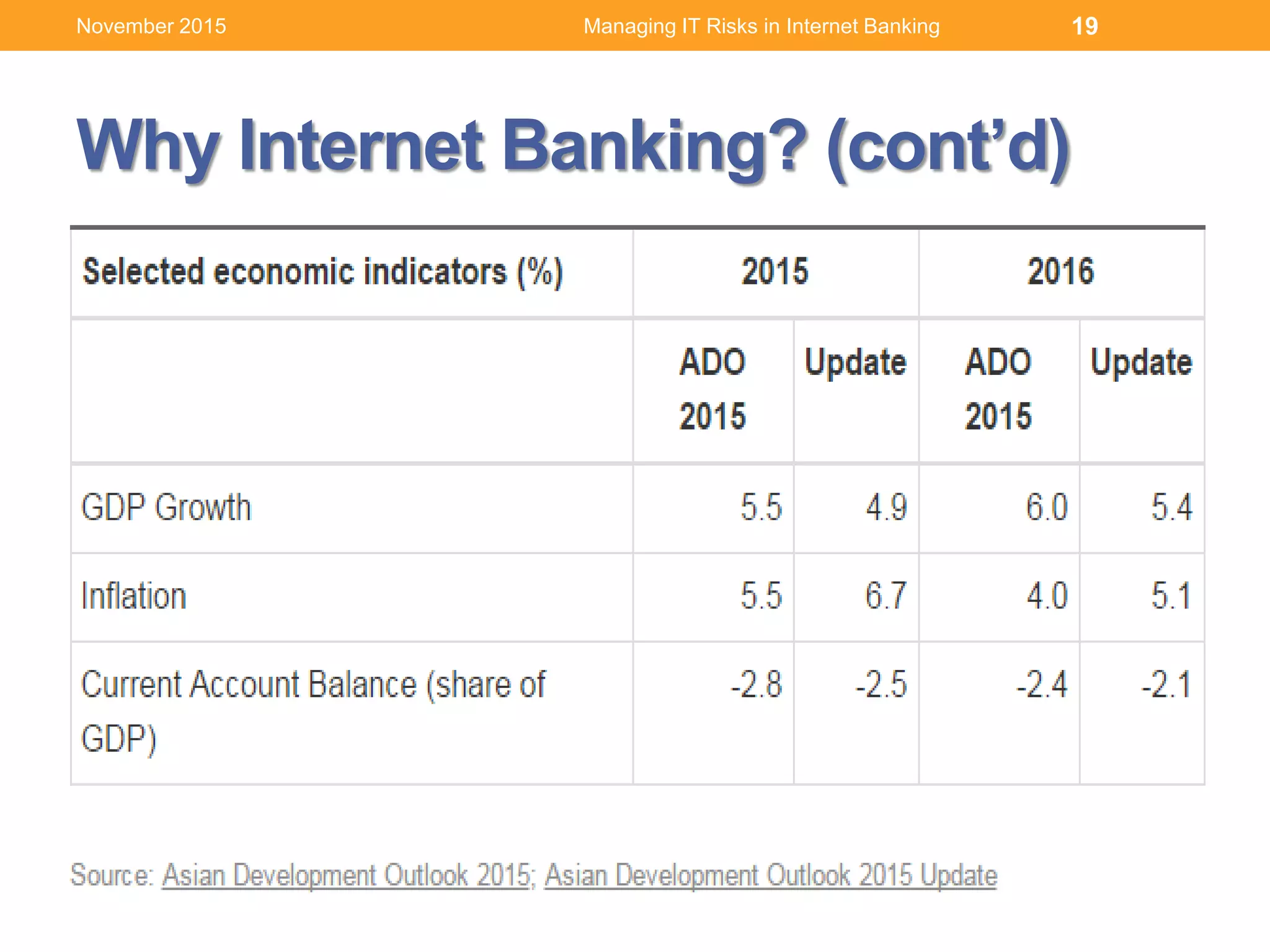
This document discusses managing IT risks in internet banking. It covers several topics:
1. Understanding user behaviors and expectations, such as their focus on speed, security and ease of use of internet banking services.
2. Acquiring and developing internet banking services, including following a system development life cycle and outsourcing management practices.
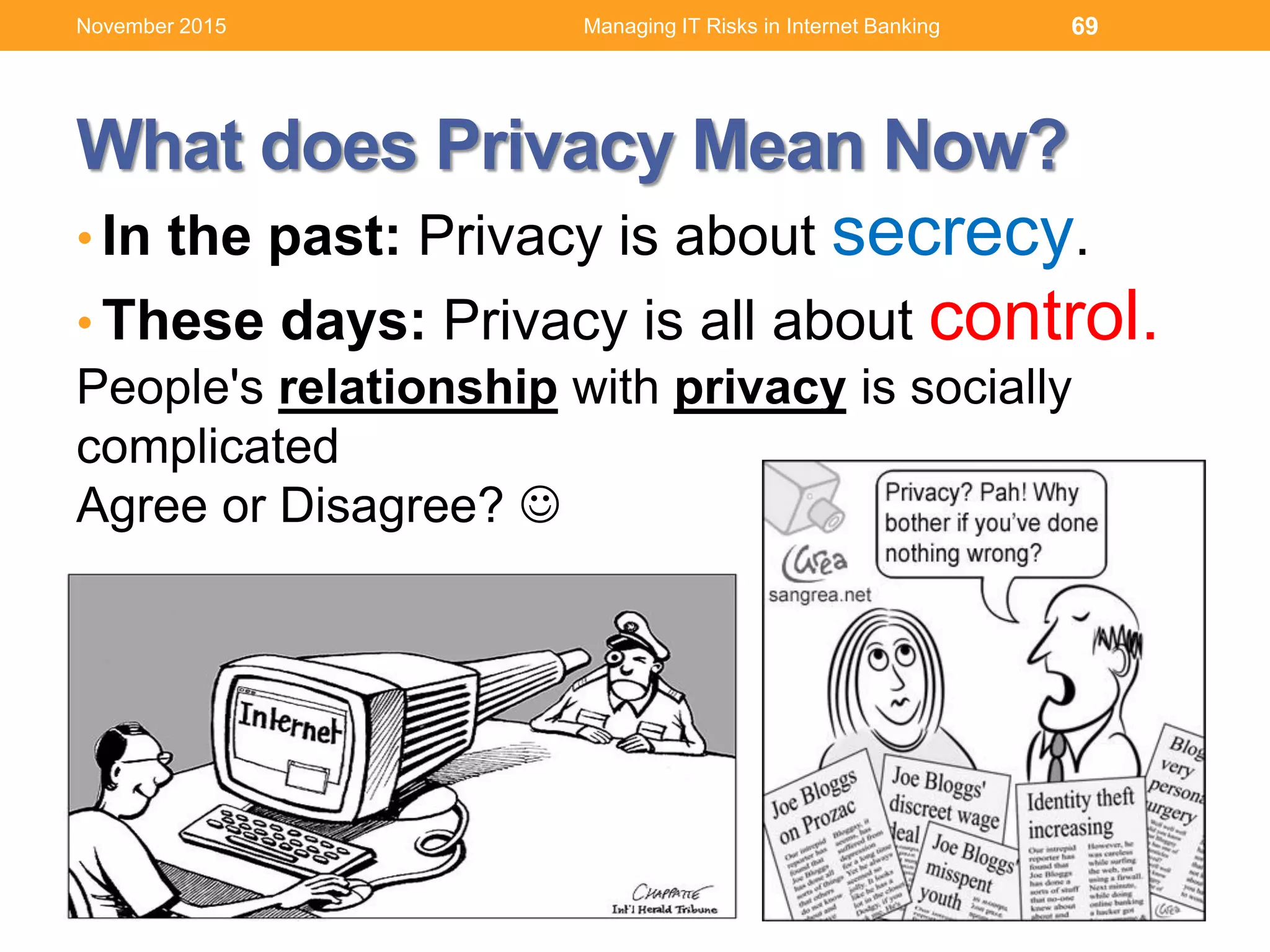
3. Comprehending information security and privacy risks like cyber attacks, and how to respond through human resources management practices around access controls, segregation of duties and training.







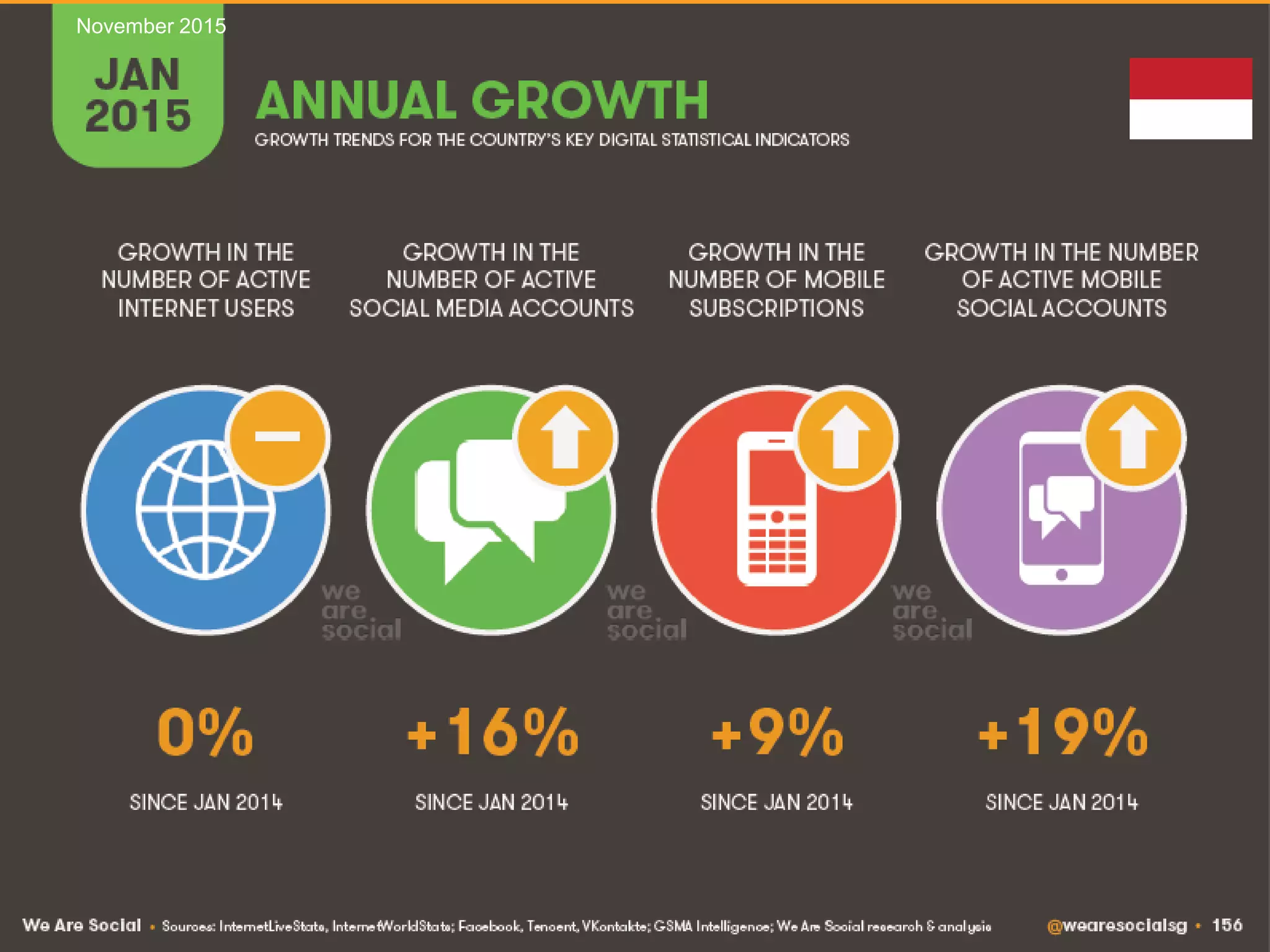
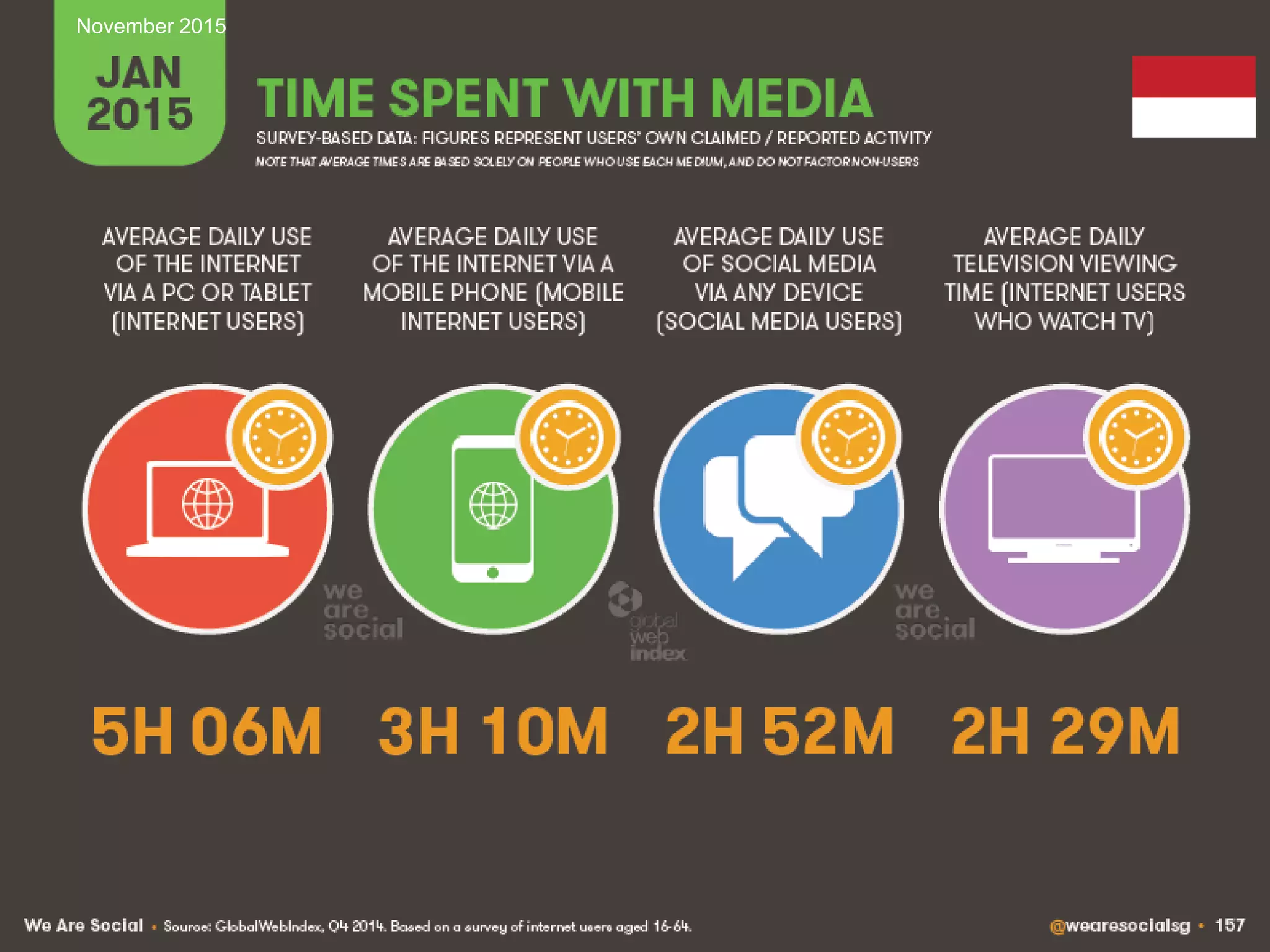
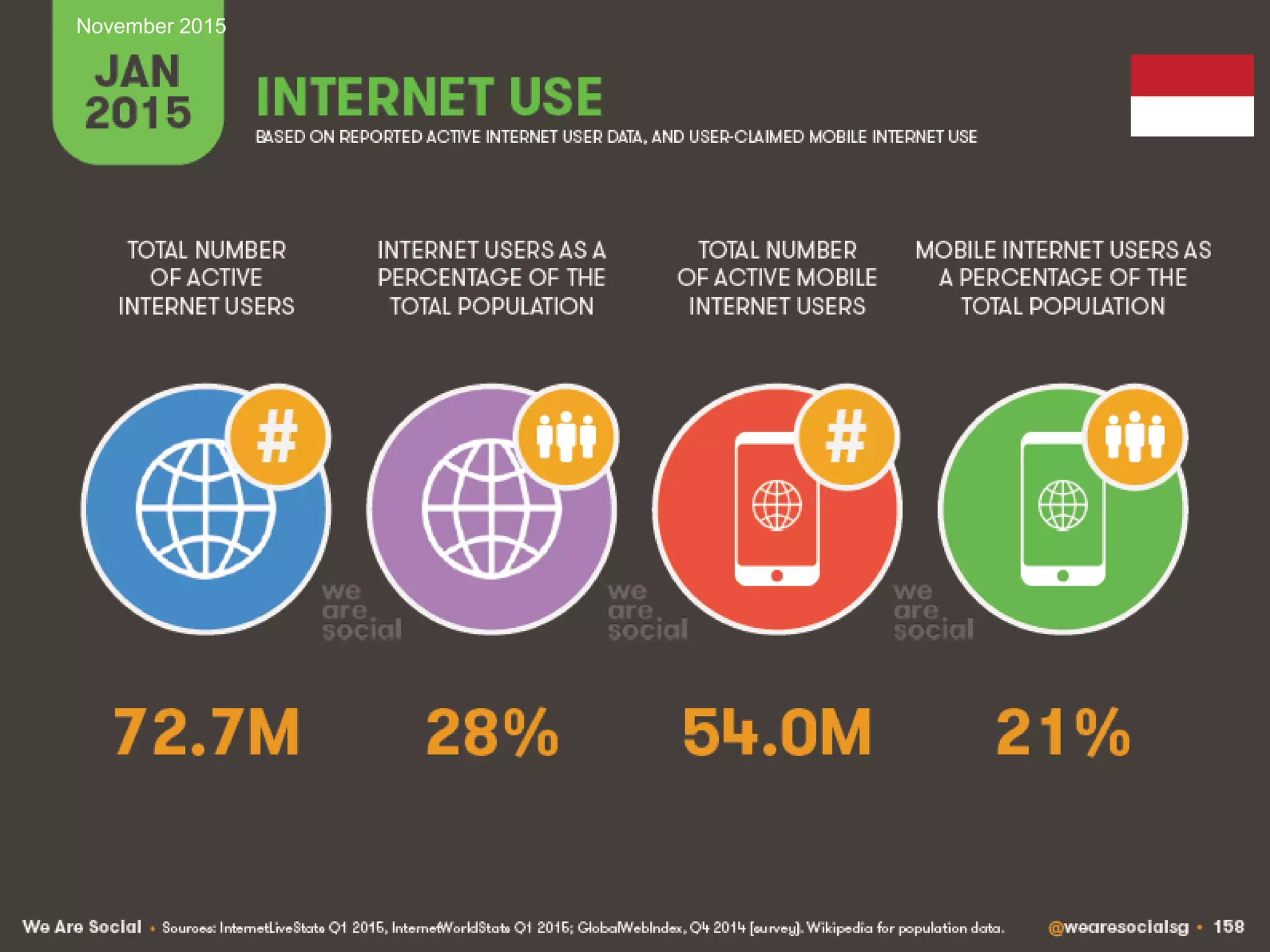
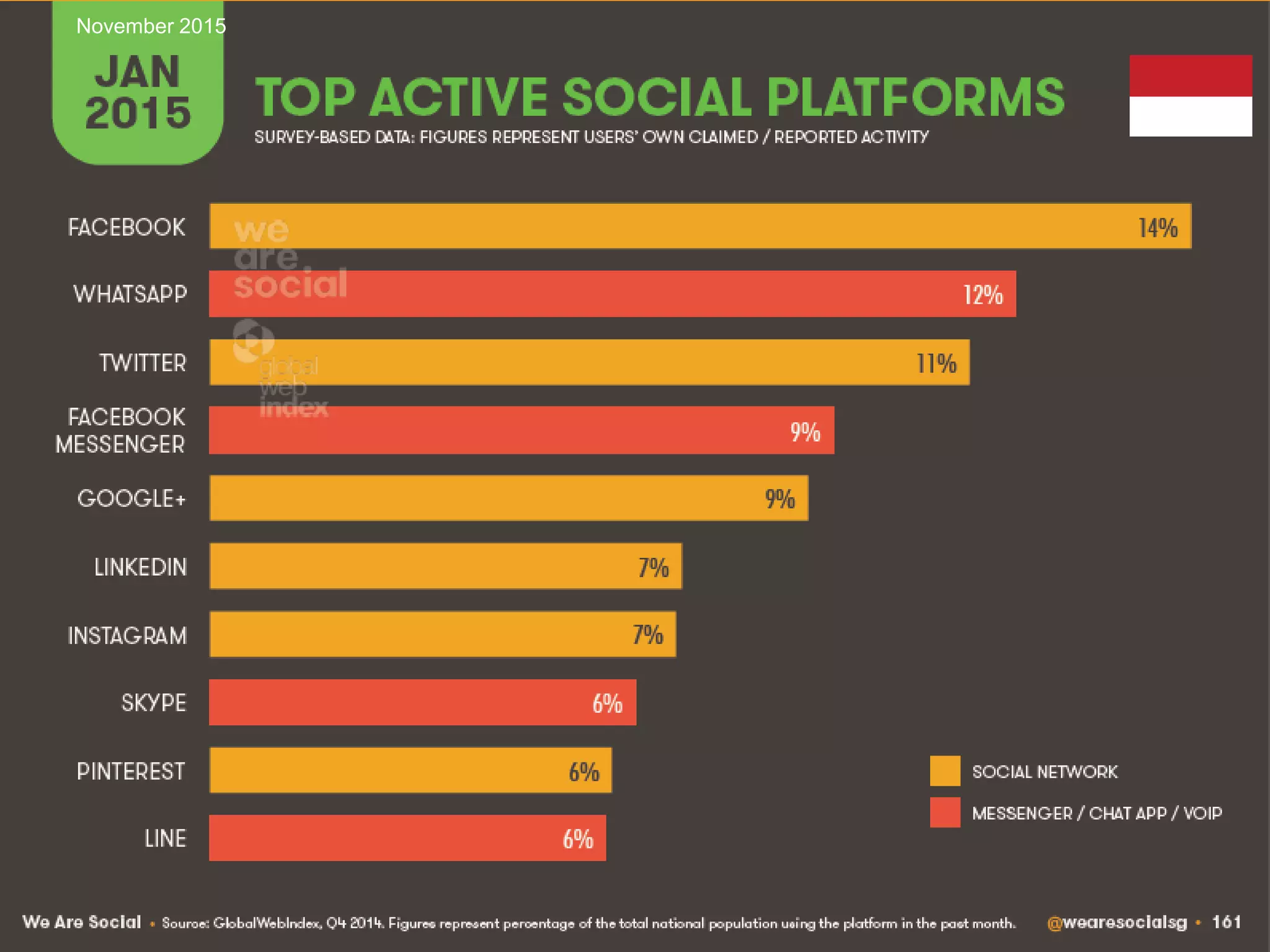

















![41
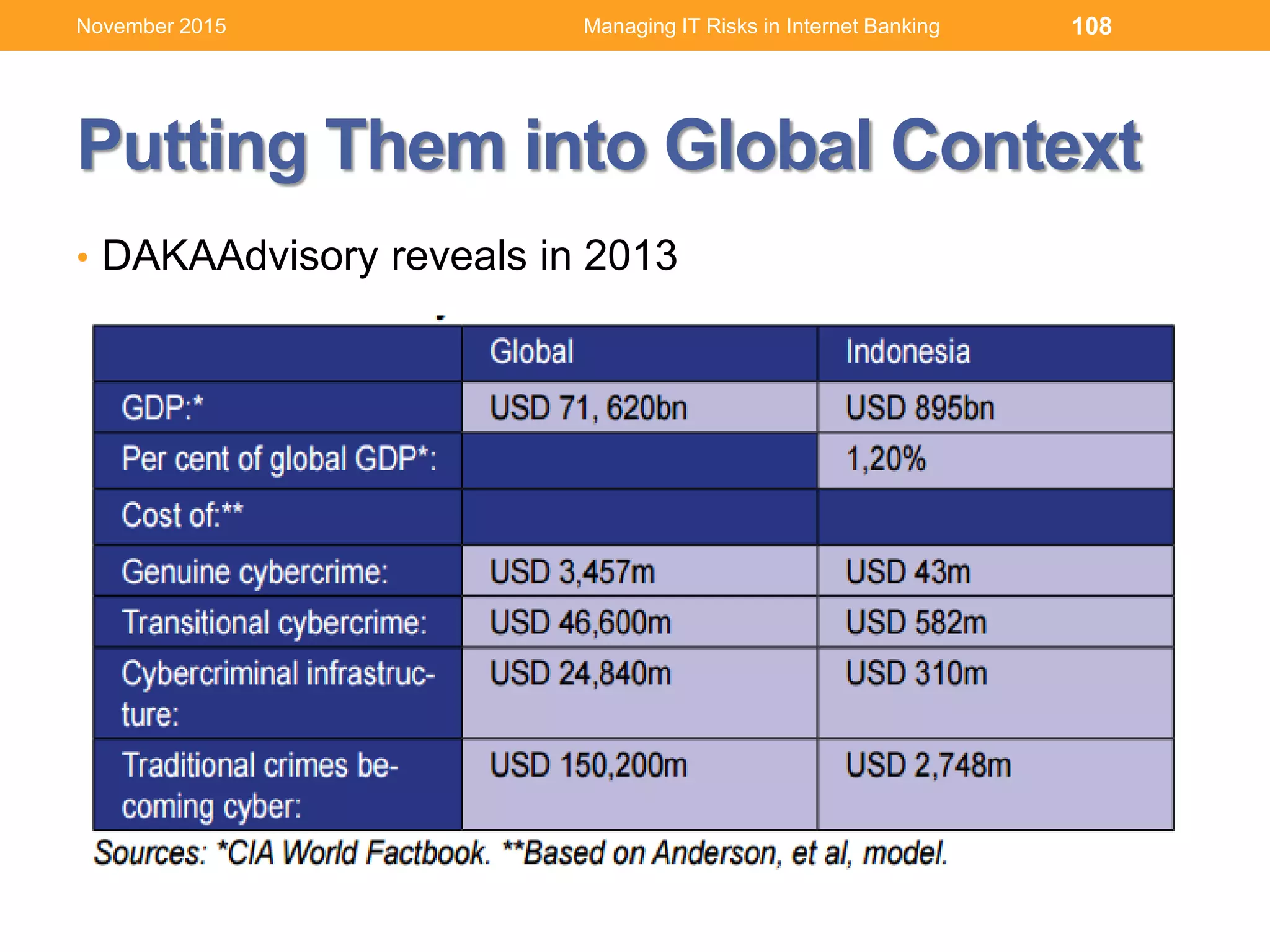
Source: IBM [1] UNODC Comprehensive Study on Cybercrime, 2013
Managing IT Risks in Internet BankingNovember 2015](https://image.slidesharecdn.com/managingitrisksininternetbankingv1-151127175650-lva1-app6892/75/Managing-IT-Risks-in-Internet-Banking-41-2048.jpg)
![42
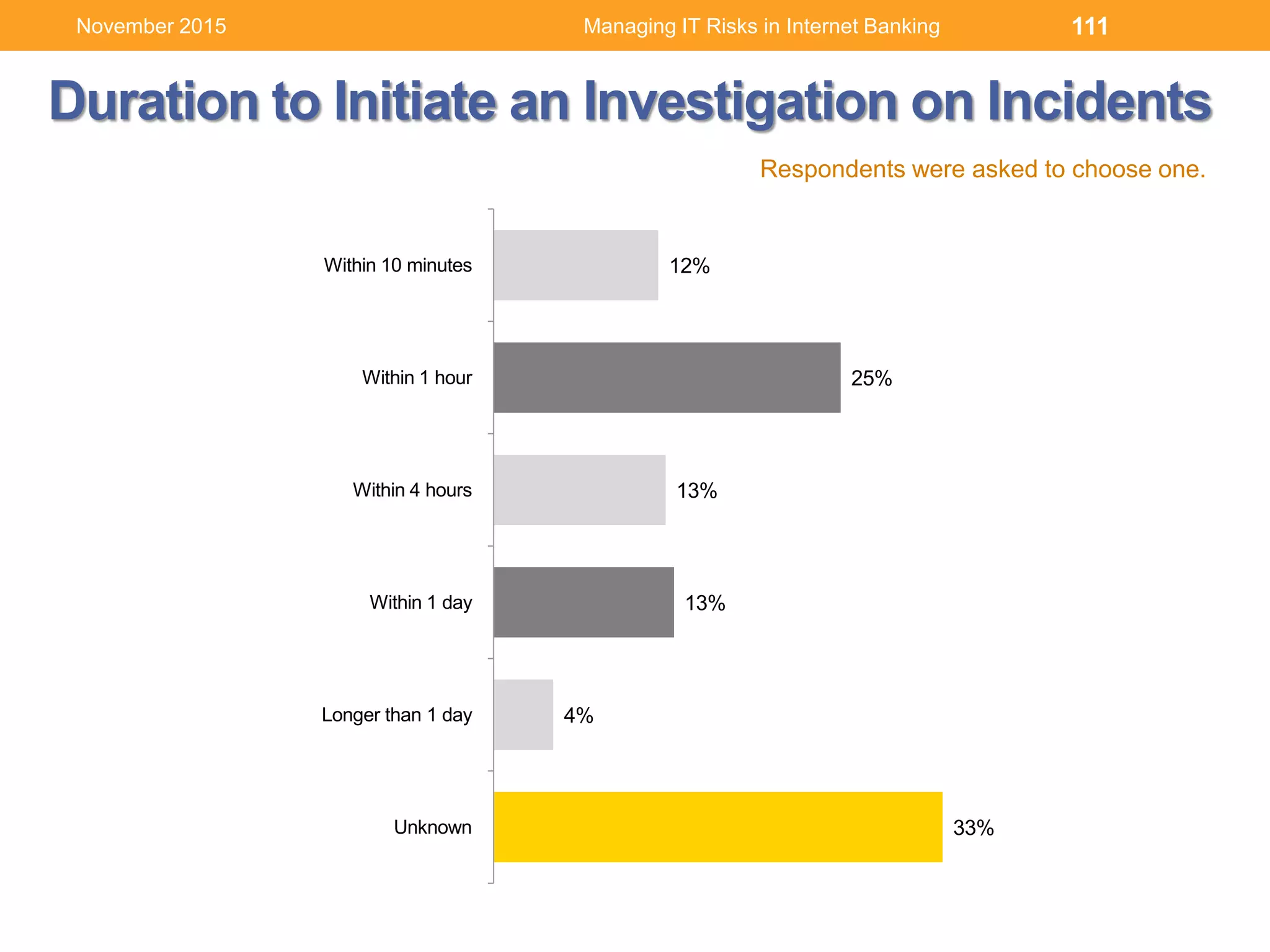
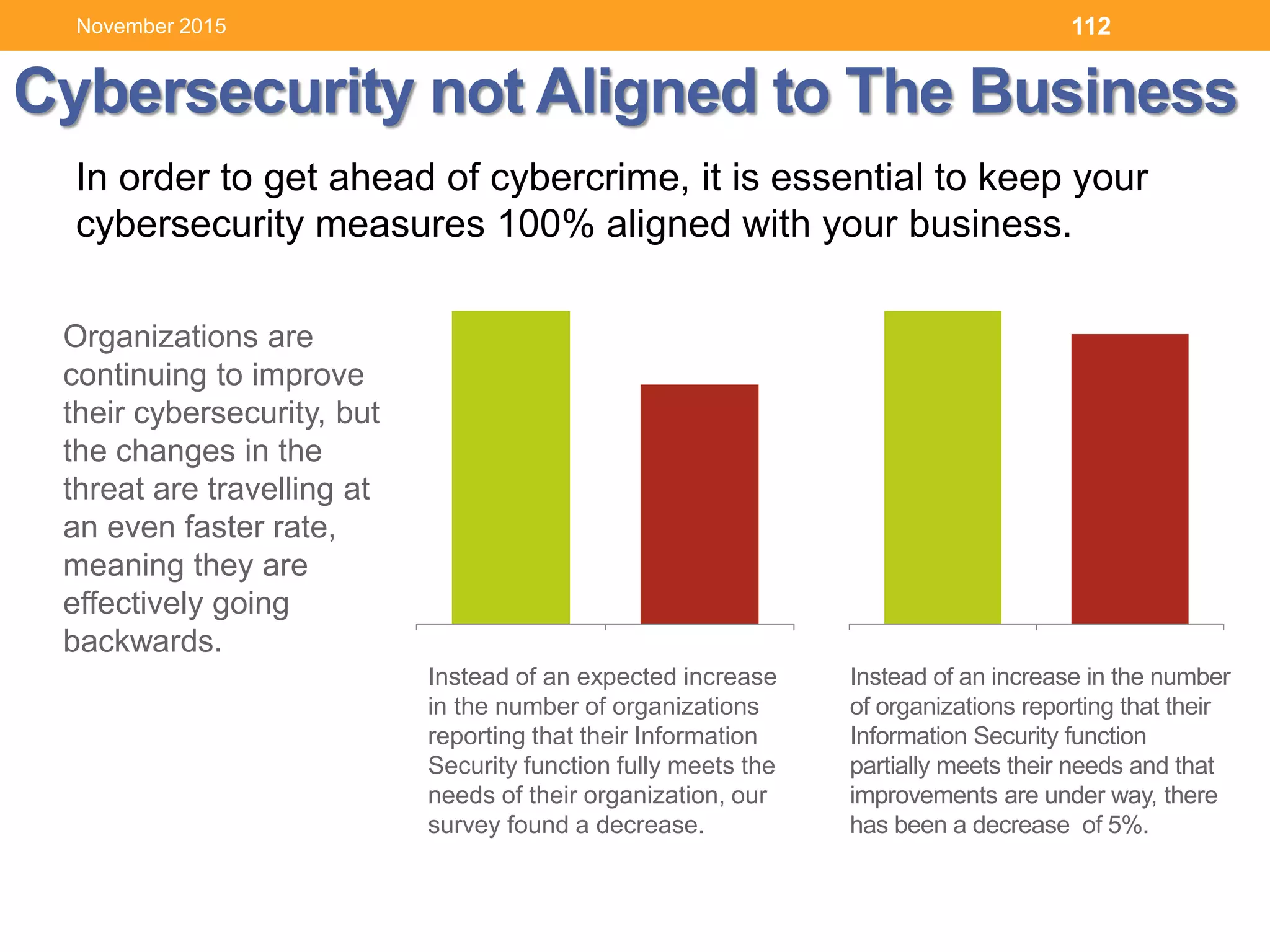
Source: IBM
[2] FBI: Crime in the United States 2013
[3] United California Bank Robbery
[4] Center for Strategic and International Studies
Managing IT Risks in Internet BankingNovember 2015](https://image.slidesharecdn.com/managingitrisksininternetbankingv1-151127175650-lva1-app6892/75/Managing-IT-Risks-in-Internet-Banking-42-2048.jpg)
![43
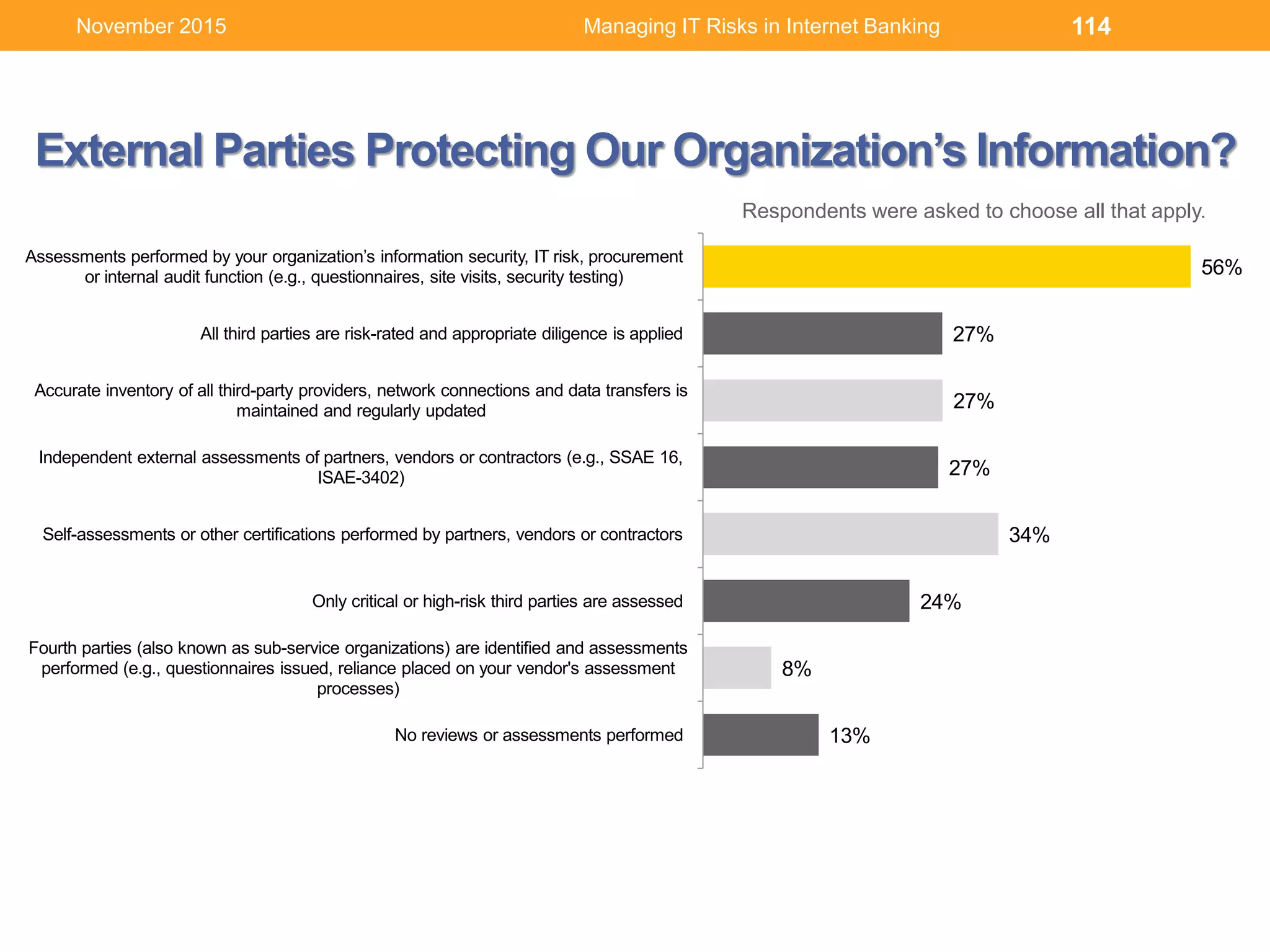
Source: IBM [6] ESG: http://bit.ly/1xzTmUW
Managing IT Risks in Internet BankingNovember 2015](https://image.slidesharecdn.com/managingitrisksininternetbankingv1-151127175650-lva1-app6892/75/Managing-IT-Risks-in-Internet-Banking-43-2048.jpg)