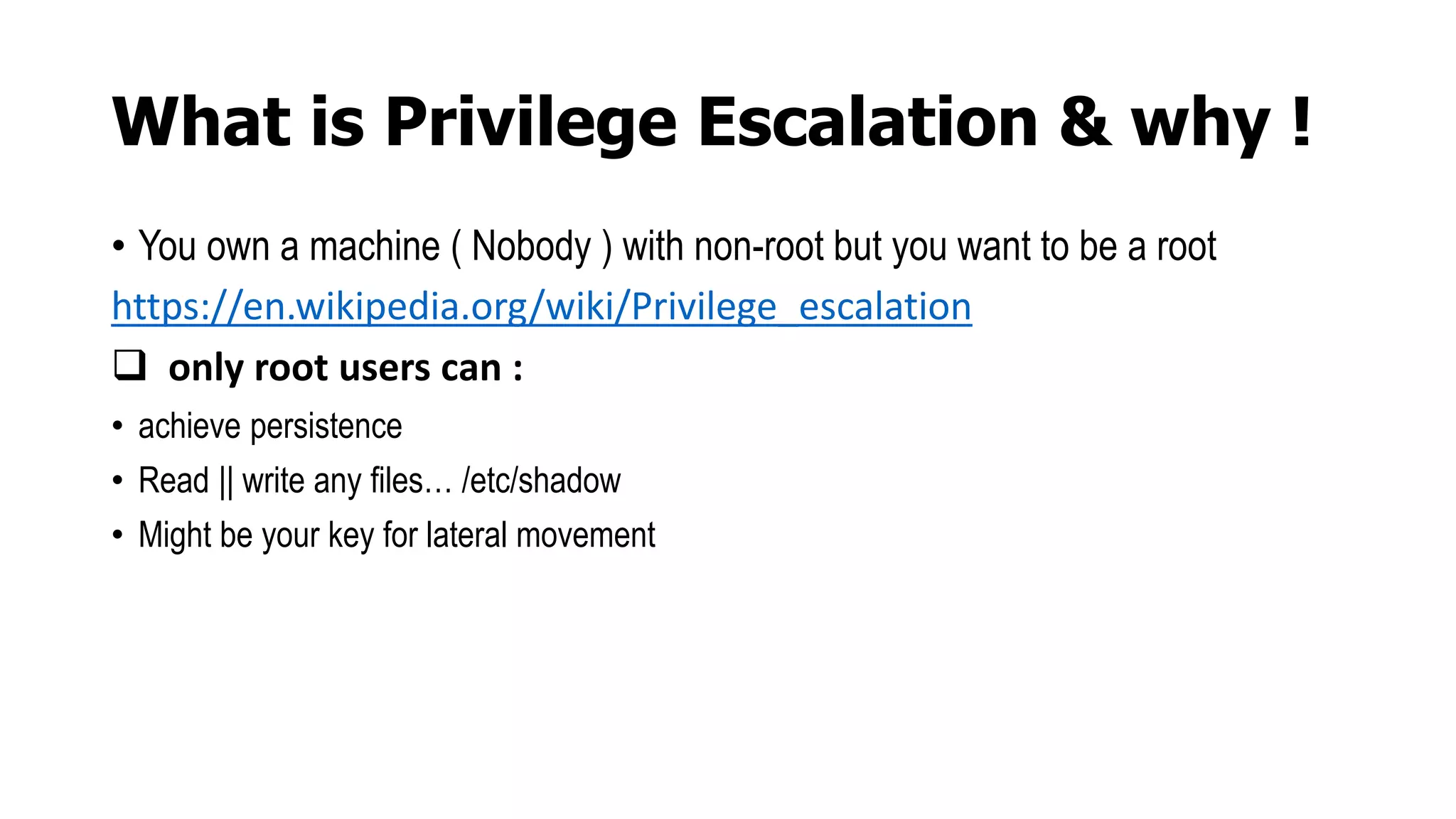
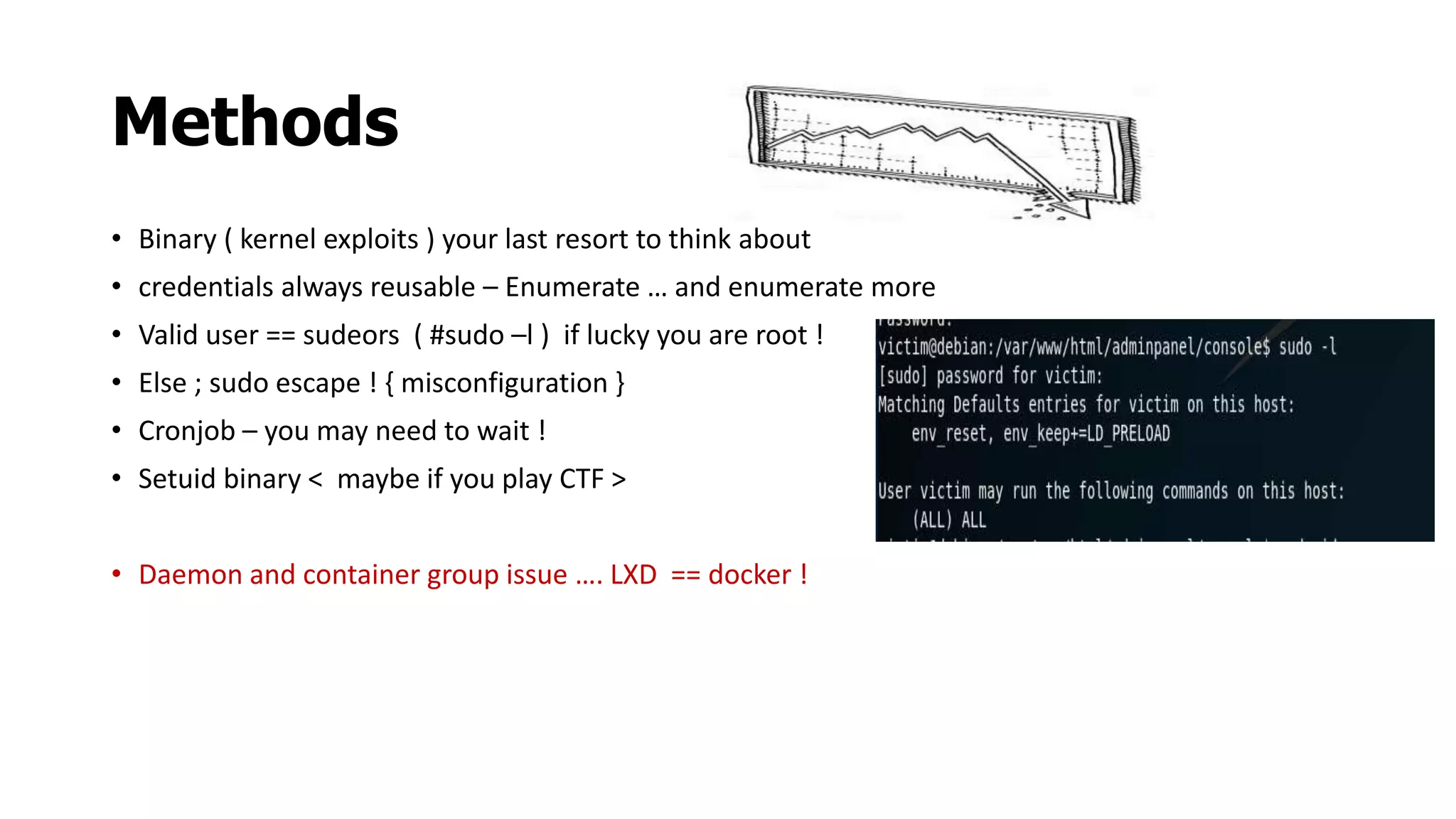
This document discusses privilege escalation techniques on Linux systems. It begins by explaining that privilege escalation involves gaining root access on a machine where you initially only have non-root access. It then outlines several common methods for escalating privileges including exploiting binaries, using valid credentials, sudo misconfigurations, cron jobs, SUID executables, and breaking out of containers. The document provides links to additional resources and recommends first reconning the system to determine which escalation methods may apply.
![Recon when you think !
Depends on how you have reached here !
- System information [ uname -a , env , cat /proc/version , /etc/issue ]
- what is running
[ ifconfing -a , netstat -antup , lsof -i , ps , daemons ……… packages ( application ) – ps aux | grep root]](https://image.slidesharecdn.com/linxprivxenumeration-usersandprivileges-sudomisconfiguration-groupanddockerdaemonprivileges-181113112205/75/Linx-privx-privileges-sudo-misconfiguration-group-and-docker-daemon-privileges-5-2048.jpg)

![Terminal – tty [ multiple jobs to do ]
• Error are not displayed
• You cant switch between users …. If you got any
http://www.dest-unreach.org/socat/doc/socat.html
its just boring to connect everytime , no up arrow key:D](https://image.slidesharecdn.com/linxprivxenumeration-usersandprivileges-sudomisconfiguration-groupanddockerdaemonprivileges-181113112205/75/Linx-privx-privileges-sudo-misconfiguration-group-and-docker-daemon-privileges-7-2048.jpg)