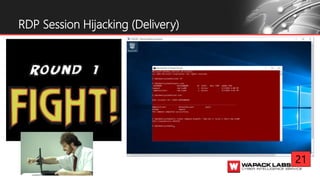
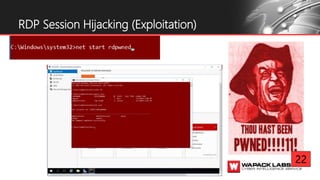
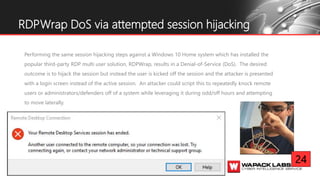
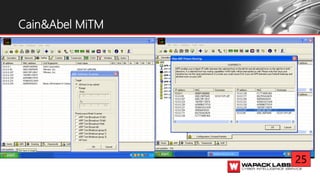
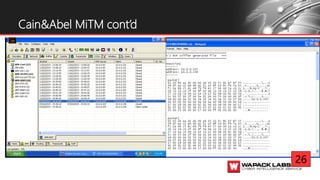
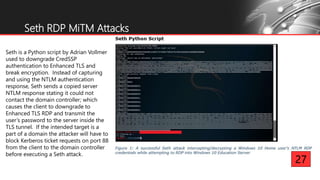
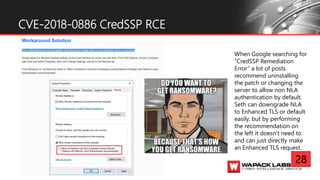
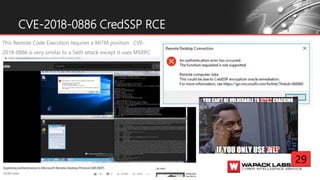
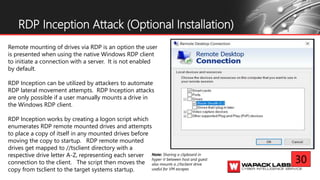
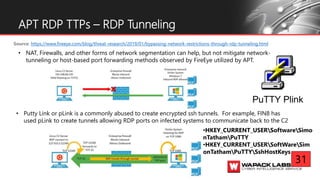
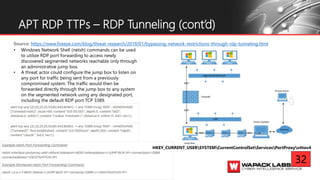
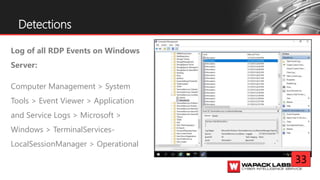
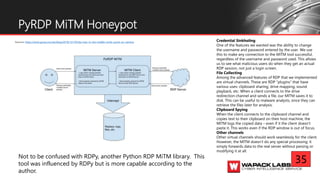
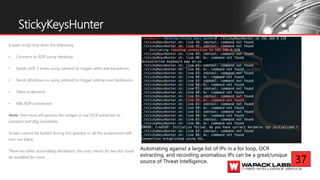
Jesse V. Burke presents on adversarial RDP tactics, techniques, and procedures (TTPs). The presentation reviews the RDP attack cycle from initial reconnaissance using tools like Shodan to identify open RDP ports, through exploitation of vulnerabilities like MS12-020 and EsteemAudit, lateral movement using session hijacking, and potential mitigations. It provides details on common RDP attacks like brute forcing passwords, downgrading encryption, and using tools like Cain & Abel or Seth to perform man-in-the-middle attacks to decrypt credentials. The presentation emphasizes that proper patching, firewalls, and securing RDP connections can help prevent many external and internal RDP attacks.







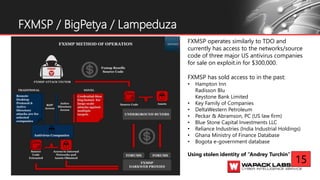
![While most actors looking to carry out a specific targeted attack against a company will usually not
have much luck in the underground without directly contacting the sellers and asking (potentially
peaking others curiosity and creating competition). There are also opportunistic actors which are not
targeting any specific company but hoping to laterally move throughout a company and get access to
the domain controller so they can sell access to the entire network. One prolific group known for
doing this was TheDarkOverlord (TDO); who was found to often use purchased RDP servers from now
seized xDedic[.]biz and move laterally throughout organizations with the initial RDP foothold. Once
TDO was able to gain primary control over the domain via administrator accounts or domain controller
they would sell access to the company for thousands (sometimes hundreds of thousands) of dollars in
private forums.
TheDarkOverlord (TDO)
14](https://image.slidesharecdn.com/hmconf7-190519121532/85/Jesse-Burke-RDPwned-HackMiami7-14-320.jpg)