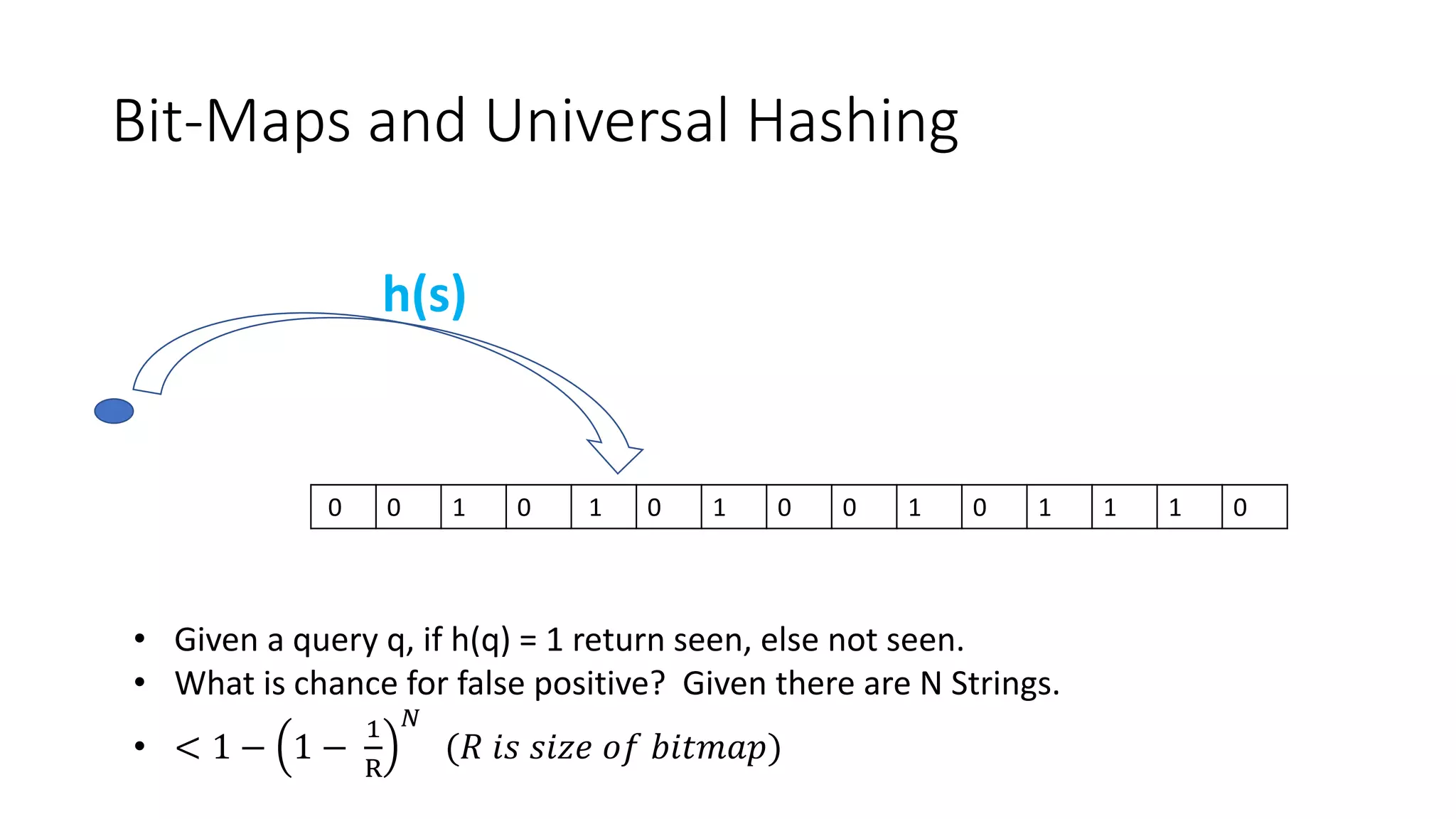
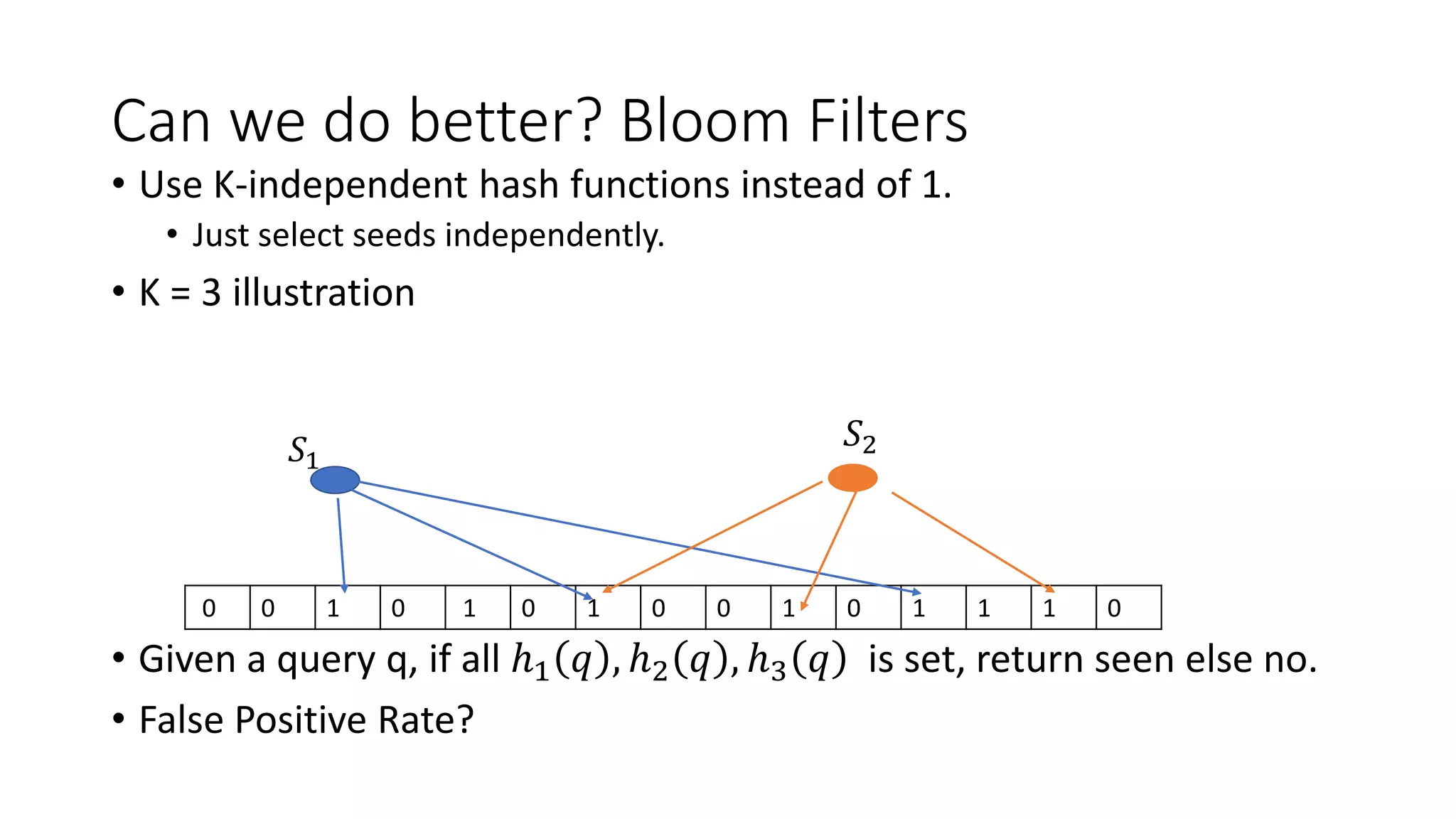
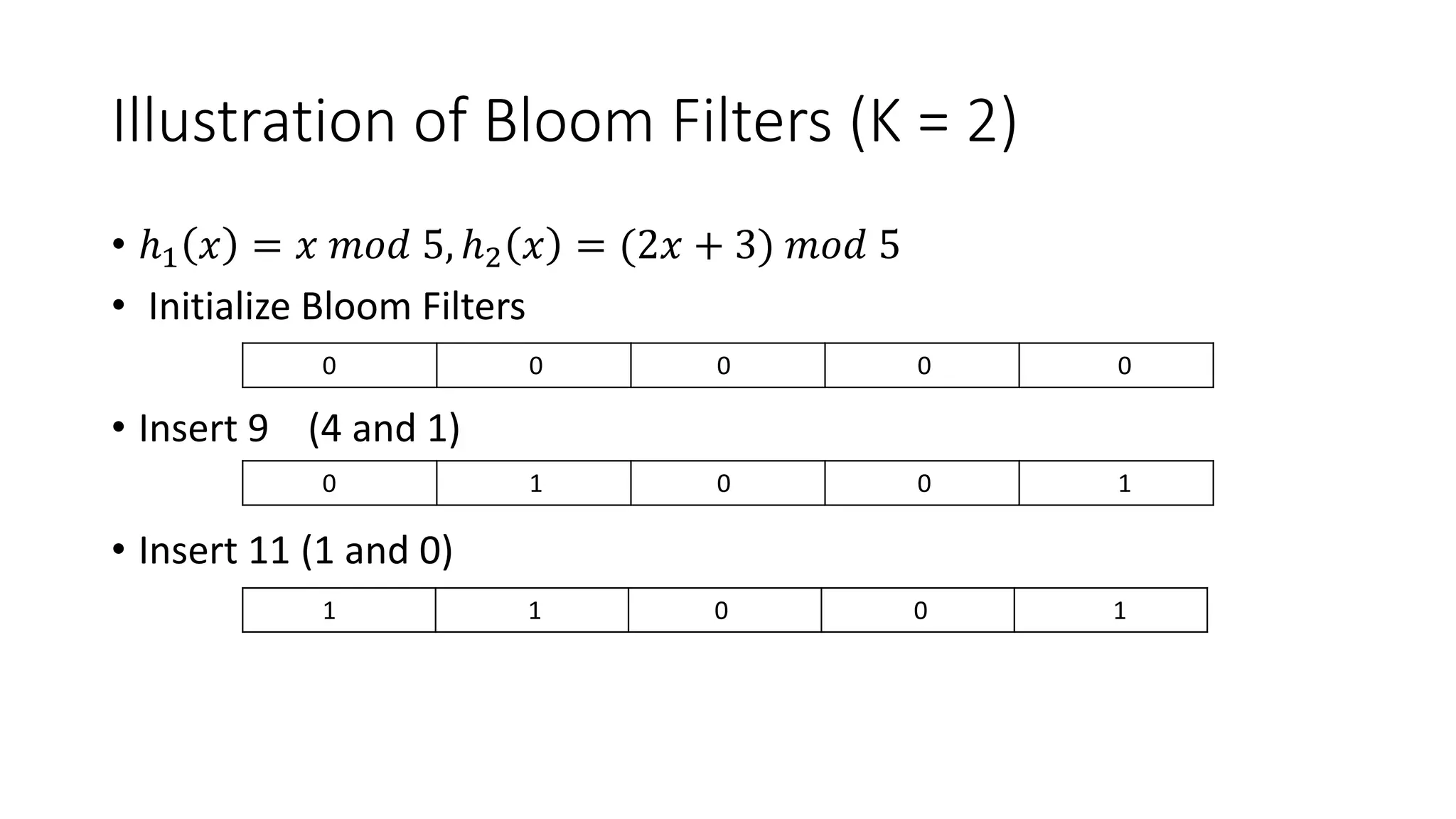
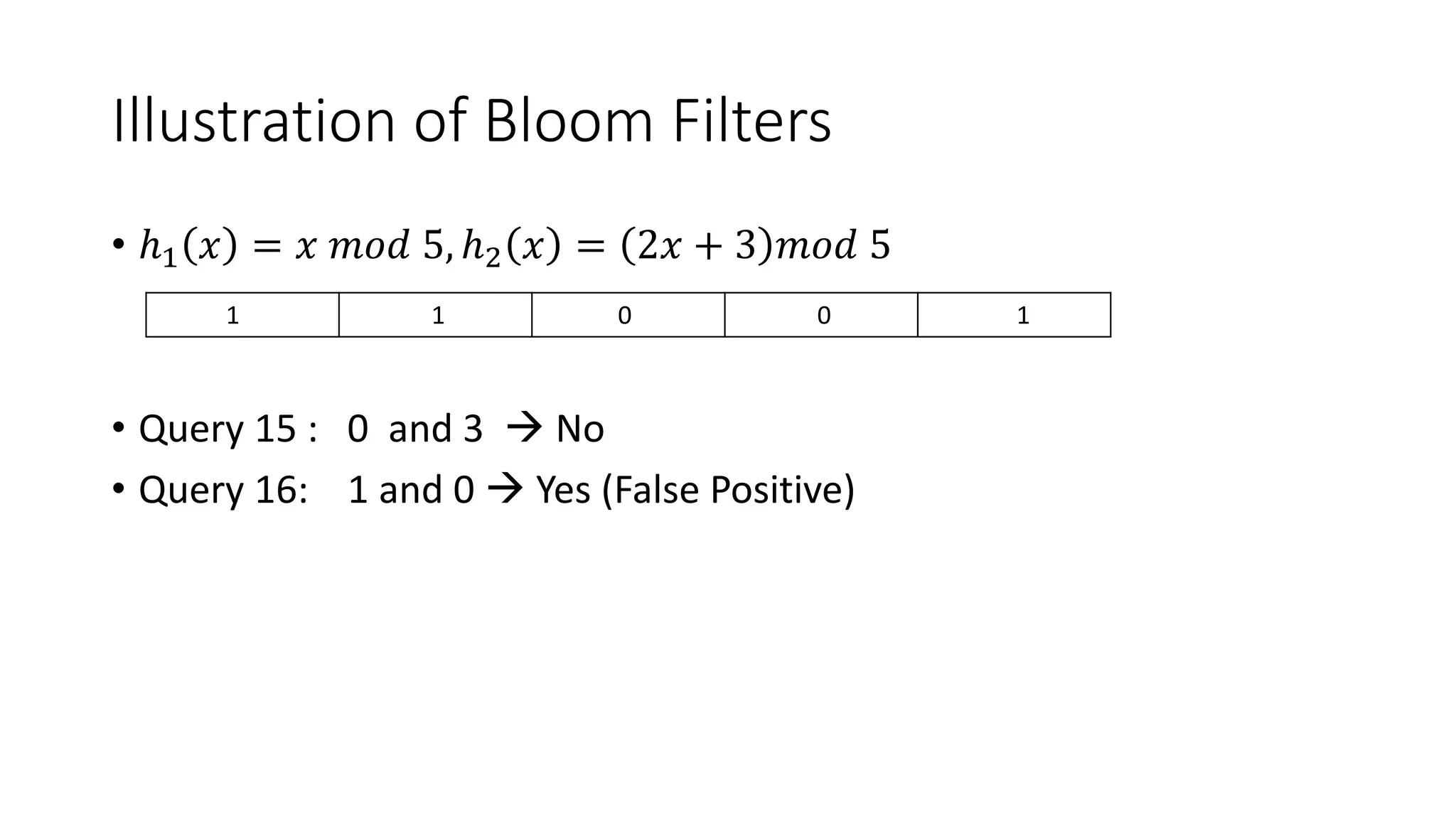
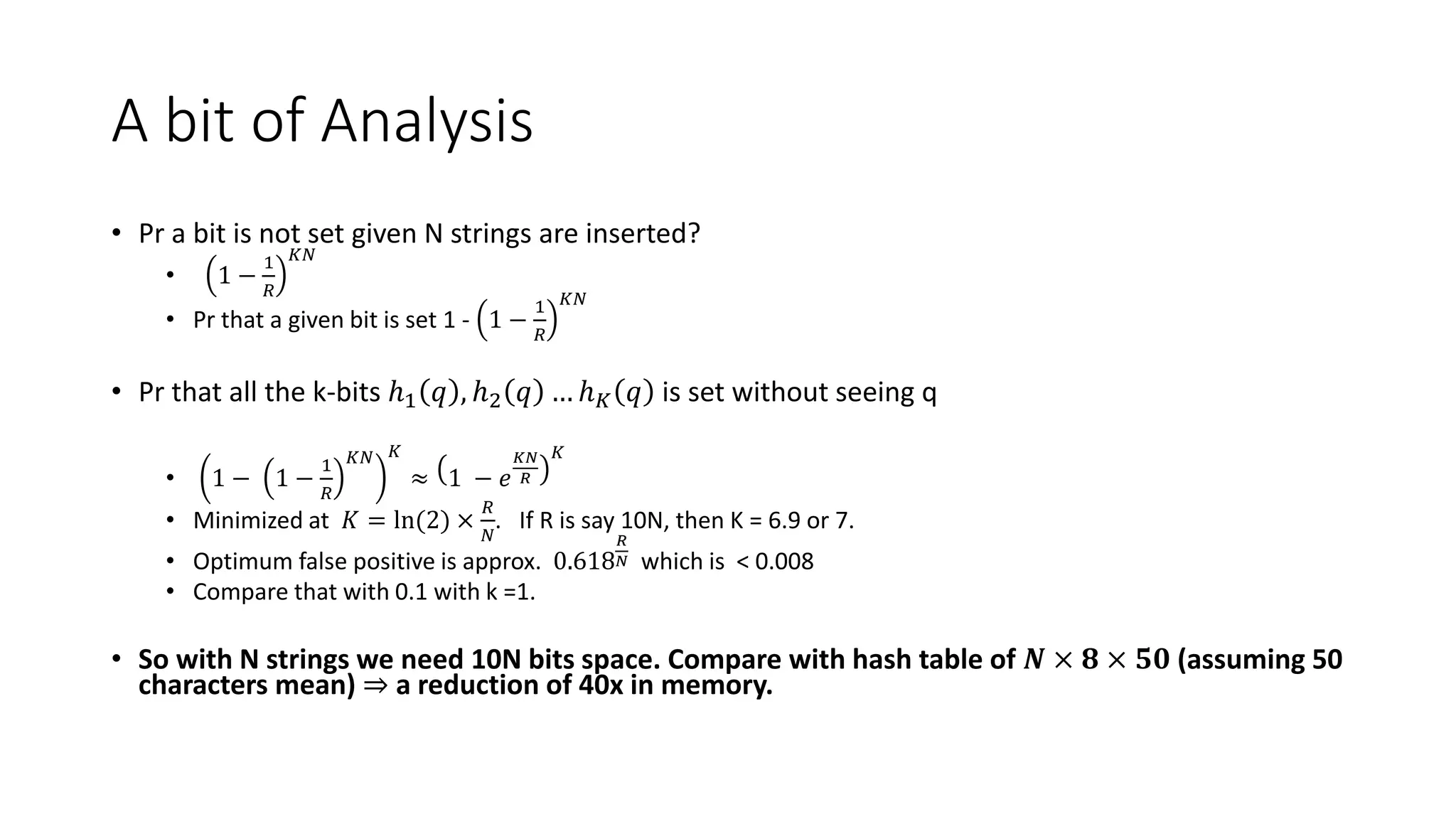
Bloom filters are a space-efficient probabilistic data structure for representing a set in order to support membership queries. A Bloom filter represents a set as a bit array and uses hash functions to map elements to bit positions, setting the bits. To query if an element is in the set, its bit positions are checked. False positives are possible but false negatives are not. Bloom filters enable representing a set using less space than a regular hash table while still supporting fast membership queries. They find many applications including caching, network routing, and database optimizations.

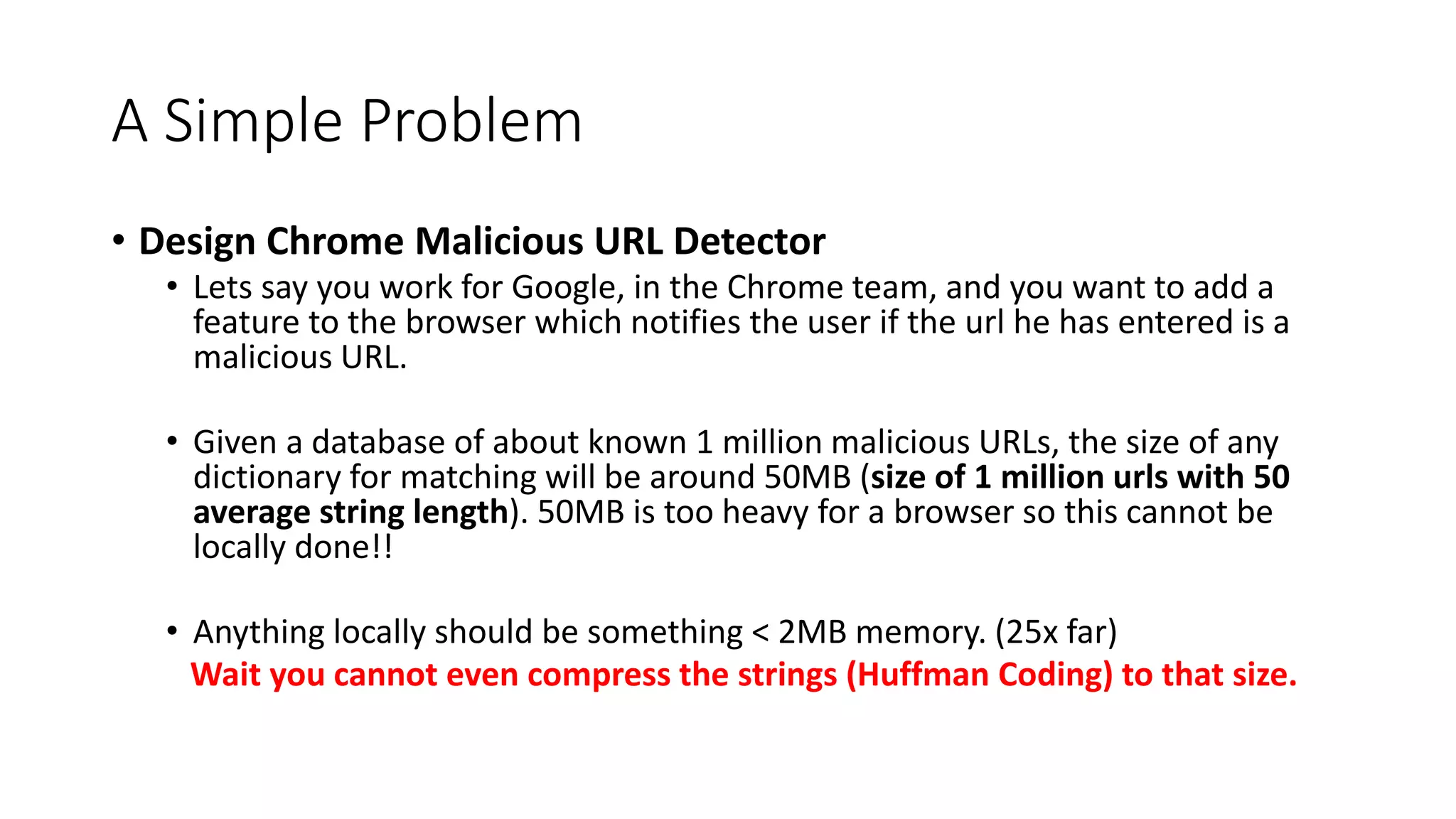
![Universal hashing review
• Goals
• Design ℎ: 𝑜𝑏𝑗𝑒𝑐𝑡𝑠 → [0 − 𝑅] such that
• If 𝑂1 ≠ 𝑂2 𝑡ℎ𝑒𝑛 ℎ 𝑂1 ≠ ℎ 𝑂2 with high probability.
• h is cheap to compute and requires almost no memory.
• Classical Example:
• Randomly generate a and b (seed), choose a prime P >> R.
• ℎ 𝑥 = 𝑎𝑥 + 𝑏 𝑚𝑜𝑑 𝑃 𝑚𝑜𝑑 𝑅 (faster if 𝑅 = 232 why?)
• For strings or other objects, use bitarrays, randomly shuffle bits based on a
some seed then take mod.
• example: See Murmurhash.
• Memory: A seed per hash function!](https://image.slidesharecdn.com/lecture3-221213062653-502ddf78/75/Lecture_3-pptx-3-2048.jpg)