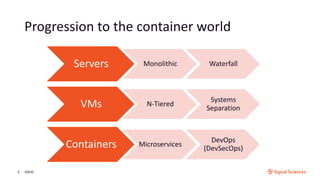
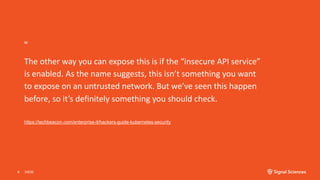
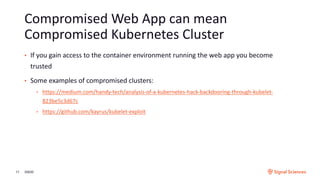
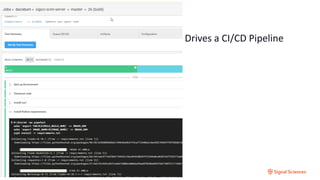
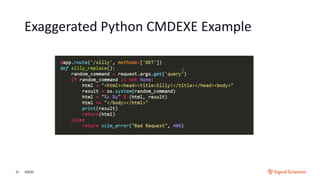
The document discusses securing containerized applications as organizations transition from monolithic systems to microservices. It highlights security complexities, including authentication and environmental security, as well as the impact of east-west traffic on datacenter security monitoring. Strategies such as utilizing service meshes like Istio and Envoy for traffic monitoring and ensuring secure CI/CD pipelines are emphasized to mitigate risks associated with compromised containers and applications.