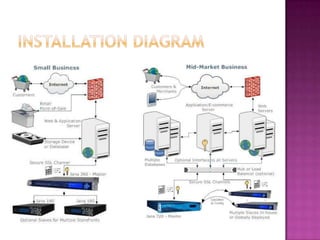
Encryption technology is important for healthcare organizations to protect patient health information. An appliance-based encryption solution like the JANA series can offer strong security while being simple to implement and manage. The JANA appliances encrypt data in transit and at rest using key management processes to ensure privacy and HIPAA compliance. They integrate easily into healthcare IT systems and scale from small practices to large networks.