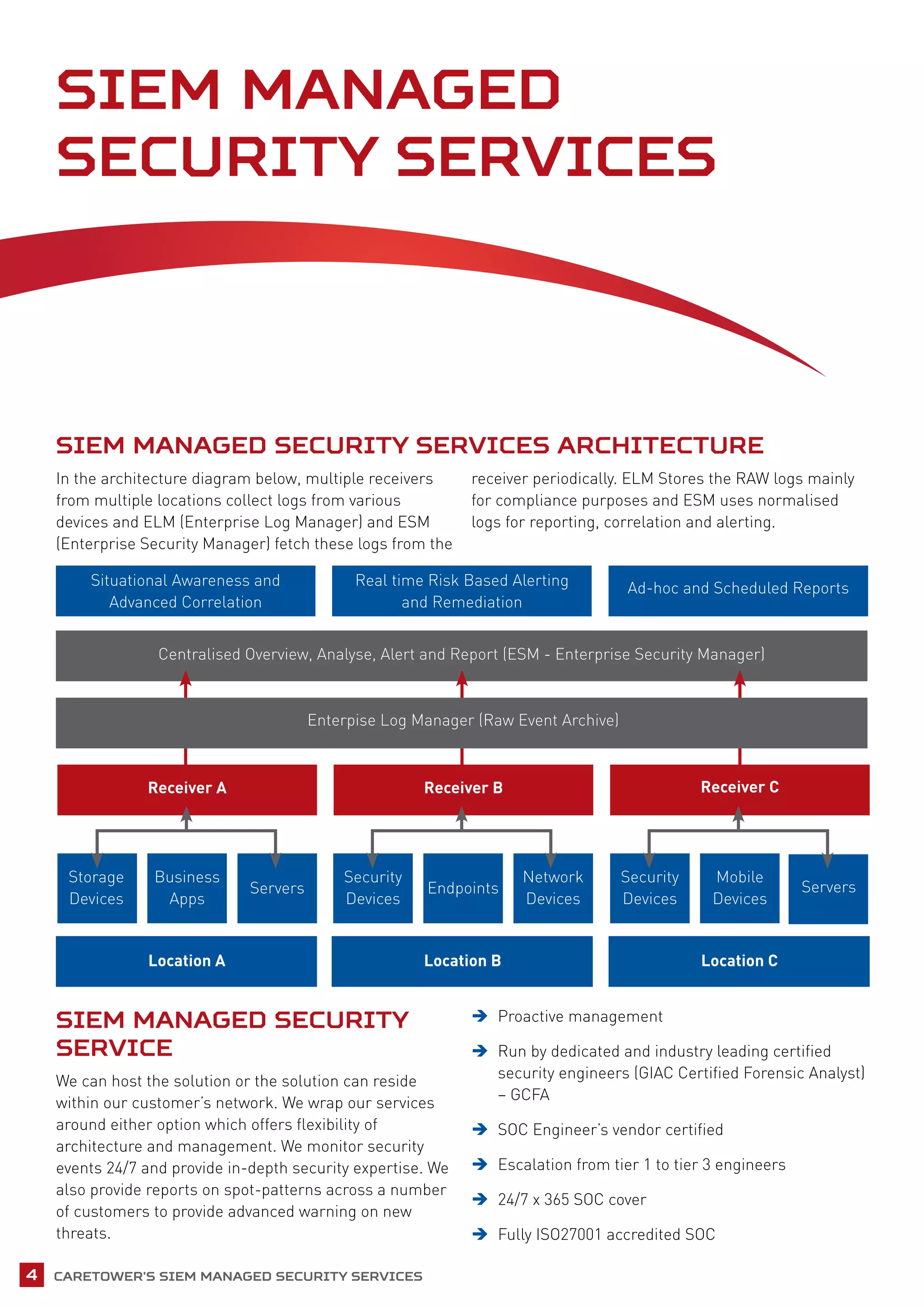
Caretower provides a managed security information and event management (SIEM) service to help organizations address challenges around security monitoring, compliance, threat detection, and incident response. Their solution collects and analyzes logs from multiple sources to correlate events, generate reports, and enable 24/7 monitoring by security experts. Key benefits include improved security posture, simplified compliance, flexible dashboards and reporting, and speed of implementation.