Embed presentation
Downloaded 48 times




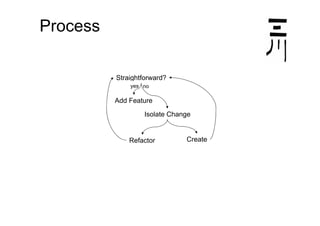
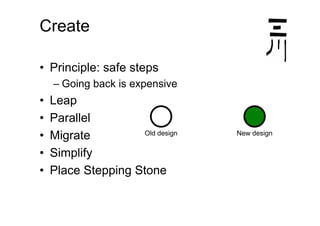
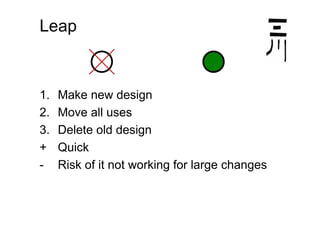
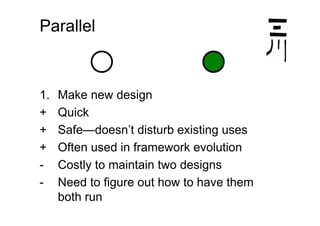
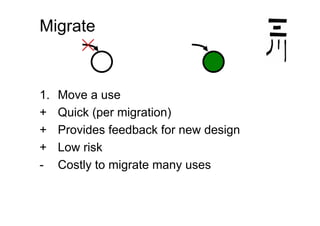
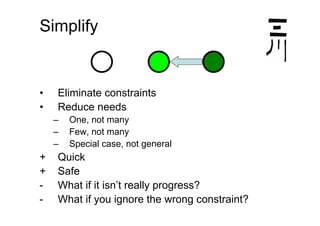
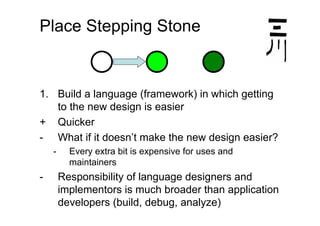


The document discusses effective design strategies, including: - Planning backwards from adding straightforward features and moving in safe steps such as refactoring to isolate changes and make progress even when the end goal is unclear. - Migrating to a new design by first moving individual uses, then deleting the old design in parallel or sequentially. Simplifying by eliminating constraints or reducing needs to special cases can also help progress but risks ignoring important factors. - Creating "stepping stones" like frameworks to make the path to a new design easier, though there are costs to consider for extra functionality and maintenance.













