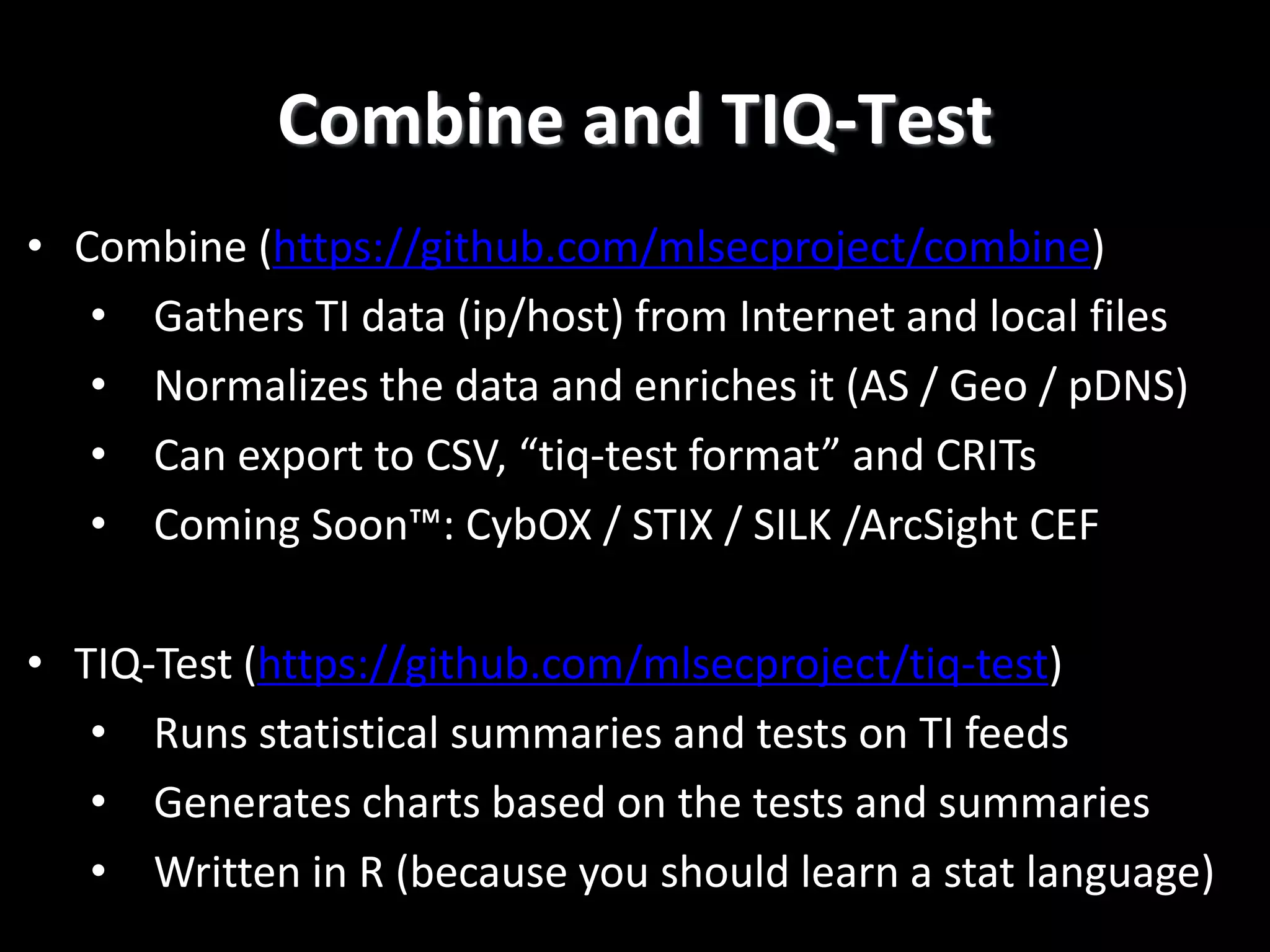
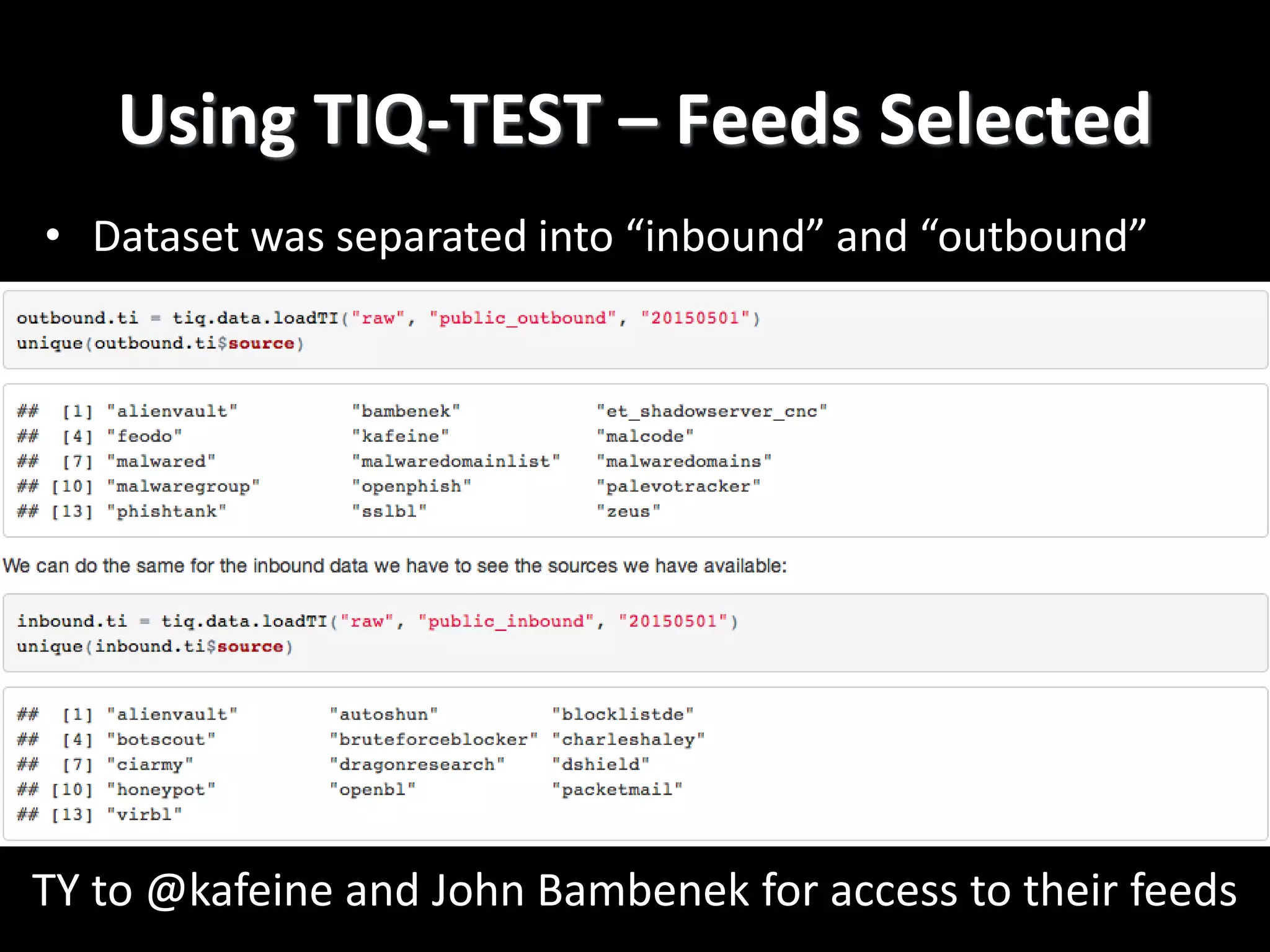
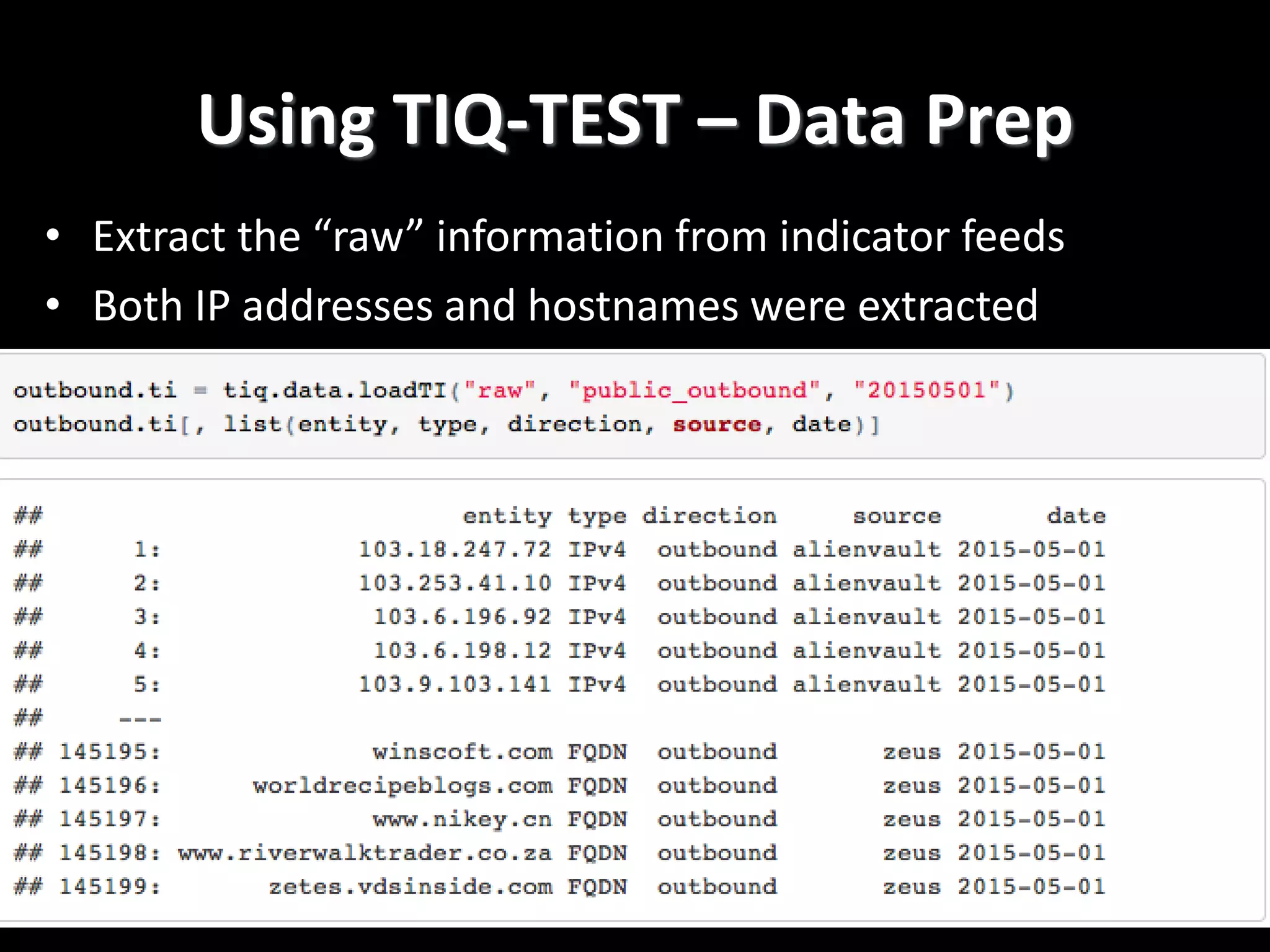
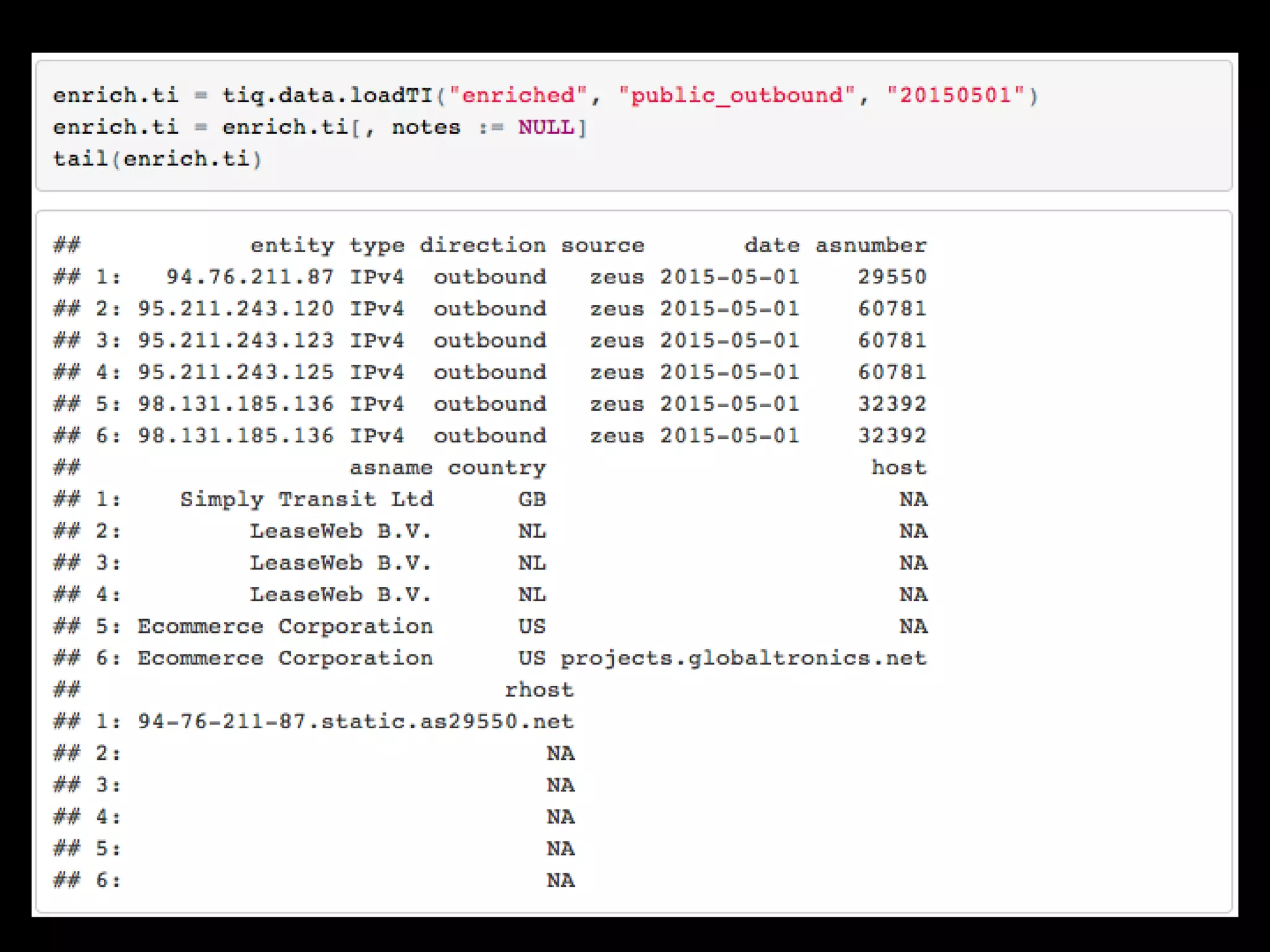
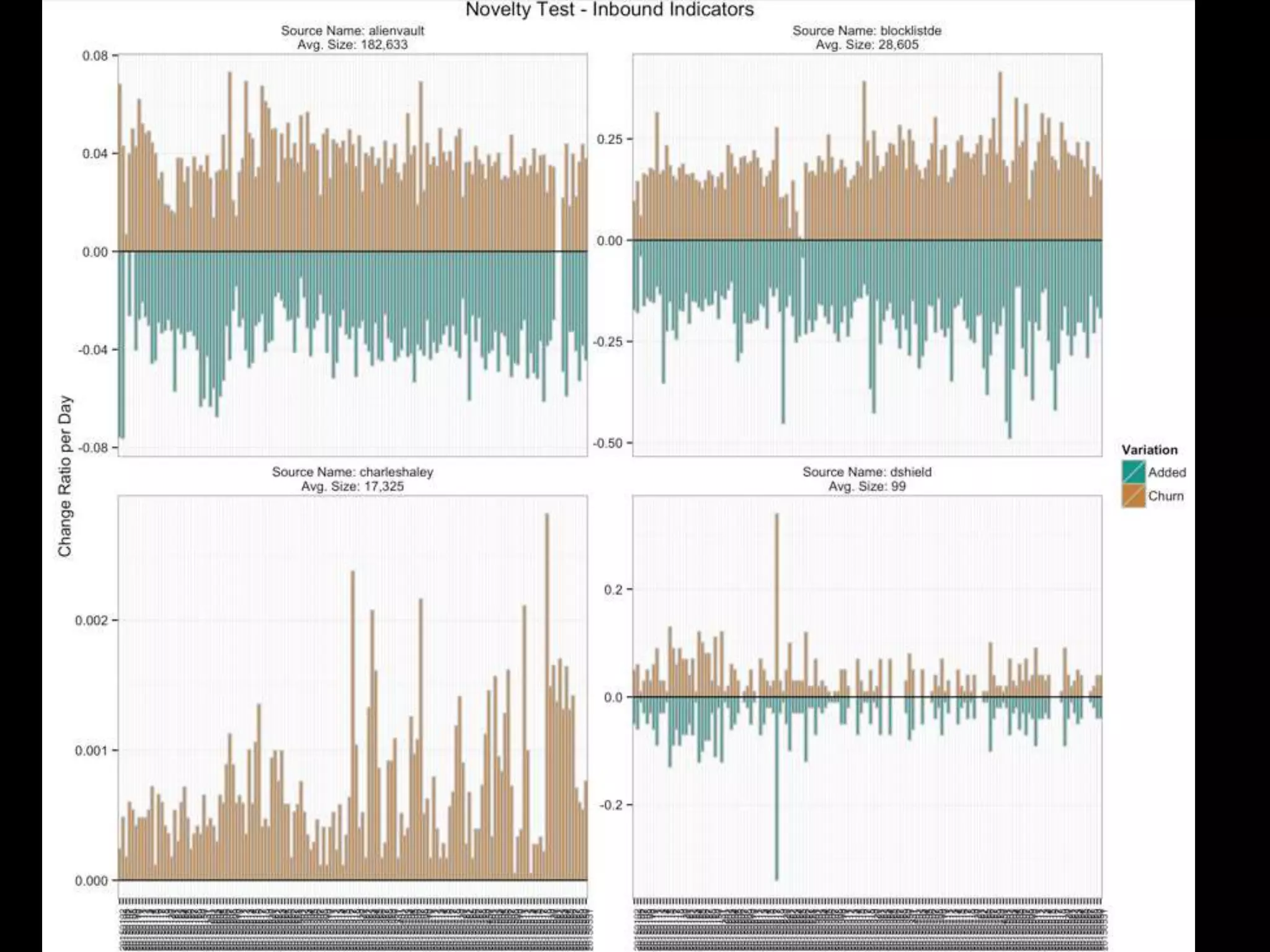
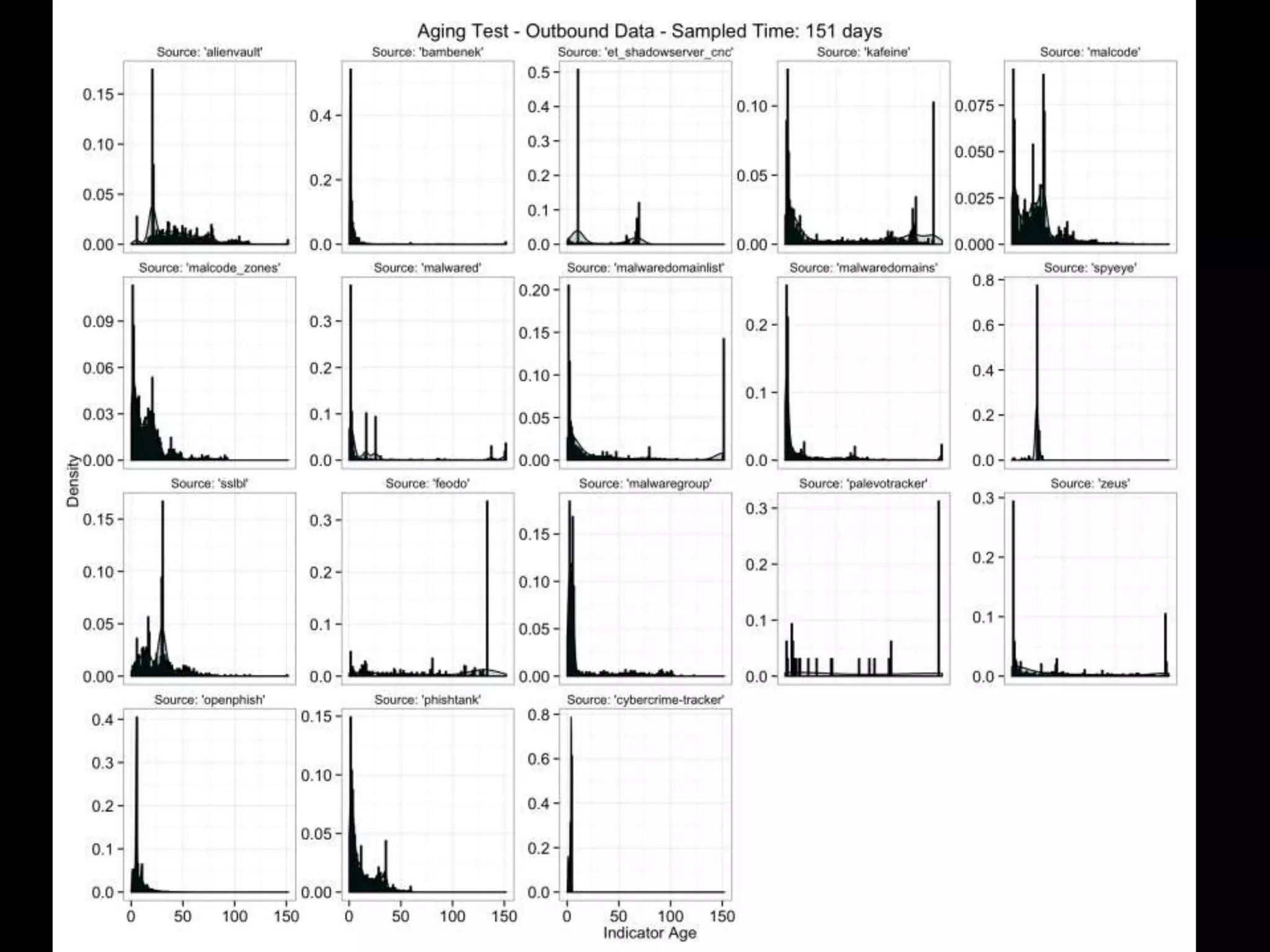
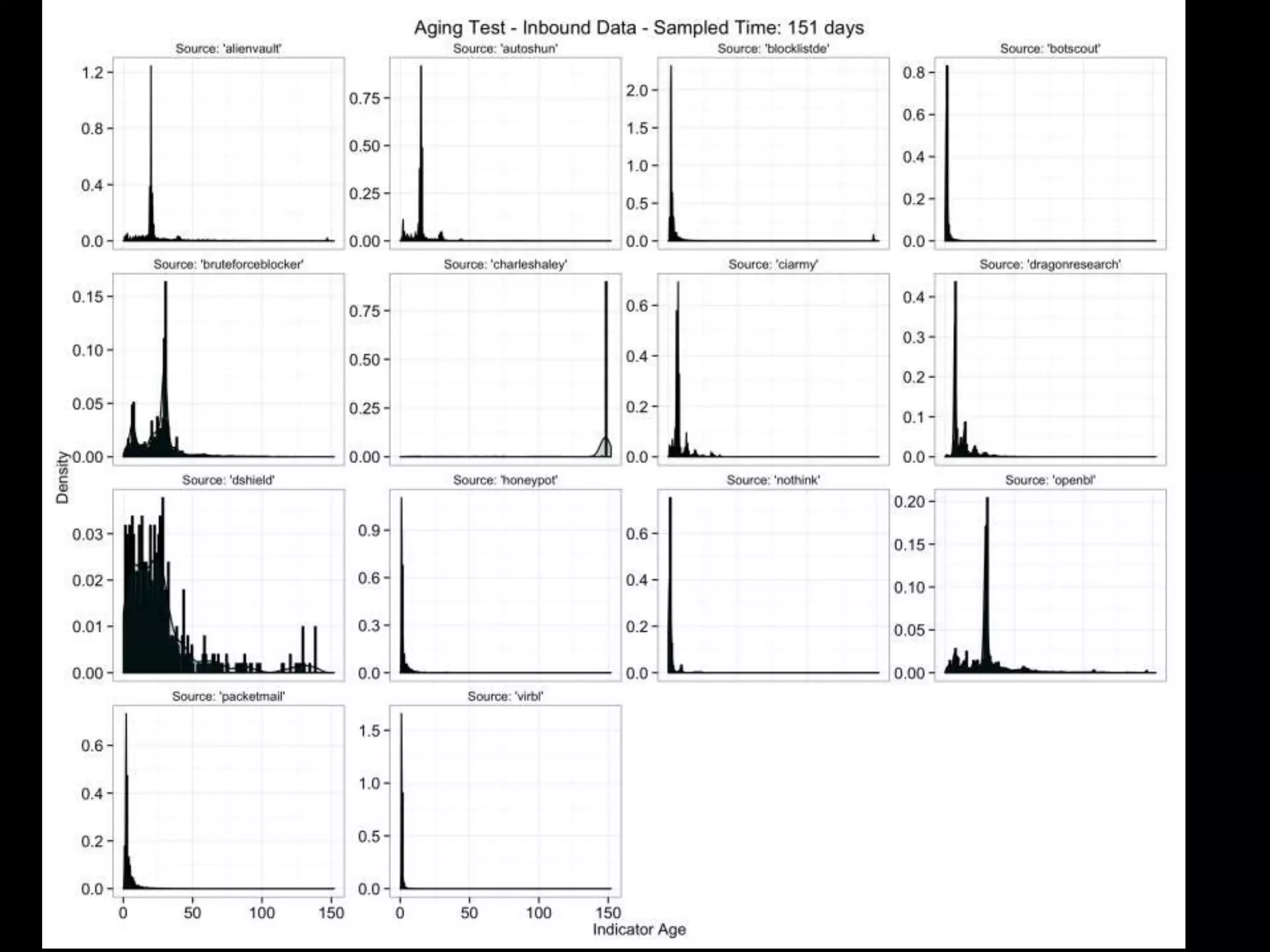
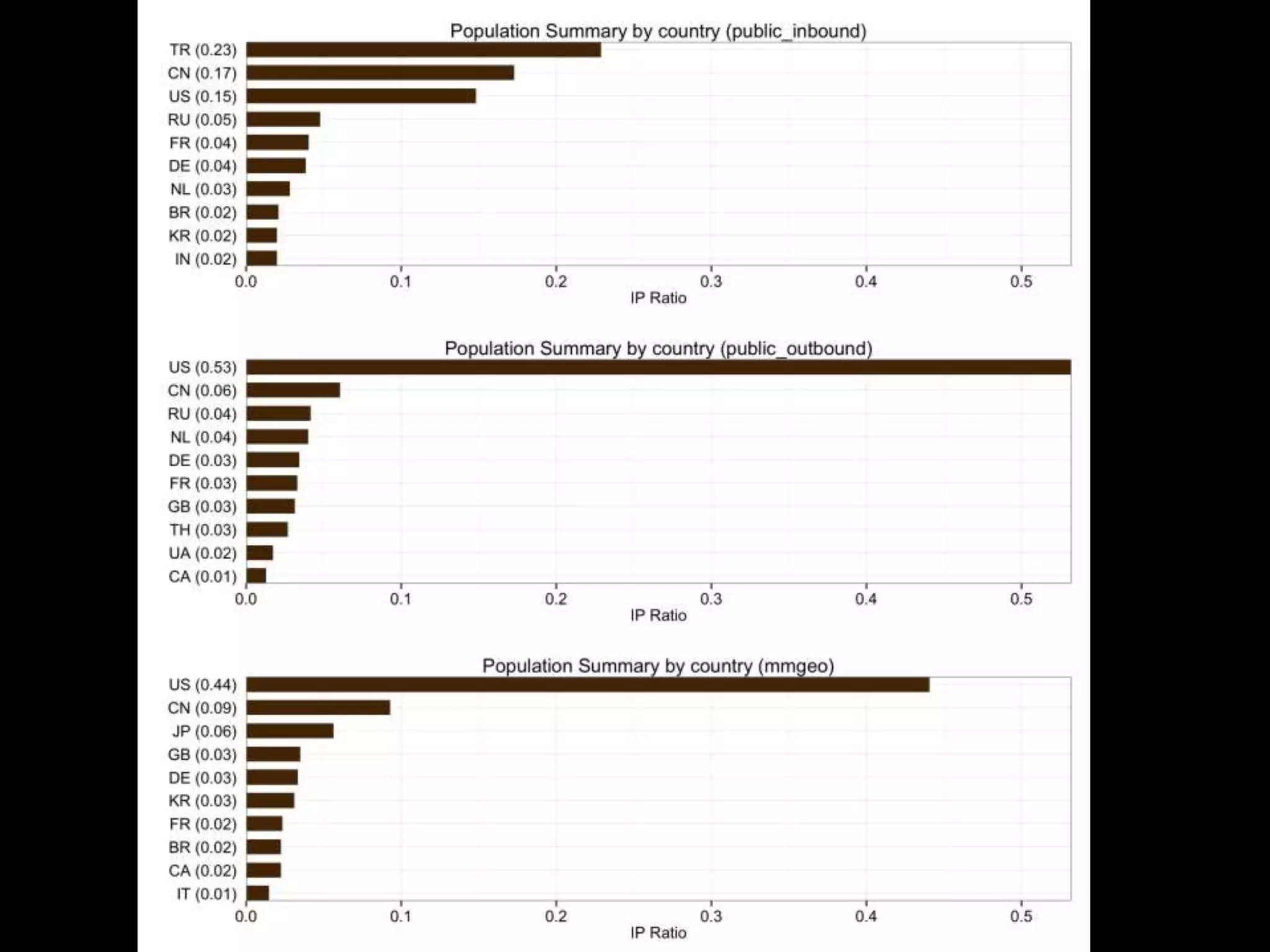
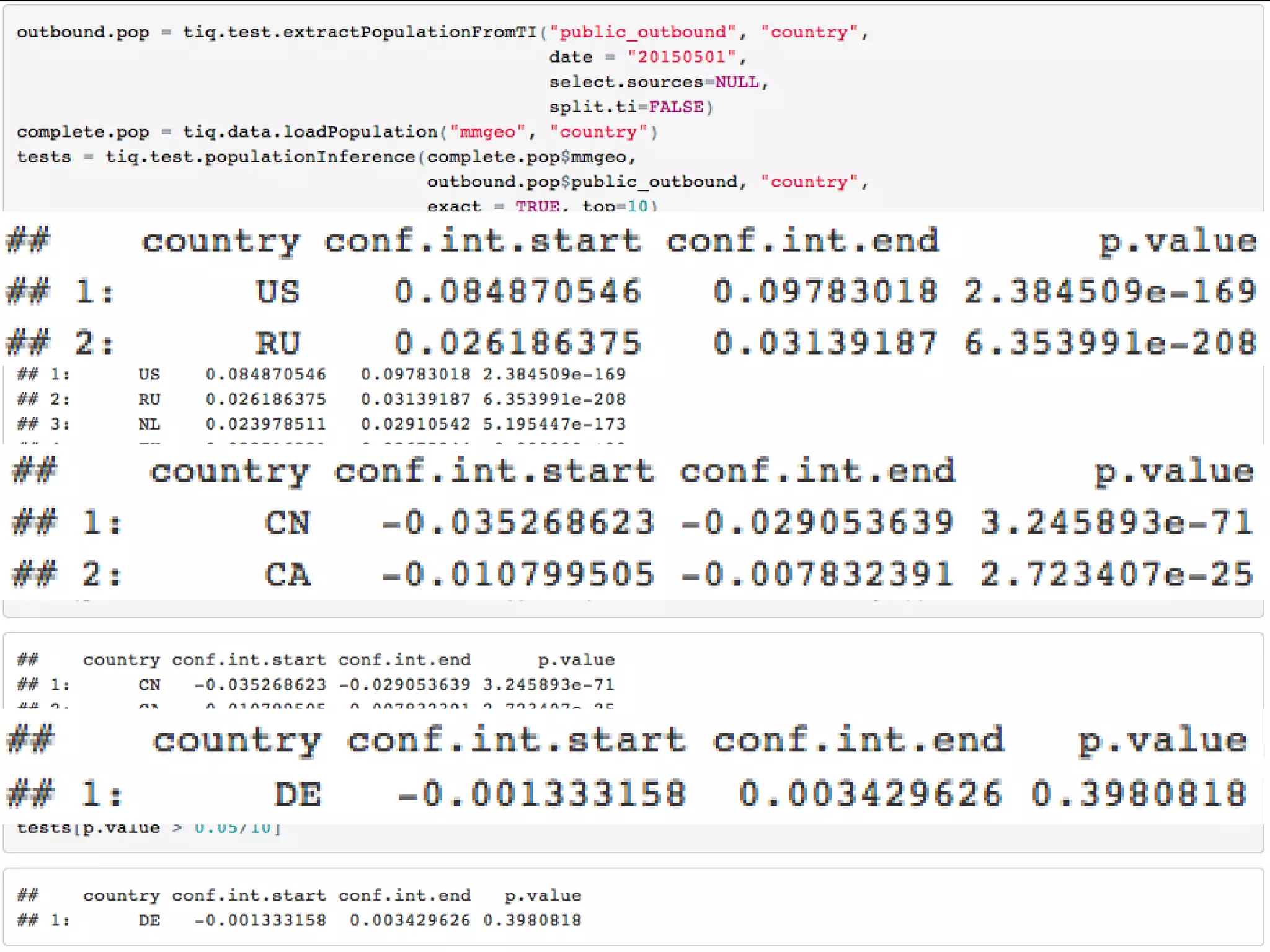
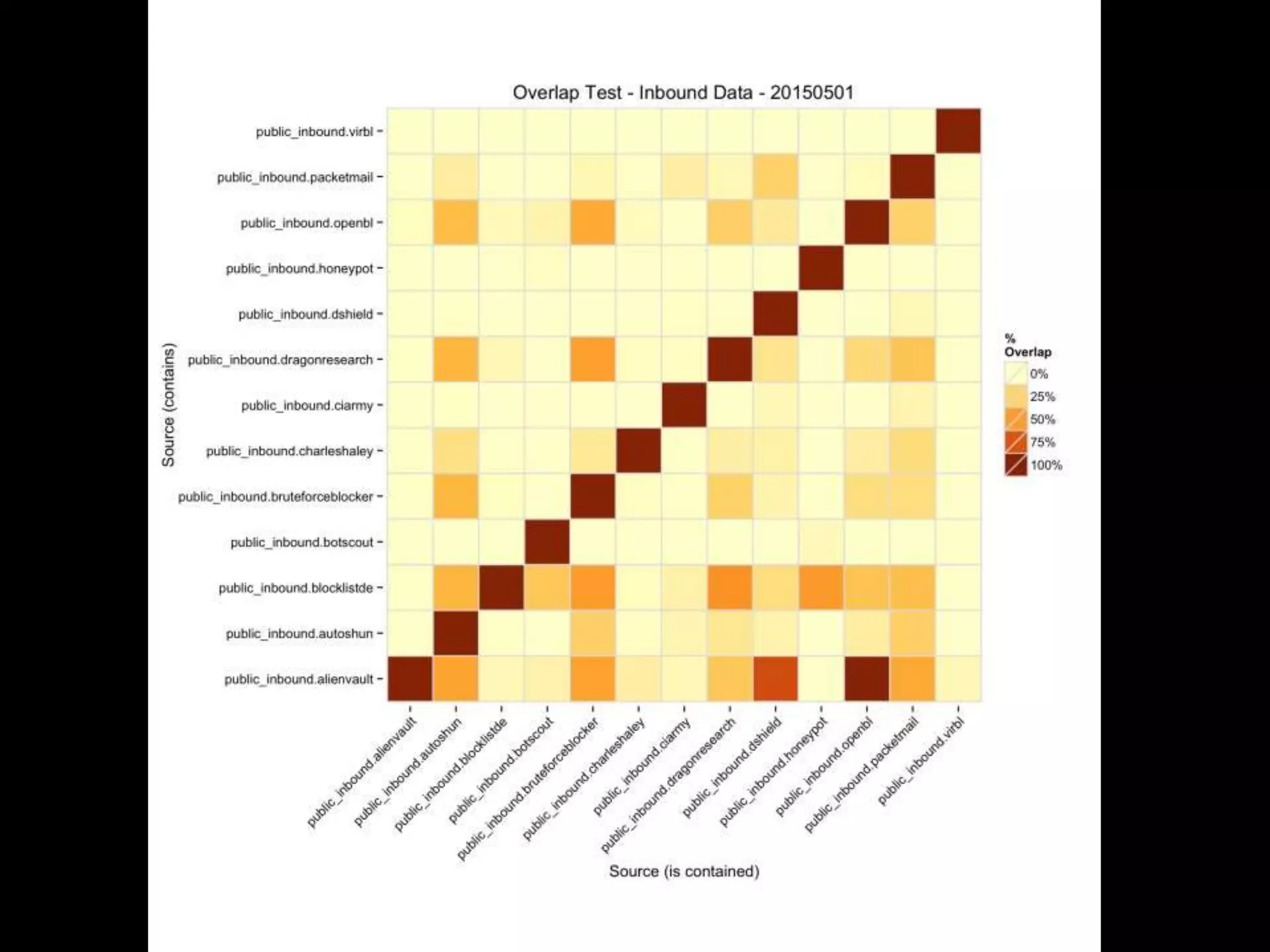
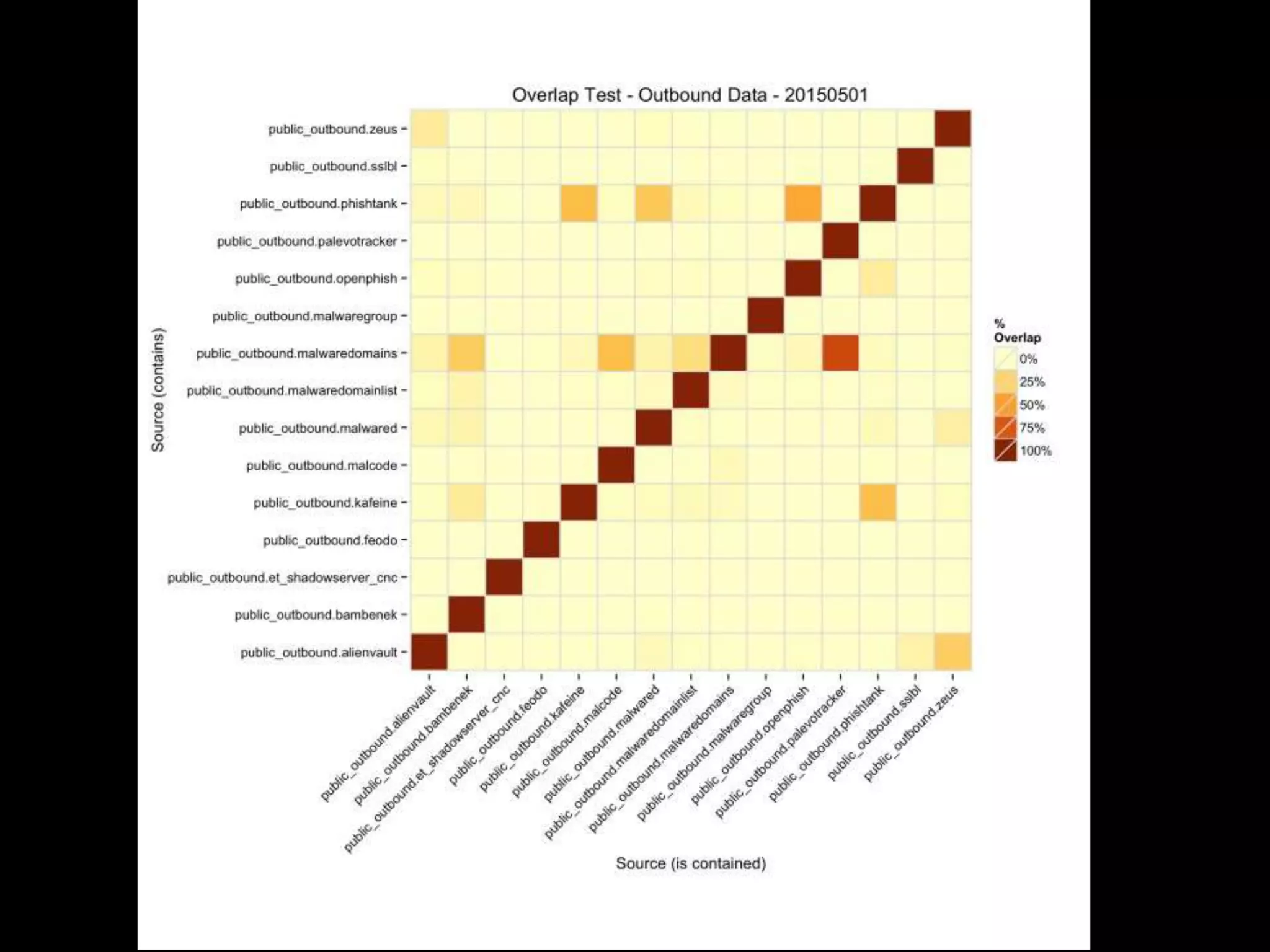
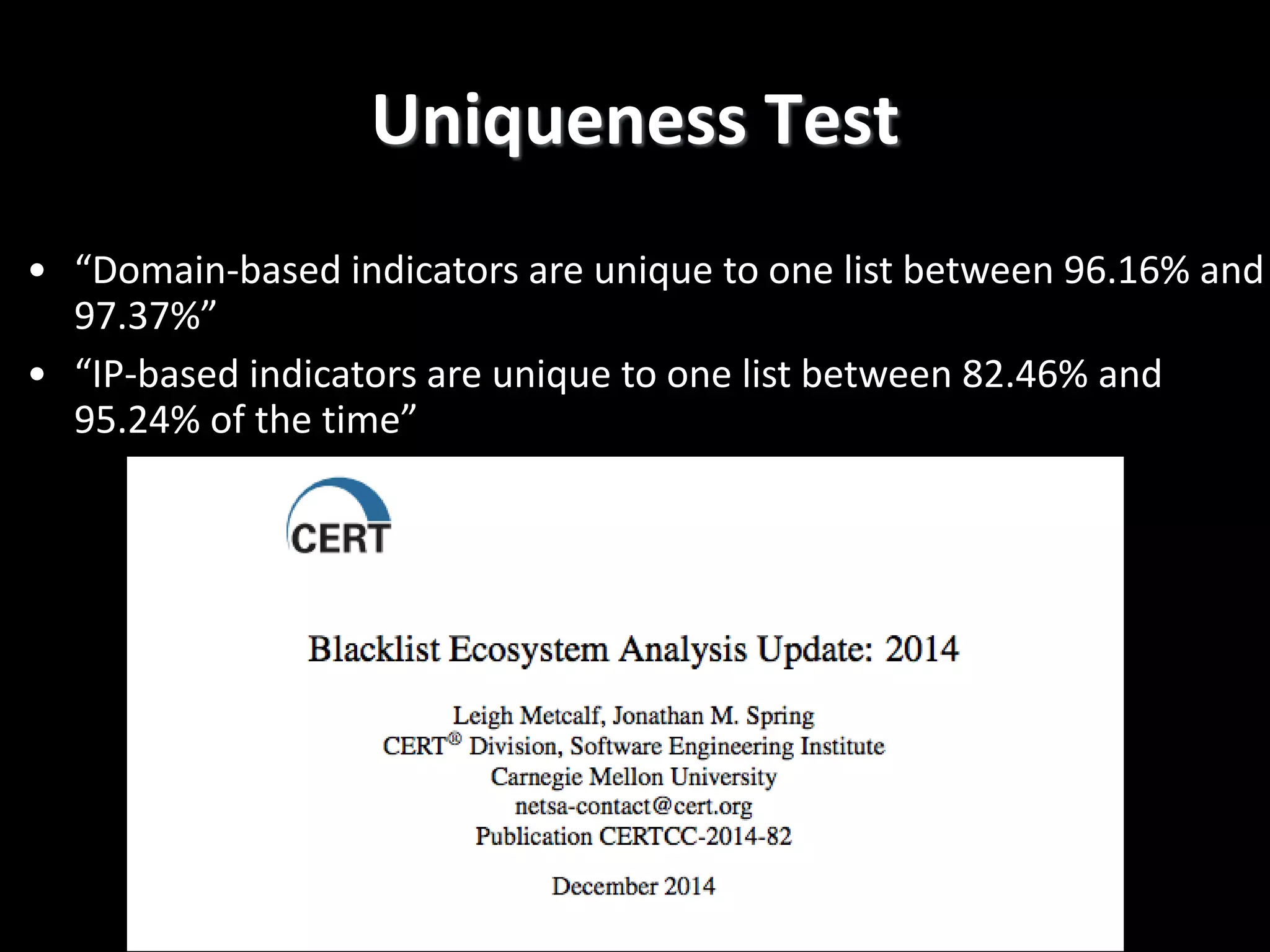
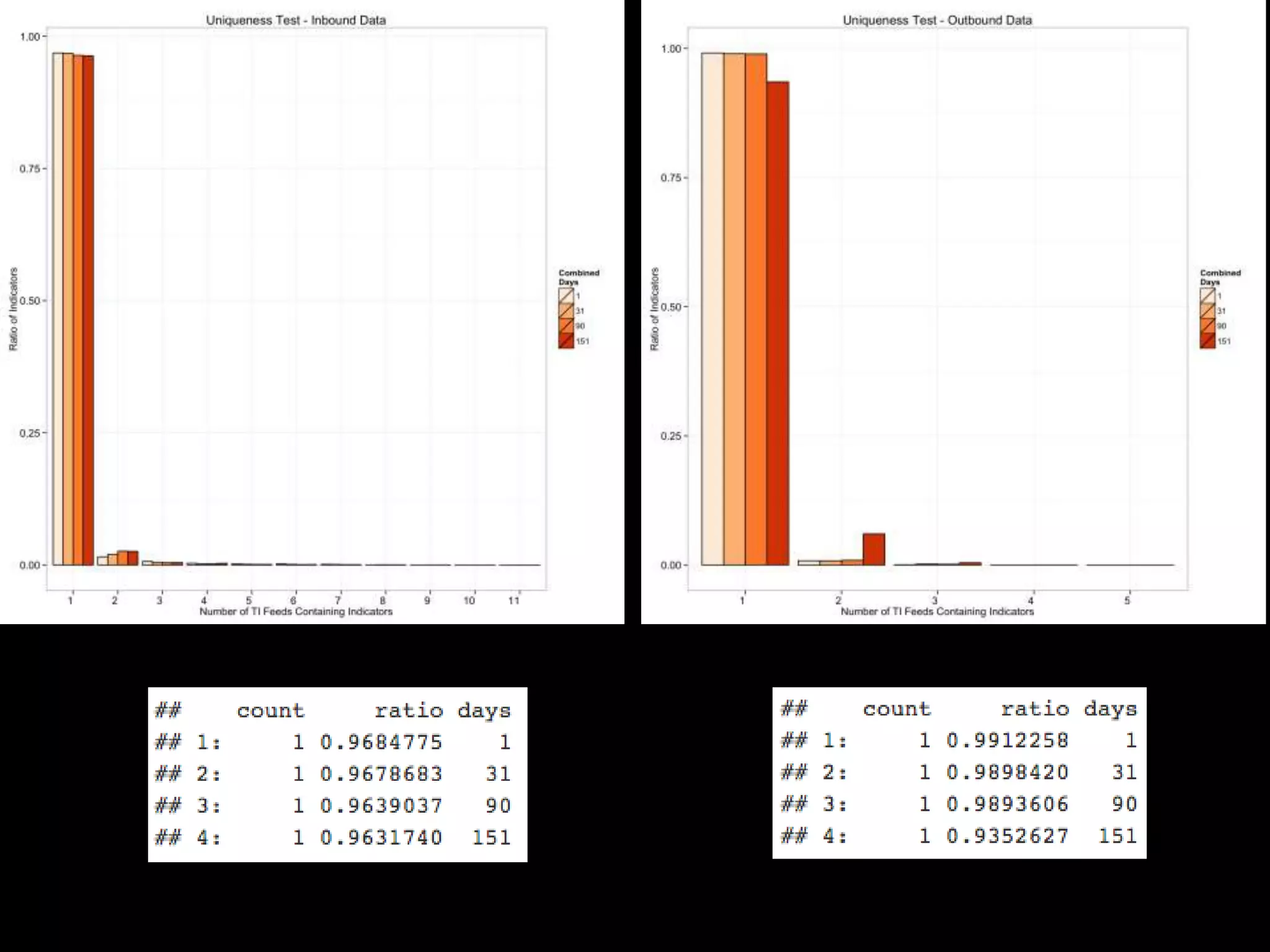
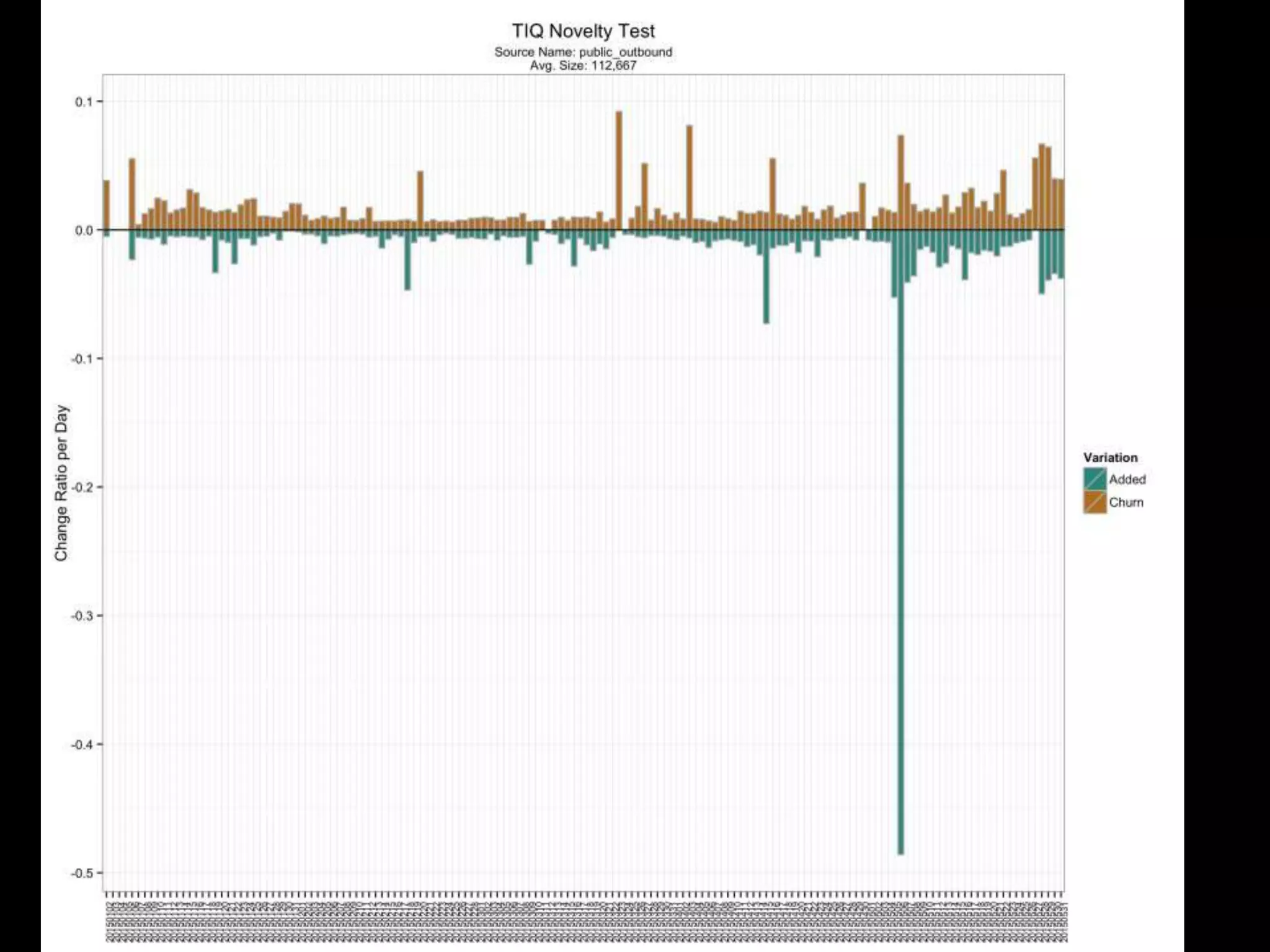
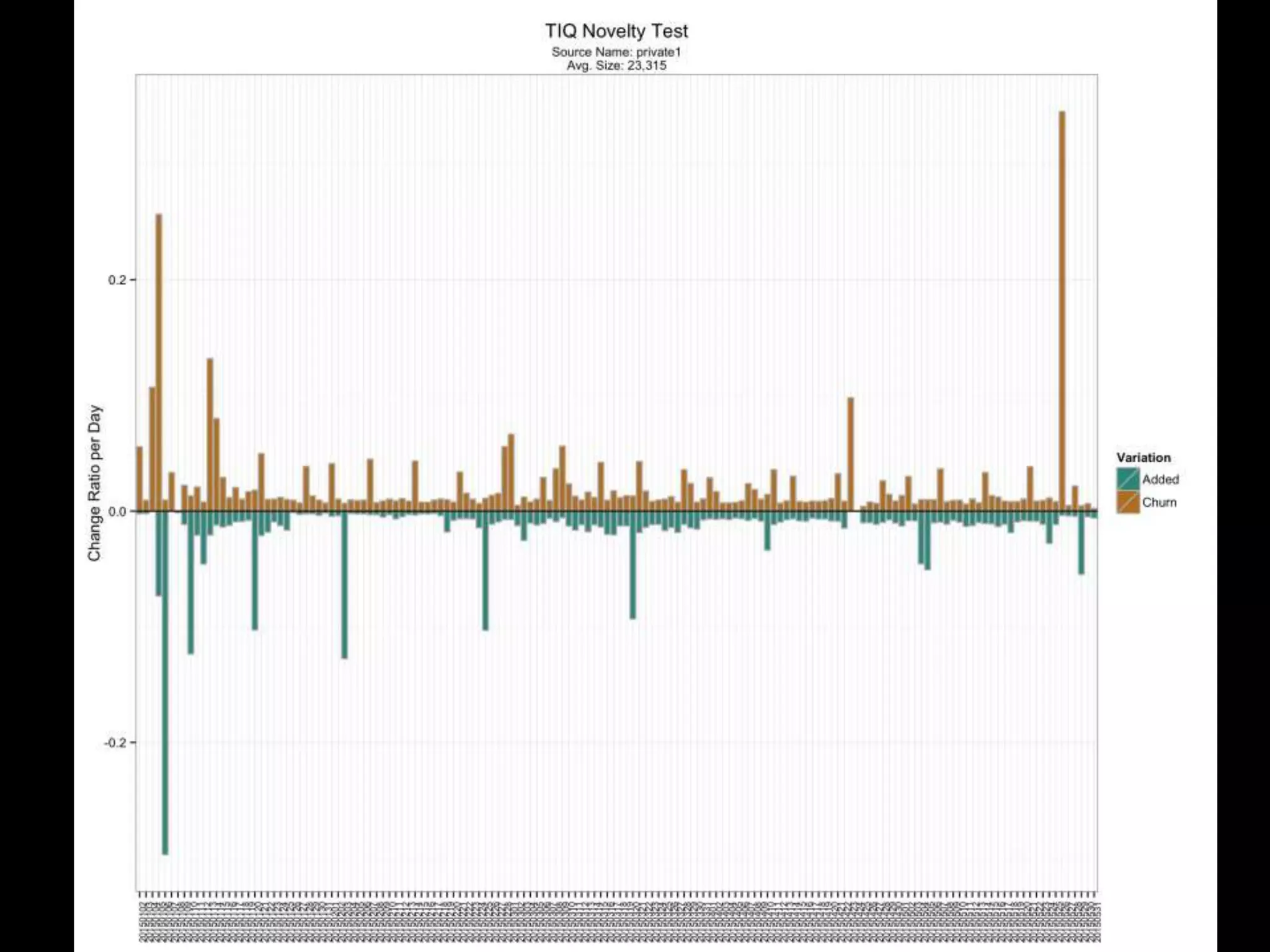
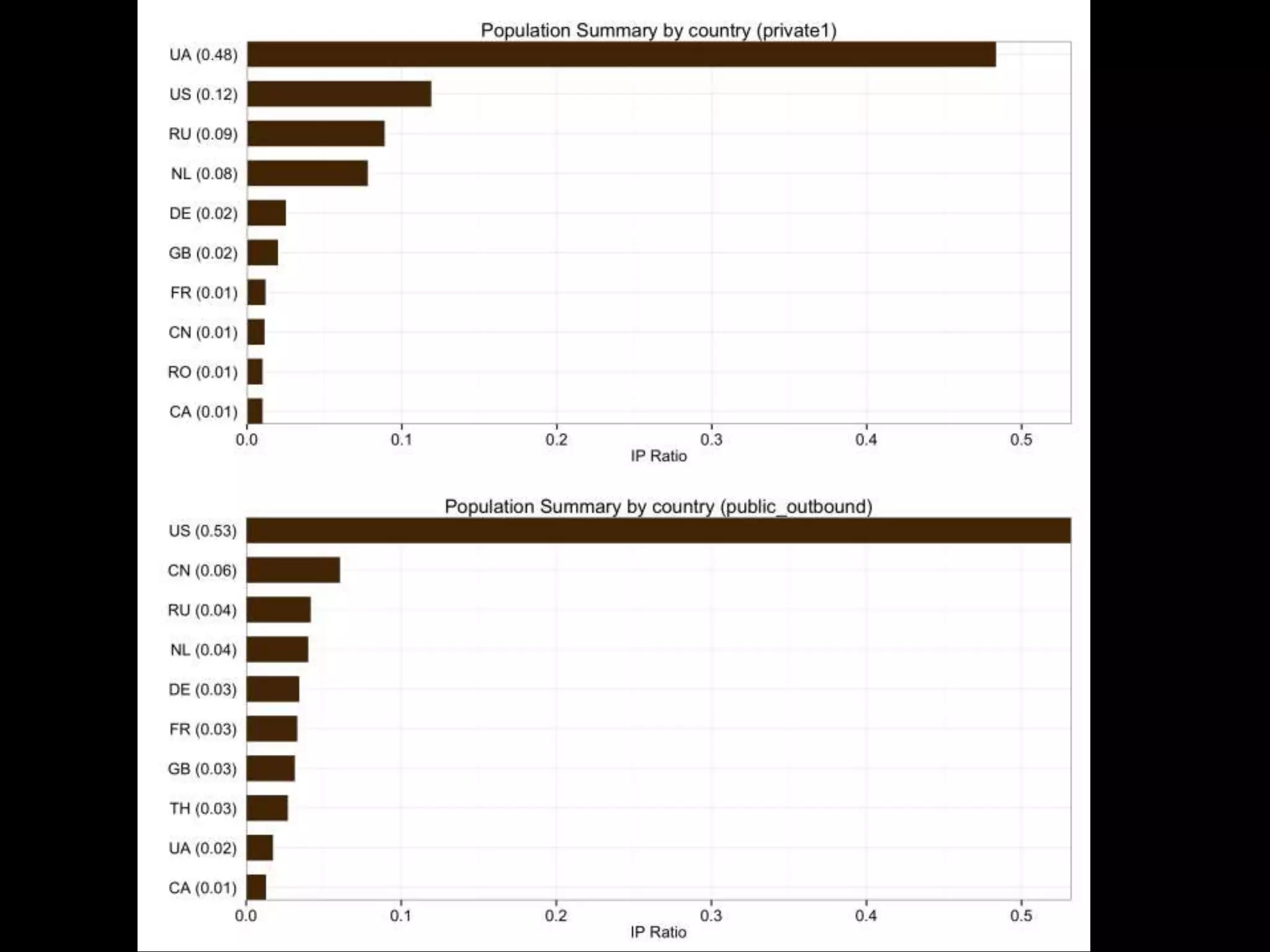
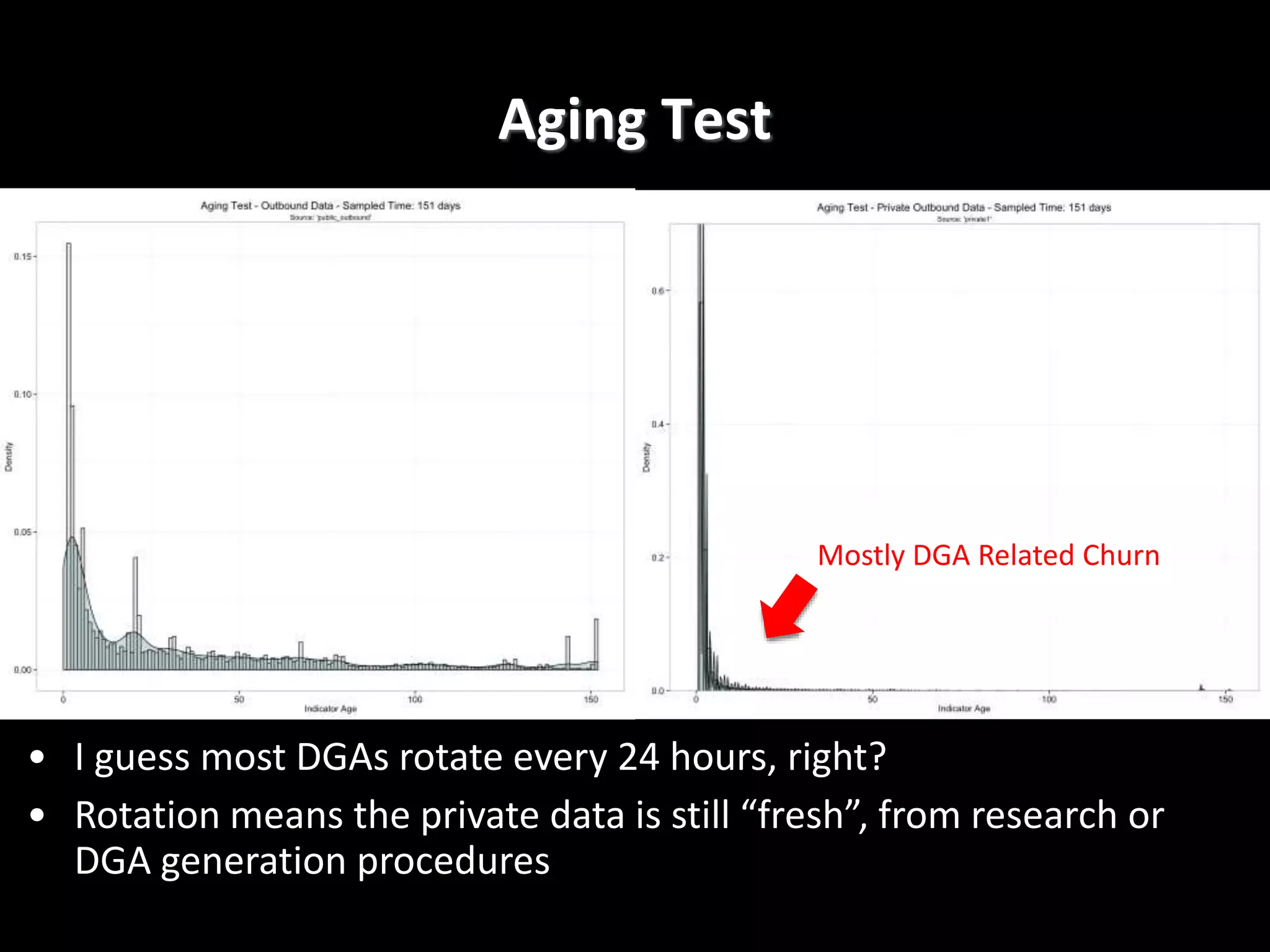
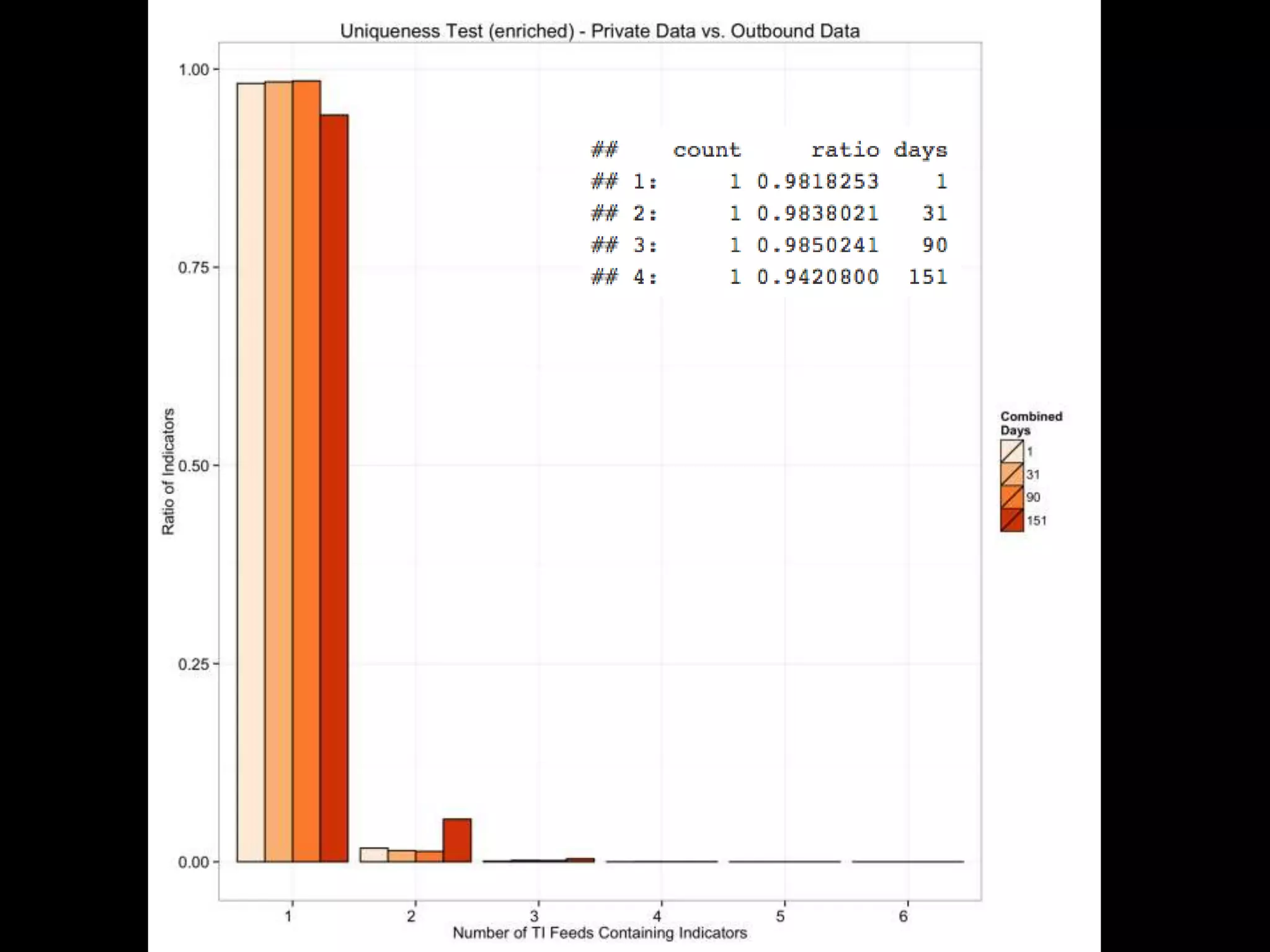
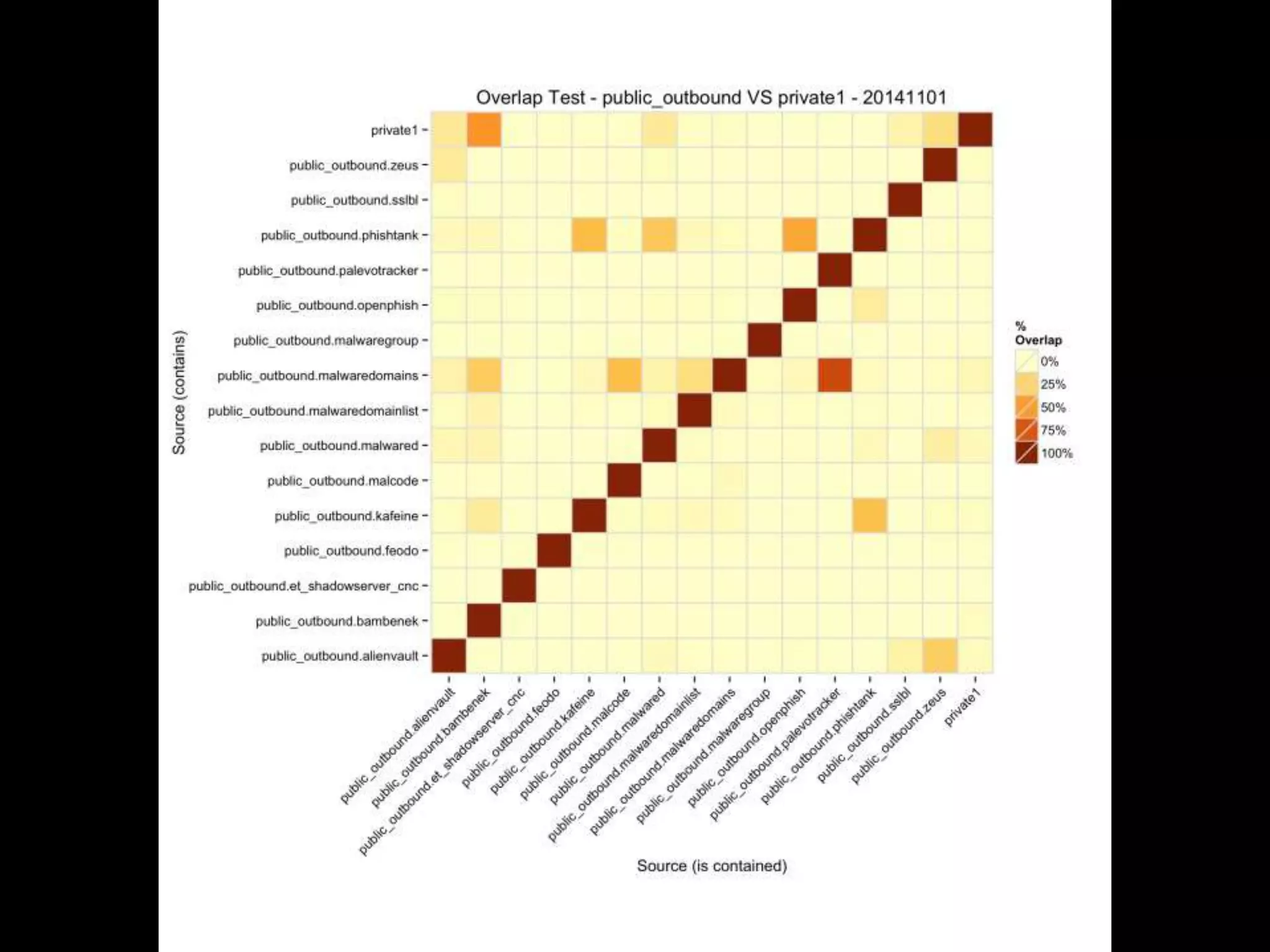
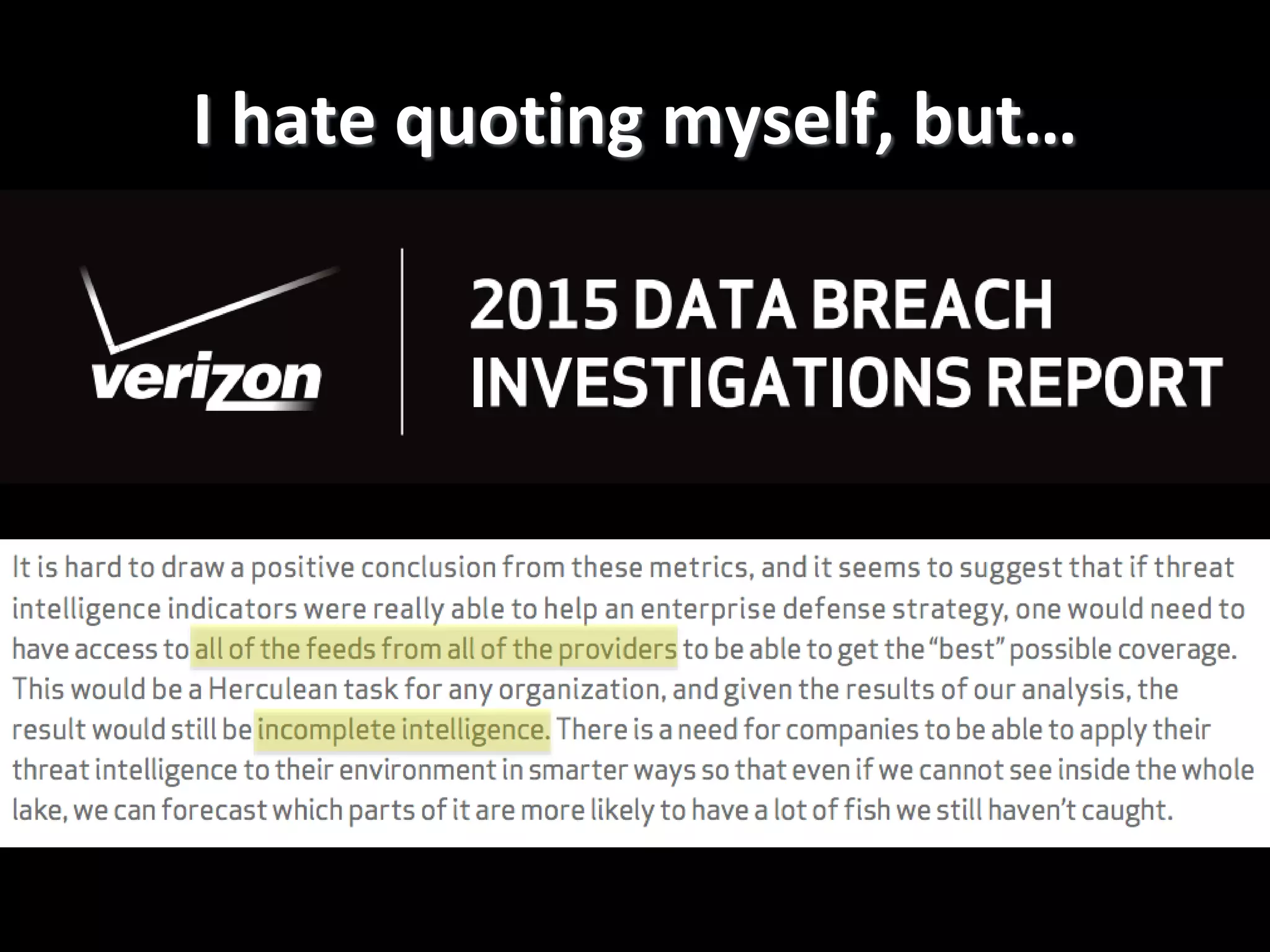
The document discusses data-driven threat intelligence methods and tools developed by the MLSec project and Niddel, emphasizing the importance of validating threat intelligence feeds through statistical analysis using tools like 'tiq-test'. It also highlights the significance of accurately measuring and comparing threat indicators to derive actionable insights for cybersecurity defense. Future research directions include enhancing threat intelligence sharing and improving data analysis methods.