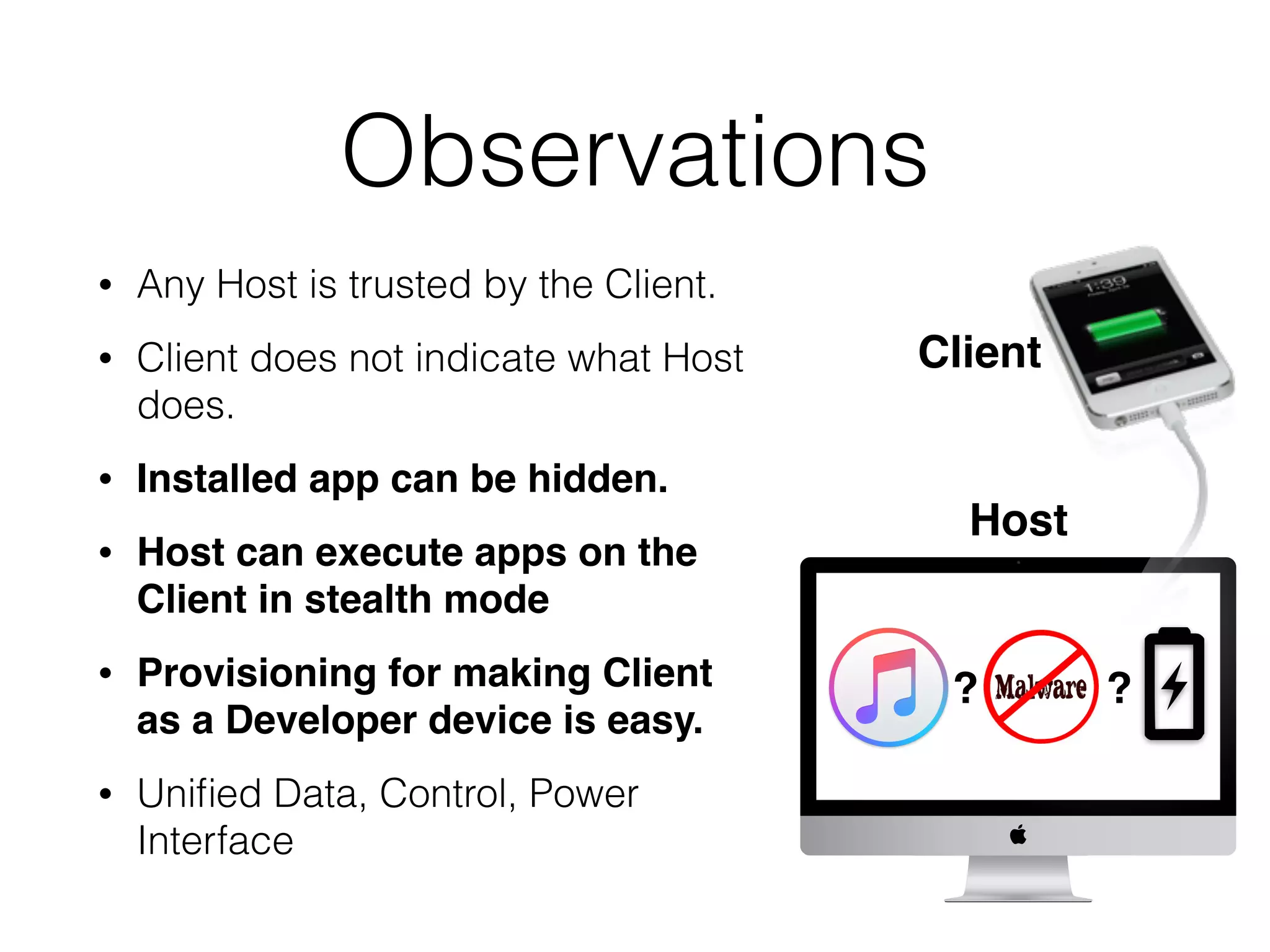
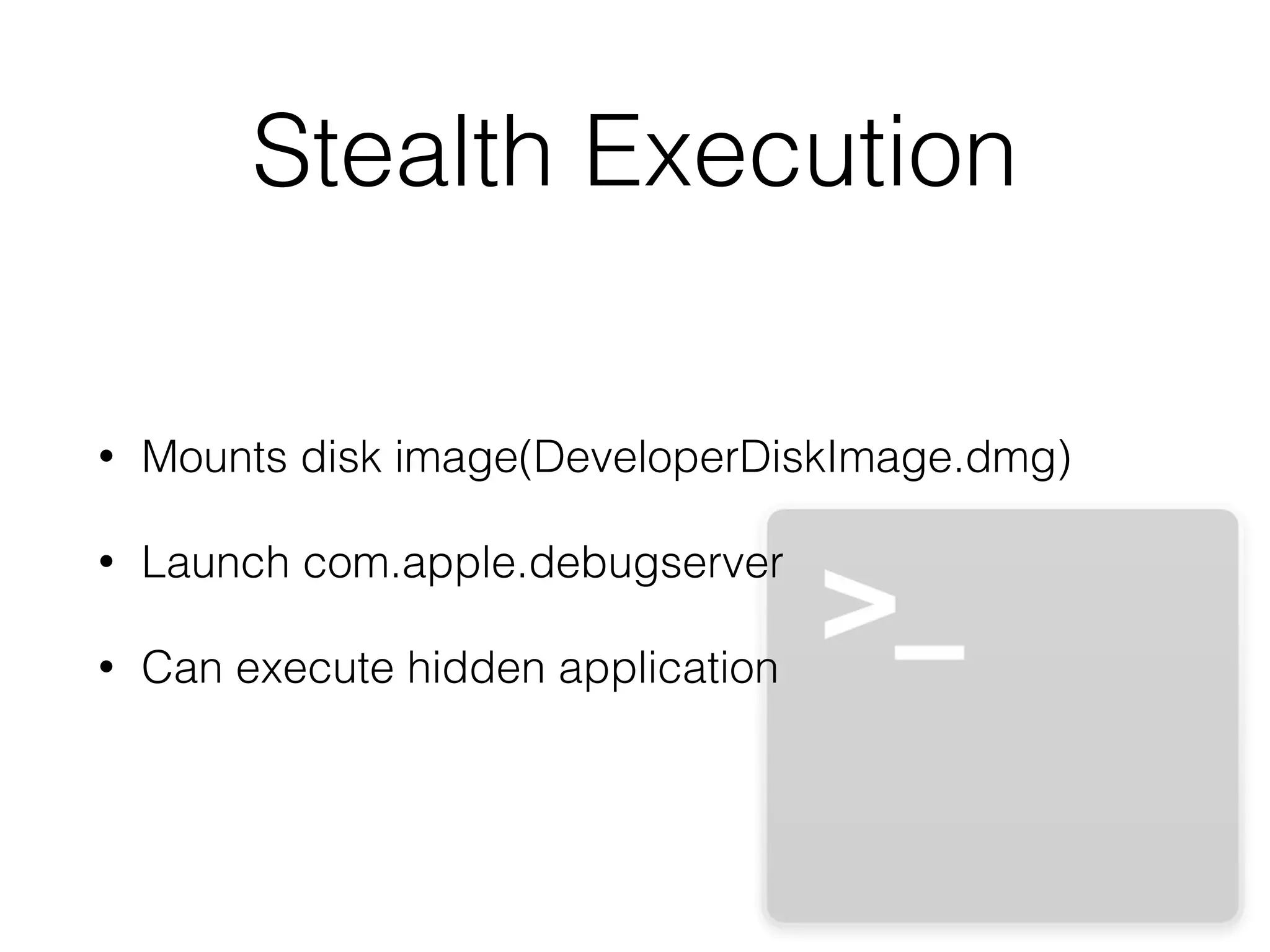
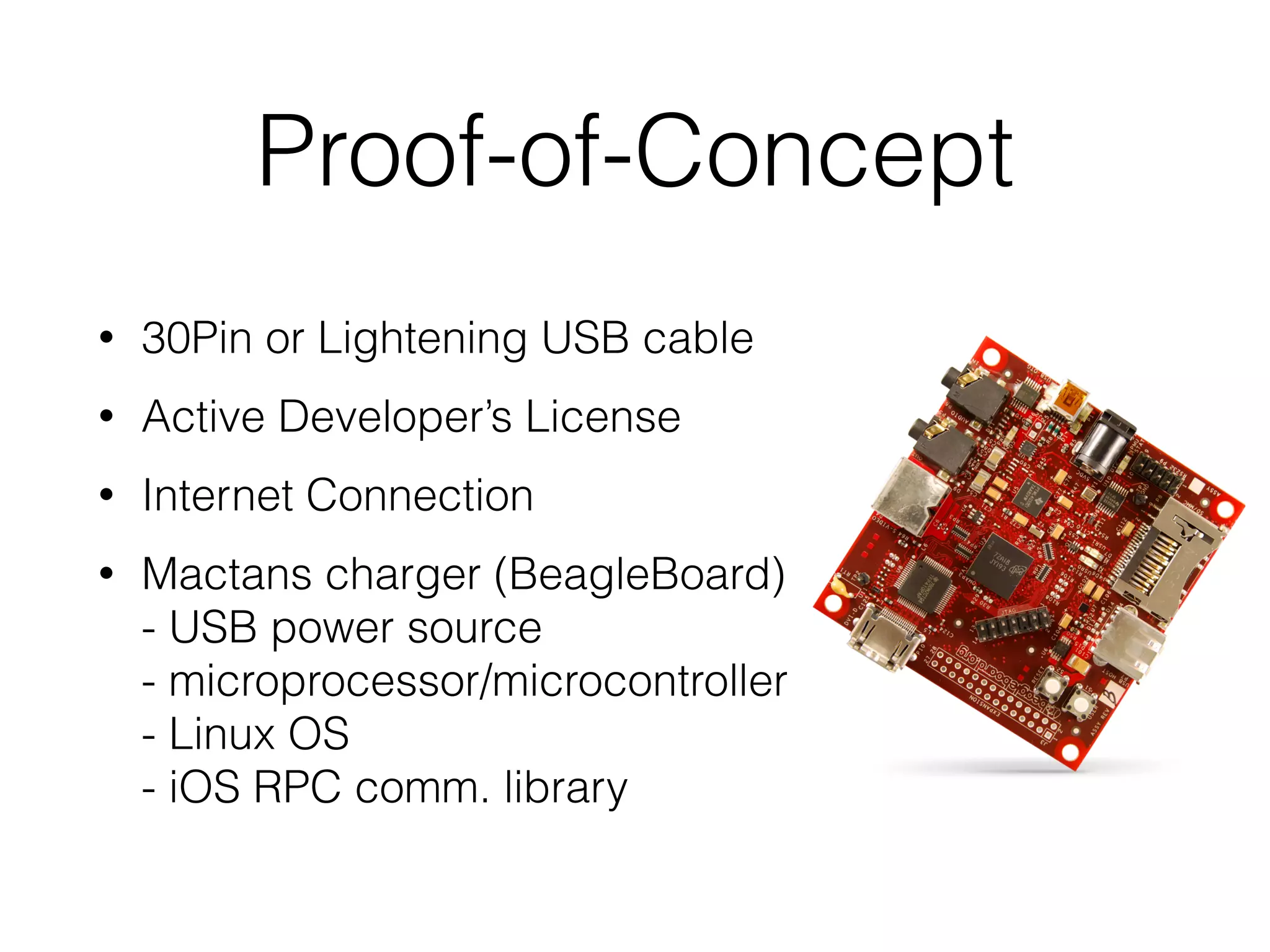
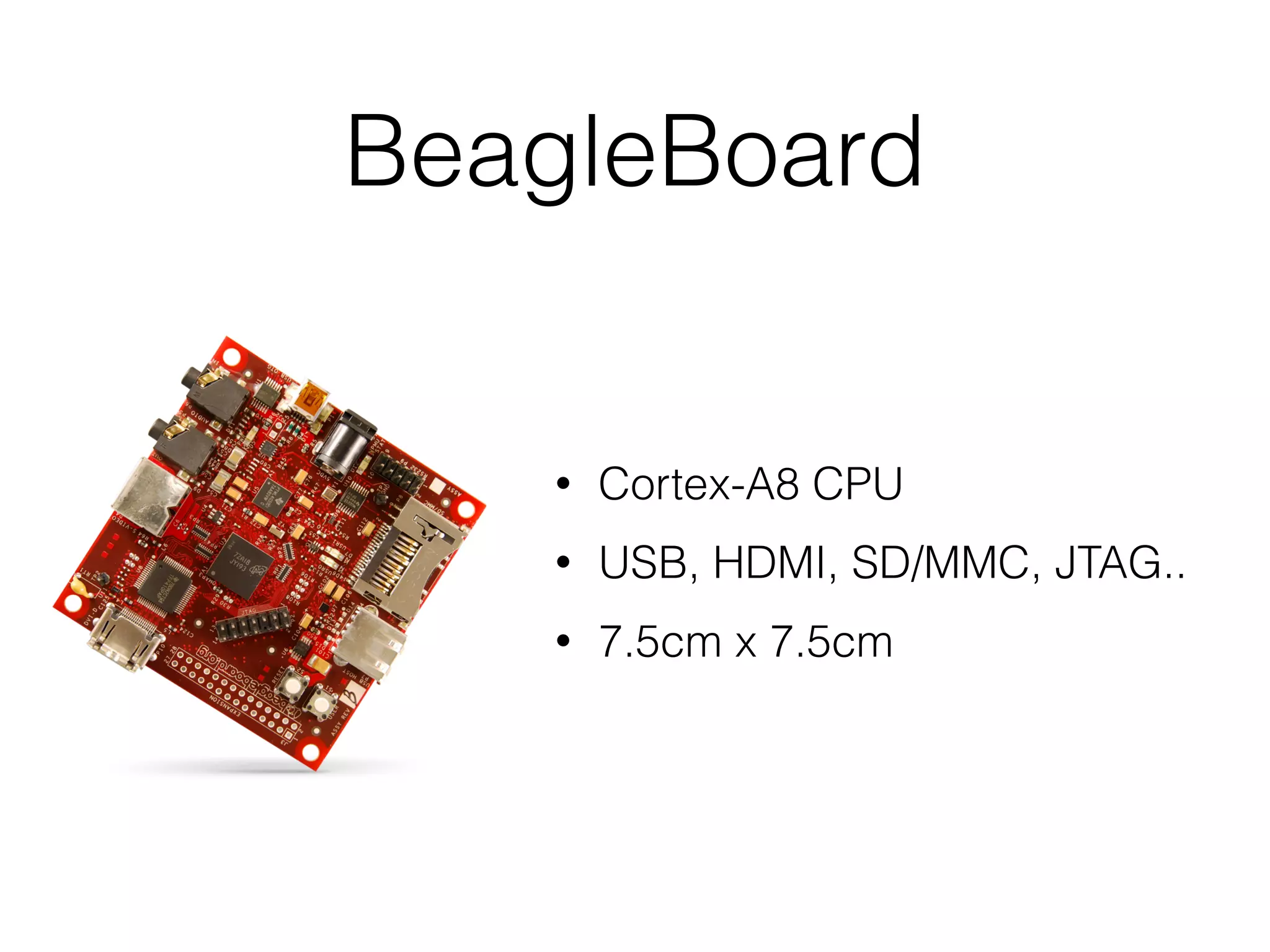
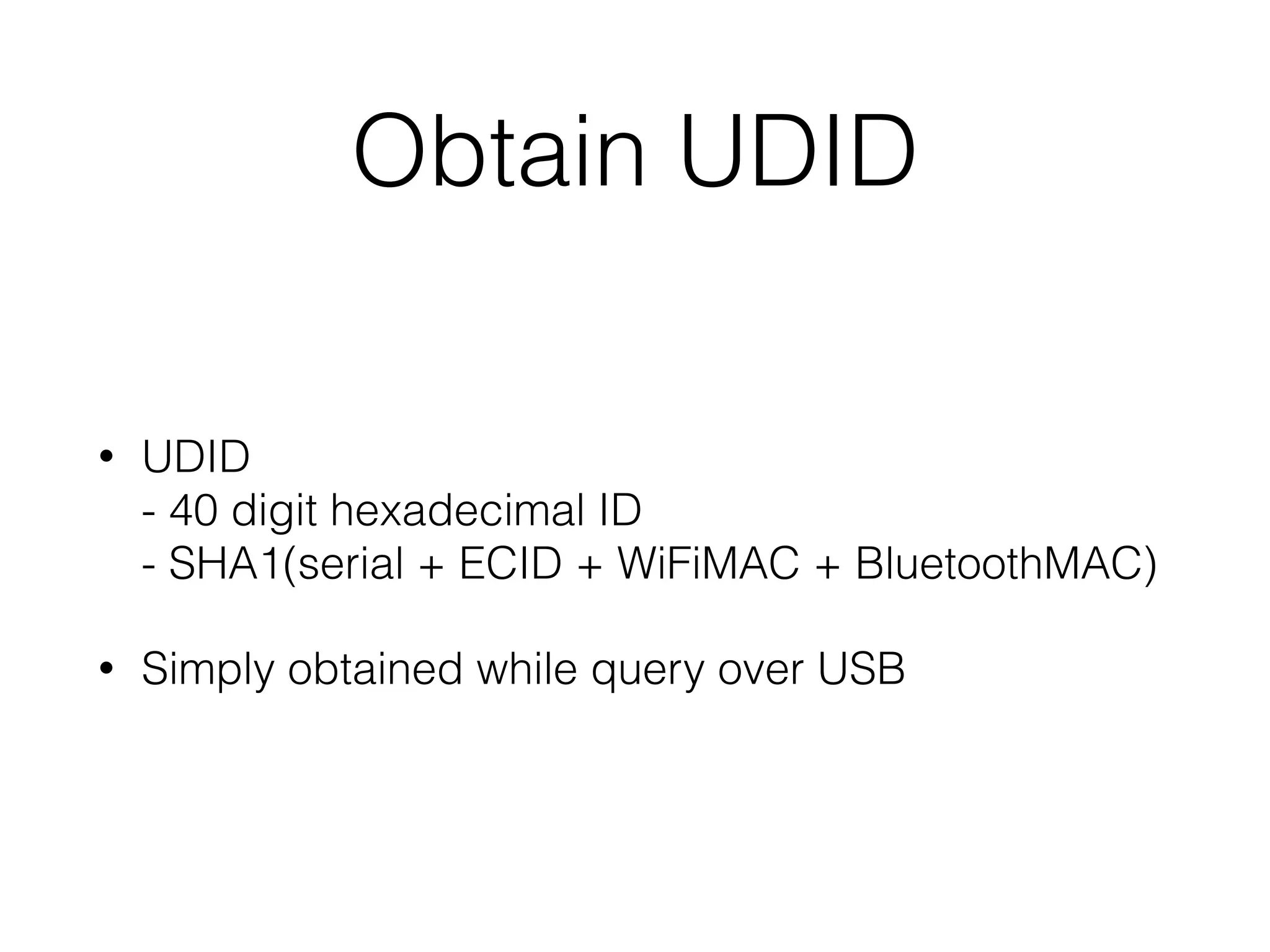
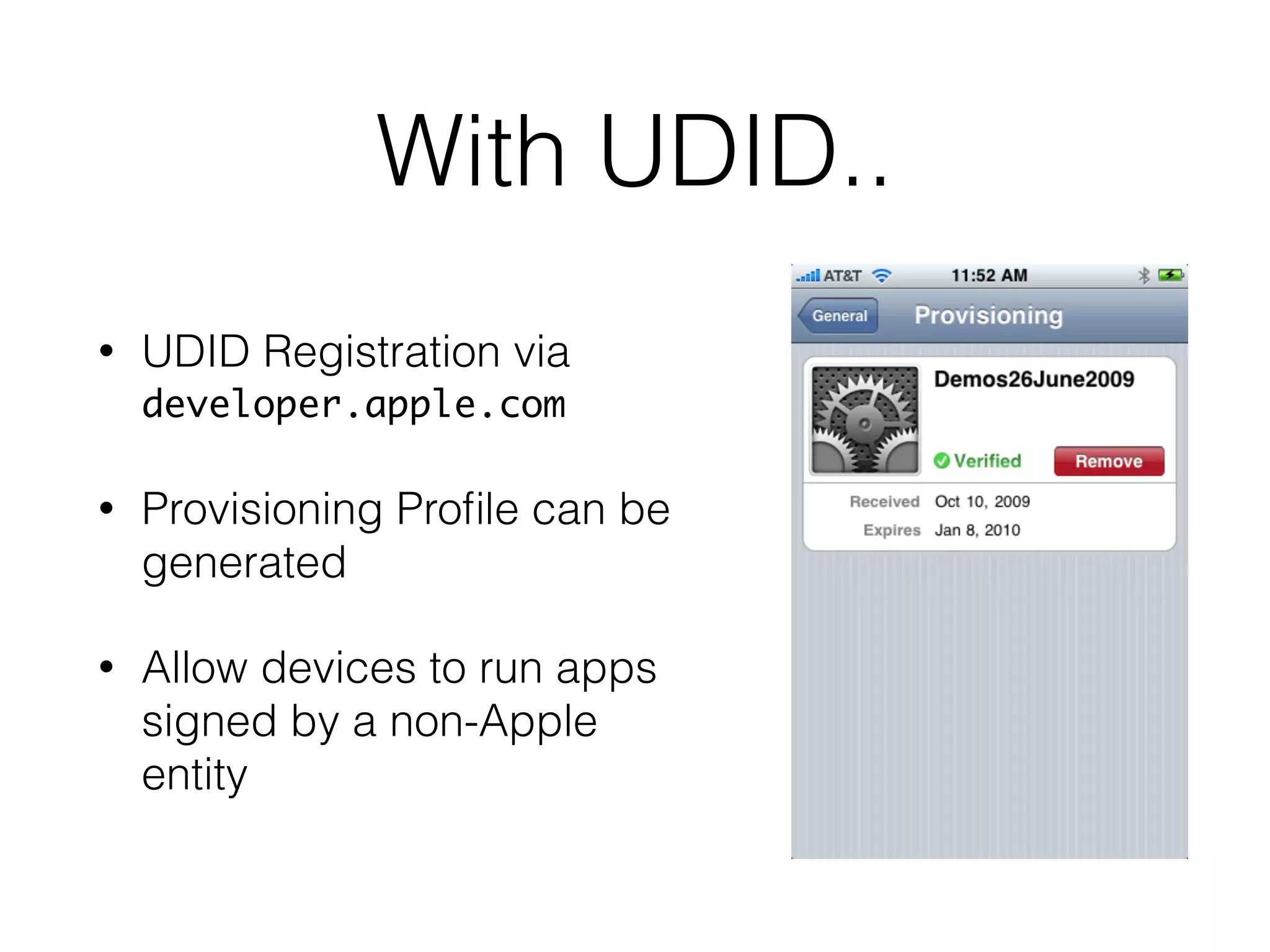
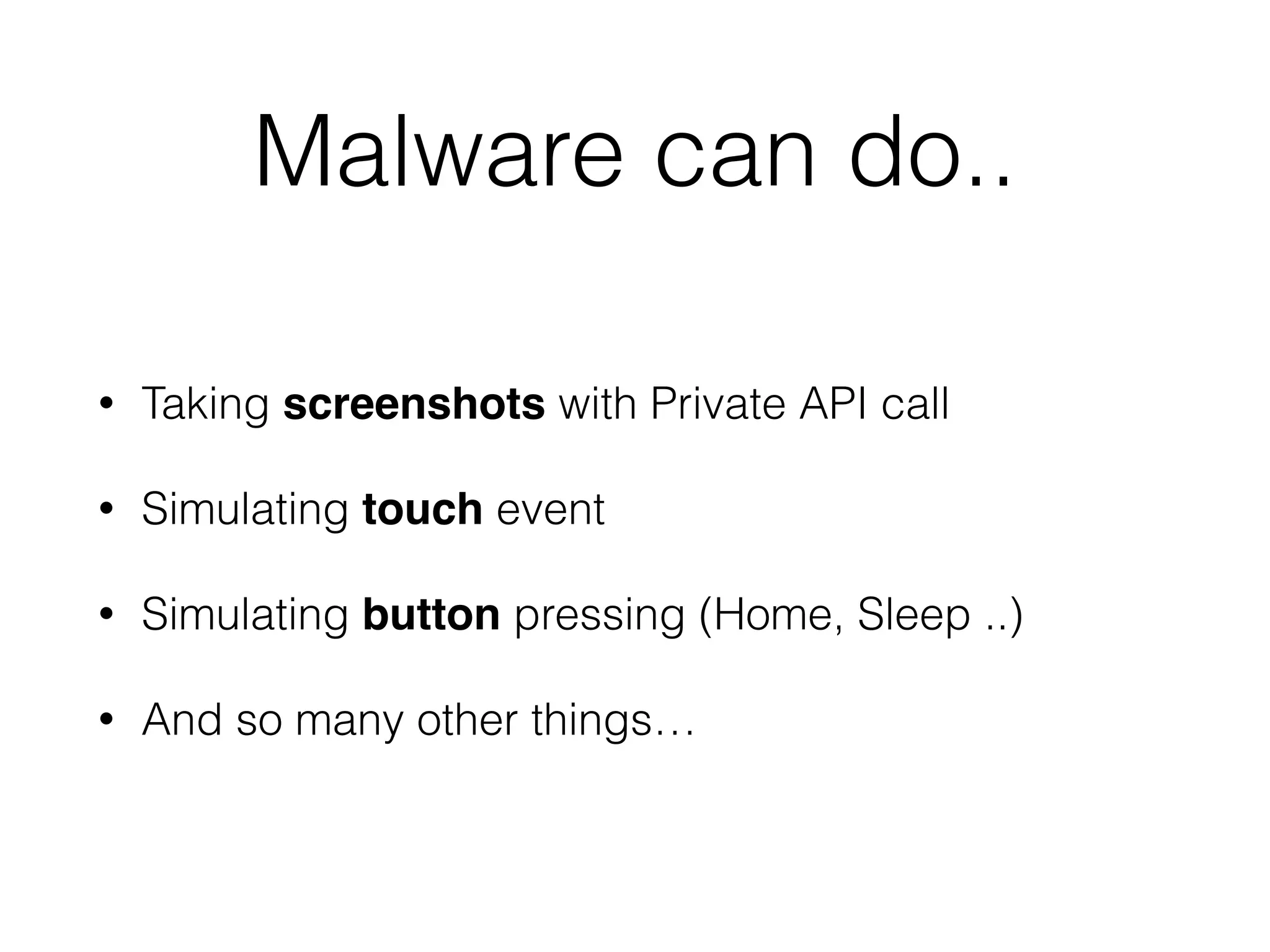
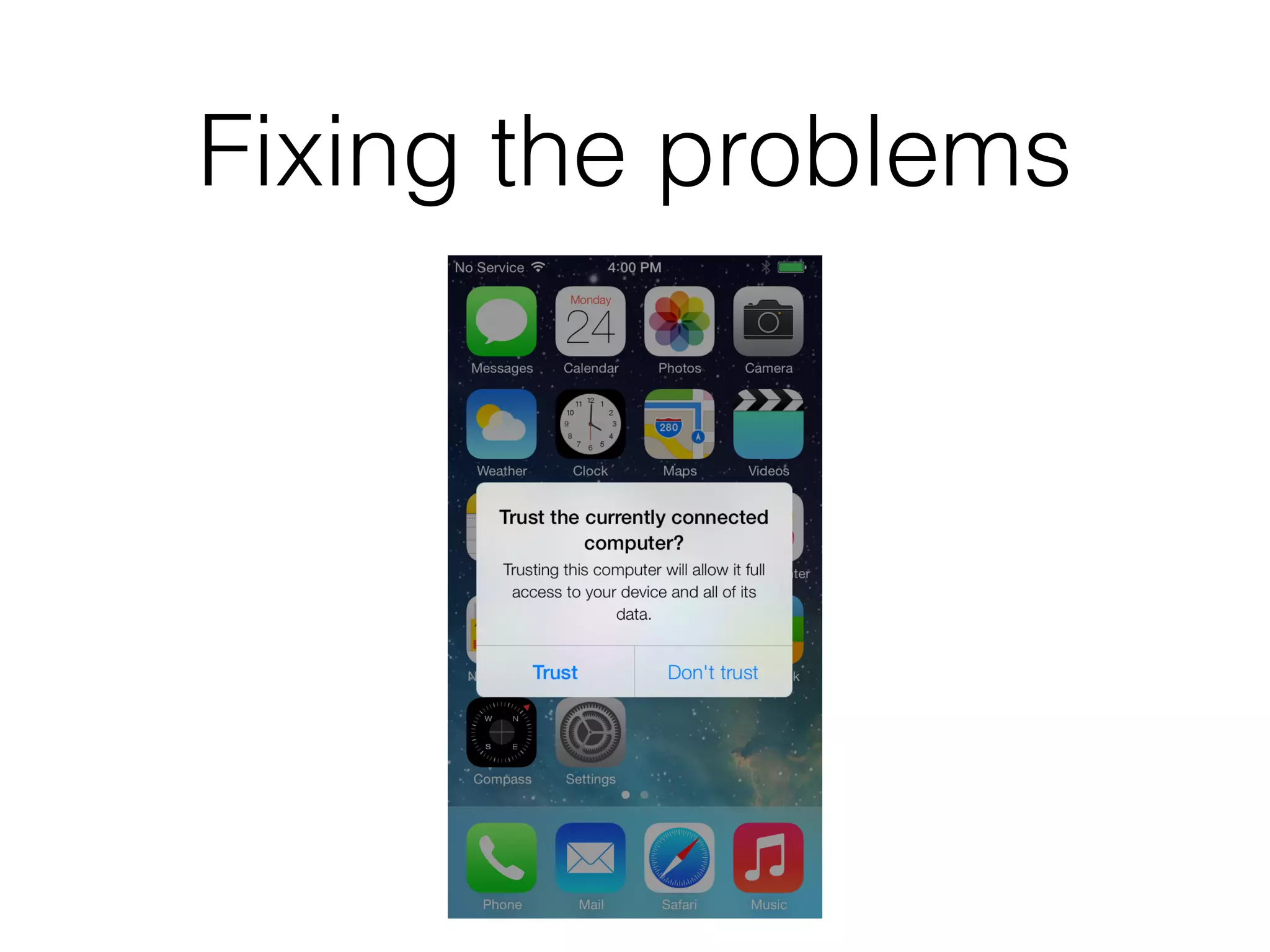
Mactans is a proof-of-concept malicious charger that can inject malware into iOS devices via their charging port. It works by first obtaining the device's UDID to register it and generate a provisioning profile, allowing installation of apps signed by a non-Apple entity. The charger then replaces a legitimate app with a hidden, repackaged version containing malware. When launched, the malware executes before the original app. This attack highlights issues with iOS trusting any host device and the ease of provisioning profiles to install third-party apps without user interaction. Apple has since patched the vulnerabilities in iOS 7, but similar attacks may still target public charging stations or modified environments to infect devices stealthily.