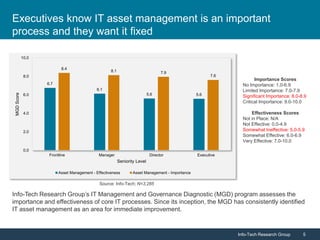
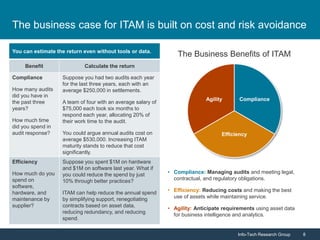
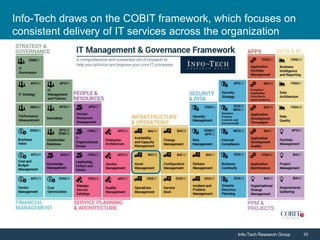
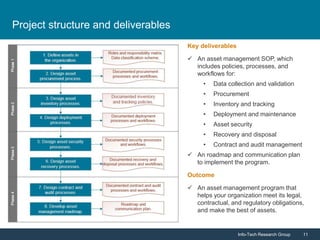
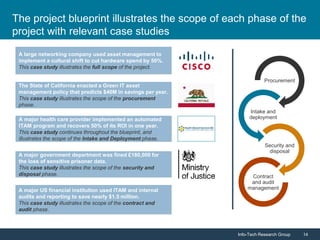
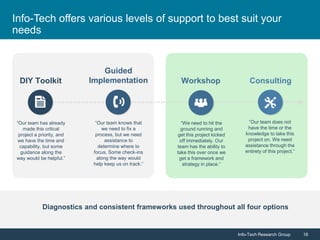
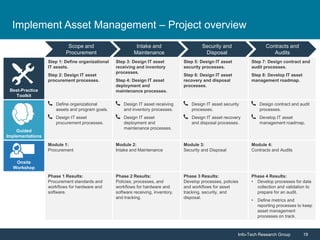
Info-Tech Research Group emphasizes the importance of IT asset management (ITAM) in reducing costs, improving security, and enhancing organizational efficiency. The document outlines steps for successful ITAM implementation, including defining procurement processes, managing asset security, and utilizing data for better business decisions. It highlights the proactive nature of ITAM as a dynamic process that requires continuous improvement and integration across an organization.