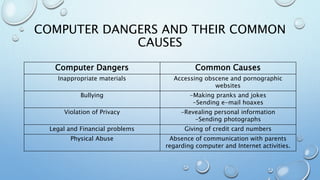
This document provides information about computer ethics and safety. It discusses intellectual property rights, copyright, and software piracy. It also outlines 10 commandments for computer ethics and lists some common computer dangers and their causes. Students are assigned to create 10 pledges for computer and internet safety.