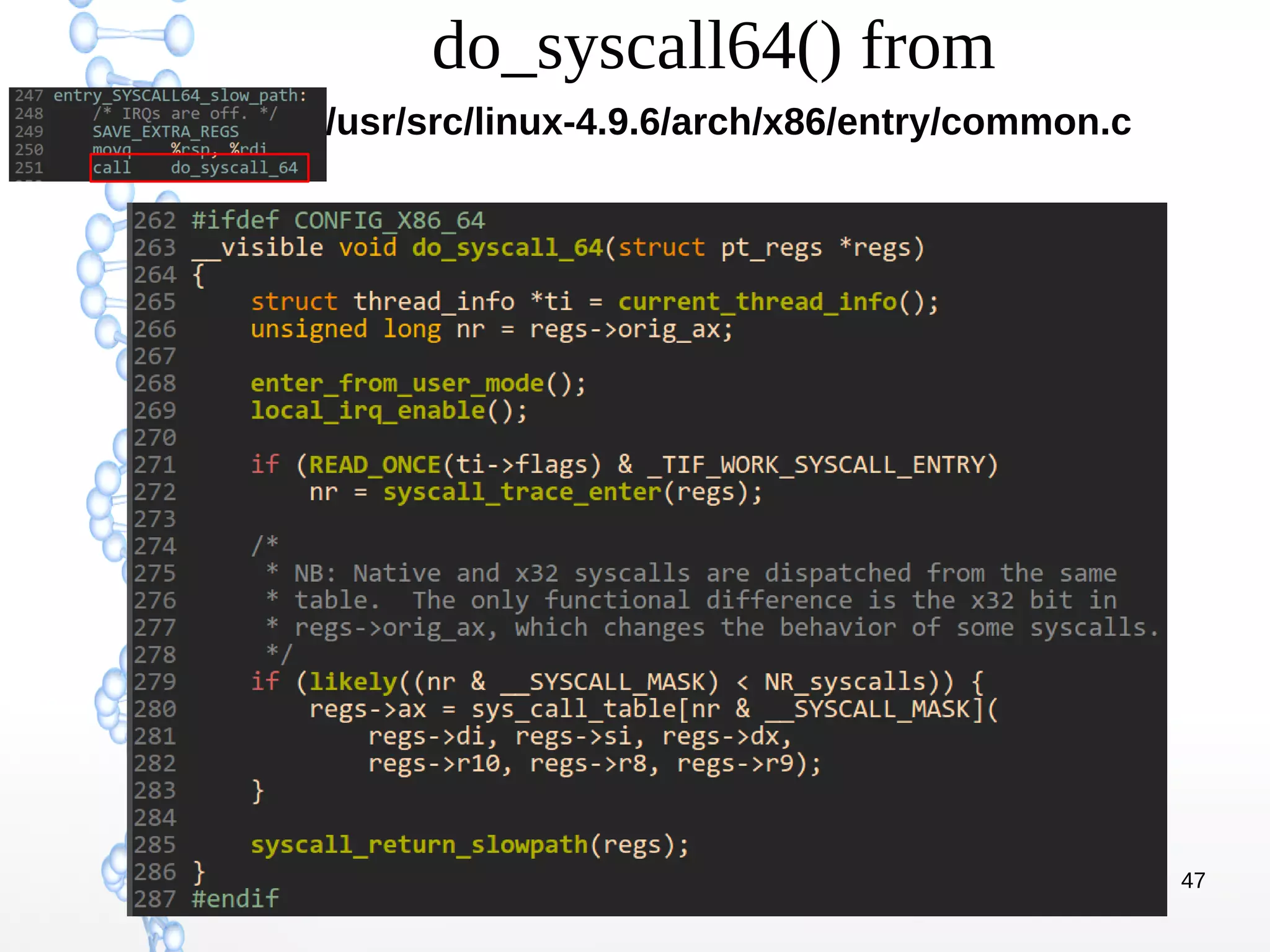
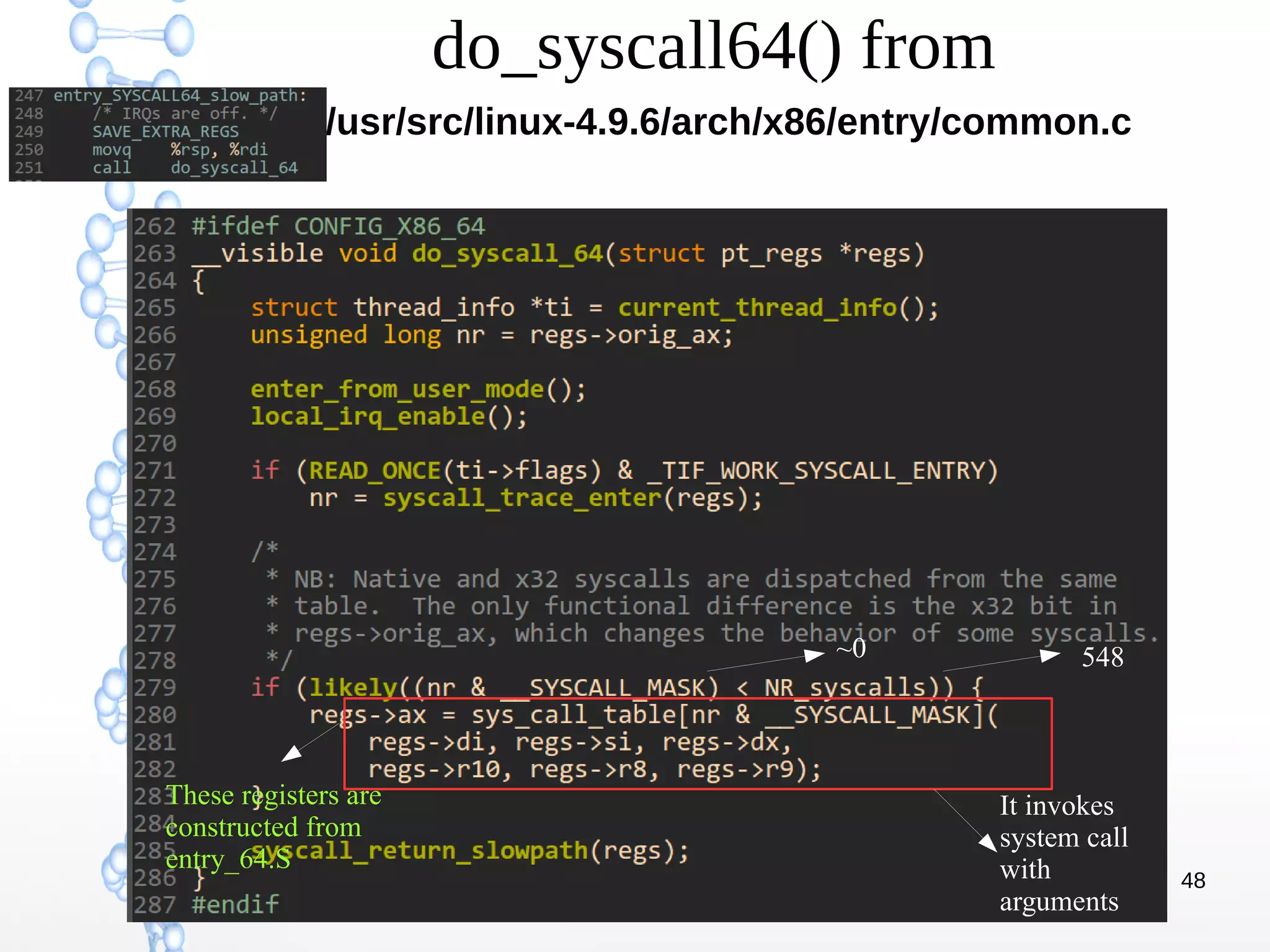
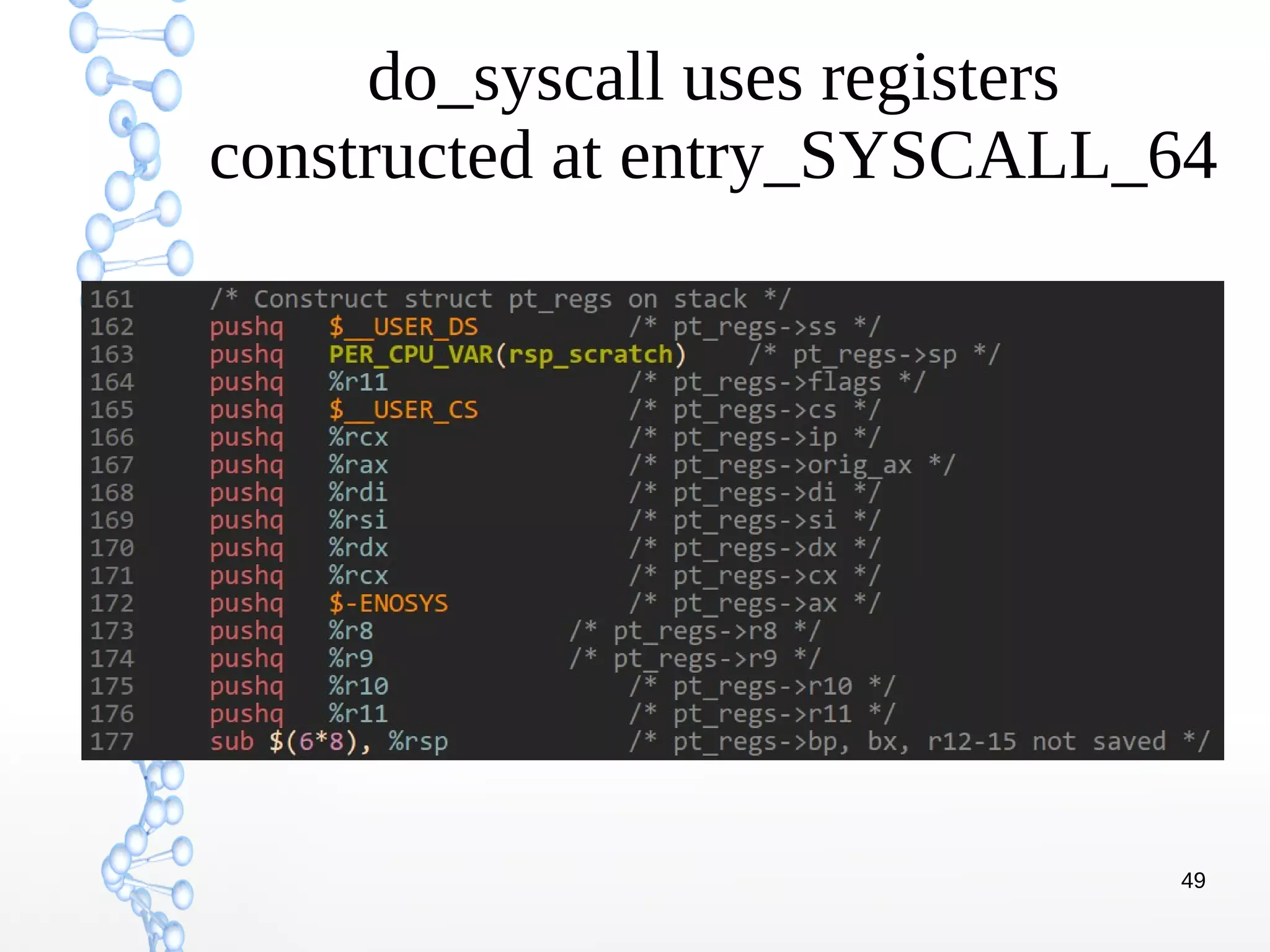
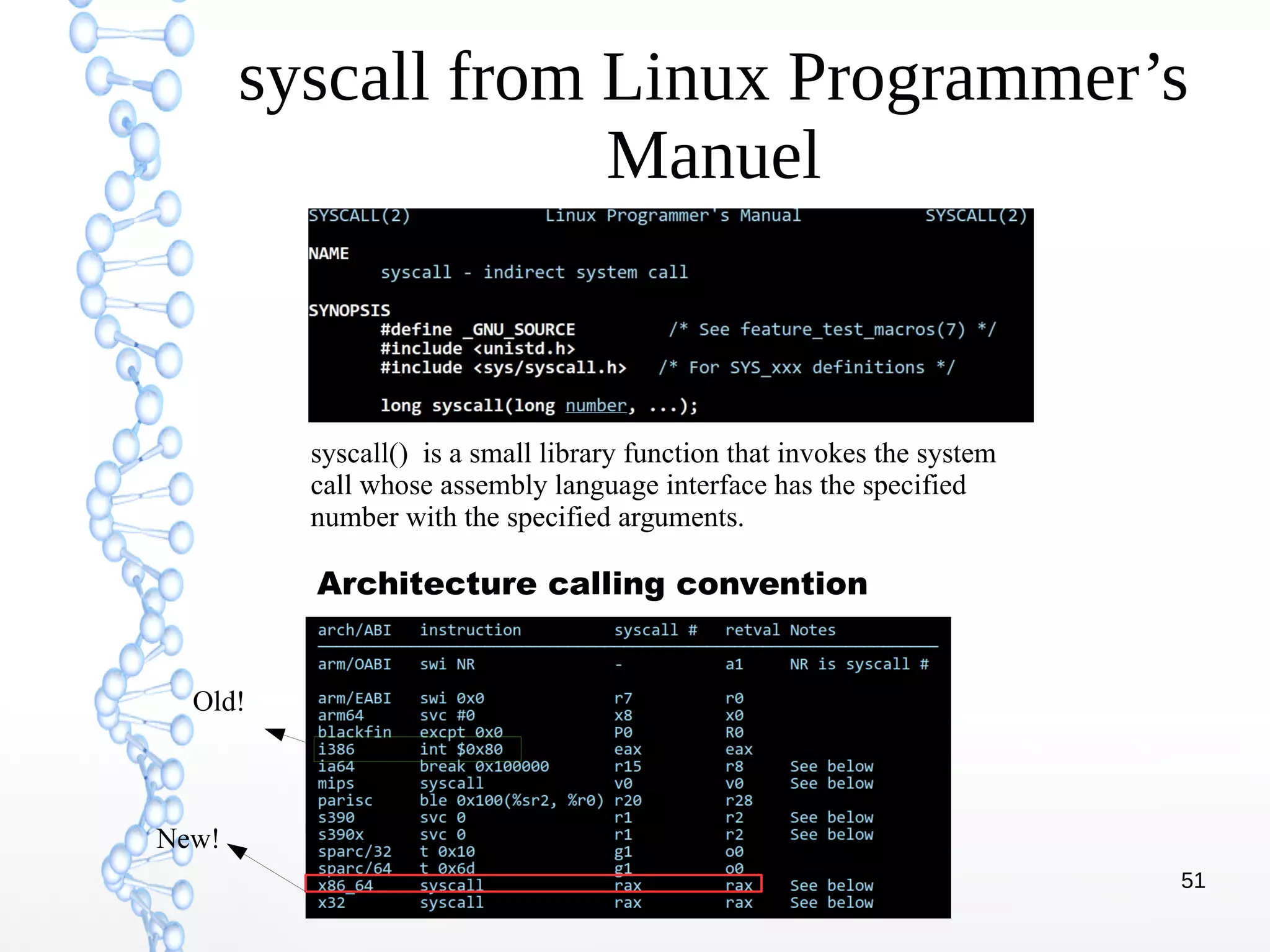
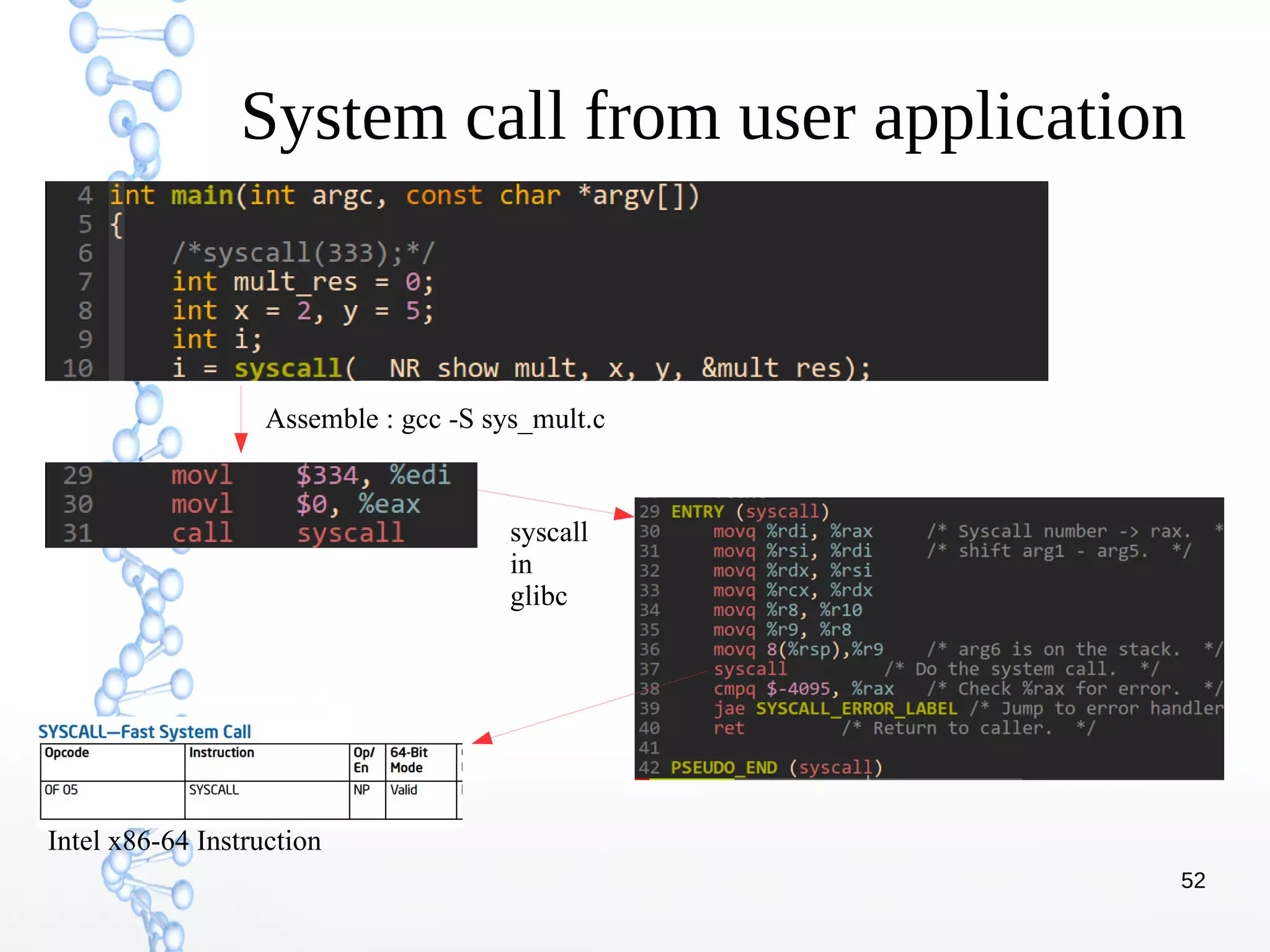
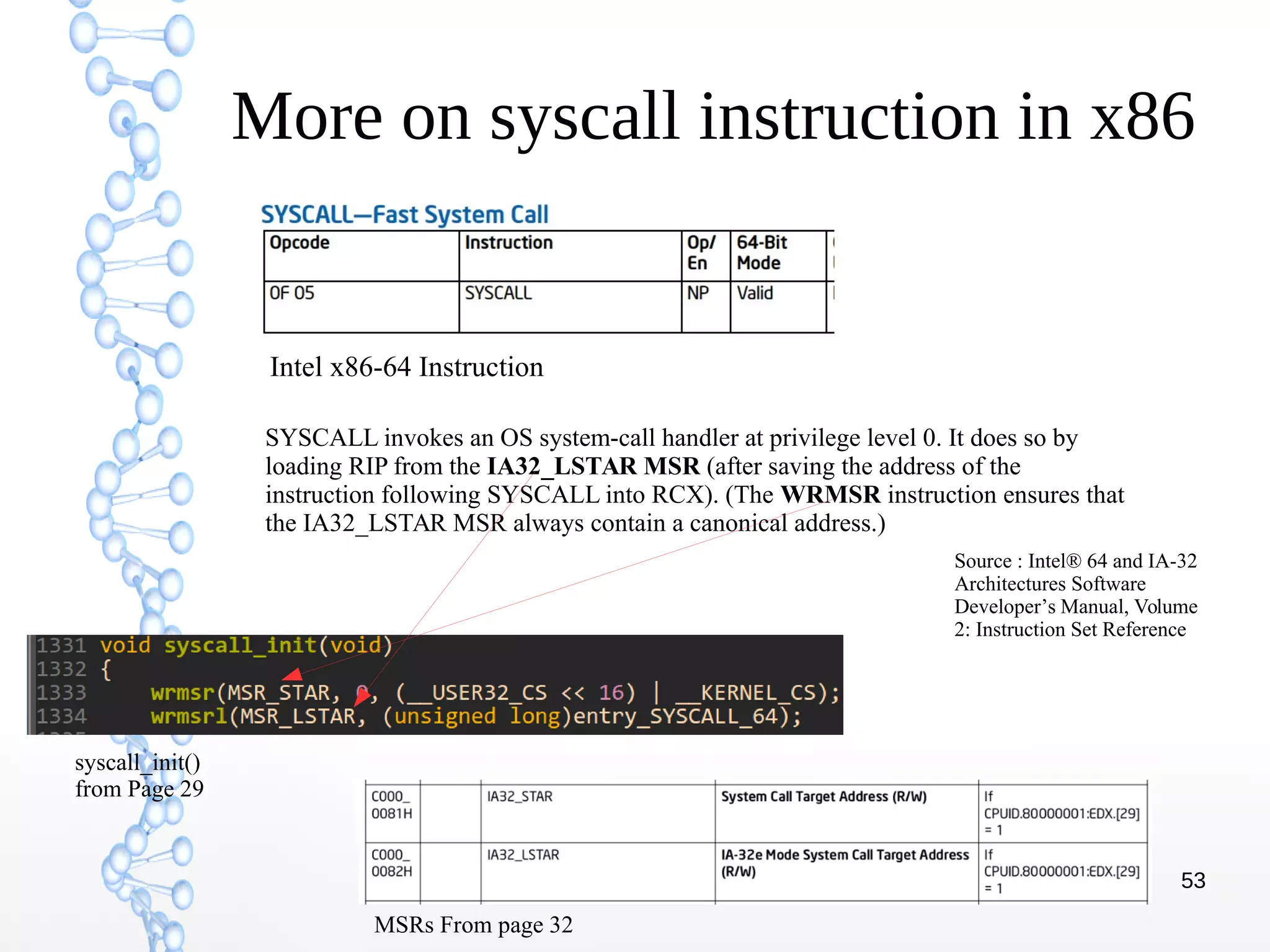
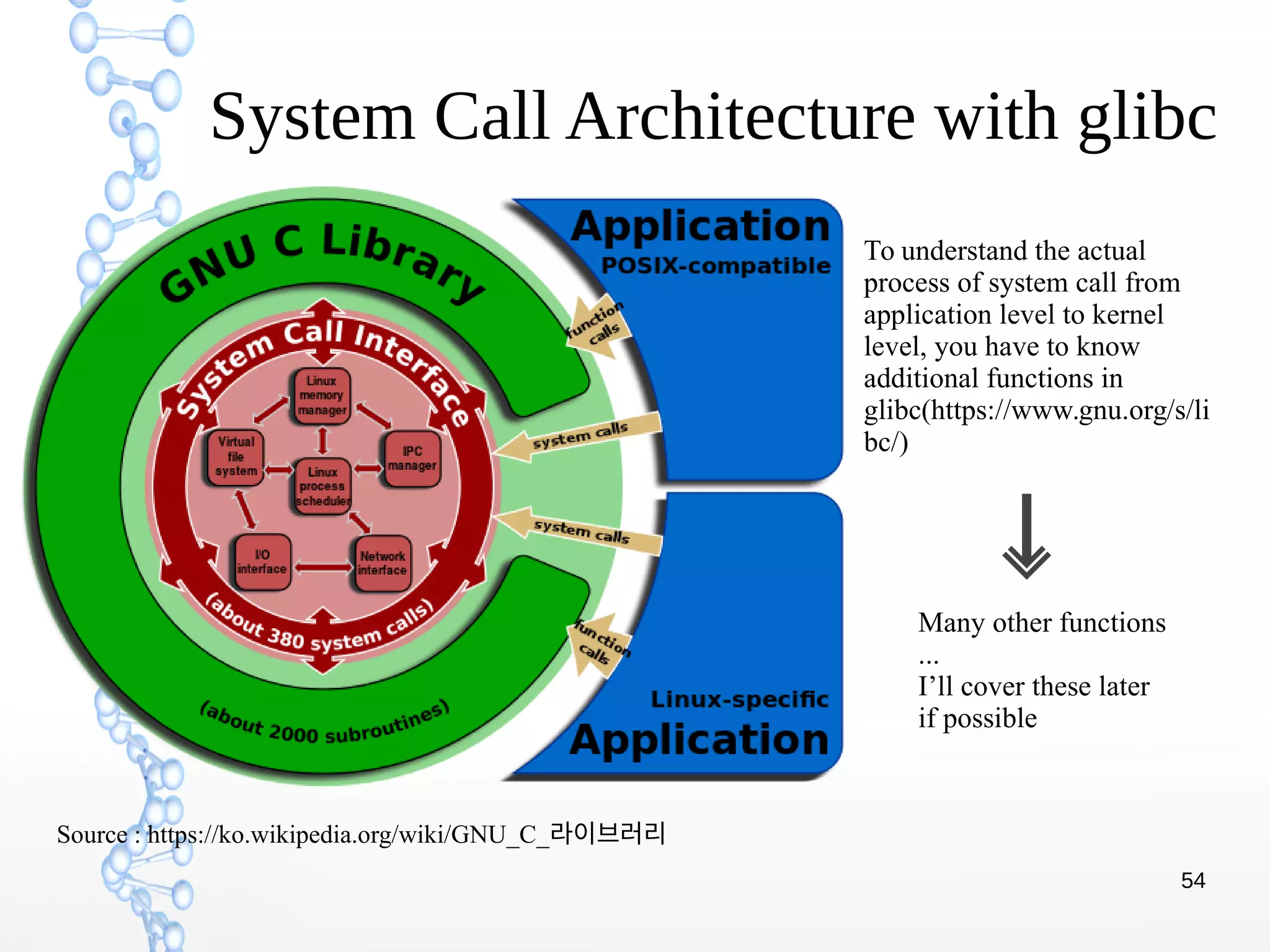
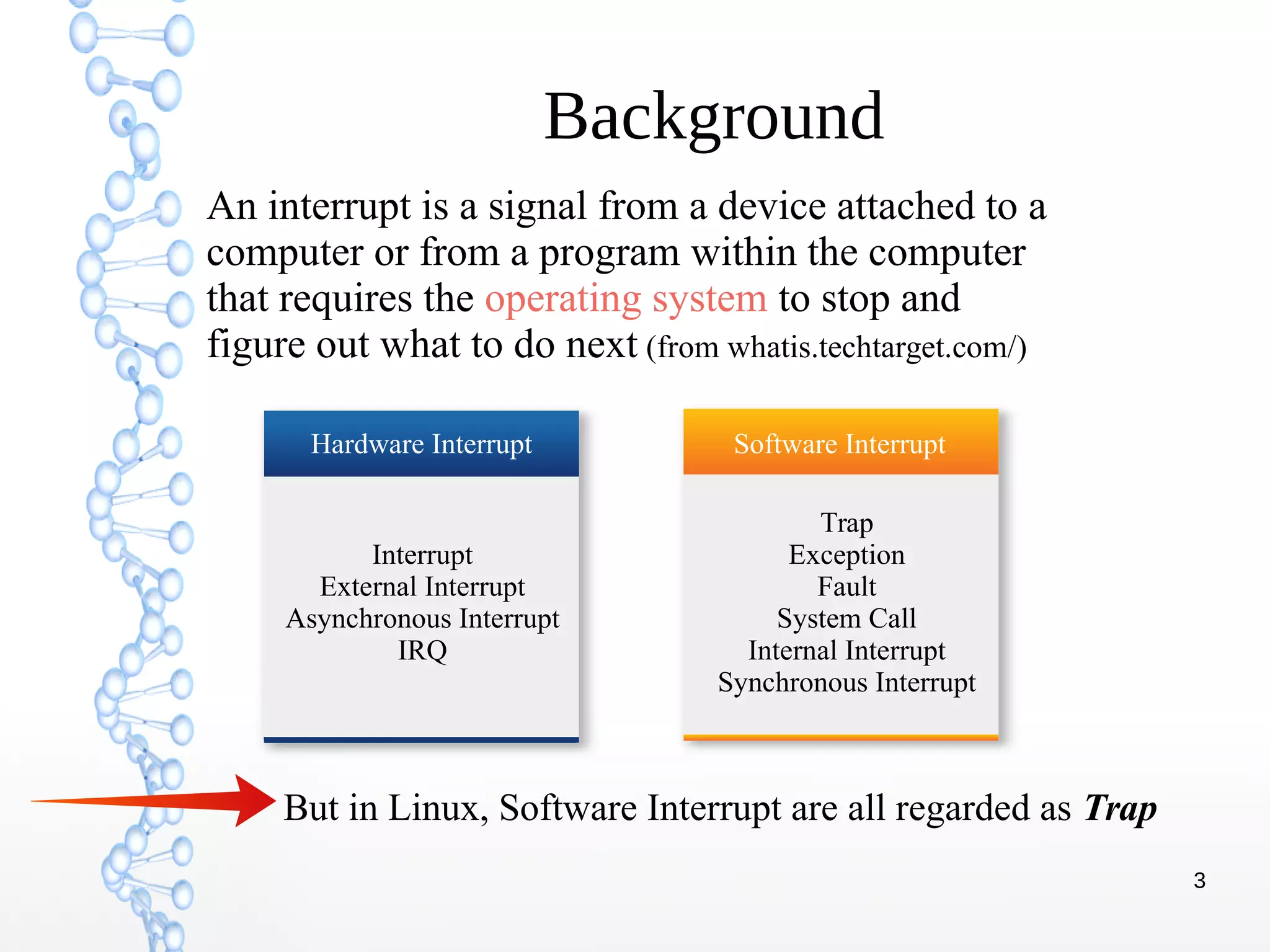
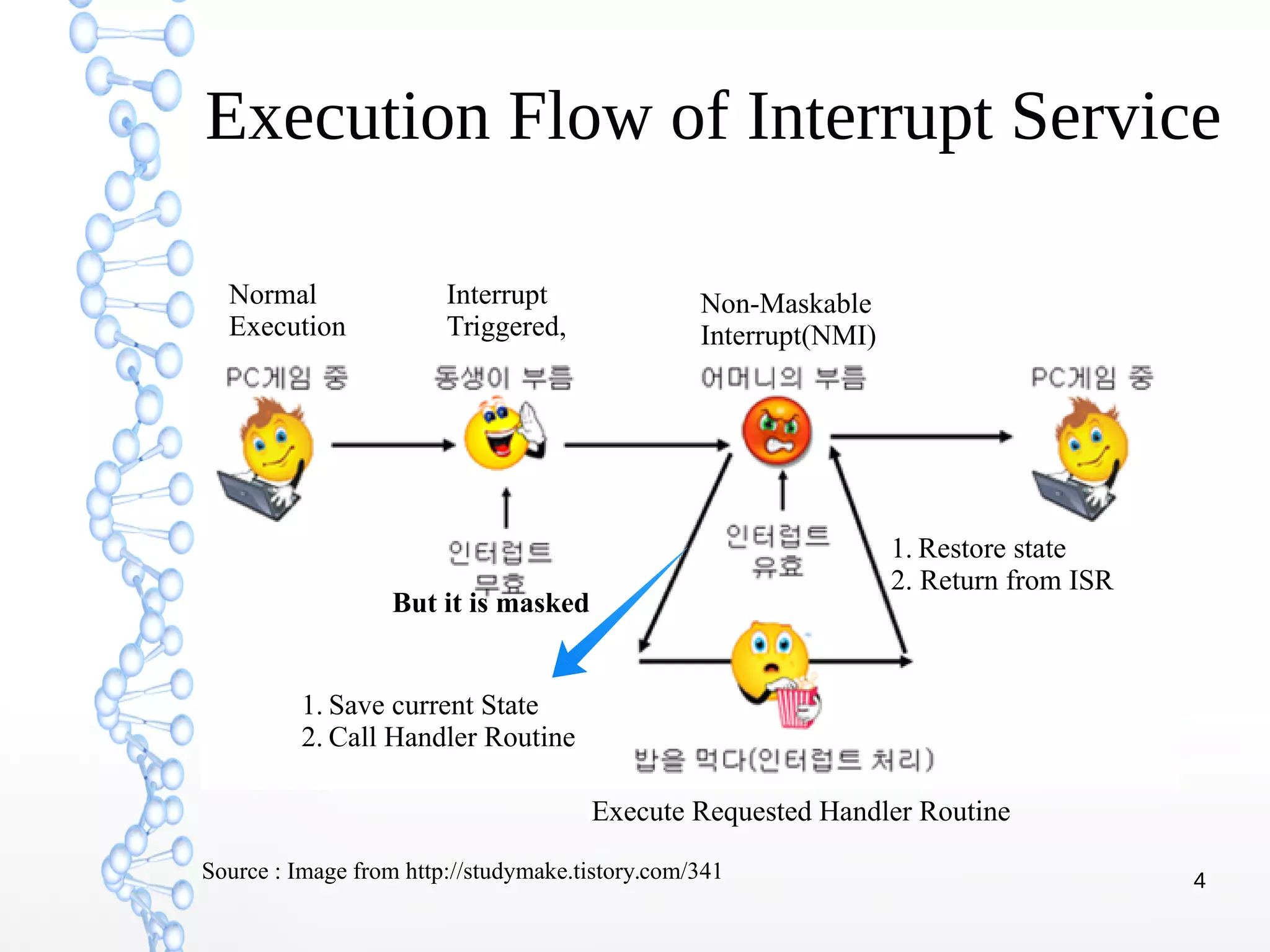
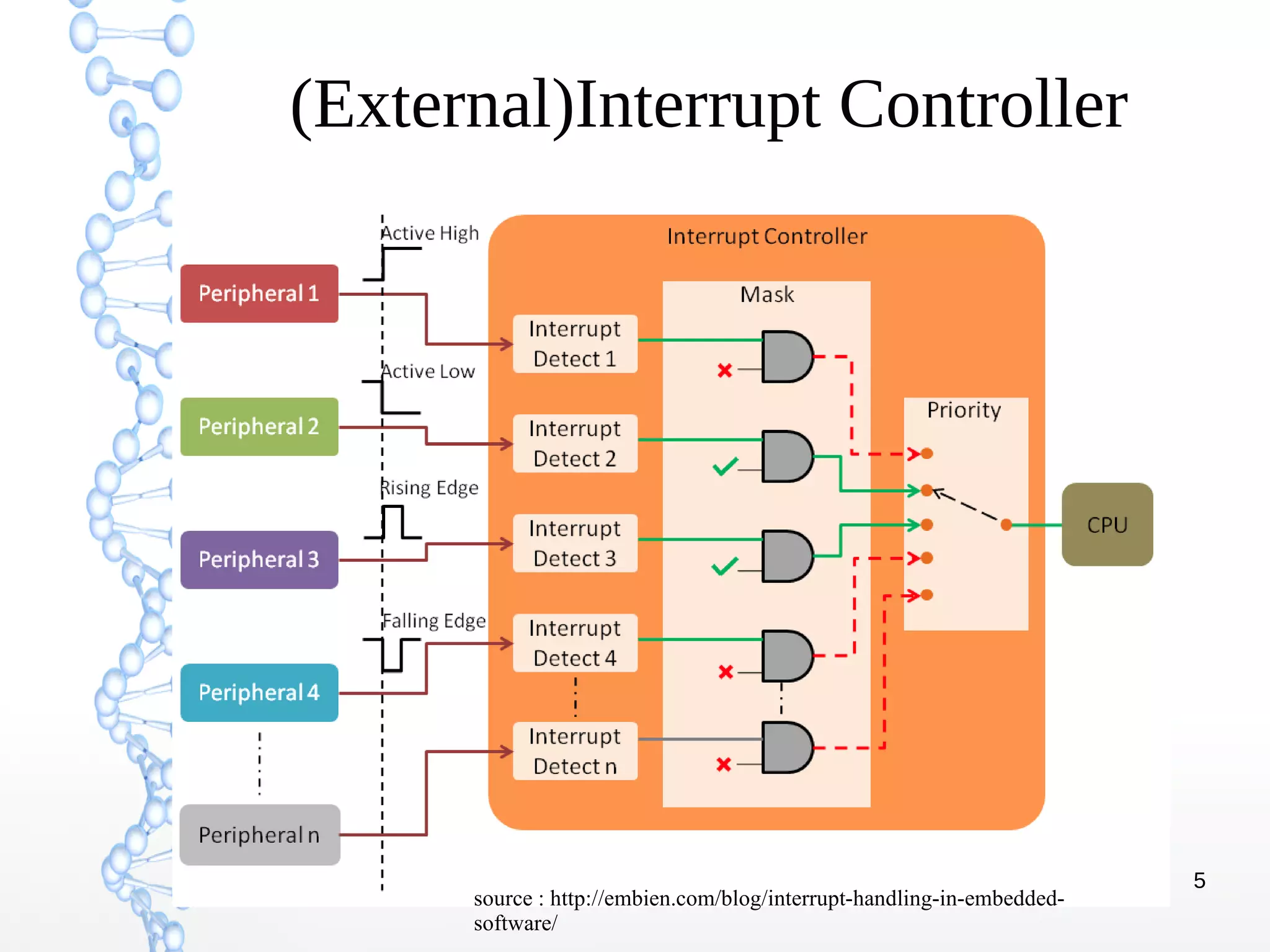
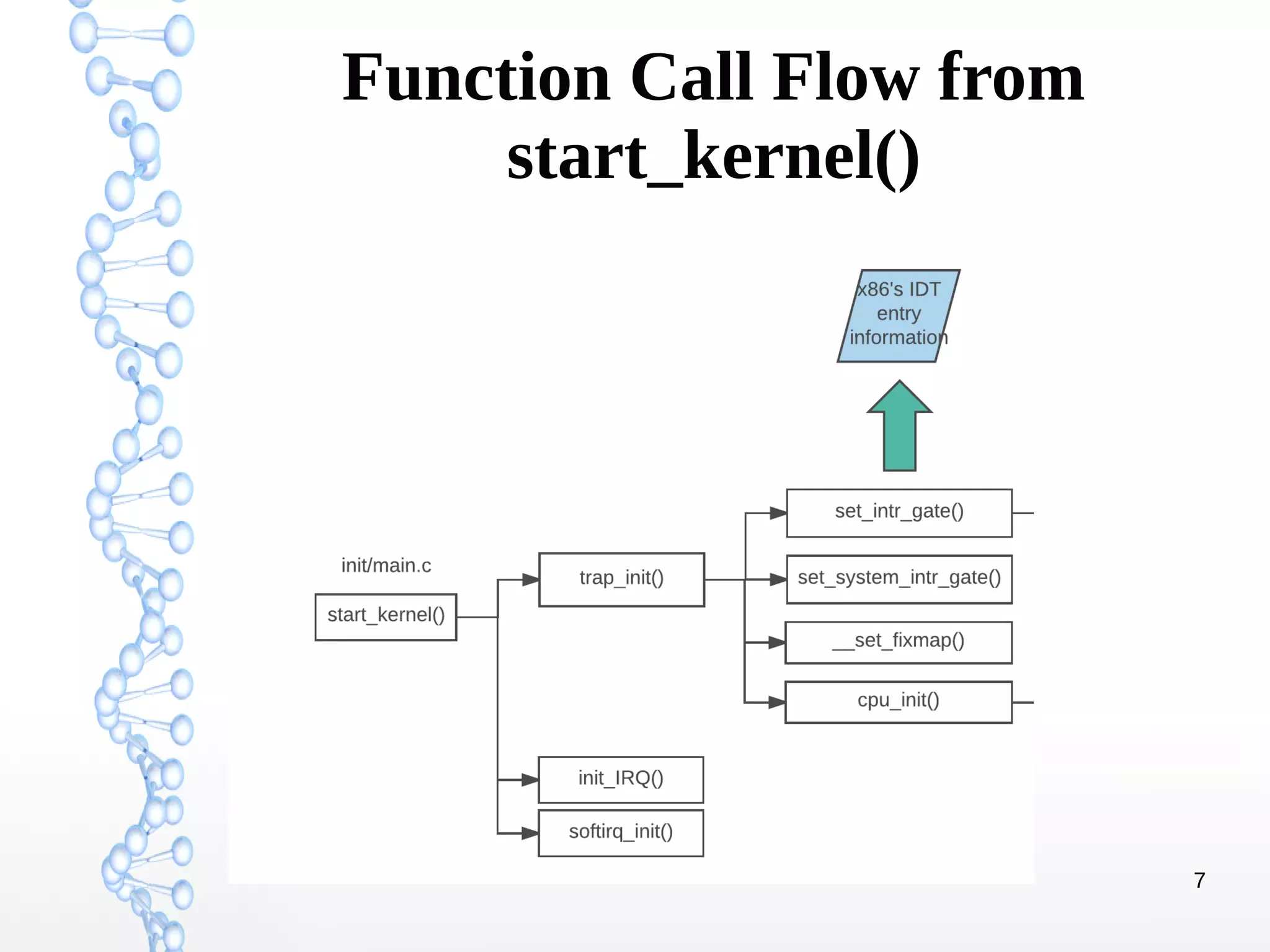
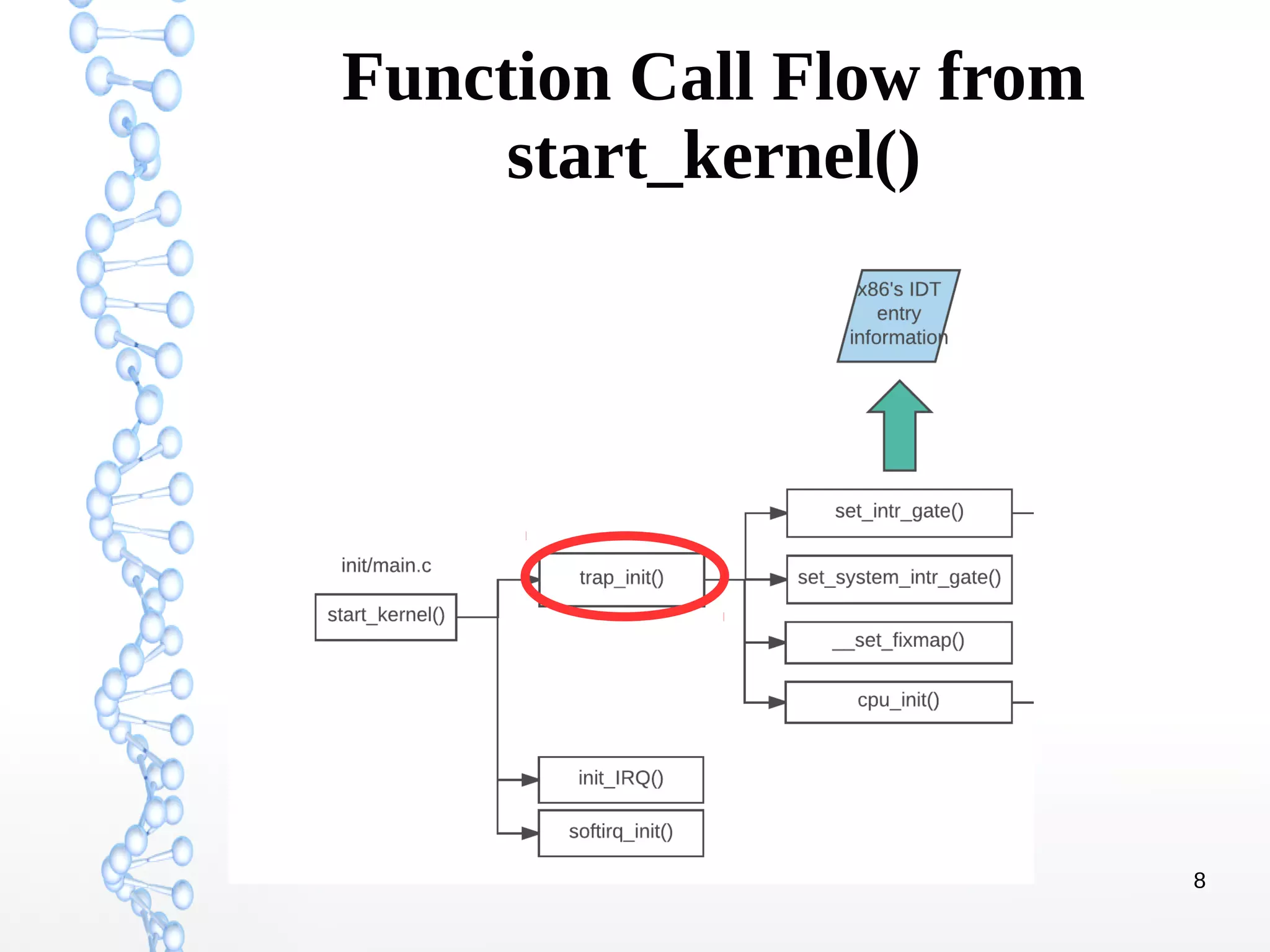
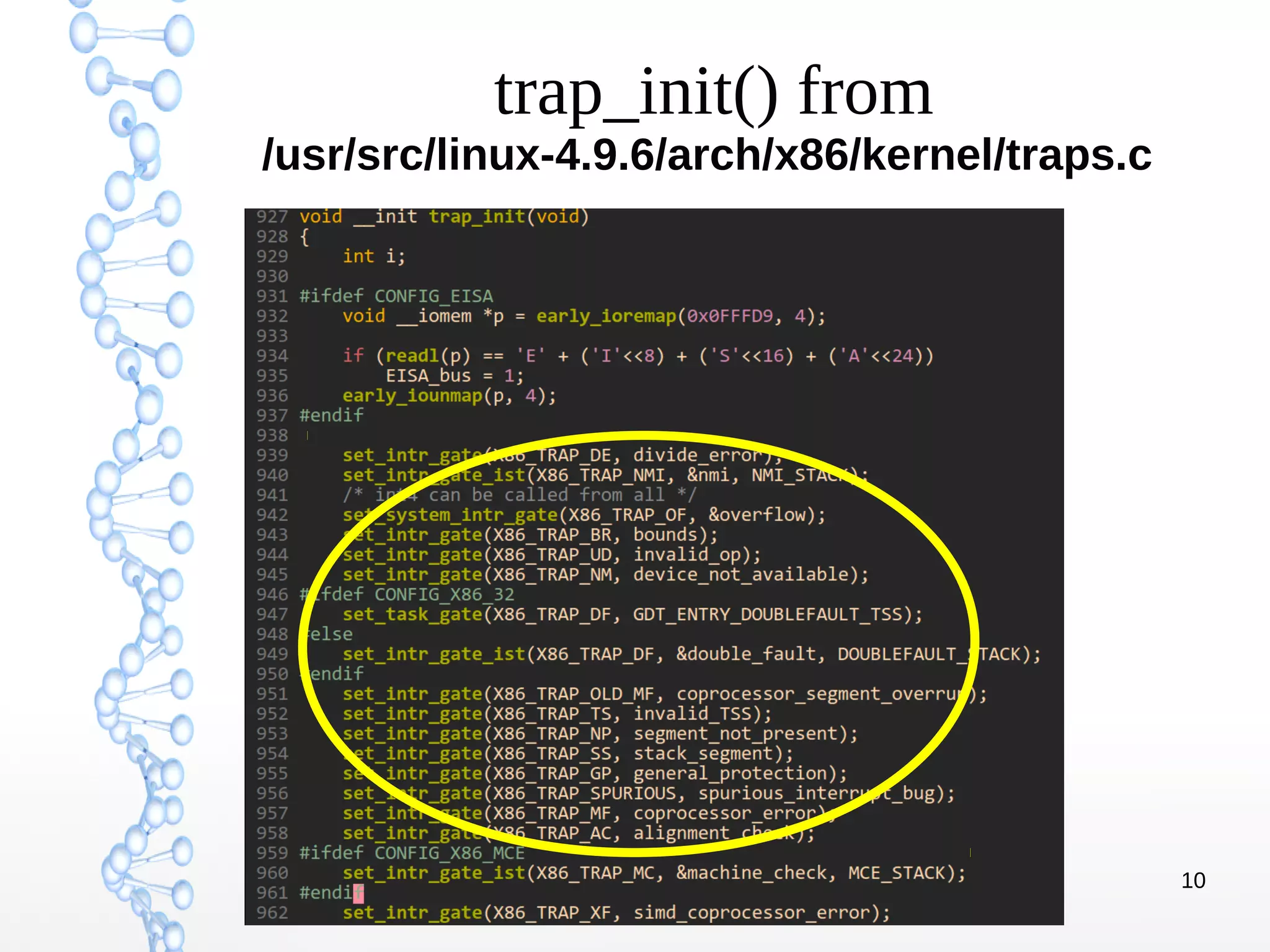
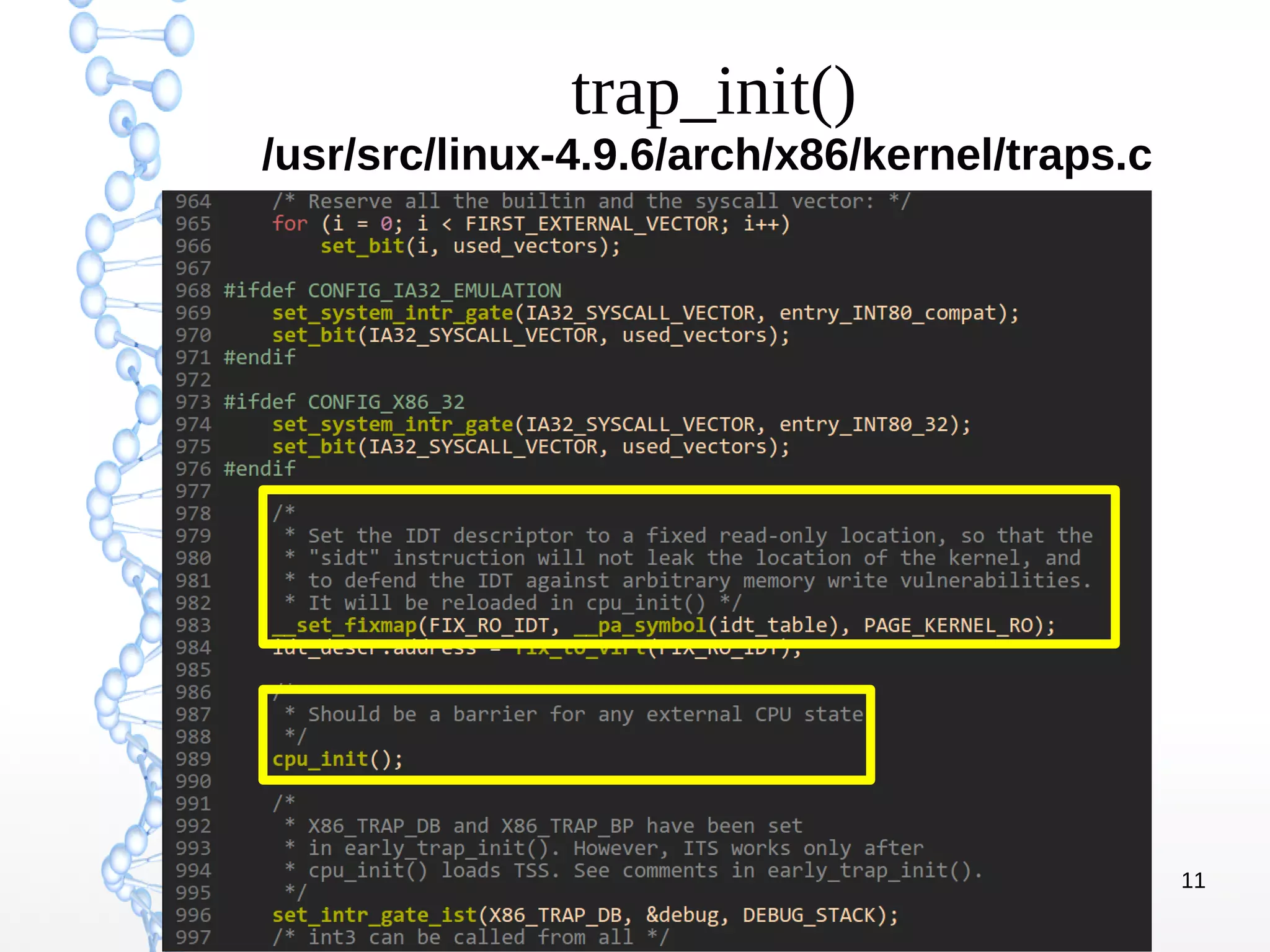
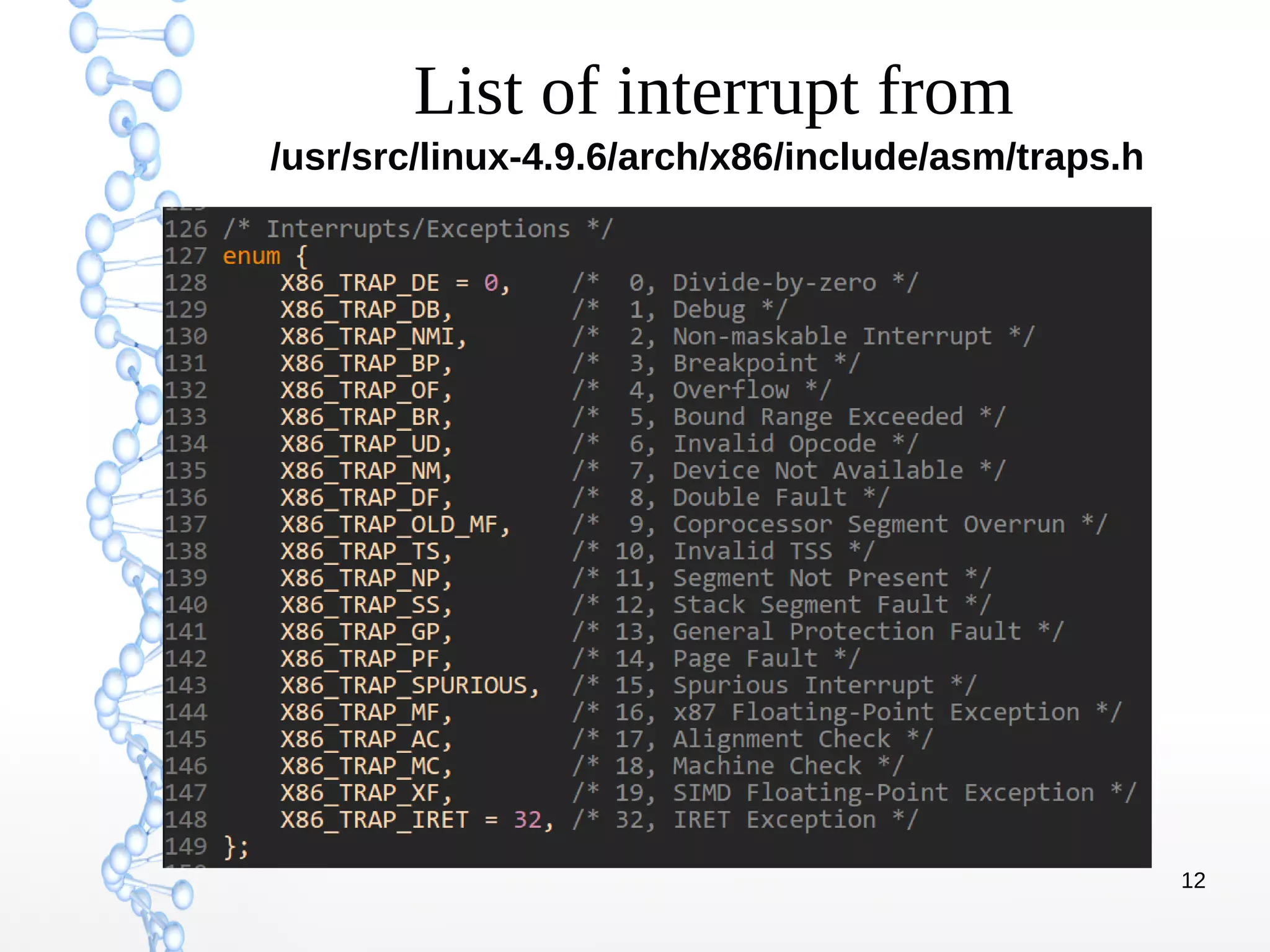
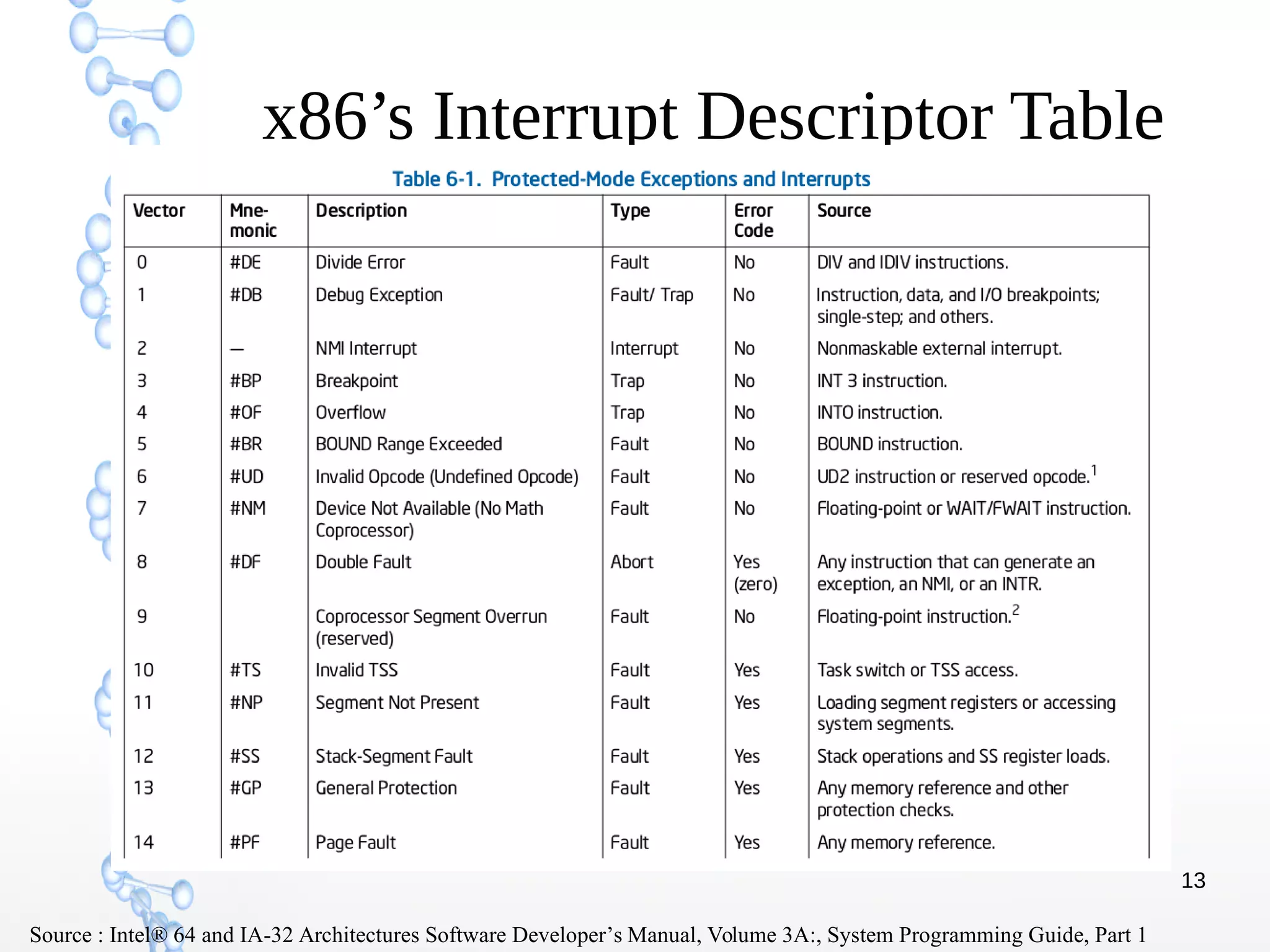
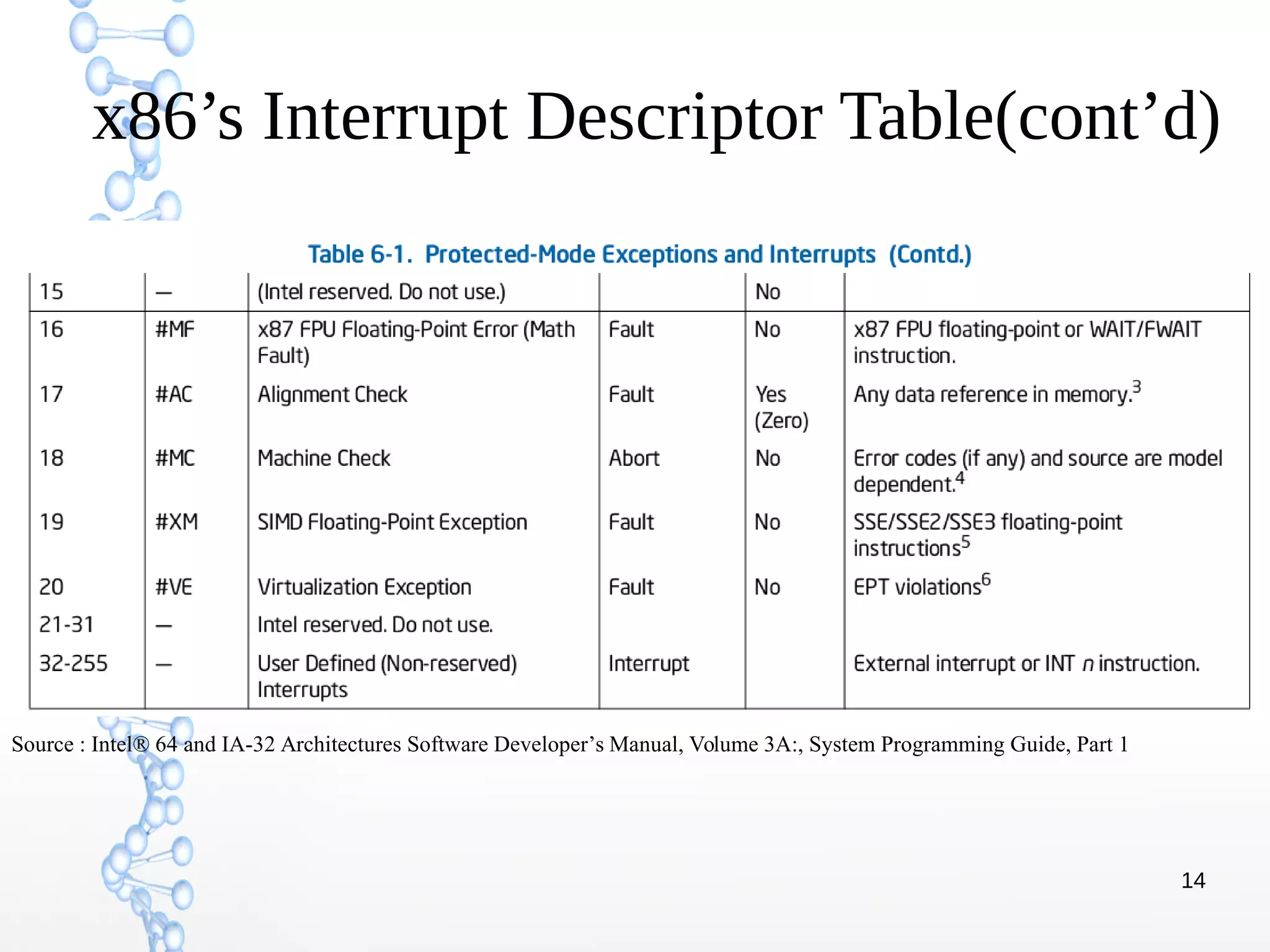
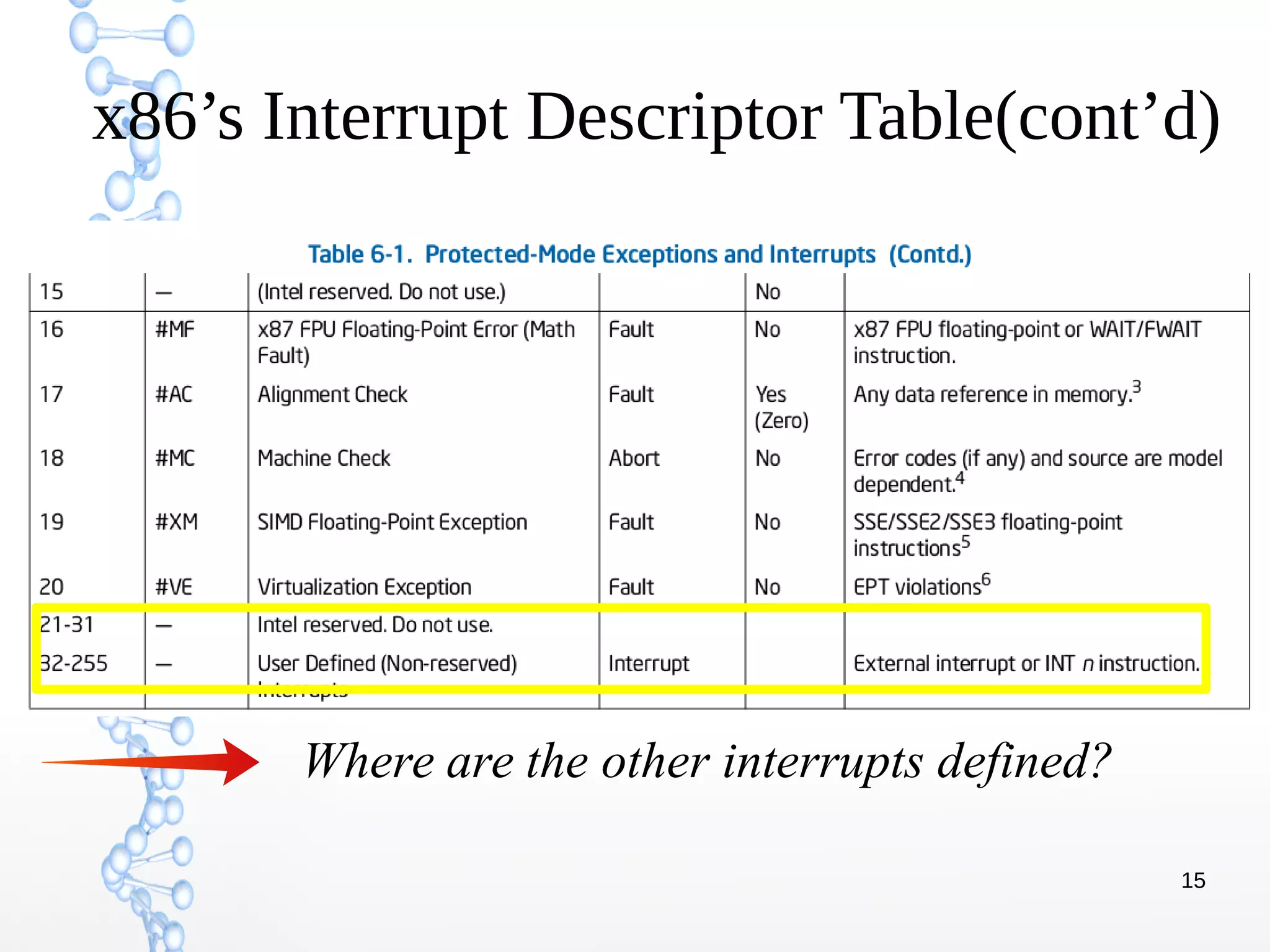
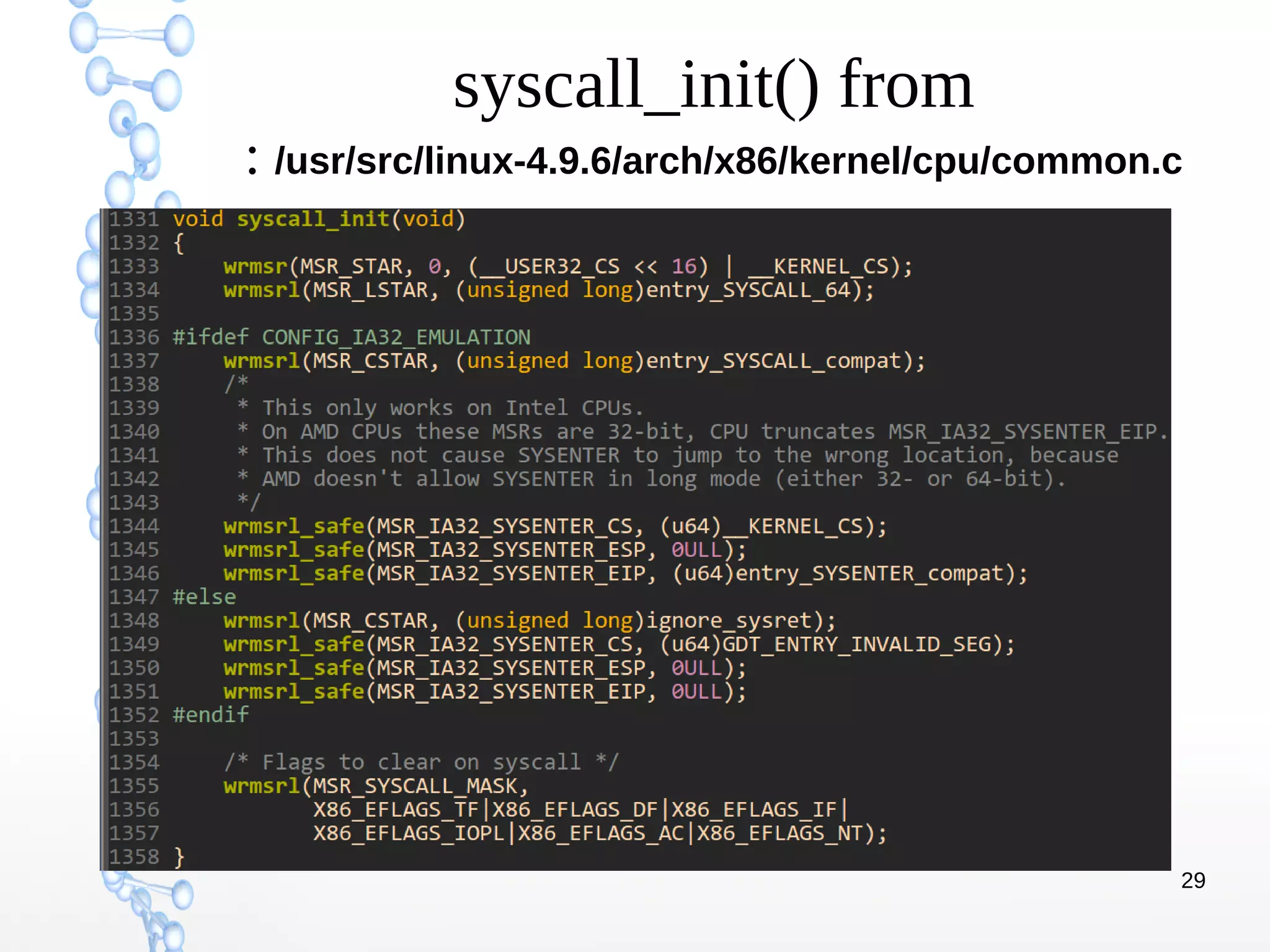
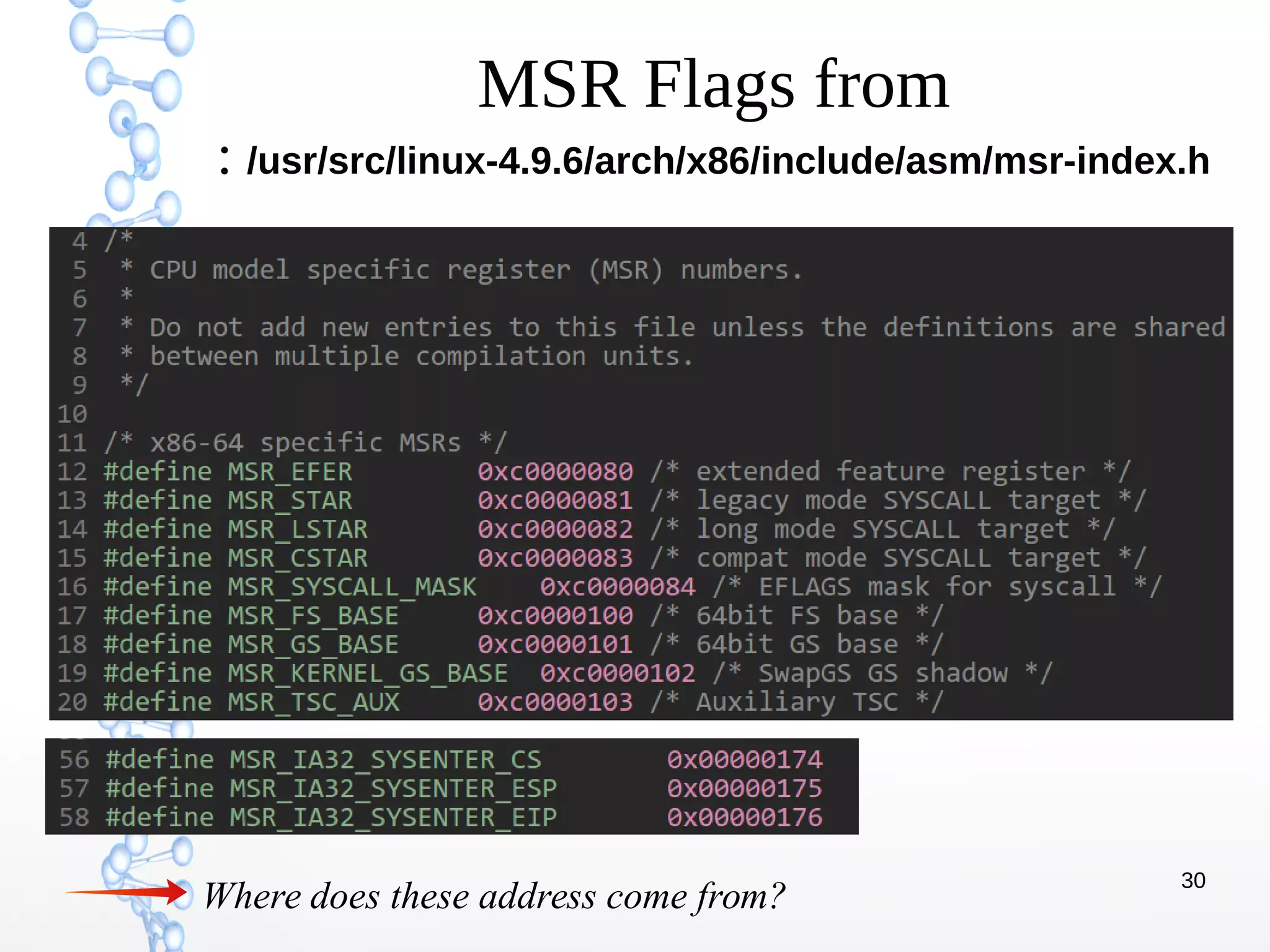
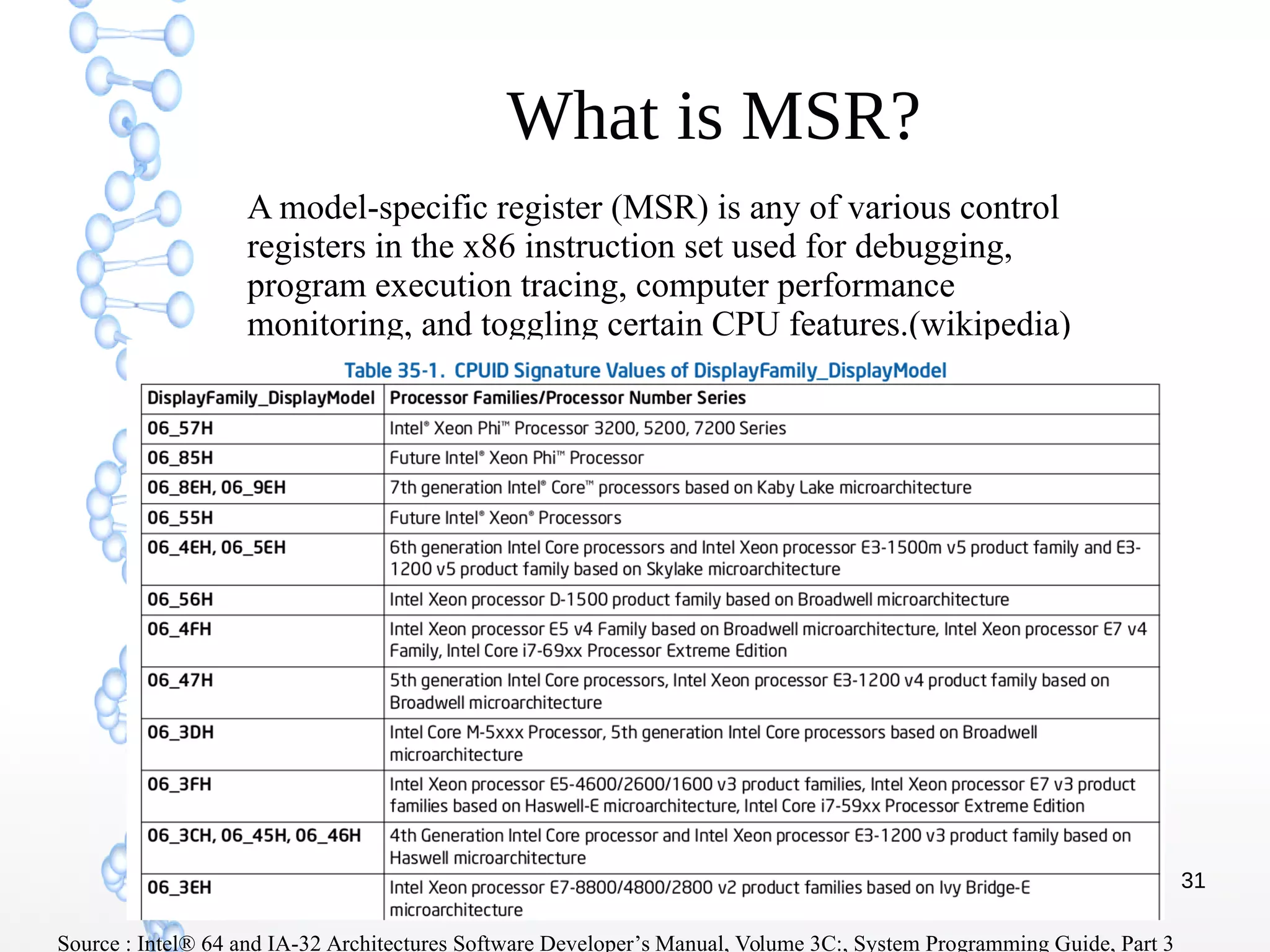
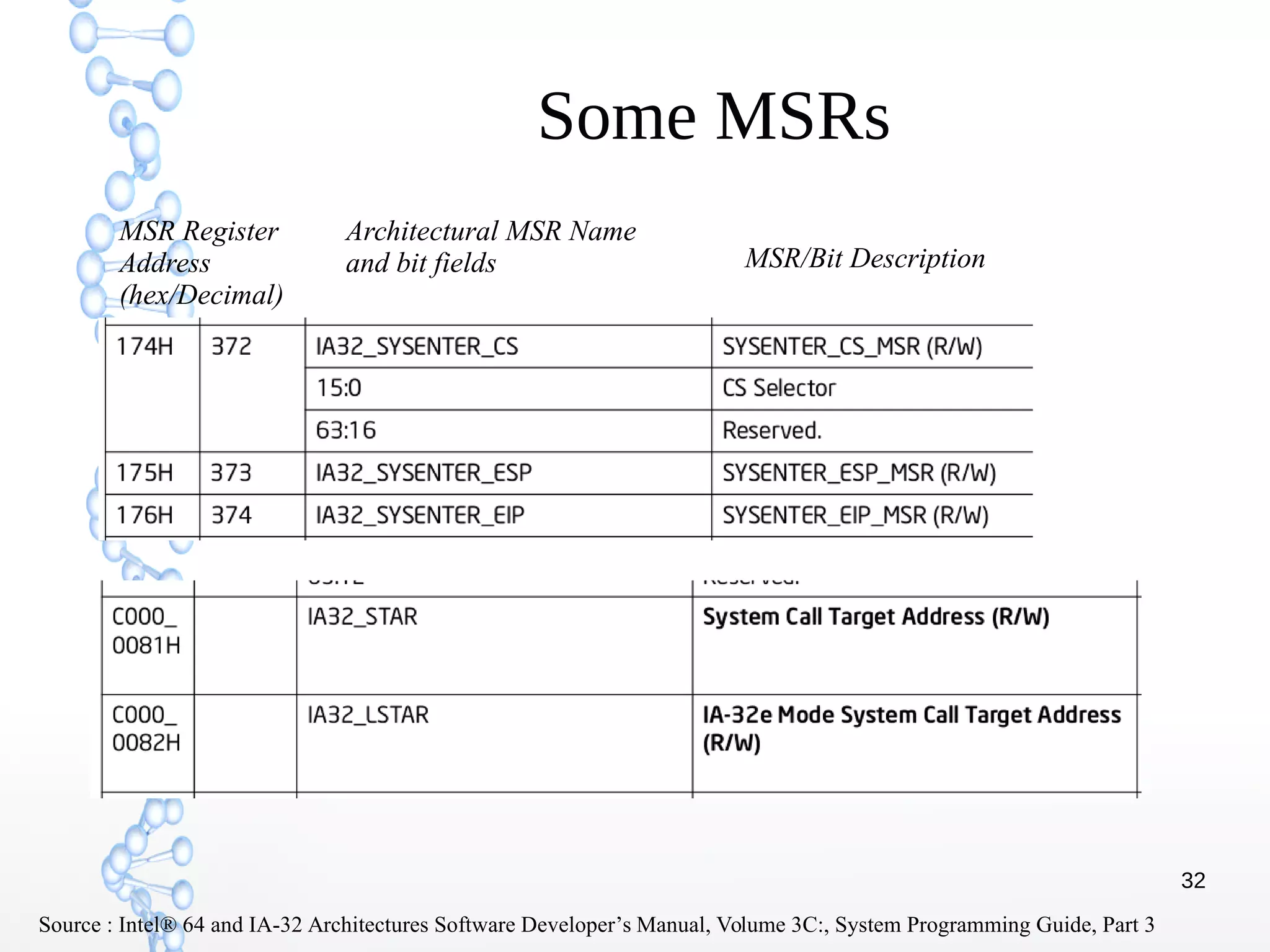
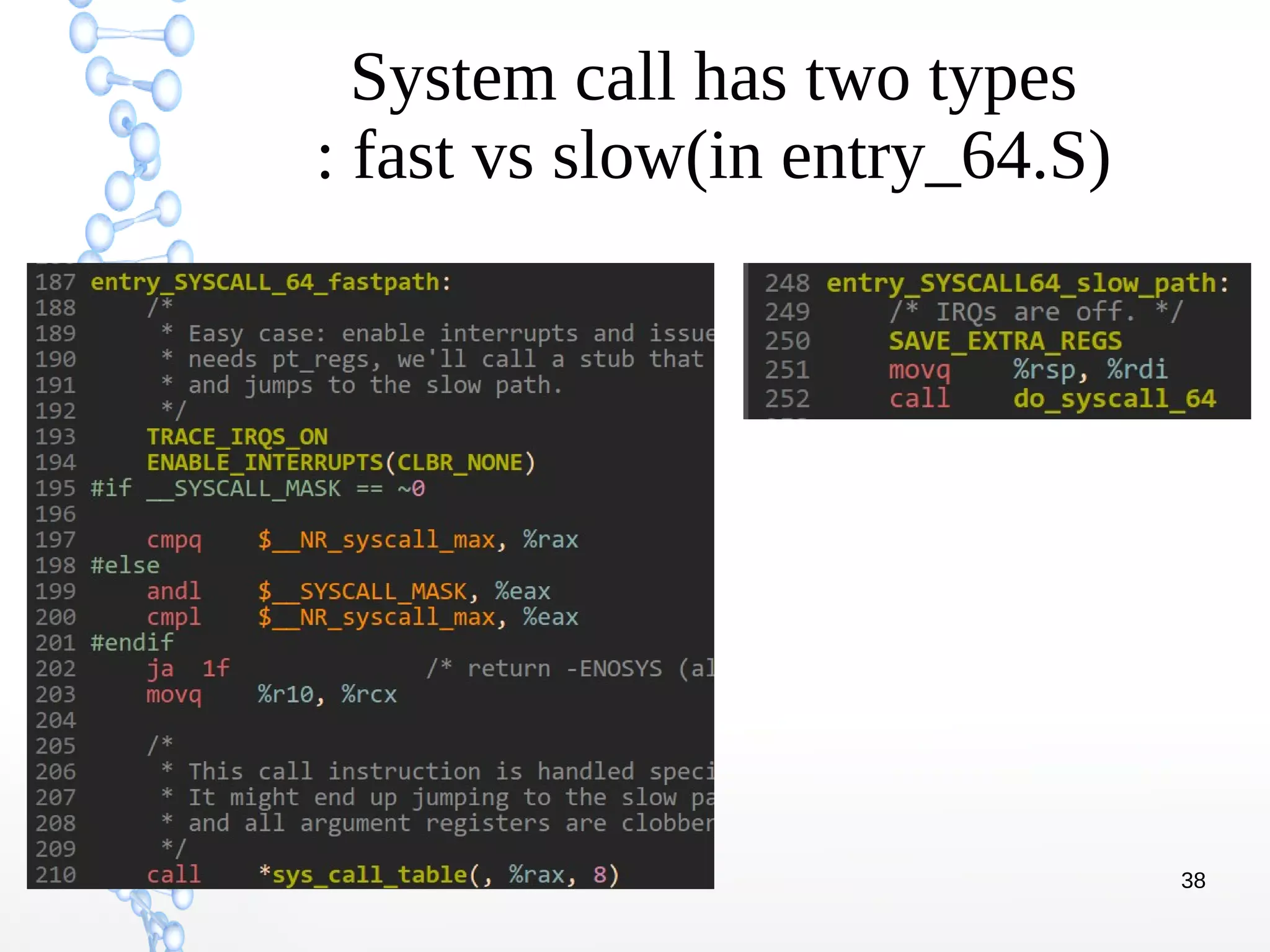
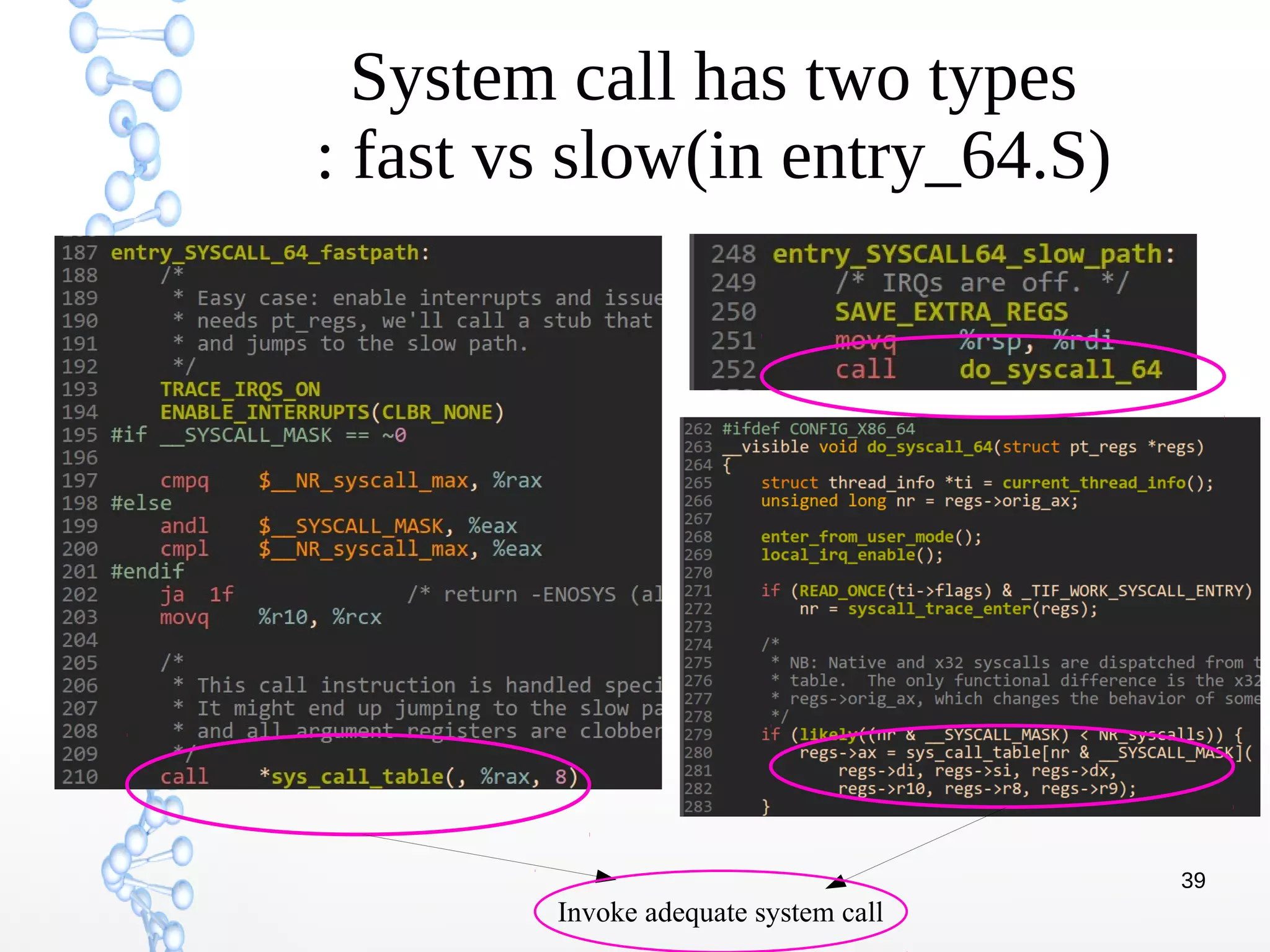
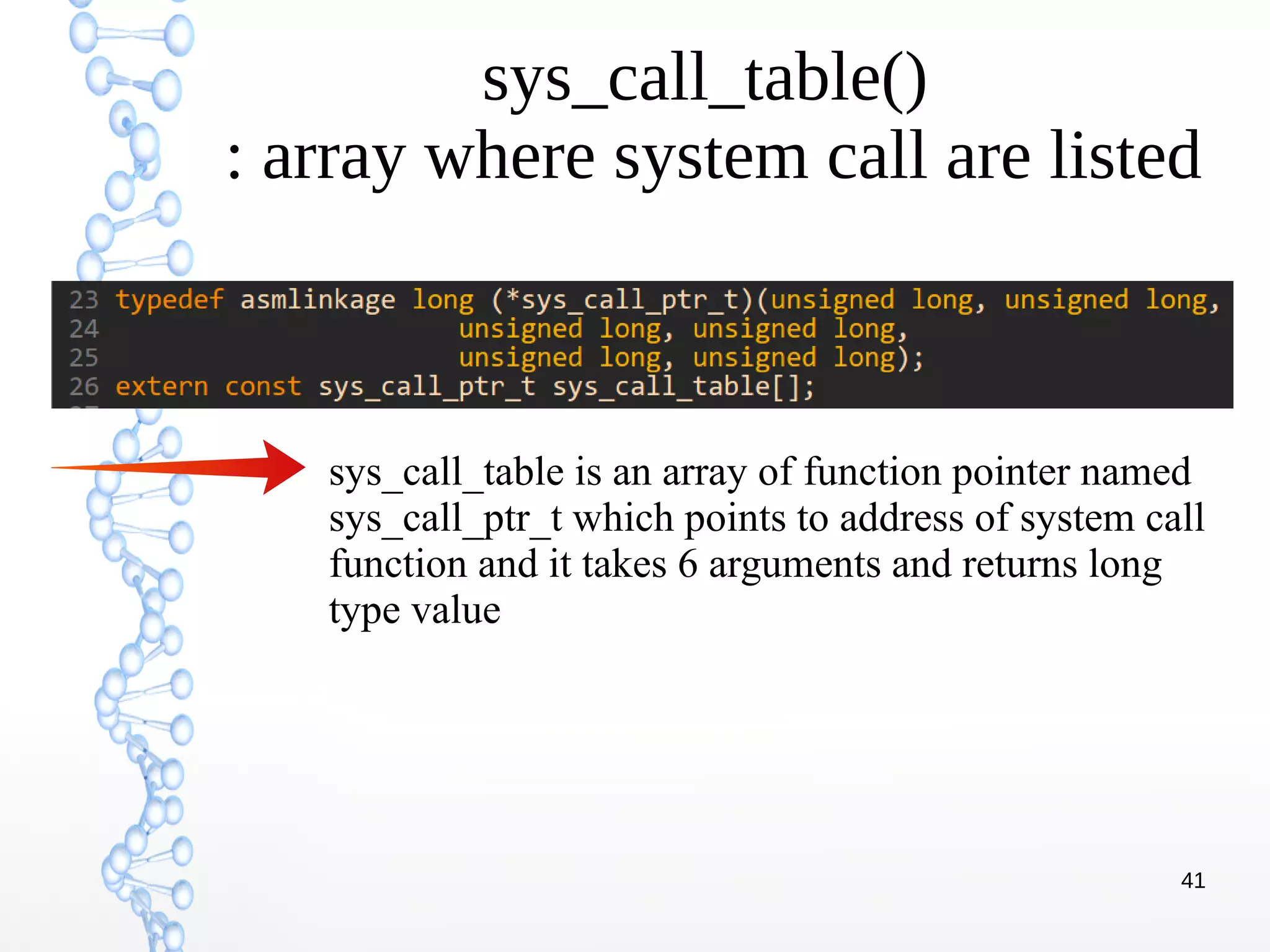
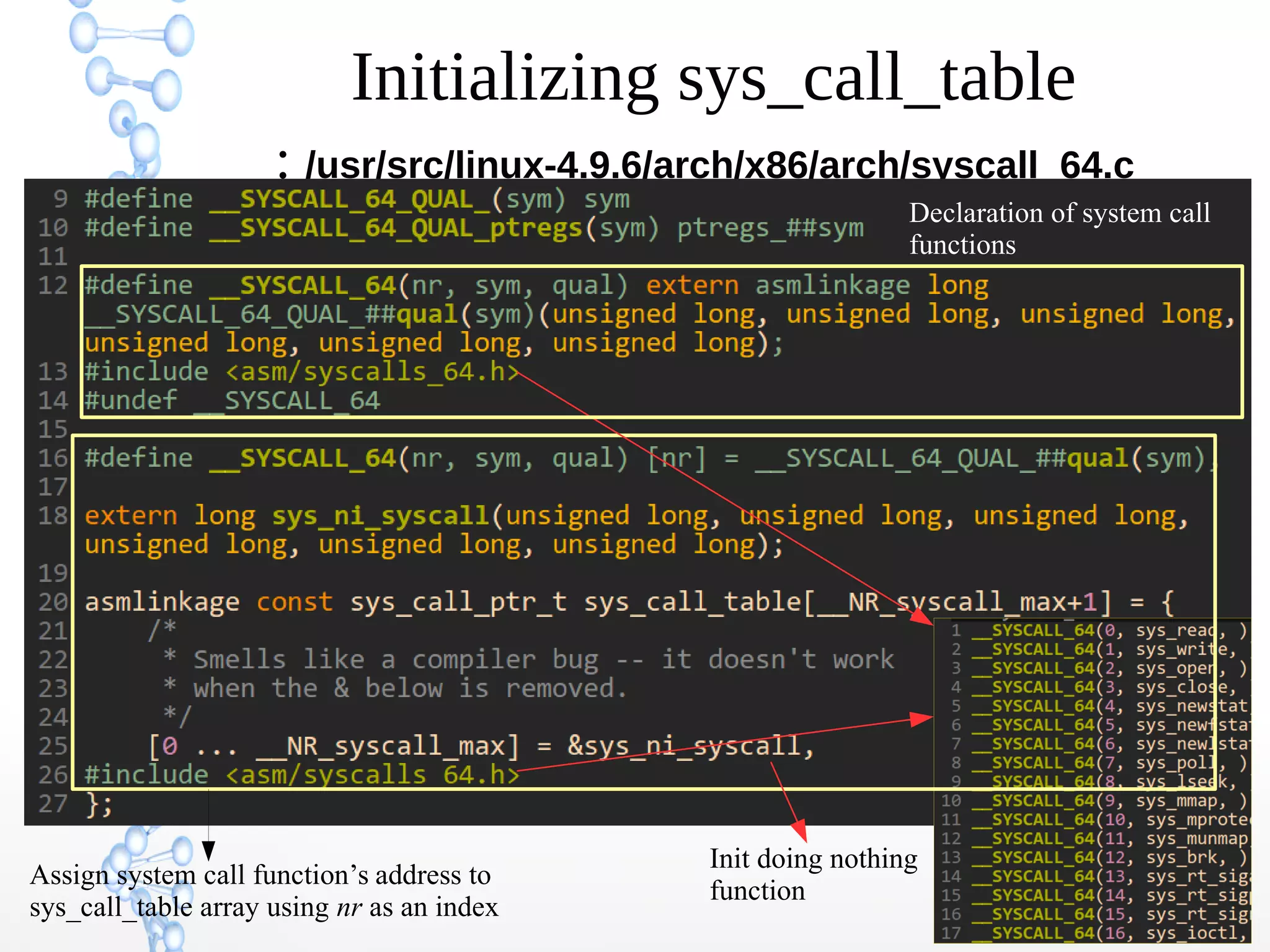
The document discusses trap handling in Linux, focusing on system calls. It begins with background on interrupts, traps, and system calls. It then describes the function call flow from start_kernel() and initialization of the Interrupt Descriptor Table (IDT). Next, it covers system call entry and initialization of the system call table. Finally, it discusses the system call procedure from a user application using glibc and the Linux kernel. Key topics include IDT structure and gates, MSR register usage for system calls, fast vs slow system call paths, and how system calls are invoked and handled in the kernel.





![45
Designated Initializers
Standard C90 requires the elements of an initializer to appear in a fixed order,
the same as the order of the elements in the array or structure being initialized.
In ISO C99 you can give the elements in any order, specifying the array
indices or structure field names they apply to, ...
To specify an array index, write ‘[index] =’ before the element value. For
example,
int a[6] = { [4] = 29, [2] = 15 };
is equivalent to
int a[6] = { 0, 0, 15, 0, 29, 0 };
To initialize a range of elements to the same value, write ‘[first ... last] =
value’. This is a GNU extension. For example,
int widths[] = { [0 ... 9] = 1, [10 ... 99] = 2,
[100] = 3 };
Source : https://gcc.gnu.org/onlinedocs/gcc/Designated-Inits.html](https://image.slidesharecdn.com/techsem-trap-handling-in-linux-190724160509/75/Trap-Handling-in-Linux-45-2048.jpg)
![46
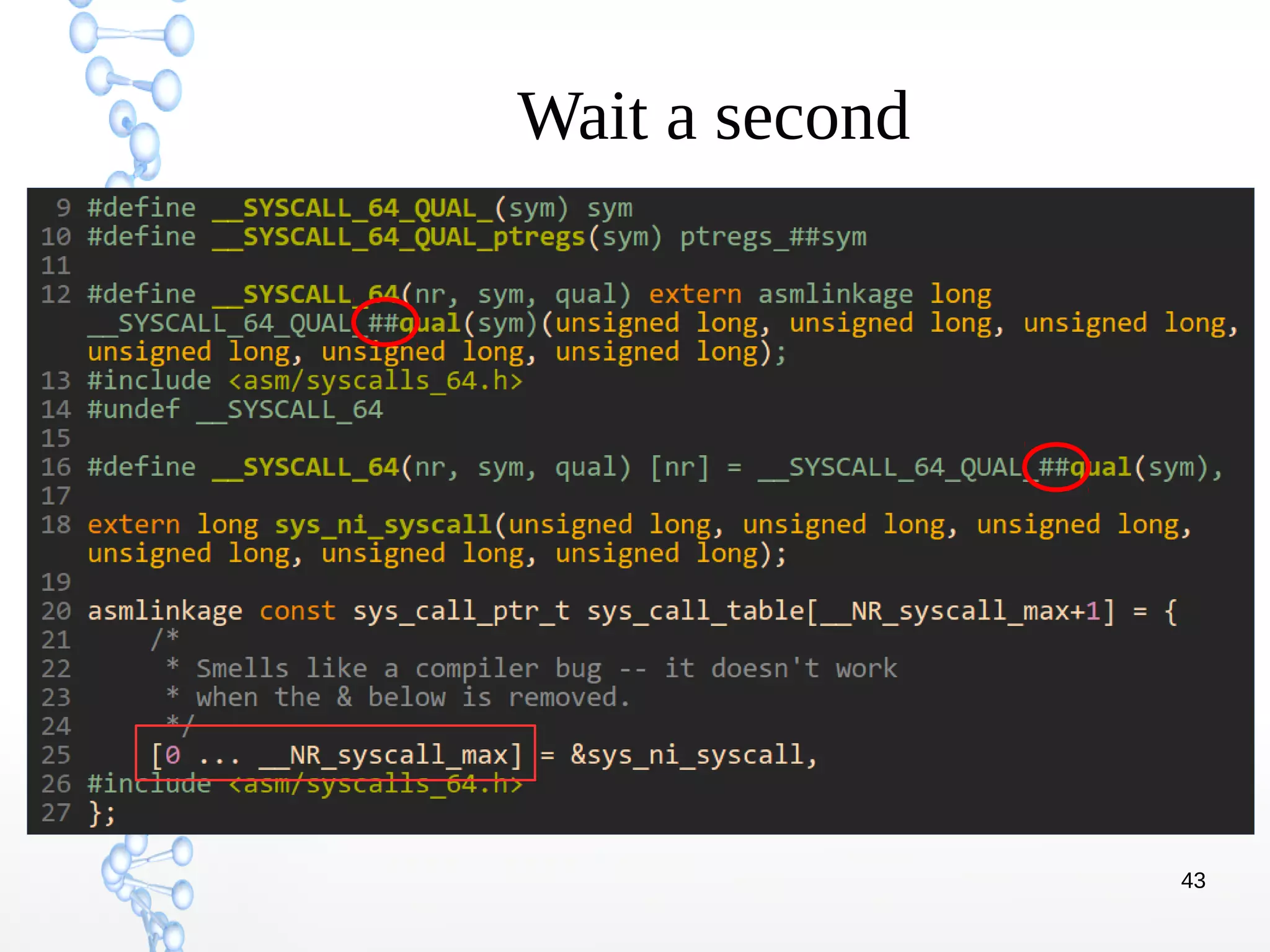
C Preprocessor’s #, ## Macro
#define STRING(x) #x means “x” : stringfy x by “x”
#define X(n) x##n means xn : concatenation with x and n
So let me roll down initialization code of sys_call_table array
For example, index 0
→
[0] = __SYSCALL_64_QUAL_##qual(sys_read)
= __SYSCALL_64_QUAL_(sys_read) : (## is concatenation
and qual is empty)
= sys_read](https://image.slidesharecdn.com/techsem-trap-handling-in-linux-190724160509/75/Trap-Handling-in-Linux-46-2048.jpg)