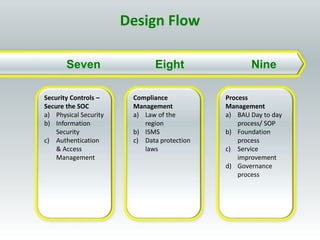
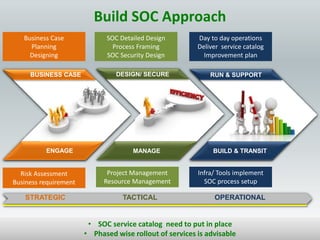
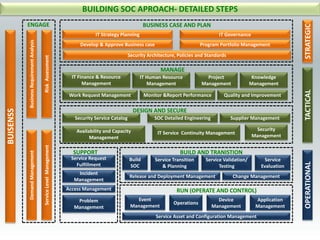
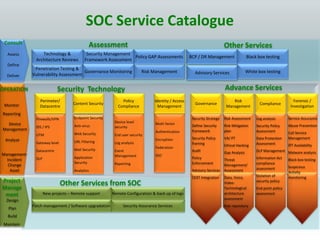
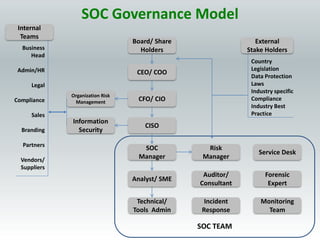
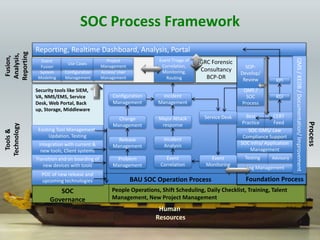
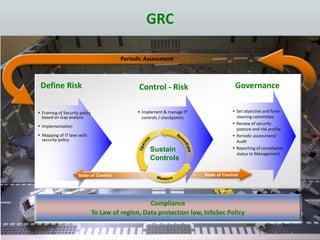
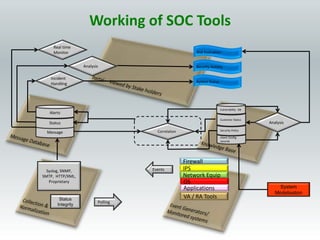
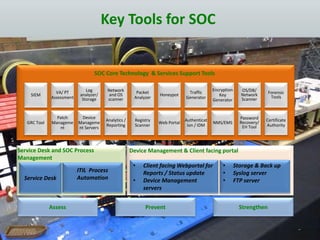
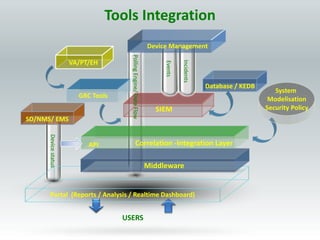
The document details the design and construction of a Security Operation Center (SOC), outlining its necessity, operational goals, core components, and the roles of personnel involved. It emphasizes achieving business alignment, cost reduction, and enhanced incident management through a centralized 24/7 operation. Additionally, it covers current trends and future innovations in SOCs including the integration of big data and proactive fraud prevention measures.