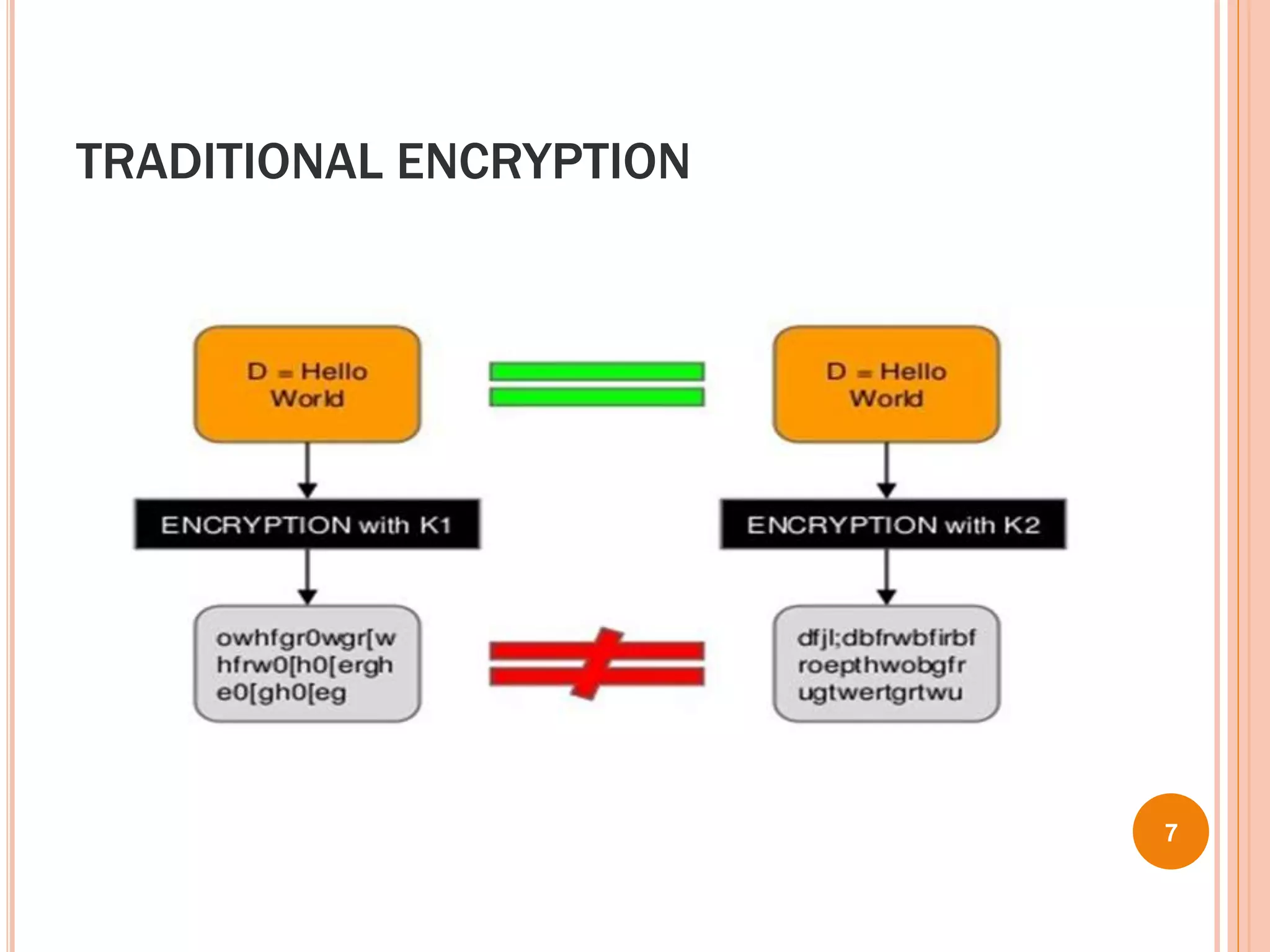
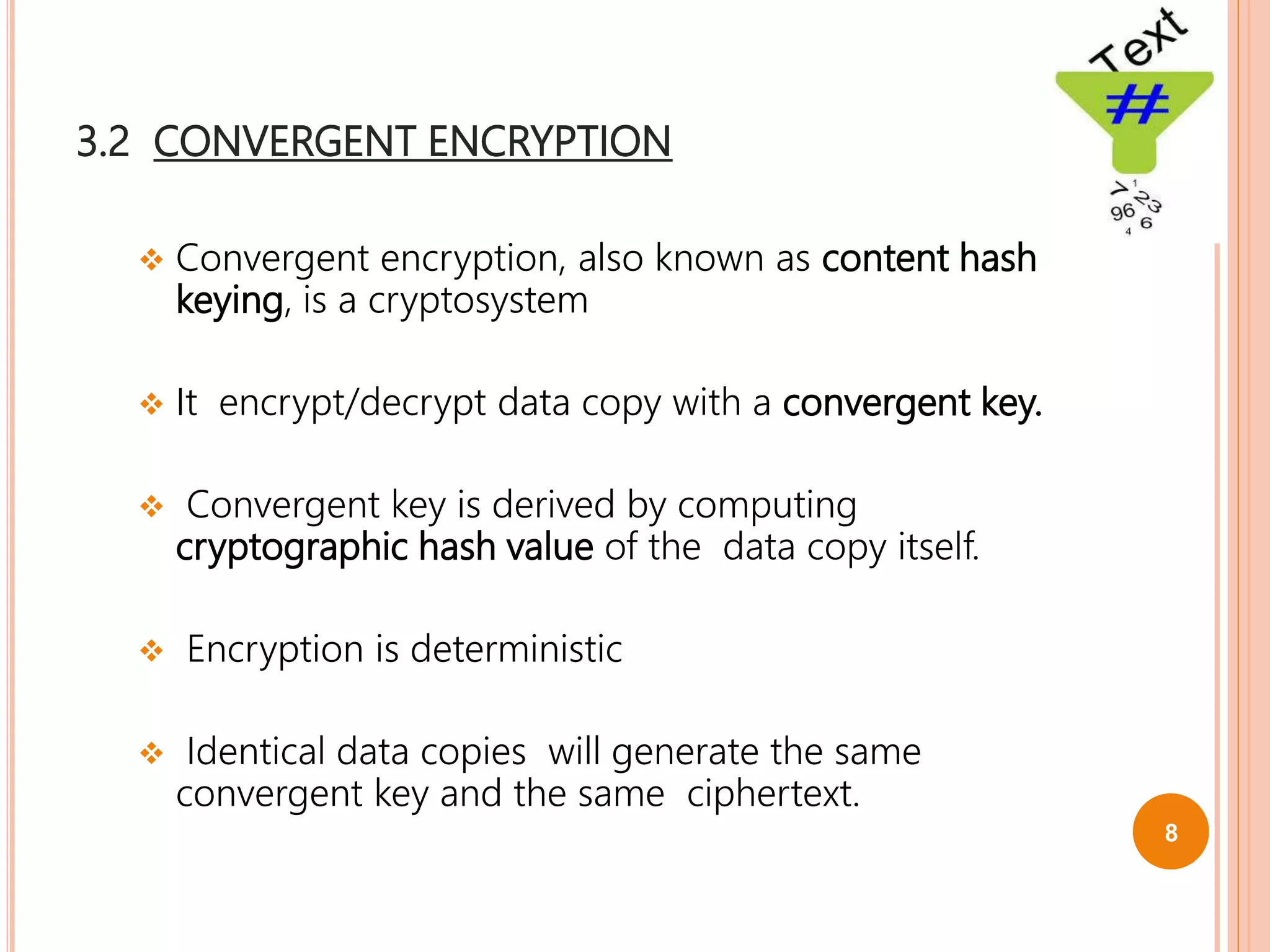
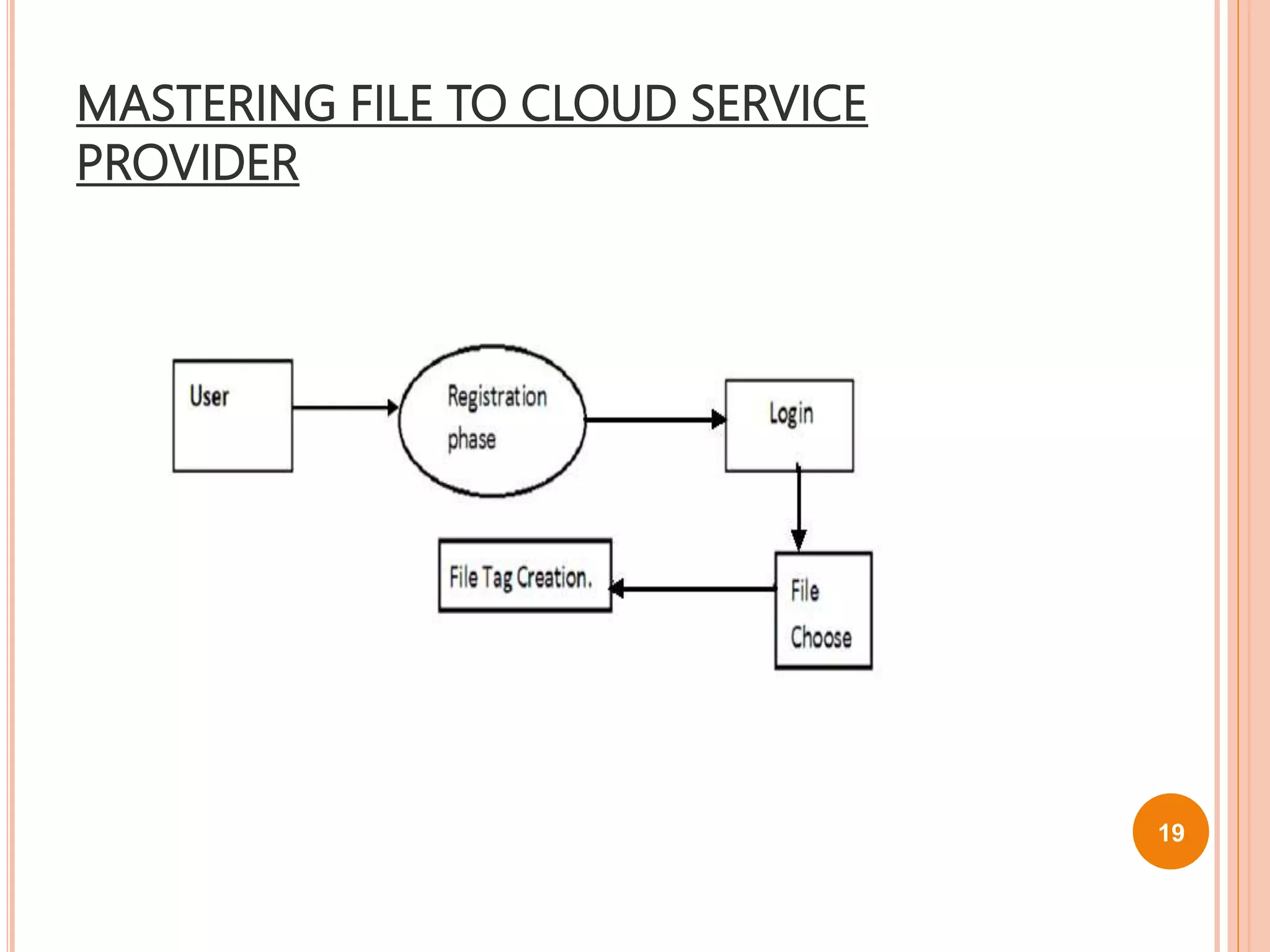
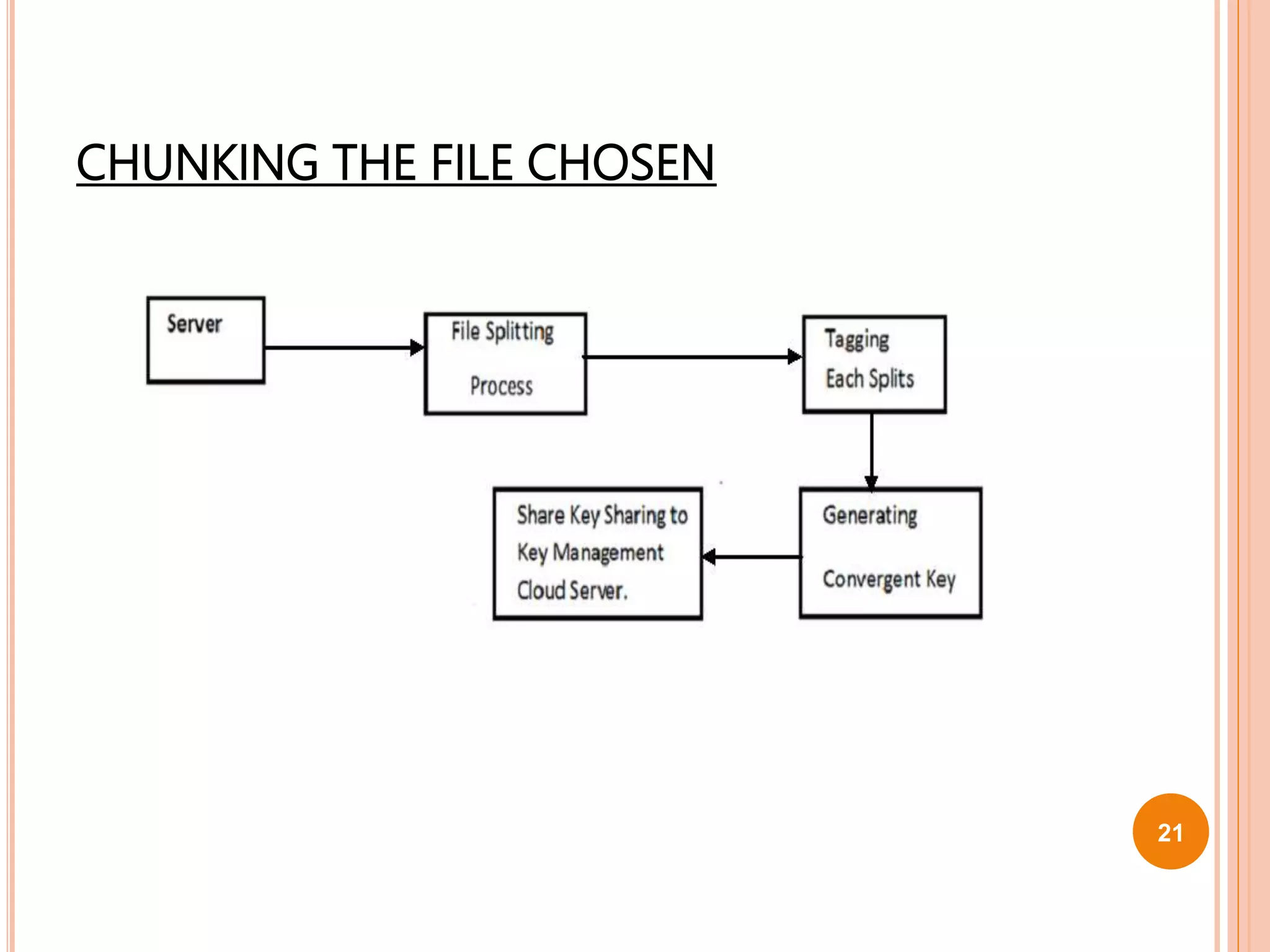
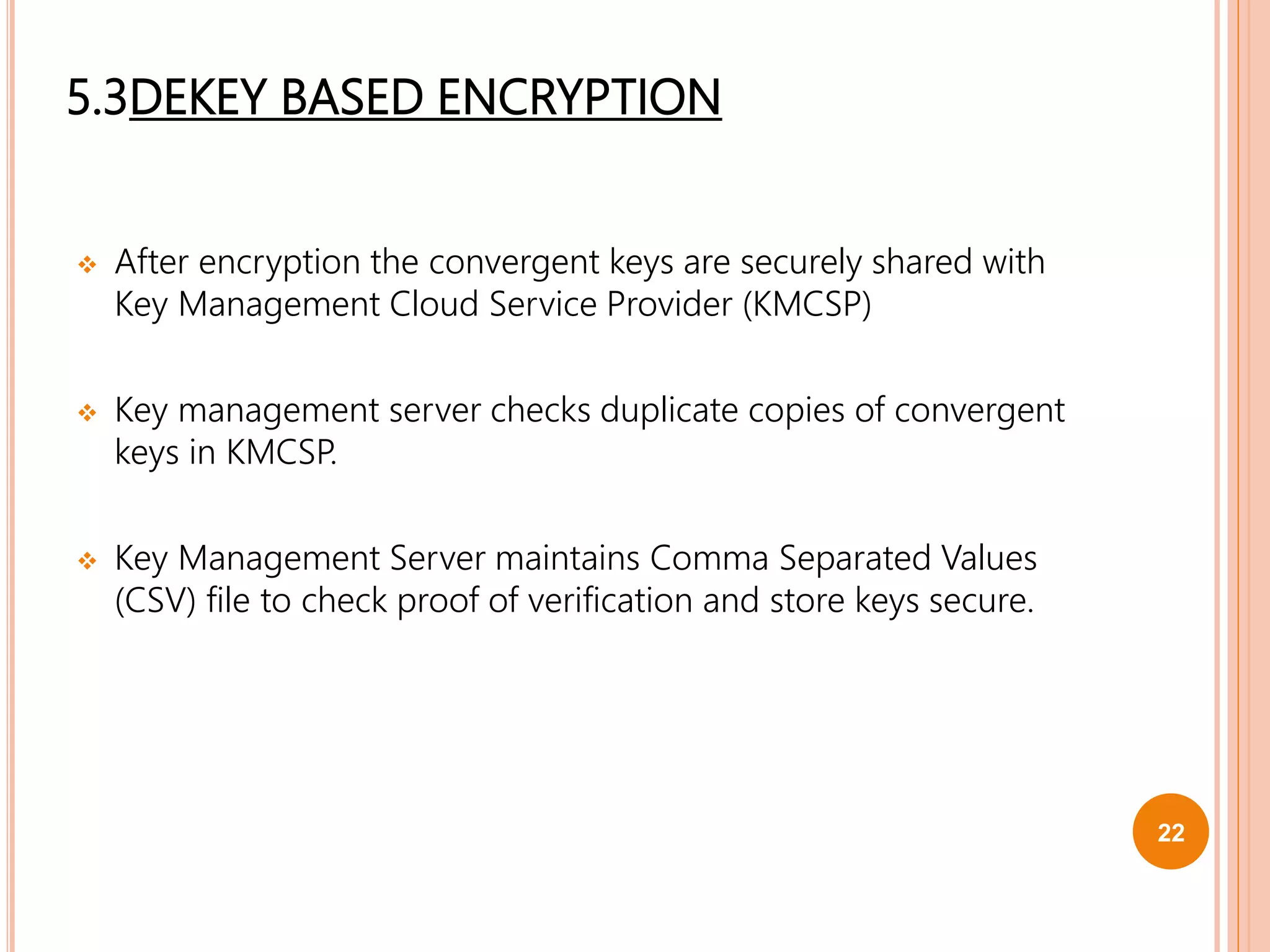
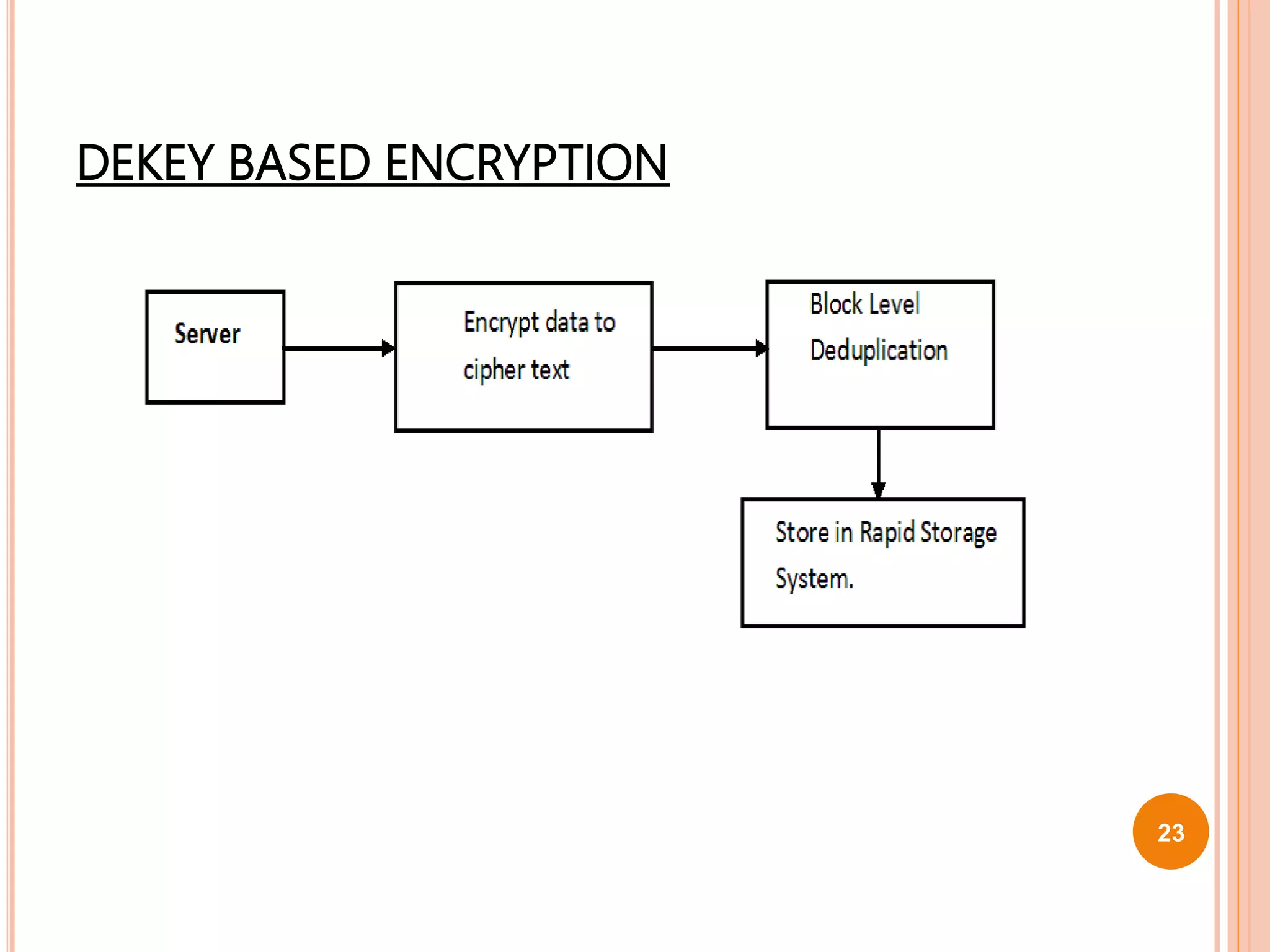
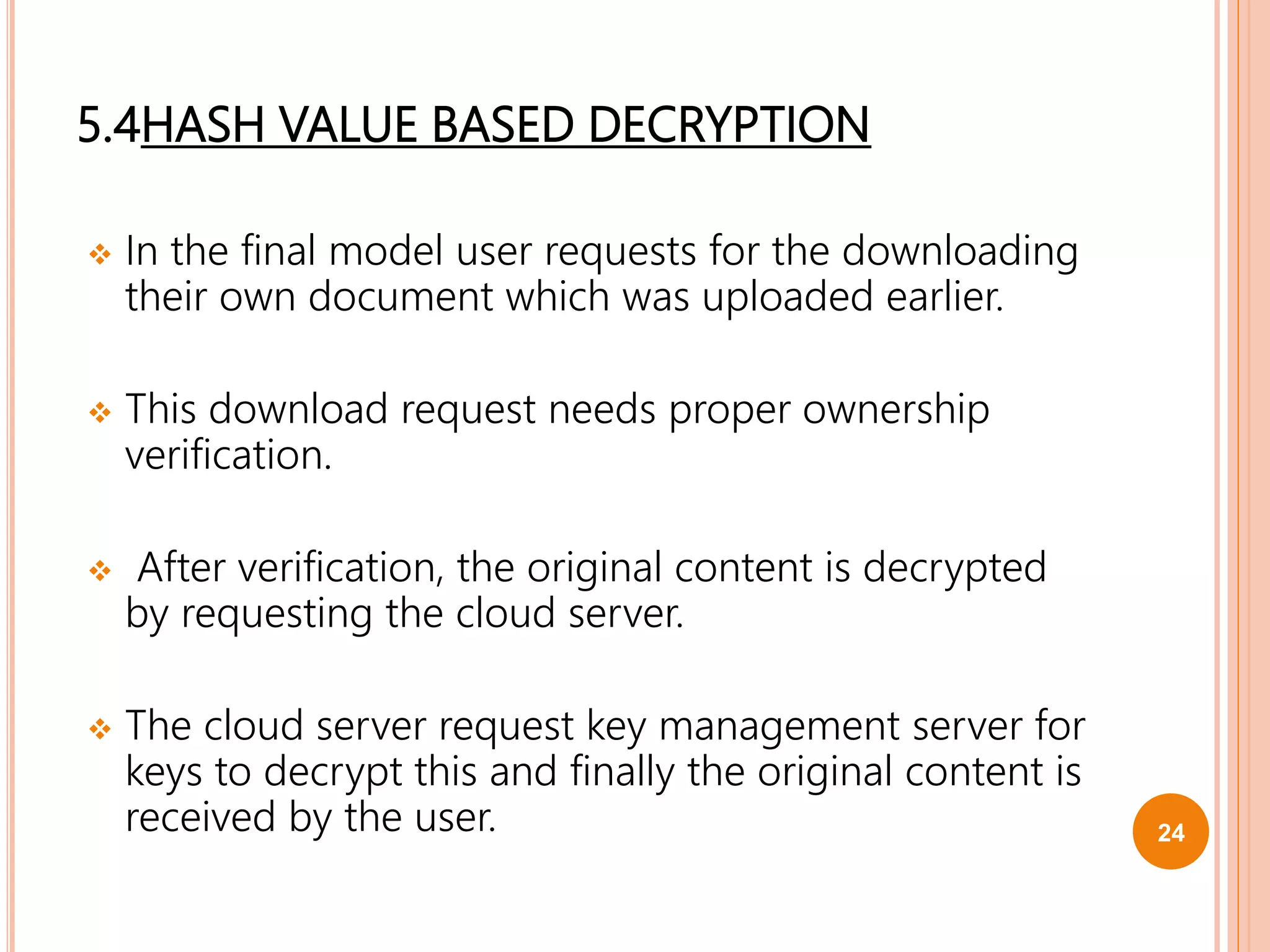
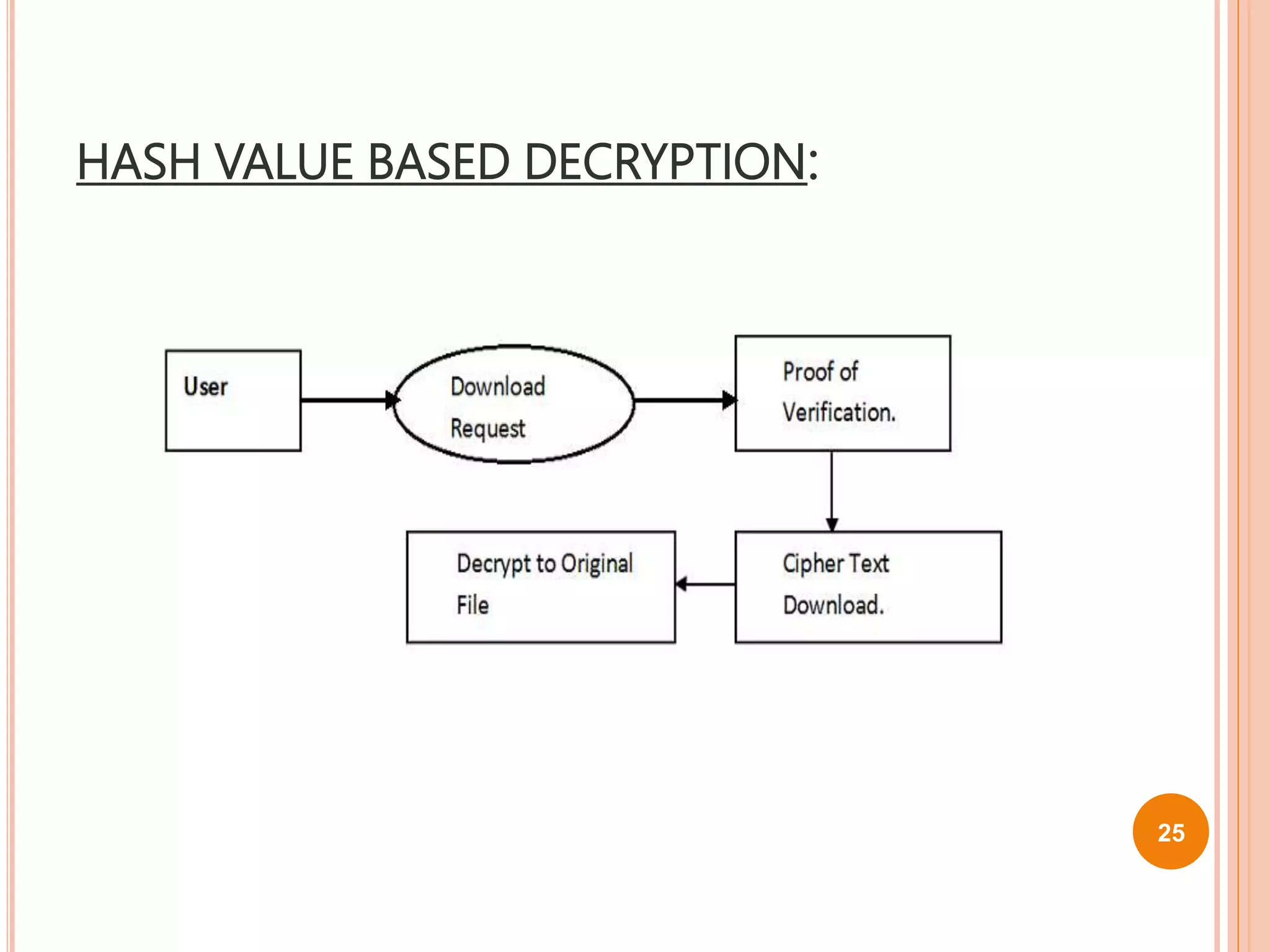
This document proposes a new technique called Dekey for secure deduplication in cloud storage. Dekey distributes convergent keys across multiple key servers to reduce key overhead and improve security compared to traditional convergent encryption. The document outlines issues with traditional encryption approaches, describes the baseline convergent encryption approach and issues with it, and then introduces the Dekey approach. Dekey supports both file-level and block-level deduplication while providing cost efficiency, security, and reliability through distributed convergent key management across multiple servers.













![8.REFERENCE
OpenSSL Project. [Online]. Available:
http://www.openssl.org/..
NIST’s Policy on Hash Functions, Sept. 2012.
[Online].
Available:http://csrc.nist.gov/groups/ST/hash/policy.html
P. Anderson and L. Zhang, ‘‘Fast and Secure Laptop
Backups with Encrypted De-Duplication,’’ in Proc.
USENIX LISA, 2010,pp. 1-8.
29](https://image.slidesharecdn.com/securededuplicatonwithefficientandreliableconvergent-161108071604/75/Secure-deduplicaton-with-efficient-and-reliable-convergent-29-2048.jpg)