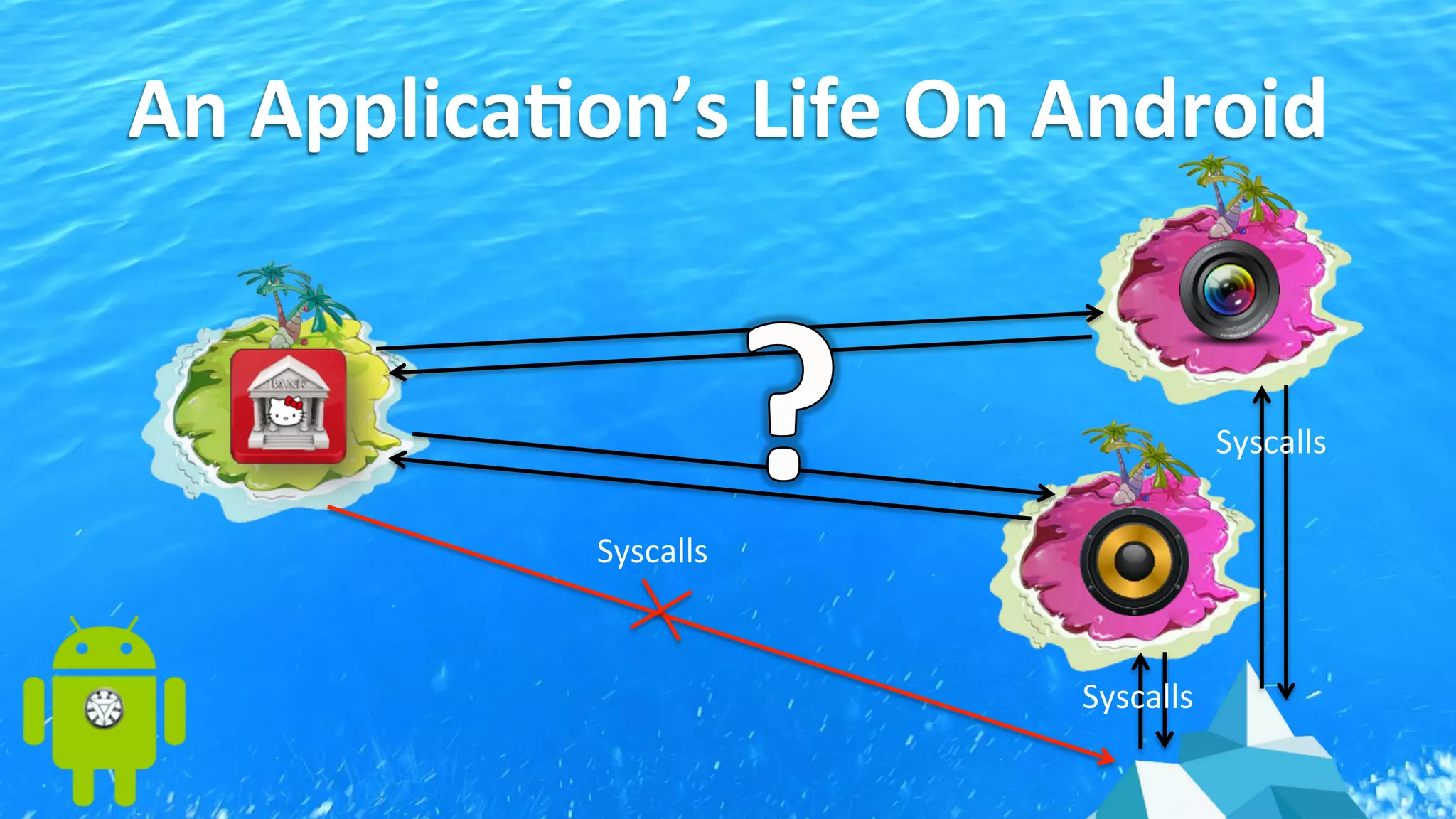
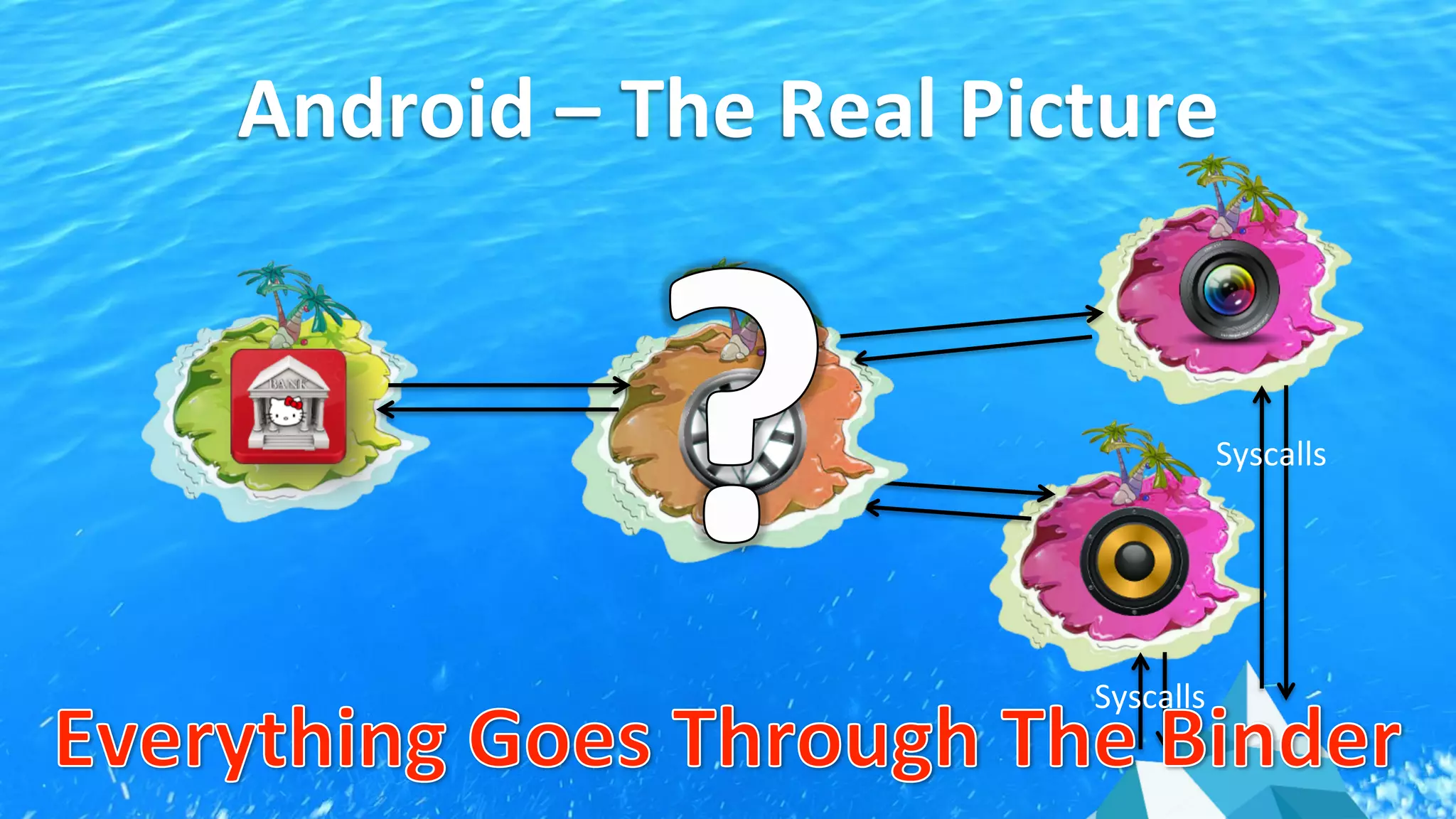
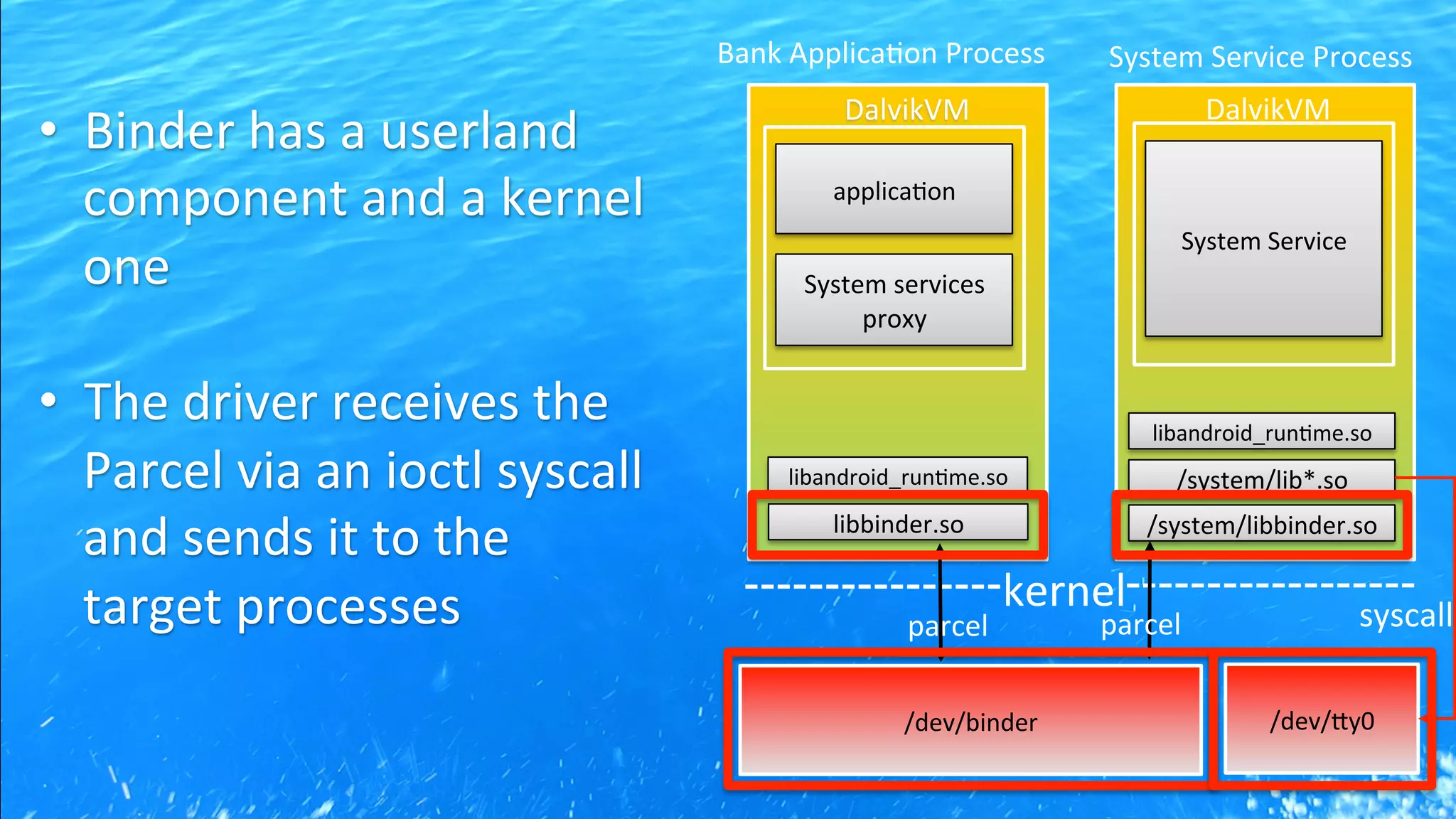
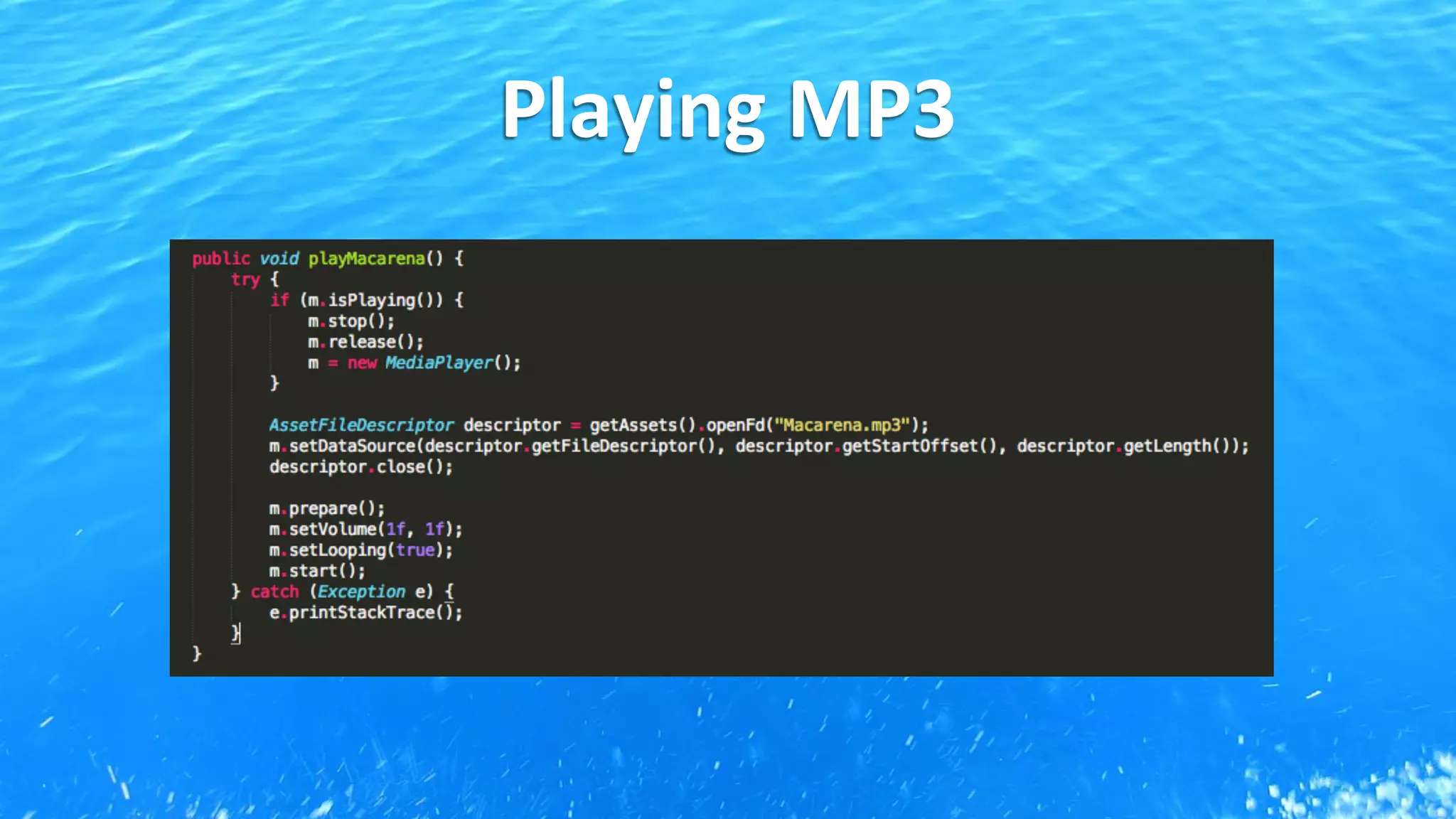
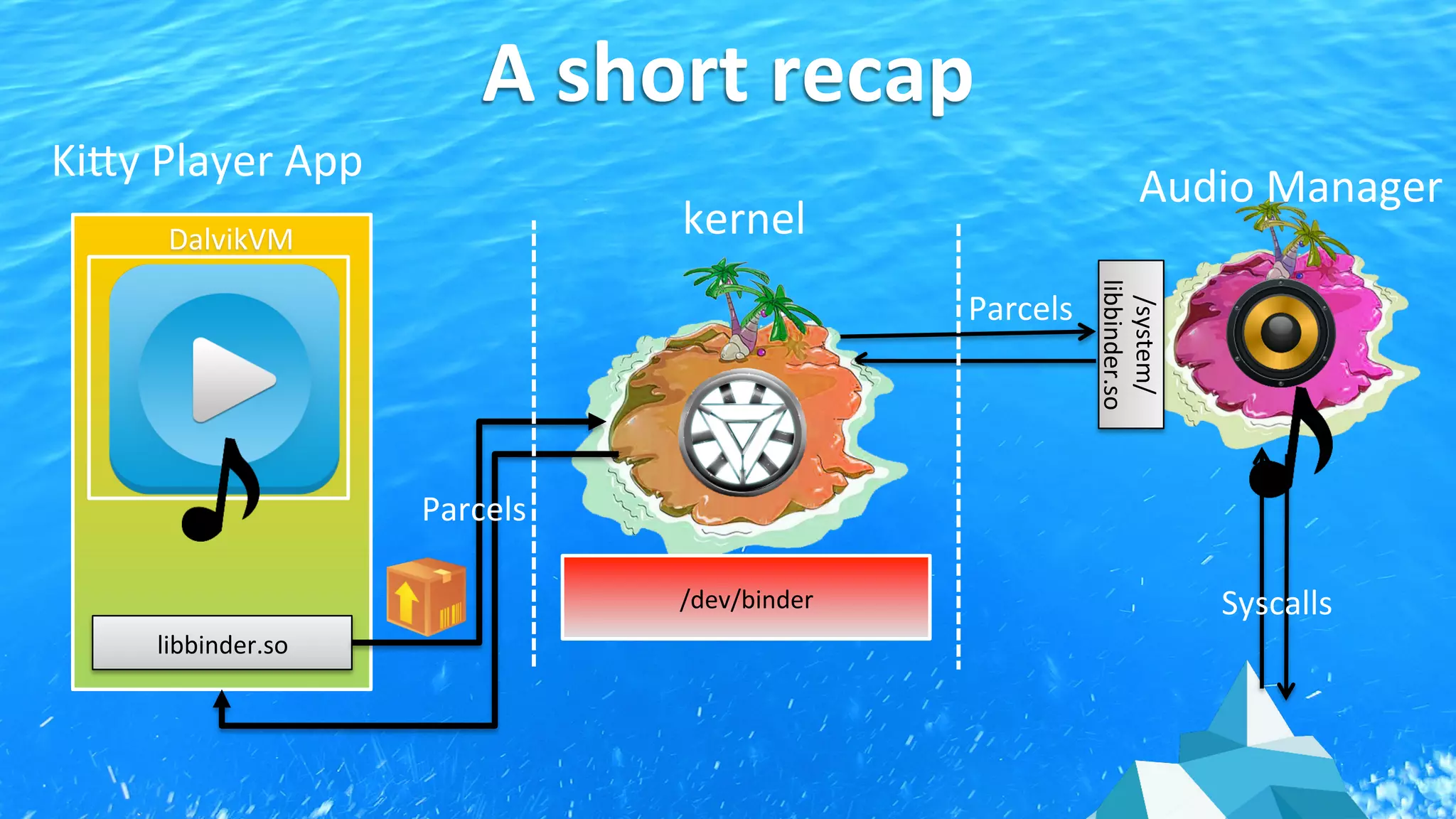
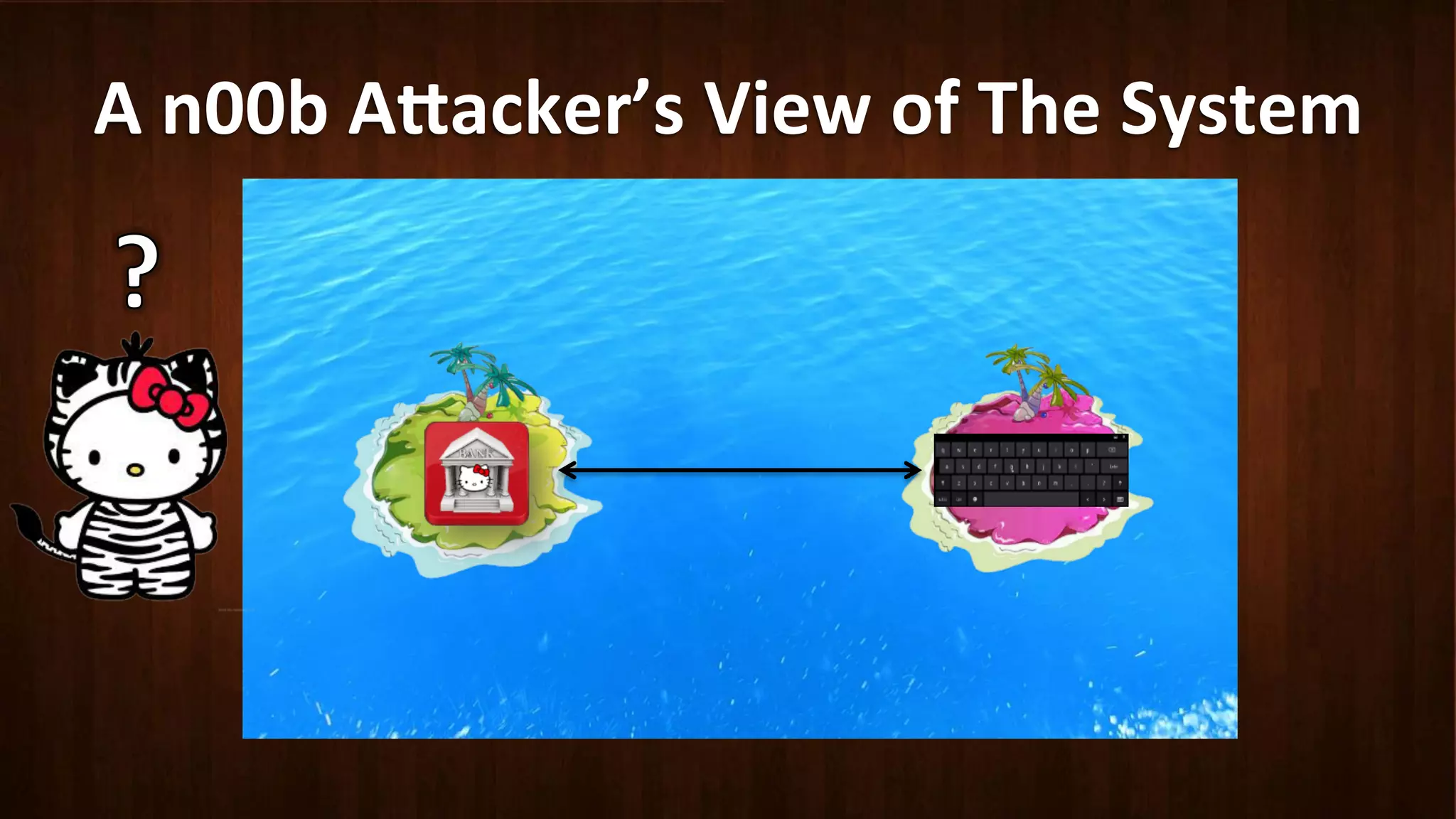
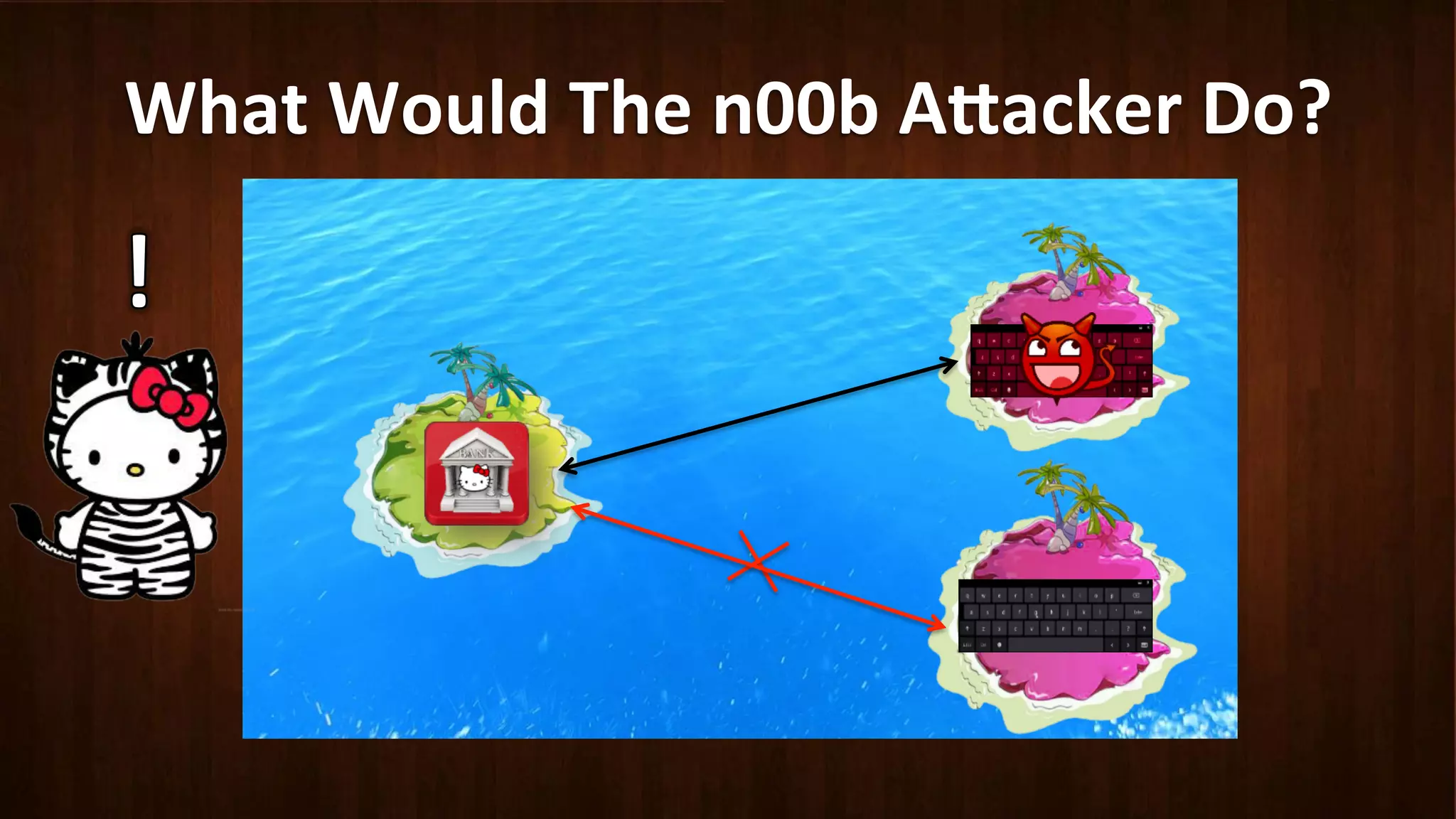
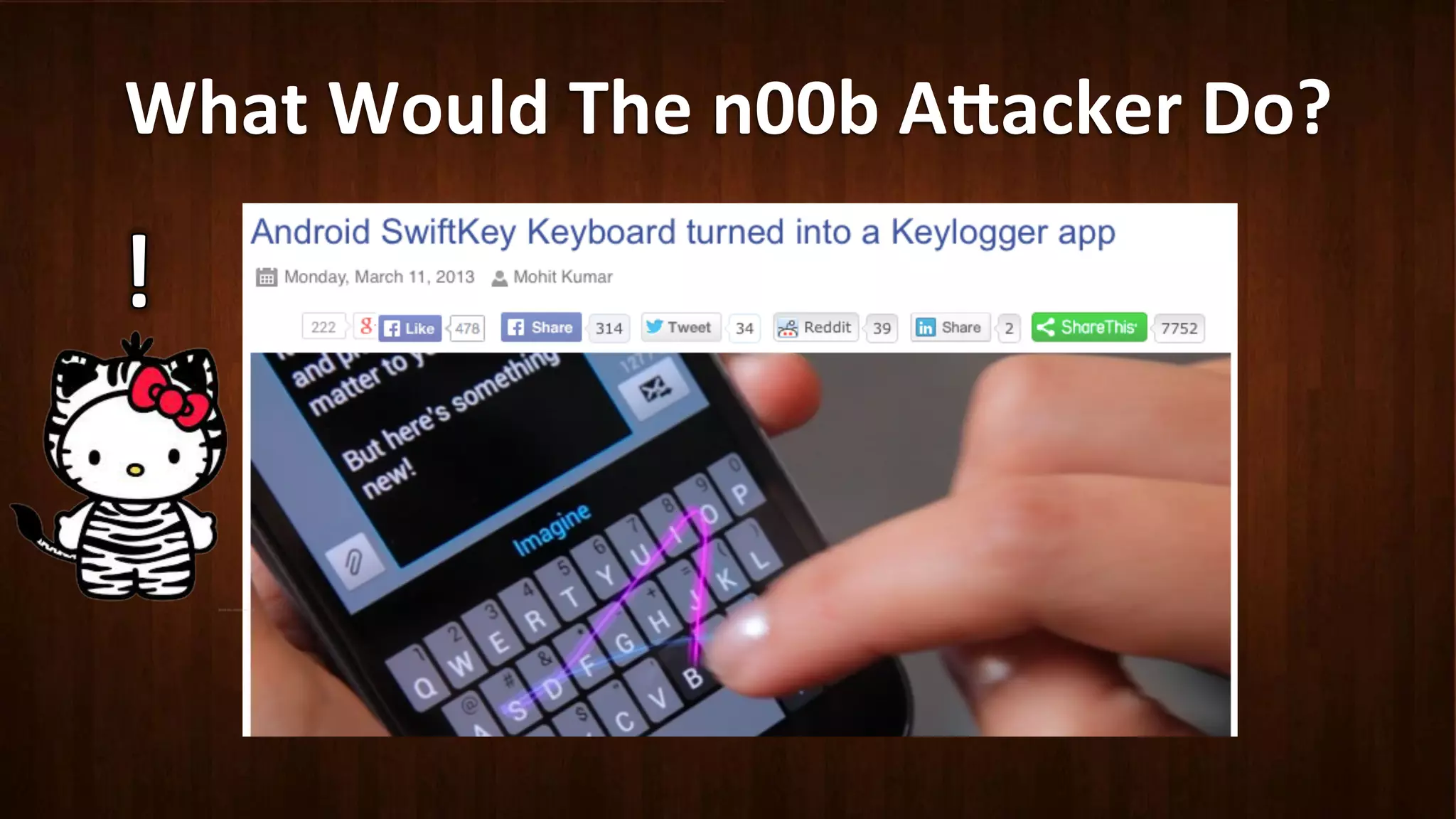
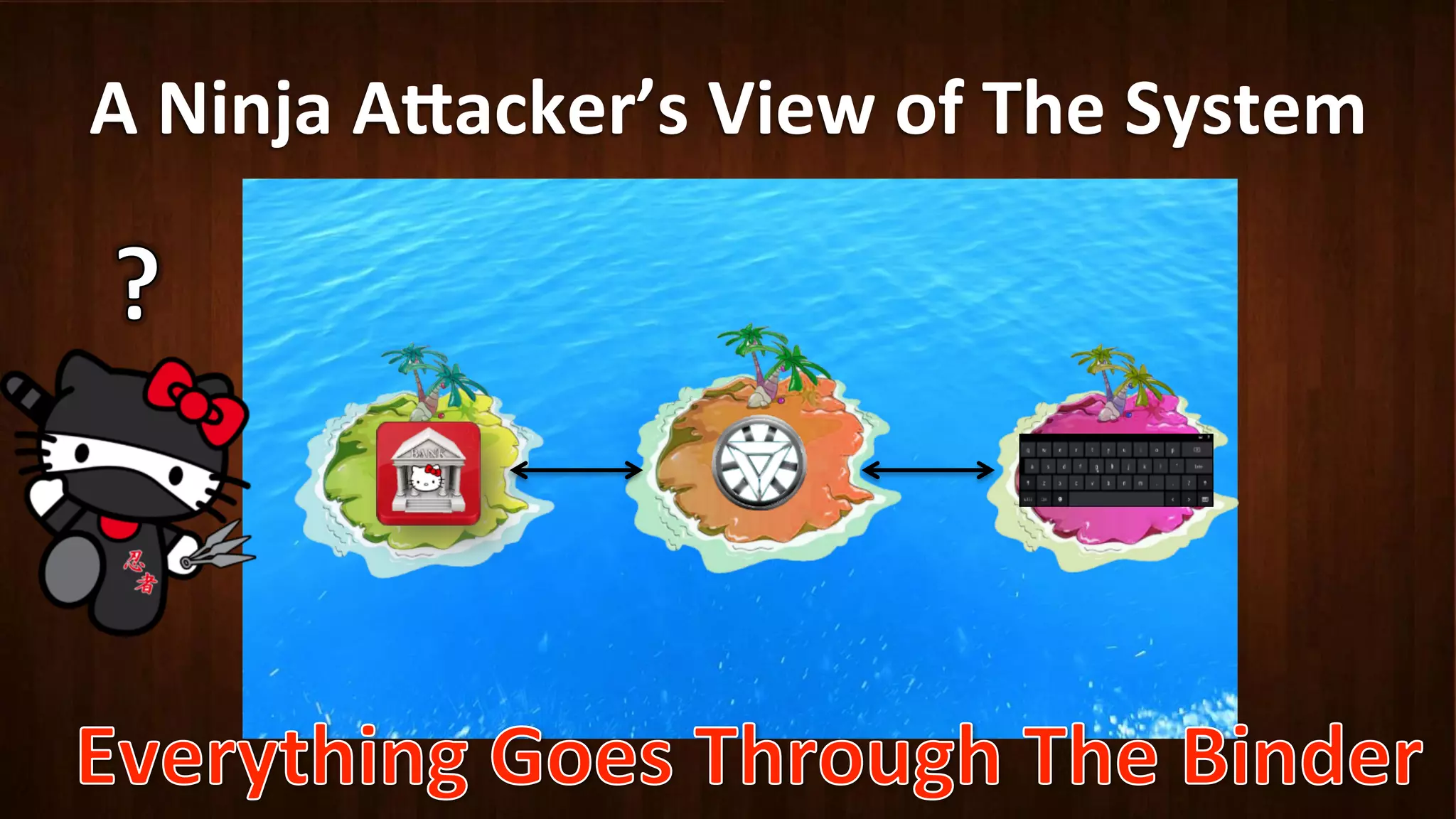
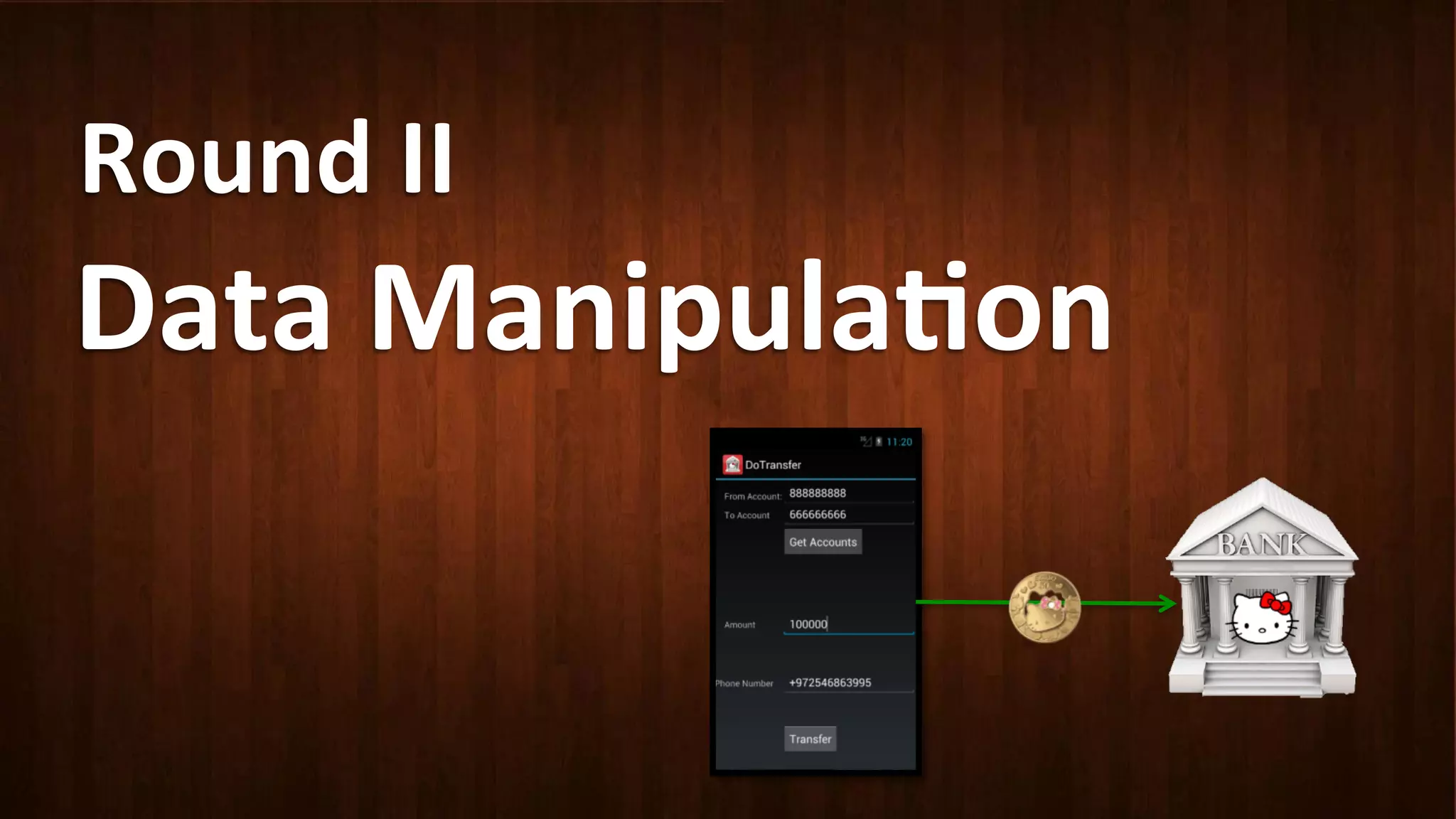
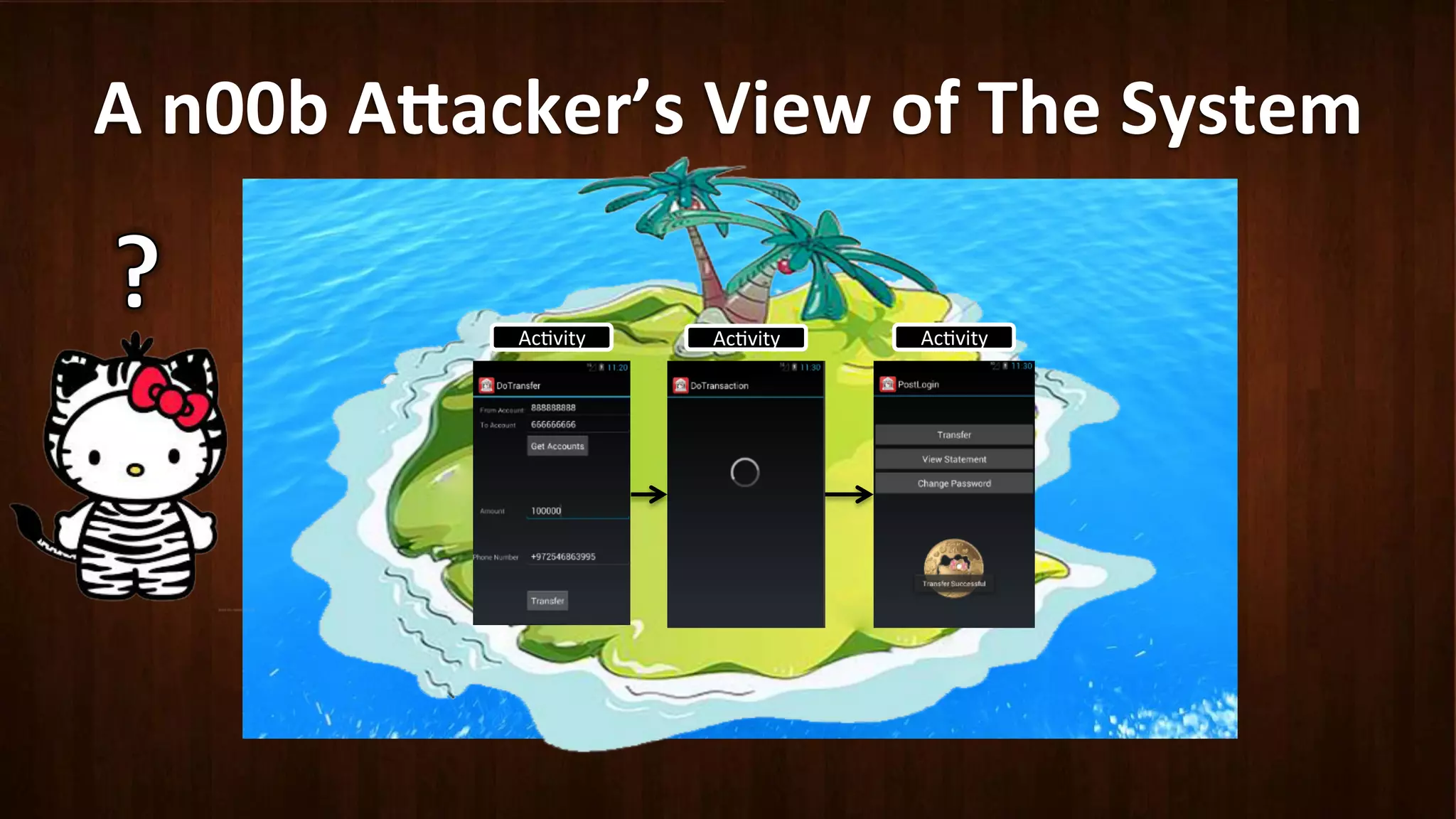
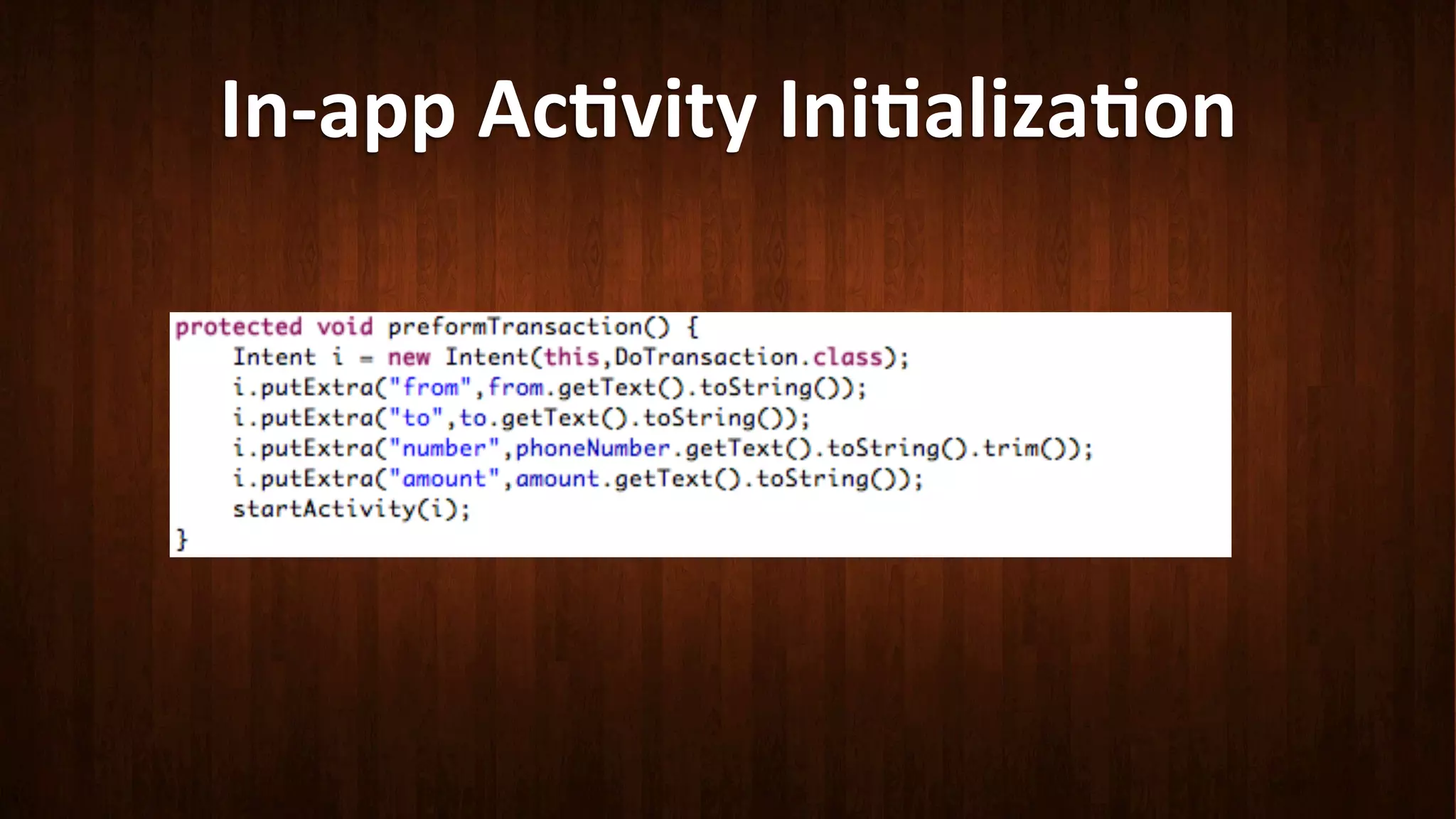
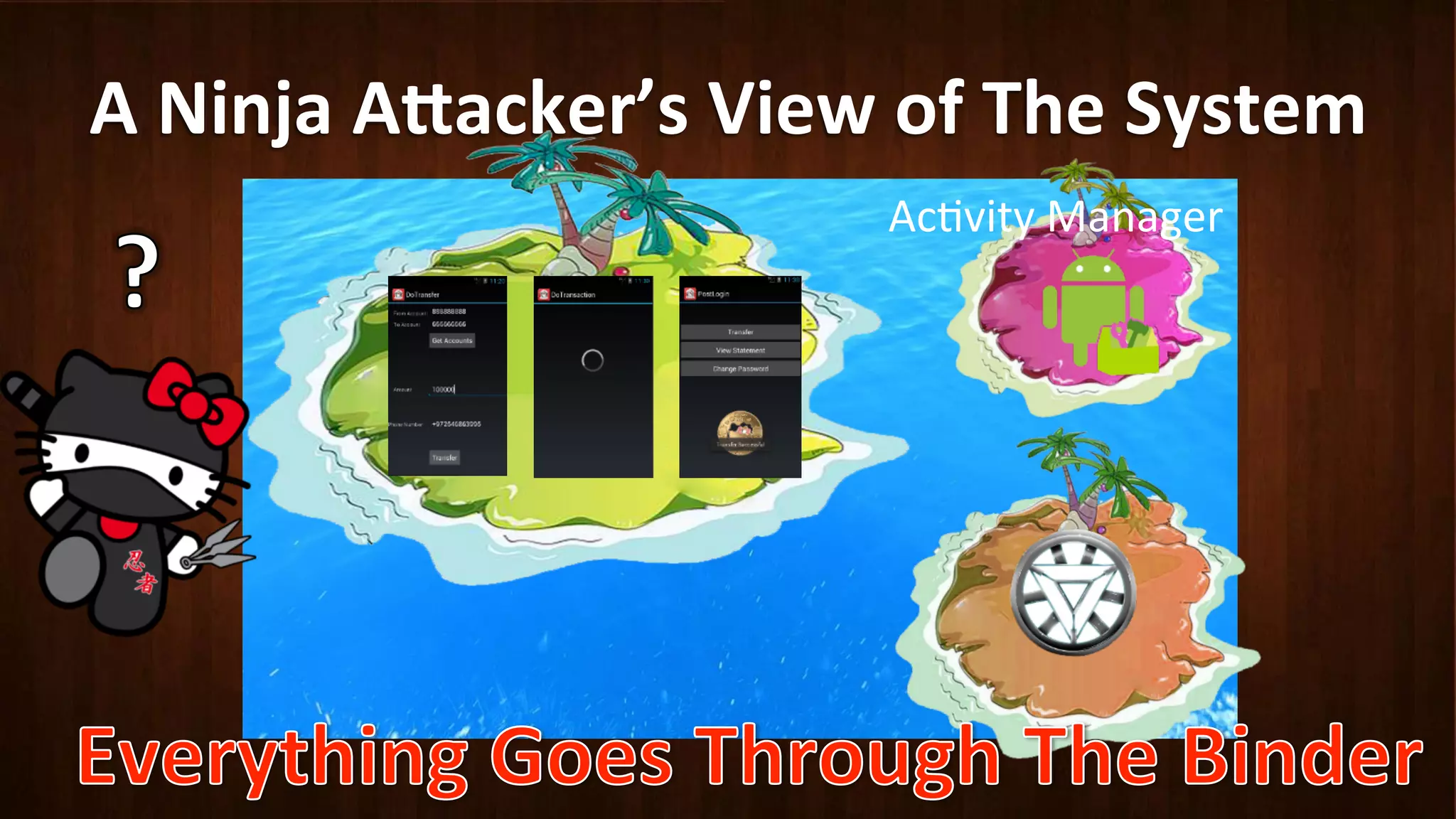
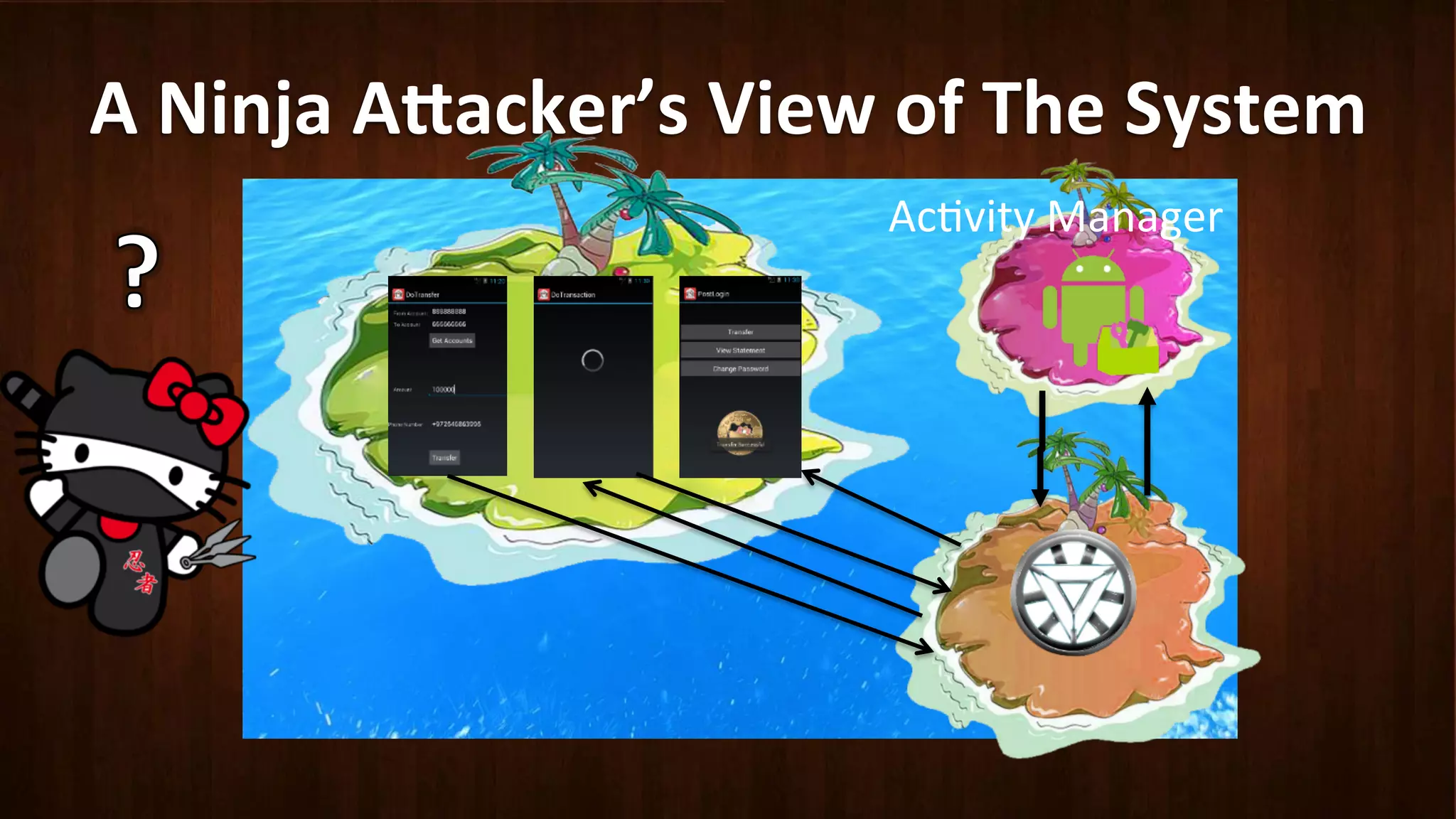
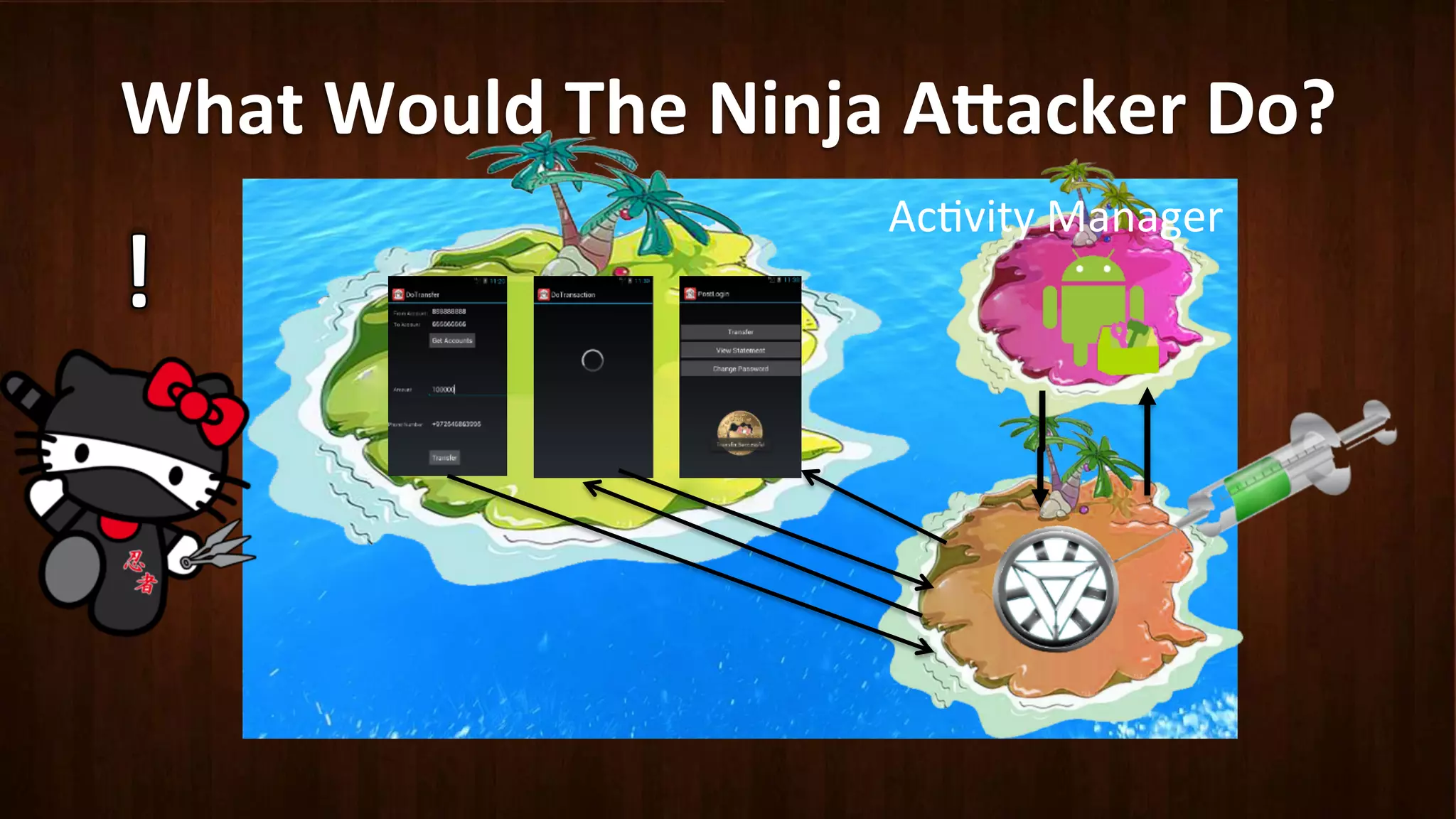
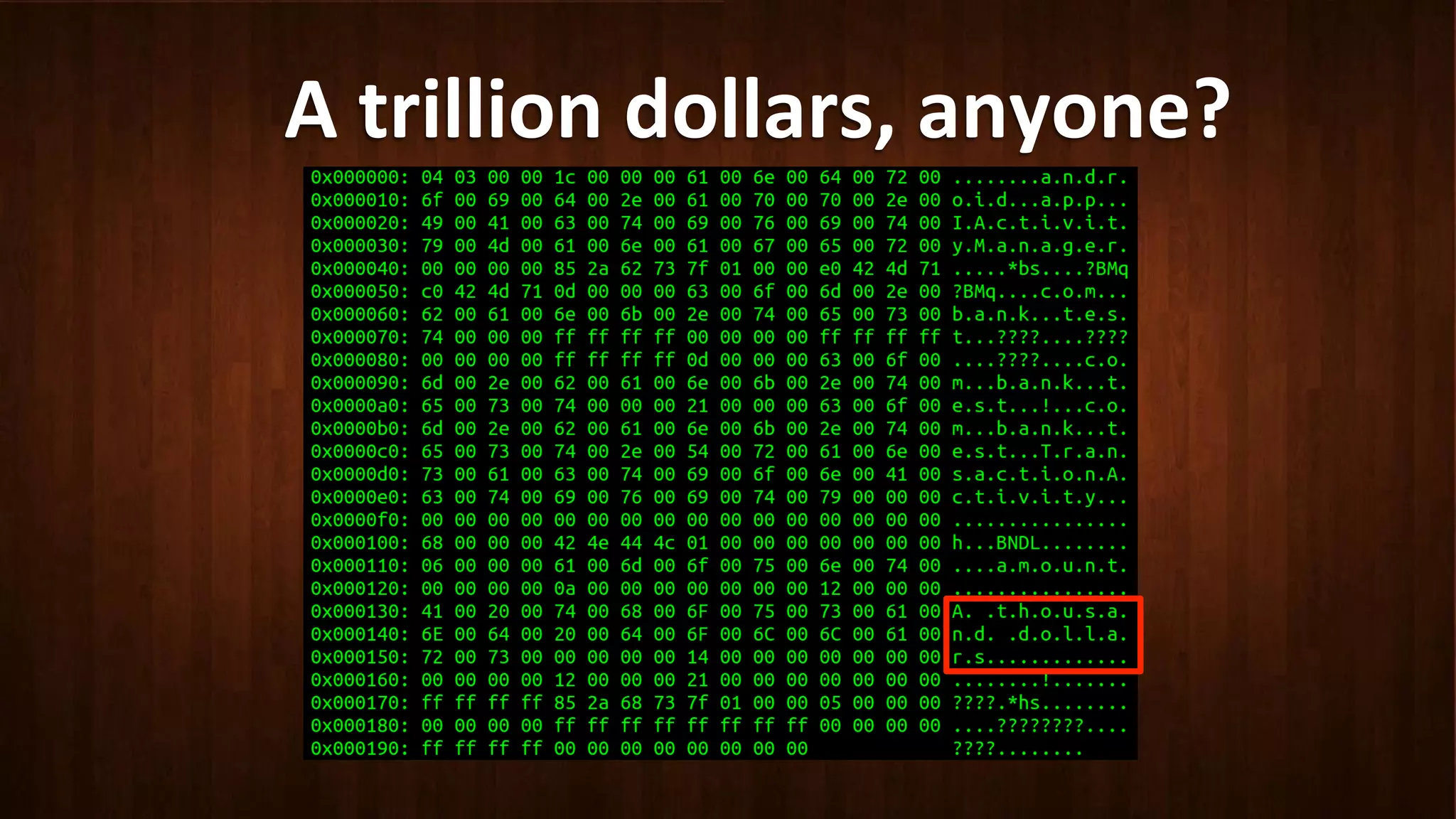
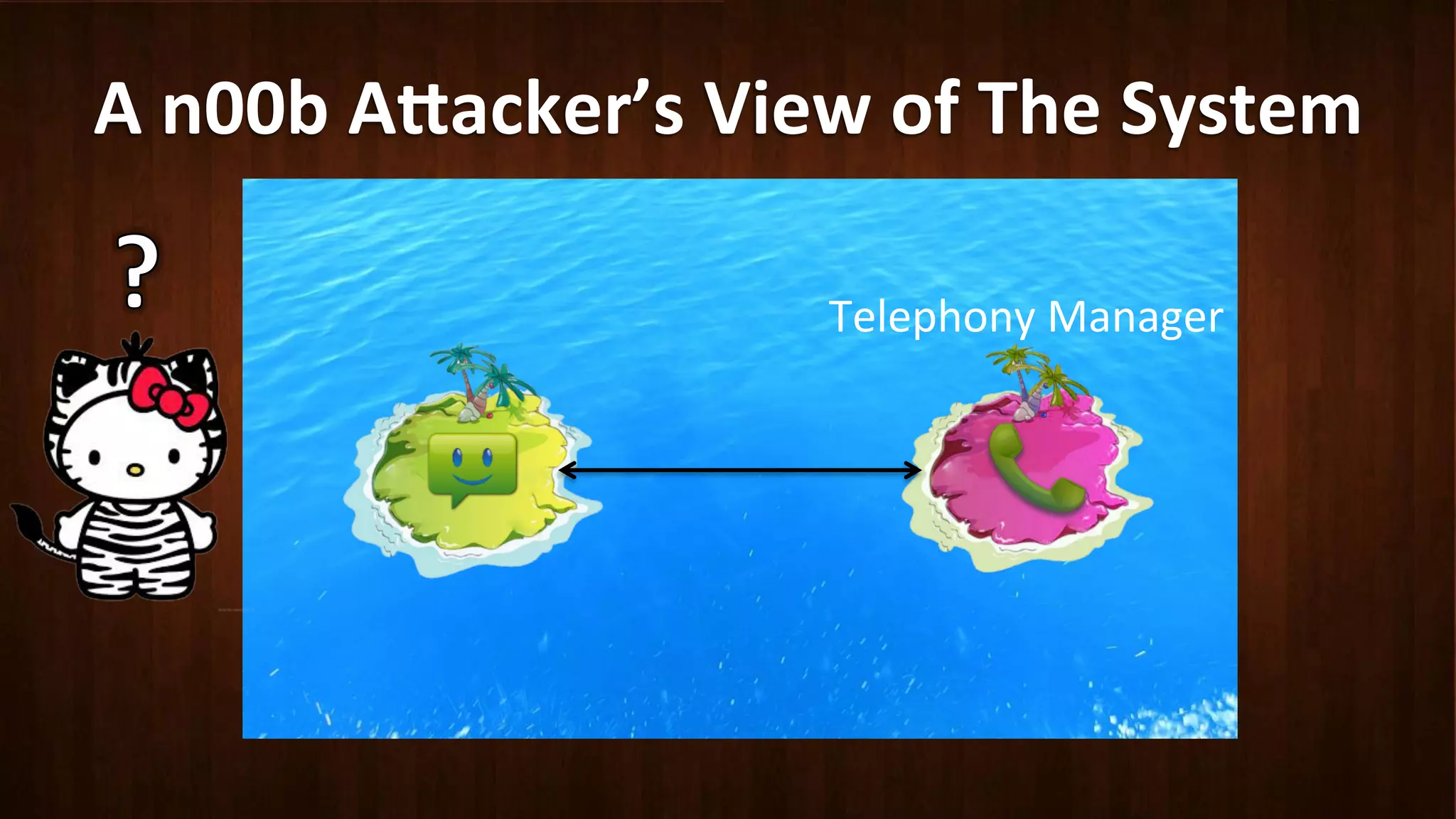
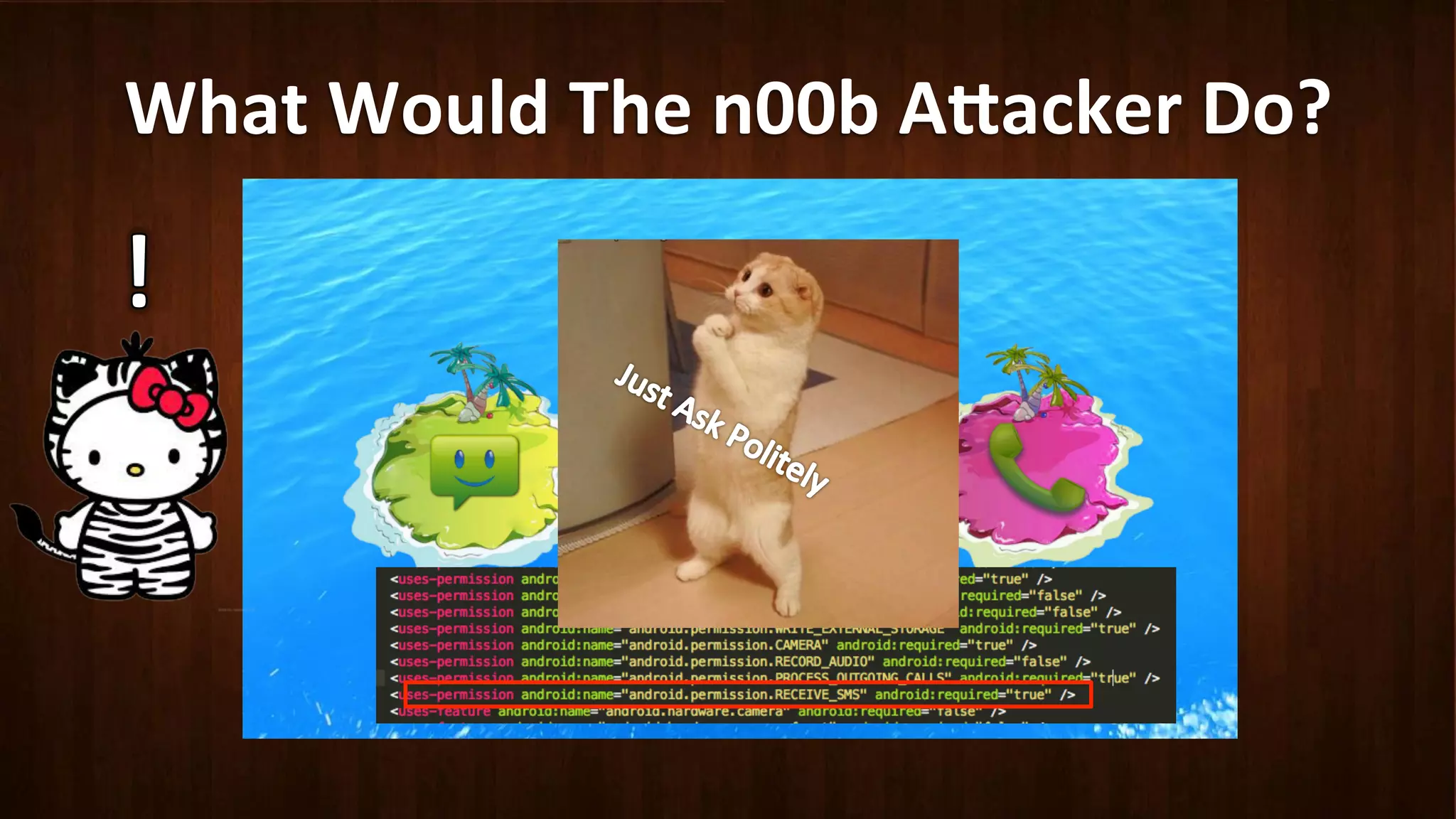
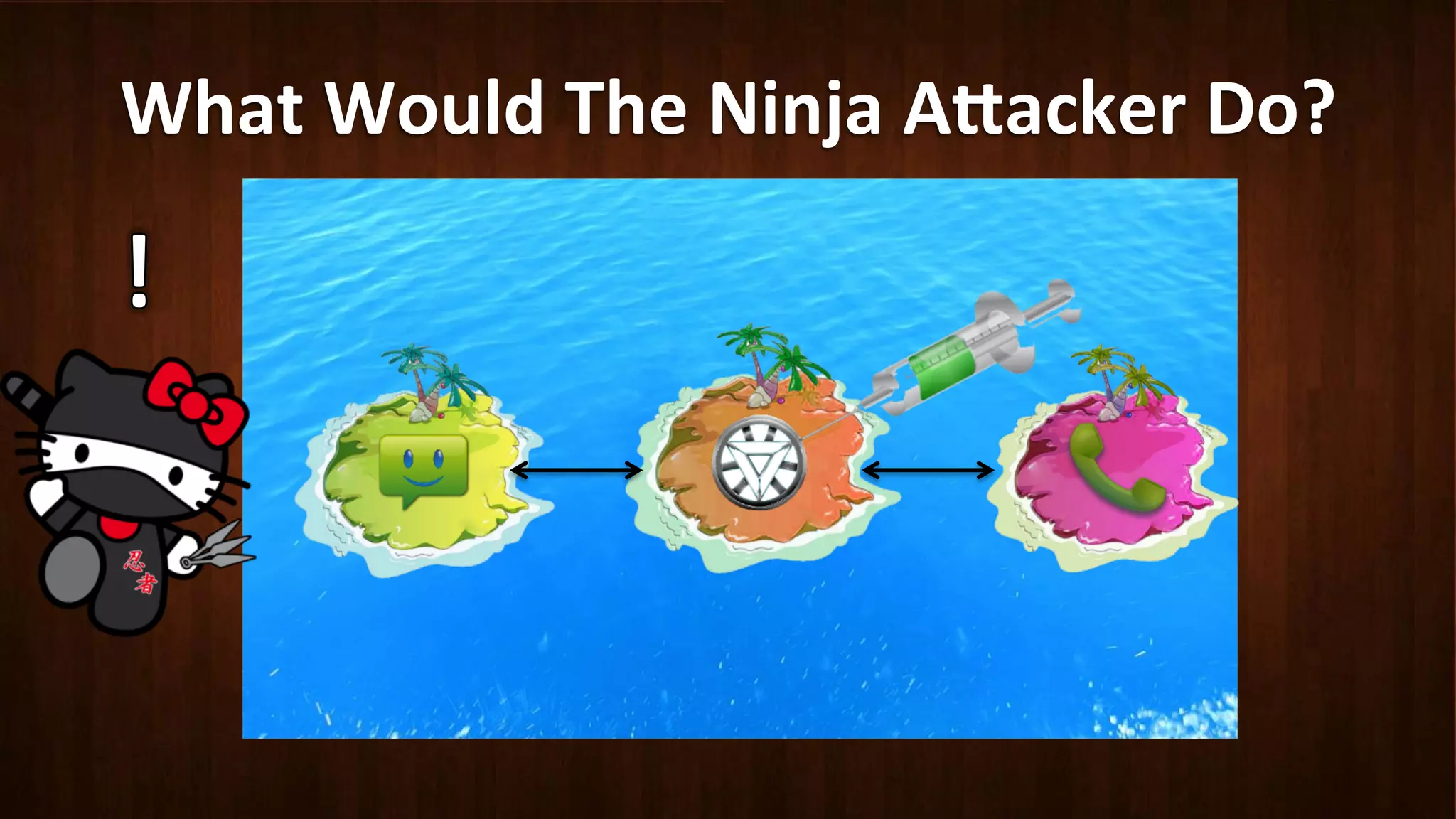
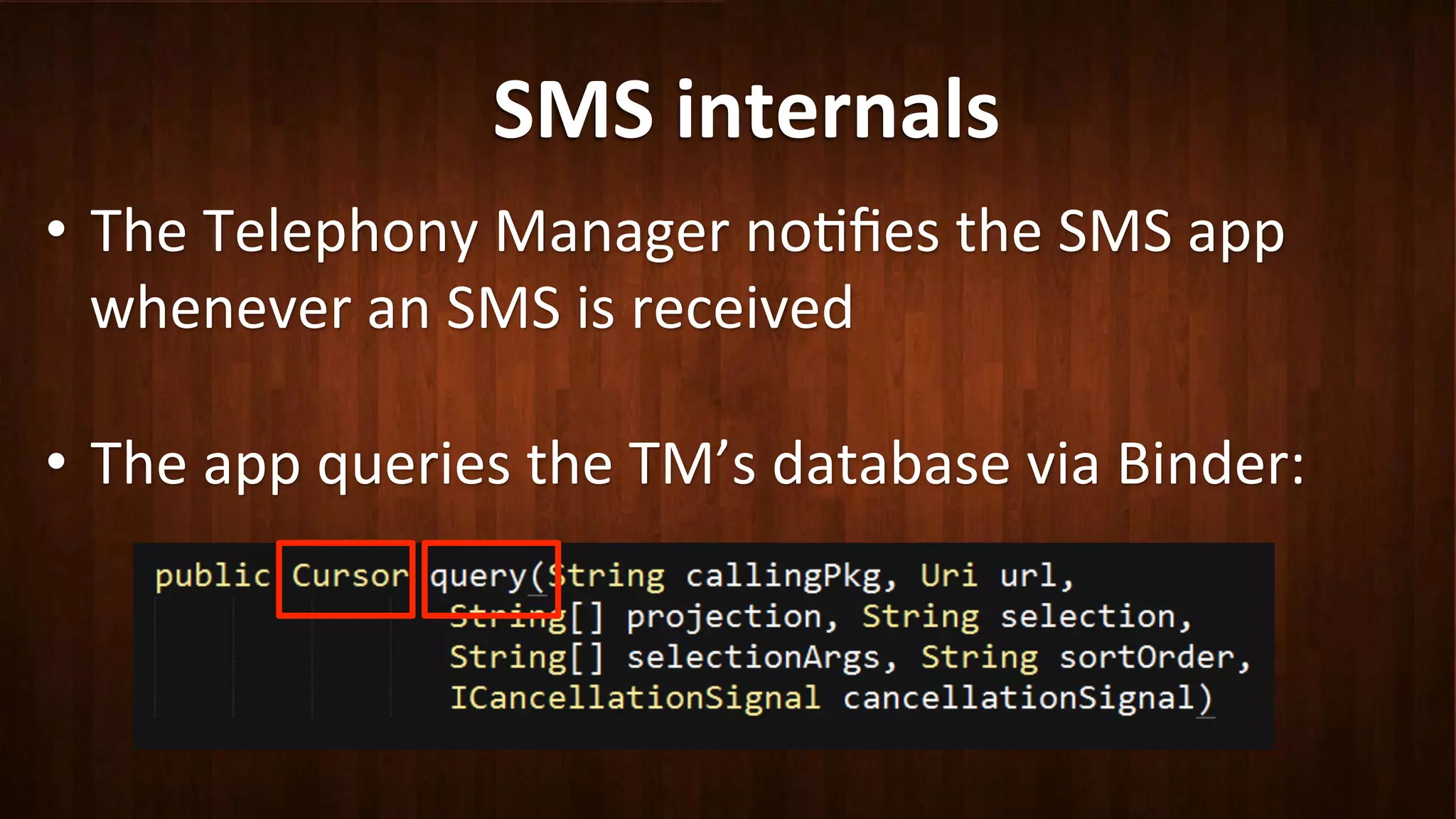
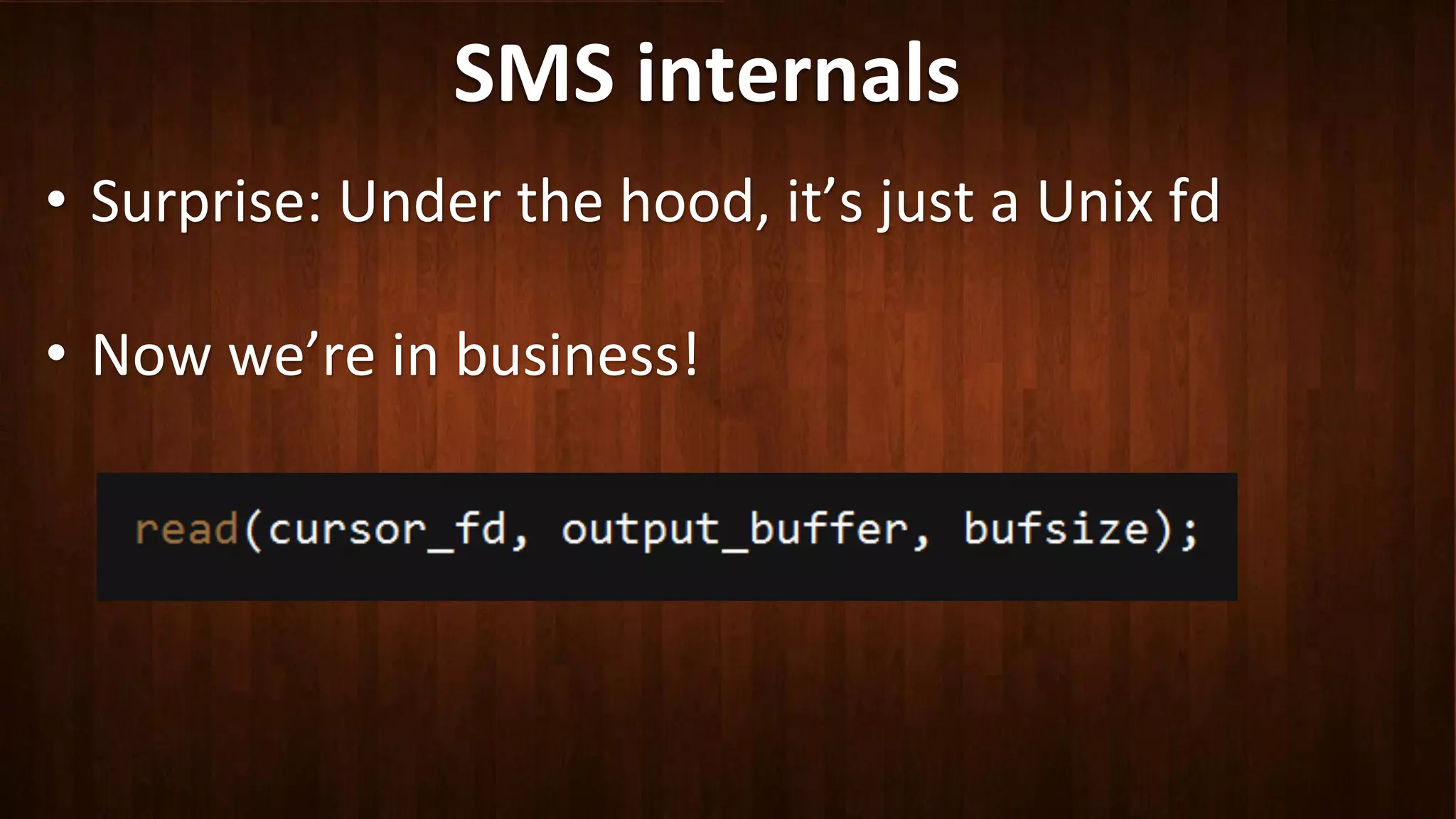
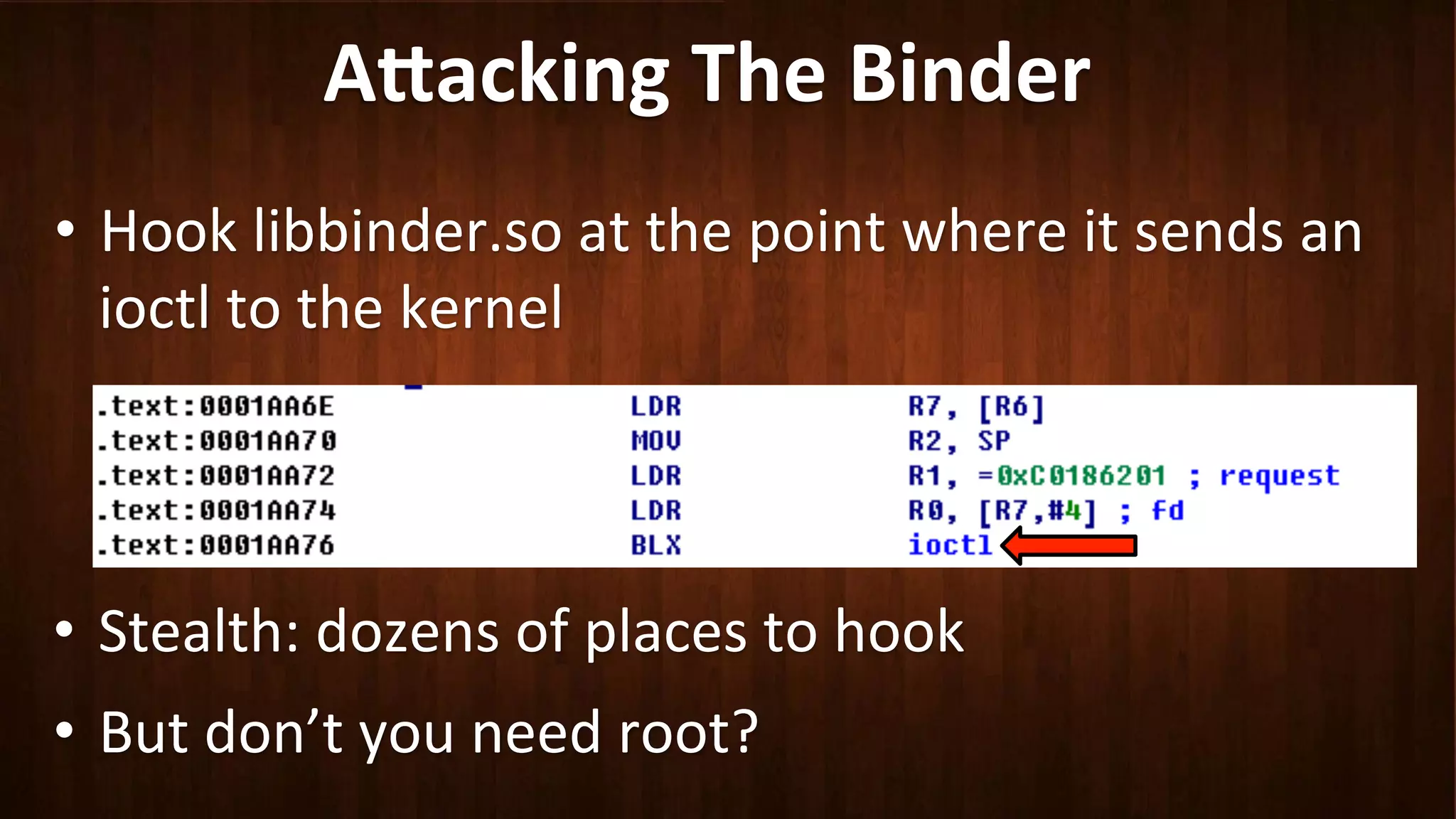
This document discusses Android application security and how a malicious attacker could intercept and manipulate application data and system services by exploiting the Android Binder inter-process communication (IPC) mechanism. It describes how even novice attackers could potentially perform keylogging or manipulate banking applications, while more advanced "ninja" attackers could intercept SMS messages by hooking into the Binder driver. The core issue is that because all application data and system service requests must pass through Binder, an attacker with root access could intercept this traffic covertly without needing to reverse engineer individual apps. Solutions proposed include app developers better securing their own processes and data, while security firms should explore more proactive monitoring techniques.




































![Further
Reading
[1]
White
paper:
“Man
in
the
Binder”,
Artenstein
and
Revivo
[2]
“On
the
Reconstruc?on
of
Android
Malware
Behaviors”,
Fatori,
Tam
et
al
[3]
“Binderwall:
Monitoring
and
Filtering
Android
Interprocess
Communica?on”,
Hausner](https://image.slidesharecdn.com/mitbdroidcon15-150618122042-lva1-app6892/75/Man-in-the-Binder-Michael-Shalyt-Idan-Revivo-CheckPoint-63-2048.jpg)