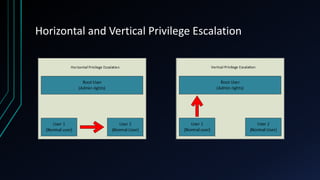
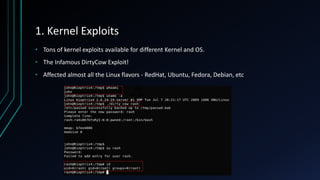
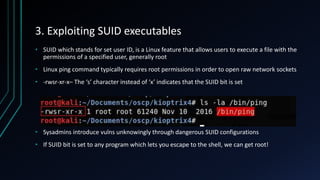
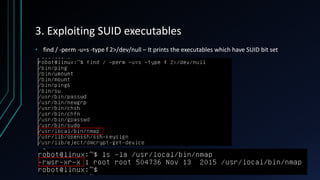
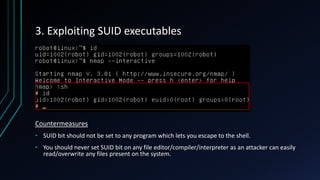
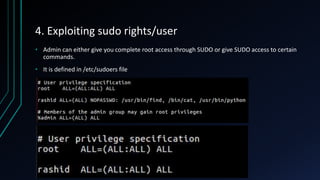
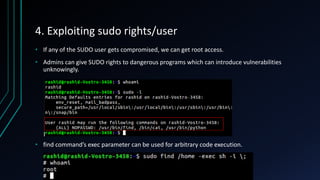
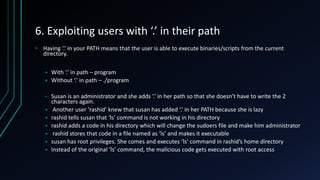
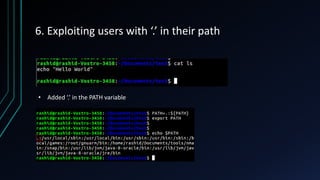
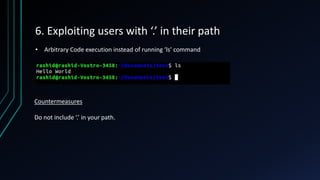
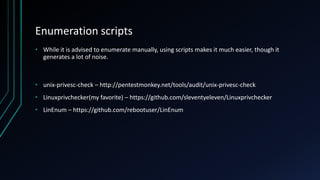
The document discusses Linux privilege escalation, explaining its definition, reasons, and methods, including kernel exploits, exploiting services, SUID executables, and cron jobs. It emphasizes the importance of maintaining security through patching and proper configuration, as well as countermeasures to prevent unauthorized escalation of privileges. The text also mentions tools for enumeration and introduces Security-Enhanced Linux (SELinux) for enhanced security management.