The document is a comprehensive introduction to Management Information Systems (MIS), authored by Yekini Nureni Asafe and Oyeyinka Isaiah Kolawole, aimed at students of various disciplines in Nigerian polytechnics and colleges. It covers theoretical and practical aspects of MIS, detailing objectives, contents, and instructional guidelines for users, alongside a thorough exploration of data, information, and various system concepts. Additionally, it emphasizes the significance of information for decision-making and the roles of both manual and computer-based information systems.














































































































![110 – Management Information System “Mordern Perspective” Yekini & Oyeyinka 2013
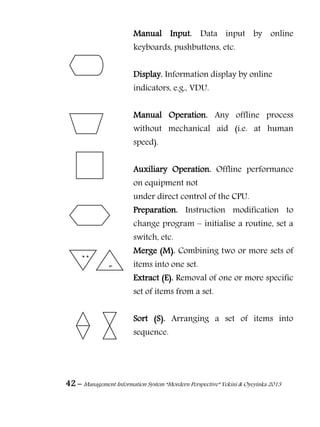
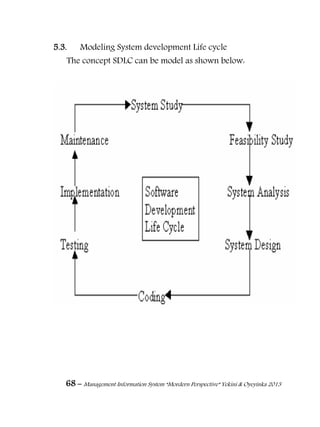
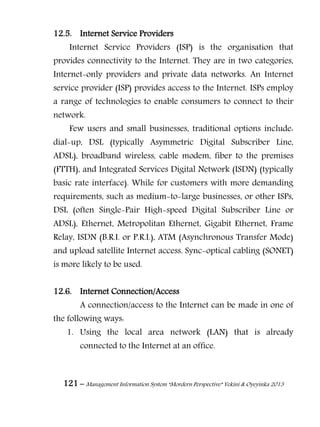
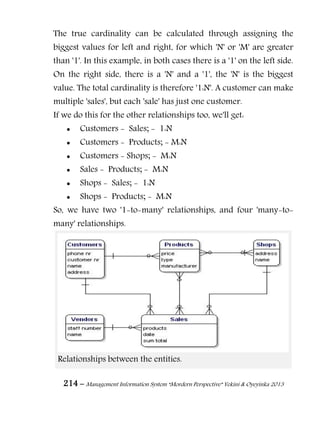
11.4. Storage Media
Regardless of the repository model that is used, the data
has to be stored on some data storage medium somewhere. Some
of the data storage media are discussed as follows.
11.4.1. Magnetic Tape
Magnetic tape has long been the most commonly used medium
for bulk data storage, backup, archiving, and interchange. Tape
has typically had an order of magnitude better capacity/price
ratio when compared to hard disk, but recently the ratios for tape
and hard disk have become a lot closer.[6]
There are myriad
formats, many of which are proprietary or specific to certain
markets like mainframes or a particular brand of personal
computer. Tape is a sequential access medium, so even though
access times may be poor, the rate of continuously writing or
reading data can actually be very fast. Some new tape drives are
even faster than modern hard disks. A principal advantage of tape
is that it has been used for this purpose for decades (much longer
than any alternative) and its characteristics are well understood.
11.4.2. Hard Disk
The capacity/price ratio of hard disk has been rapidly improving
for many years. This is making it more competitive with magnetic](https://image.slidesharecdn.com/managementinformationsystemmorderperspective-150512052007-lva1-app6891/85/Management-information-system-mordern-perspective-120-320.jpg)




















































































































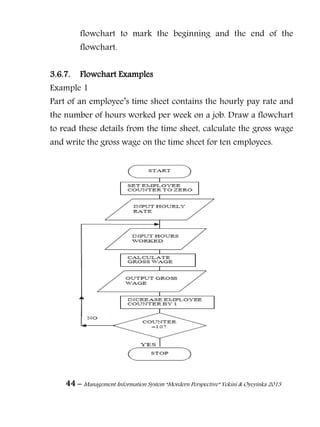
![247 – Management Information System “Mordern Perspective” Yekini & Oyeyinka 2013
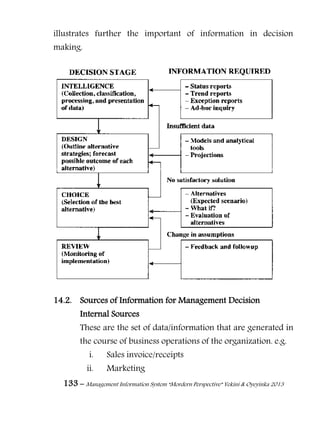
appear (in databases, log files, backups, printed receipts,
and so on), and by restricting access to the places where it
is stored. If an unauthorized party obtains the card
number in any way, a breach of confidentiality has
occurred. Confidentiality is necessary (but not sufficient)
for maintaining the privacy of the people whose personal
information a system holds.[citation needed]
2. Integrity: In information security, data integrity means
maintaining and assuring the accuracy and consistency of
data over its entire life-cycle. [6] This means that data
cannot be modified unauthorized or undetected. This is
not the same thing as referential integrity in databases,
although it can be viewed as a special case of Consistency
as understood in the classic ACID model of transaction
processing. Integrity is violated when a message is actively
modified in transit. Information security systems typically
provide message integrity in addition to data
confidentiality.
3. Availability: For any information system to serve its
purpose, the information must be available when it is
needed. This means that the computing systems used to
store and process the information, the security controls
used to protect it, and the communication channels used
to access it must be functioning correctly. High availability
systems aim to remain available at all times, preventing](https://image.slidesharecdn.com/managementinformationsystemmorderperspective-150512052007-lva1-app6891/85/Management-information-system-mordern-perspective-257-320.jpg)















![264 – Management Information System “Mordern Perspective” Yekini & Oyeyinka 2013
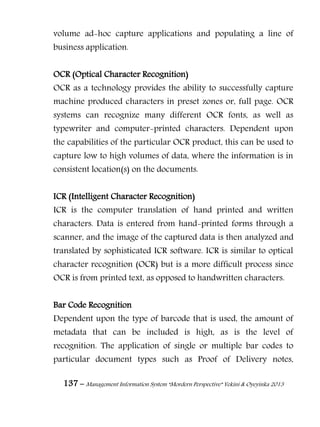
Answer to Multiple Choice Questions
1. Strategic information 2. Sorting
3. Expert systems 4. Management Information
System [MIS]
5. Batch processing 6. Real time
7. Hertz 8. Baud rate
9. Protocol 10. Gateway
11. A system is a group of related elements
or activities that are organized for a
specific purpose or to achieve a
common objective.
12. Stochastic / Probabilistic
System
13. Negative feedback 14. Spoofing
15. Salami technique 16. Trojan Horse
17. Security 18. Privacy
19. Video conferencing 20. Cost-benefit
21. Efficiency 22. Prototype
23. Operational Feasibility and Social
Feasibility
24. Direct changeover
25. Documentation 26. Corrective
27. File conversion 28. System Development
Methodology
29. Fact-finding 30. Firewalls
31. Management ACCOUNTING 32. Information technology
(IT)
33. IS strategy 34. Data processing (DP) era
35. Strategic Information Systems (SIS) 36. Technology push
37. Virtual Market Ecosystem 38. Value Chain
39. E-business 40. Supply Chain Analysis](https://image.slidesharecdn.com/managementinformationsystemmorderperspective-150512052007-lva1-app6891/85/Management-information-system-mordern-perspective-274-320.jpg)







