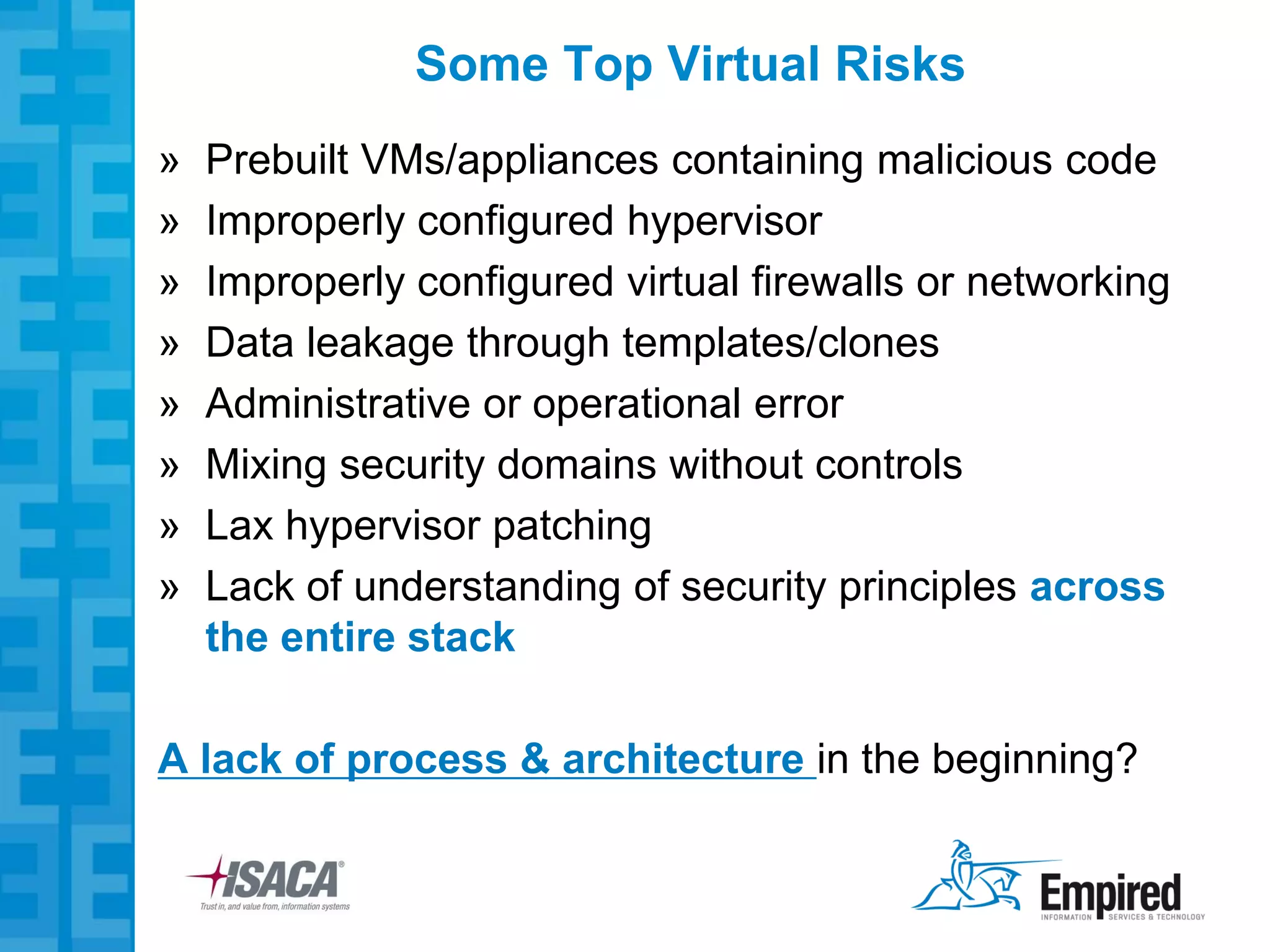
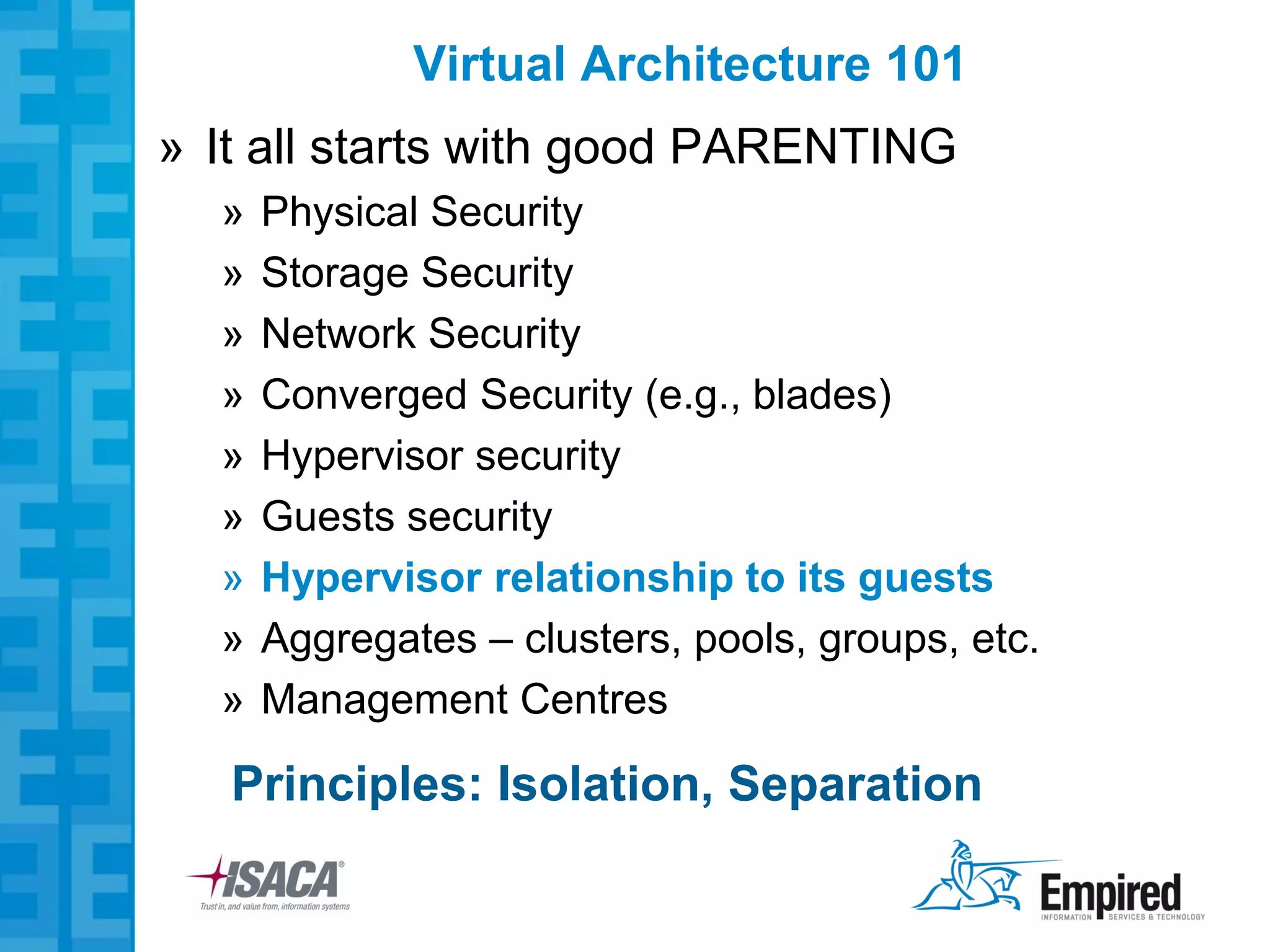
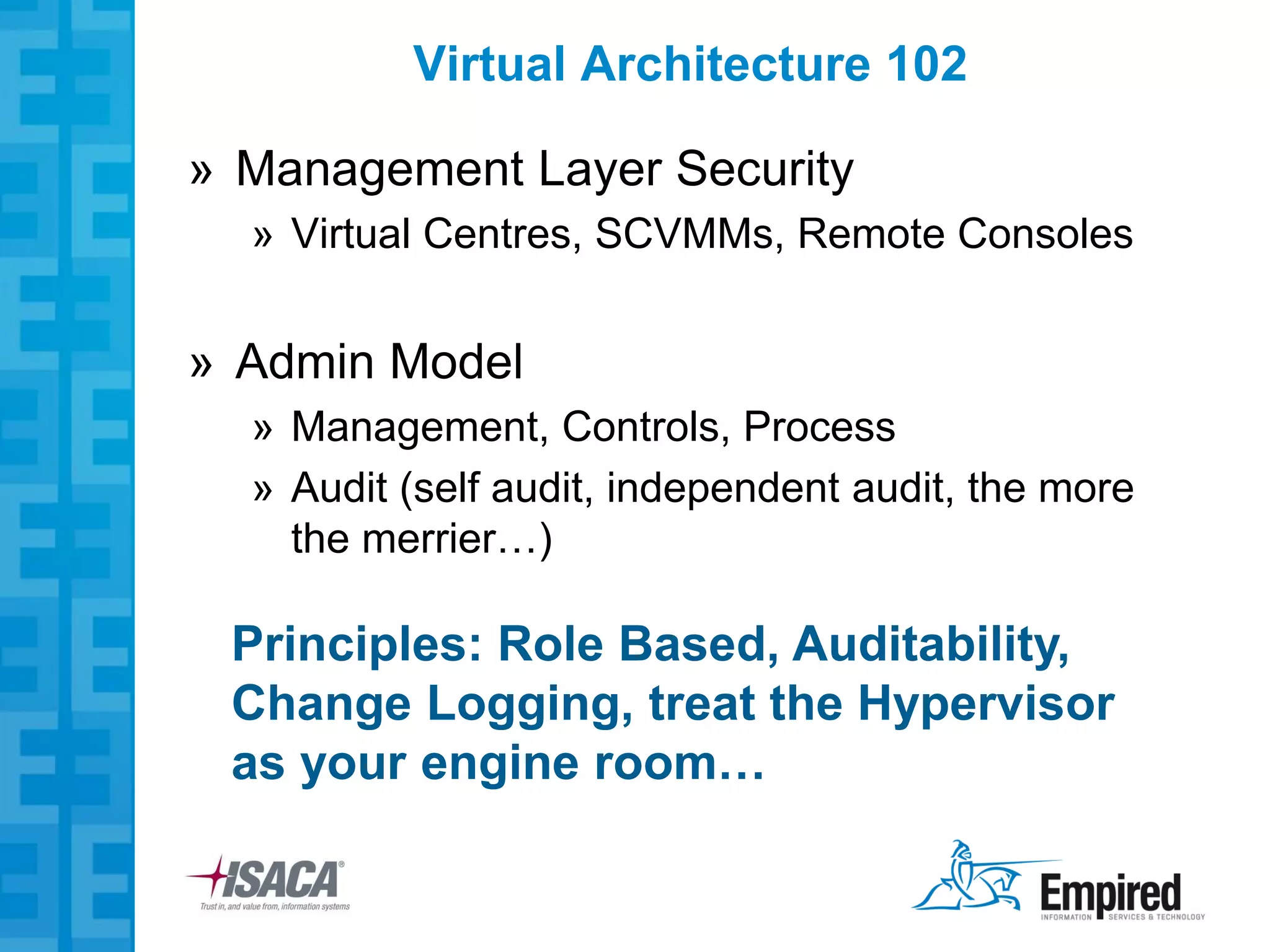
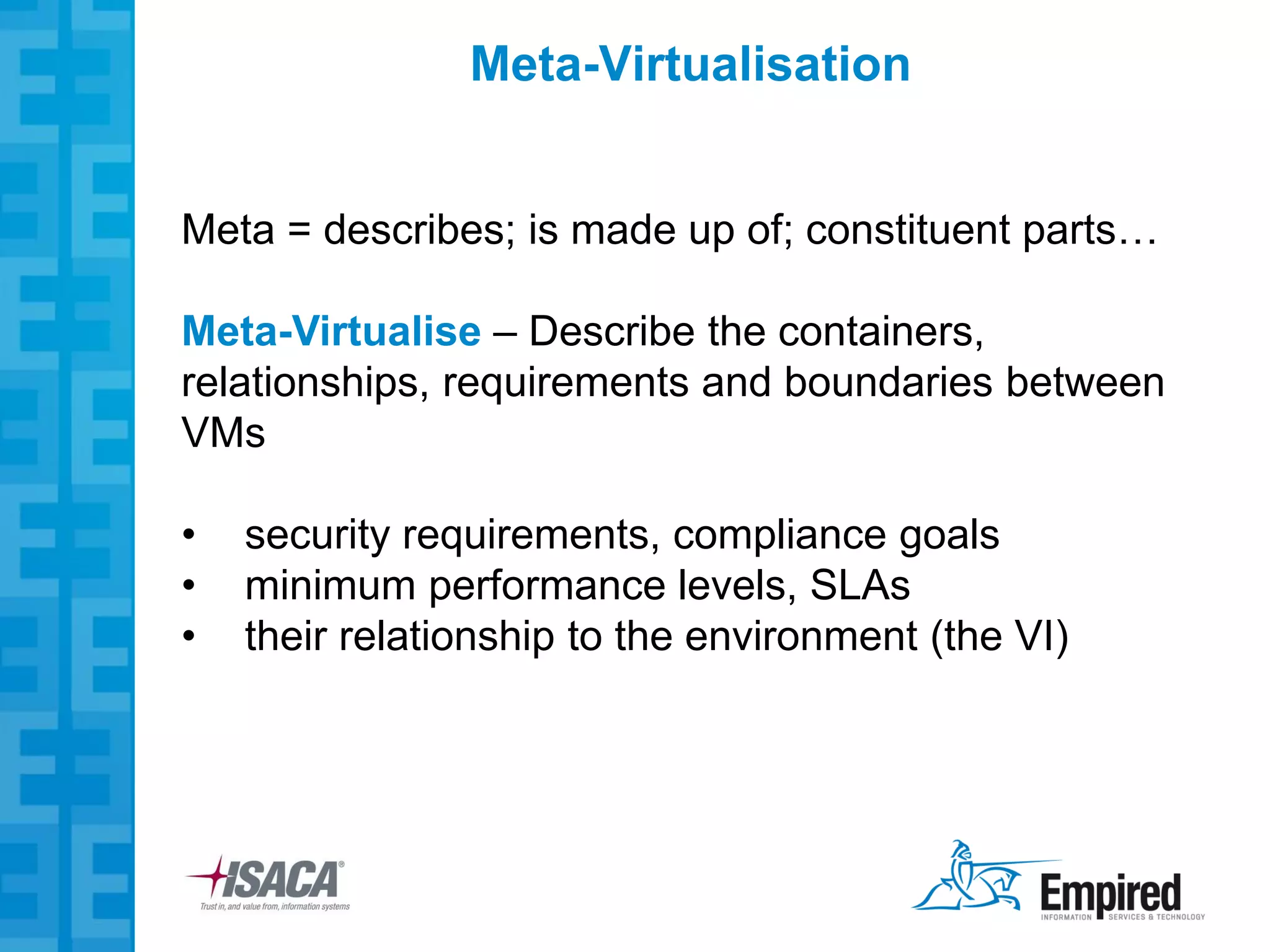
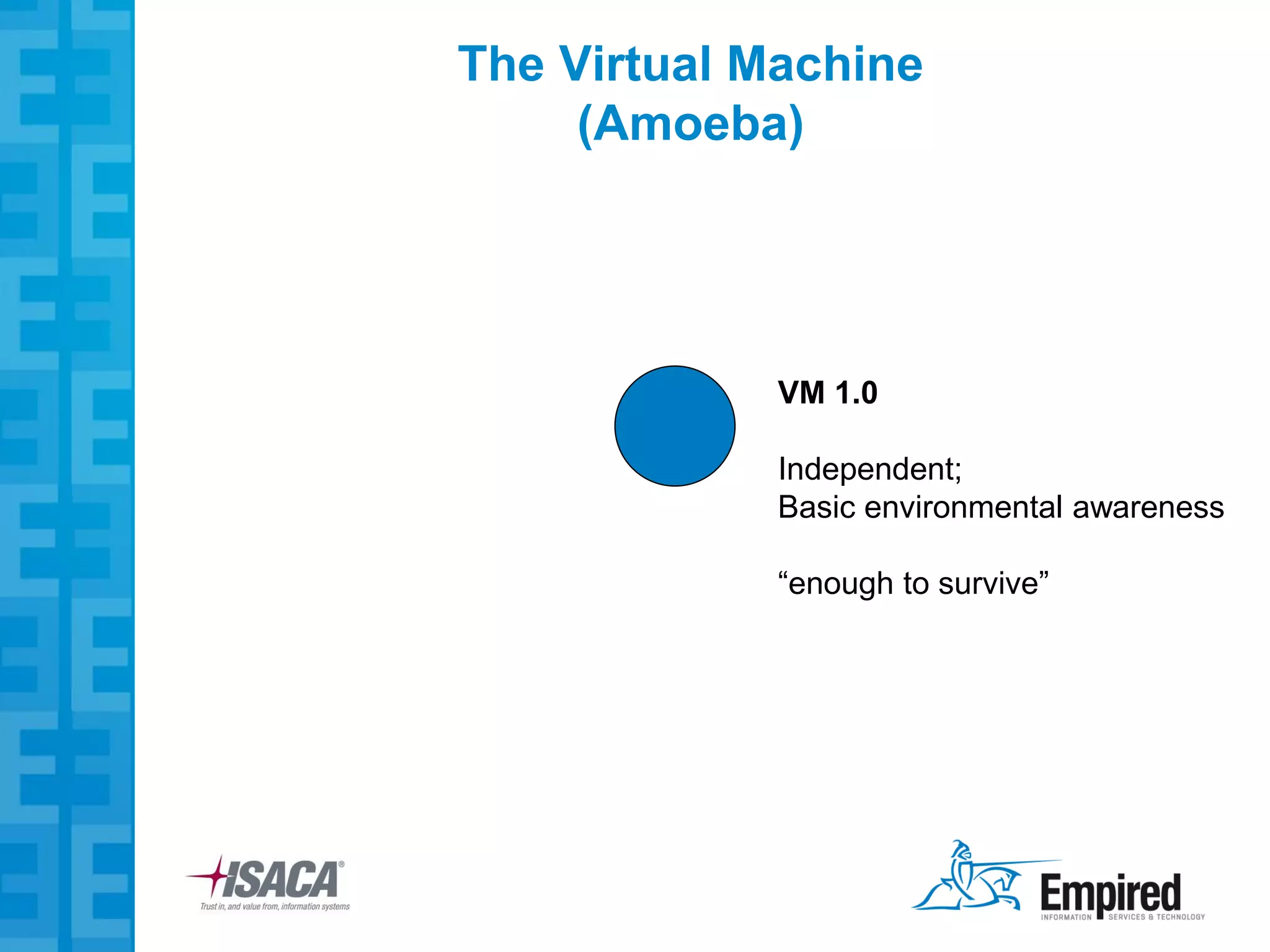
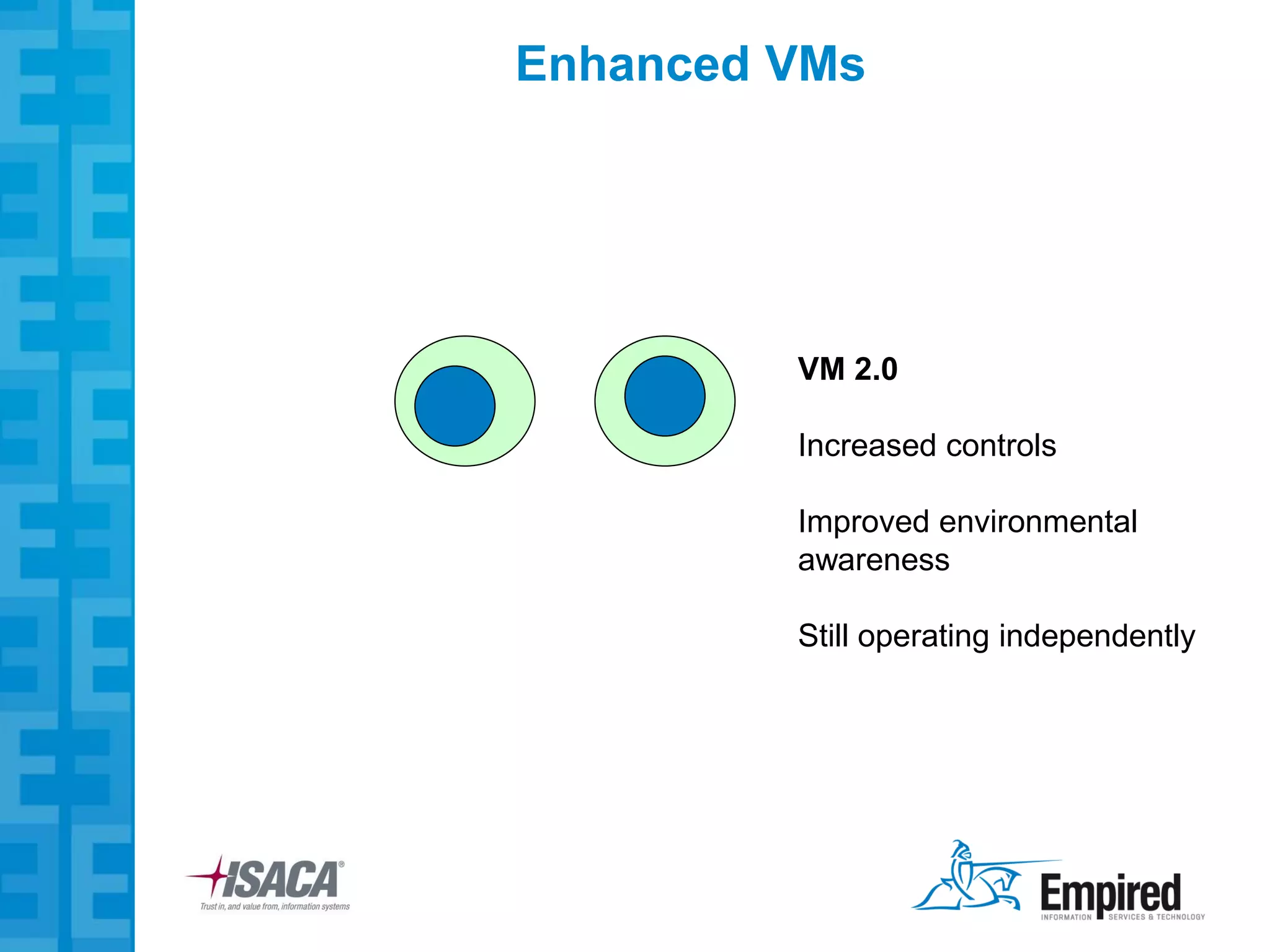
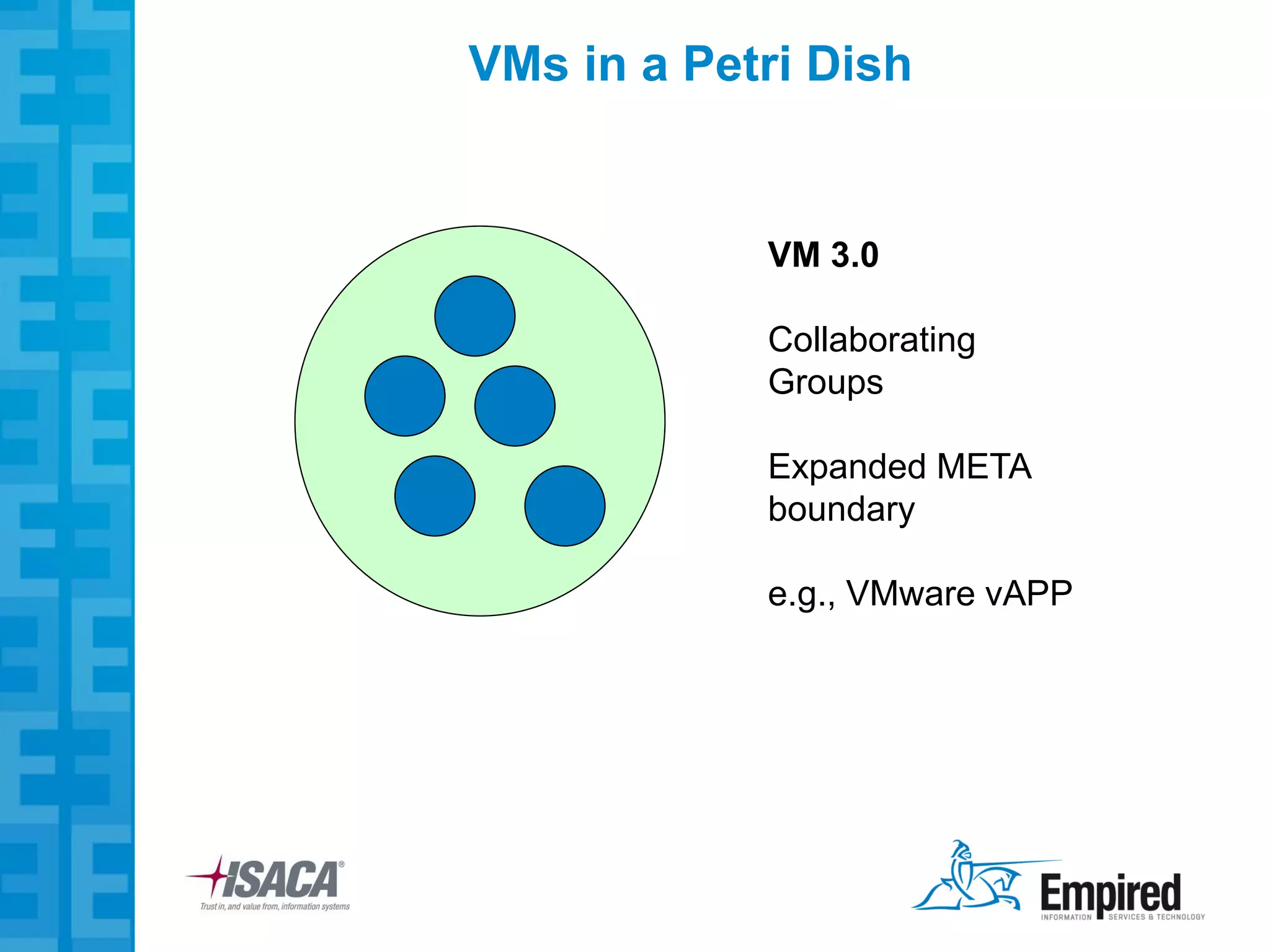
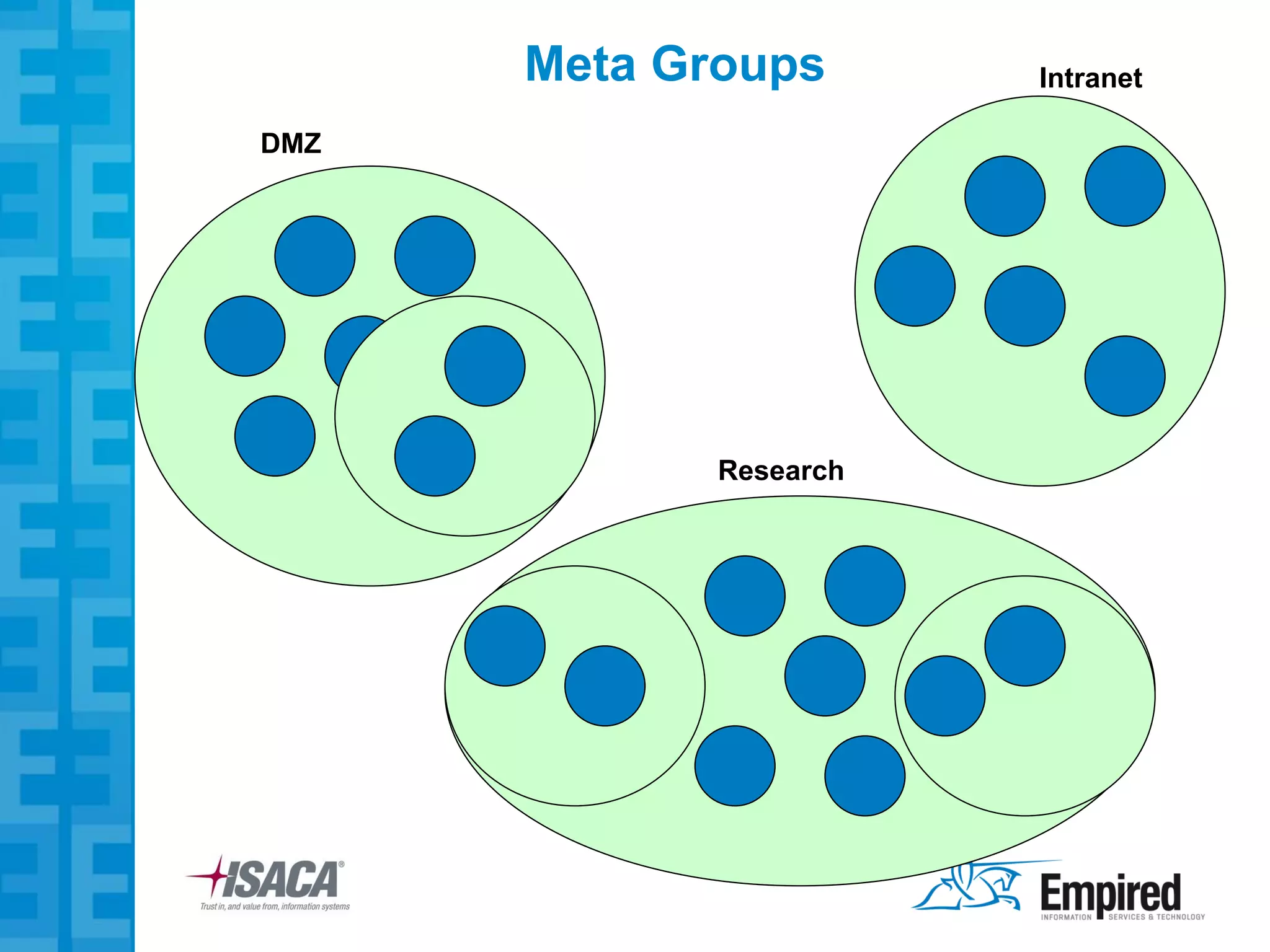
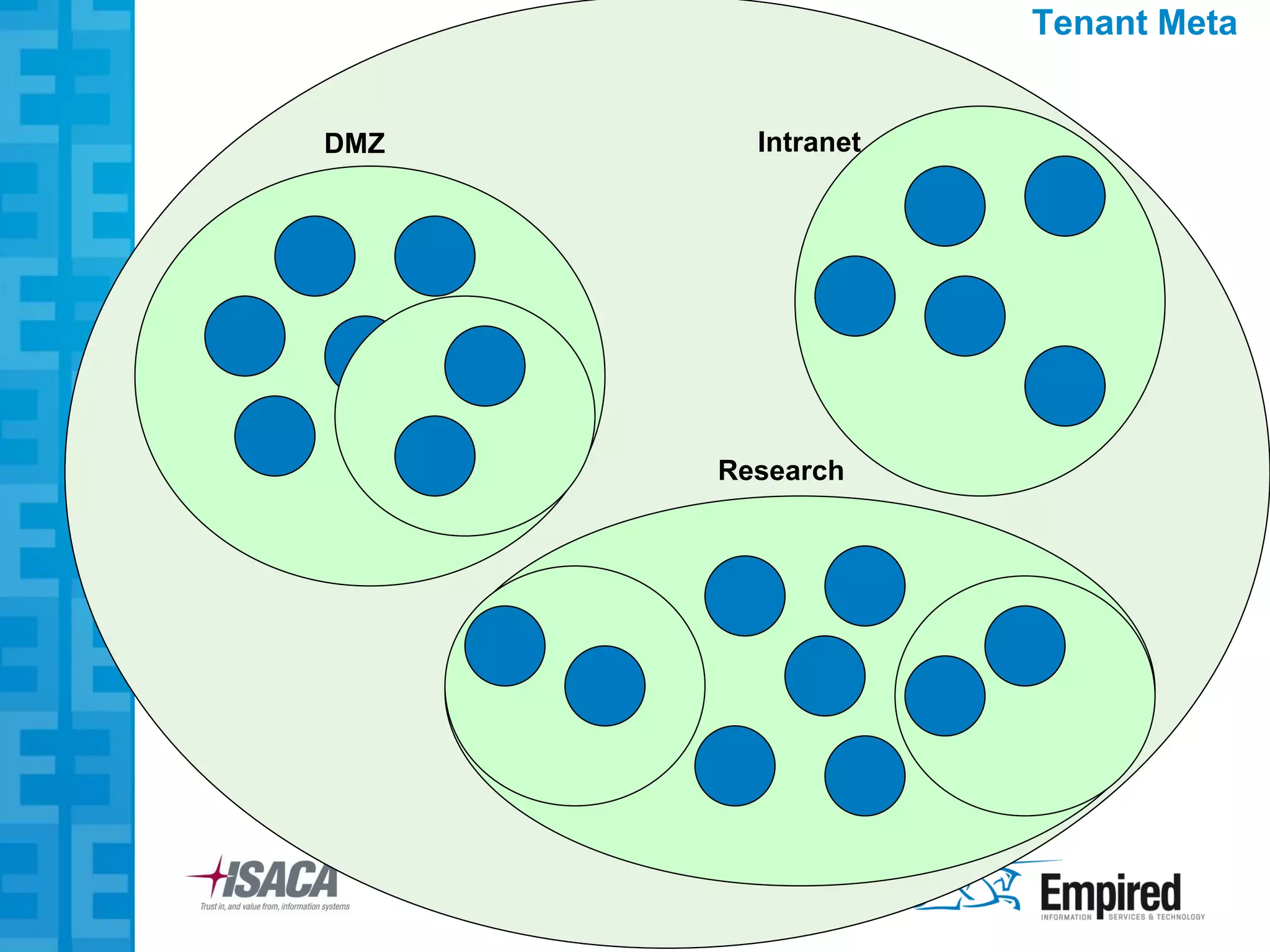
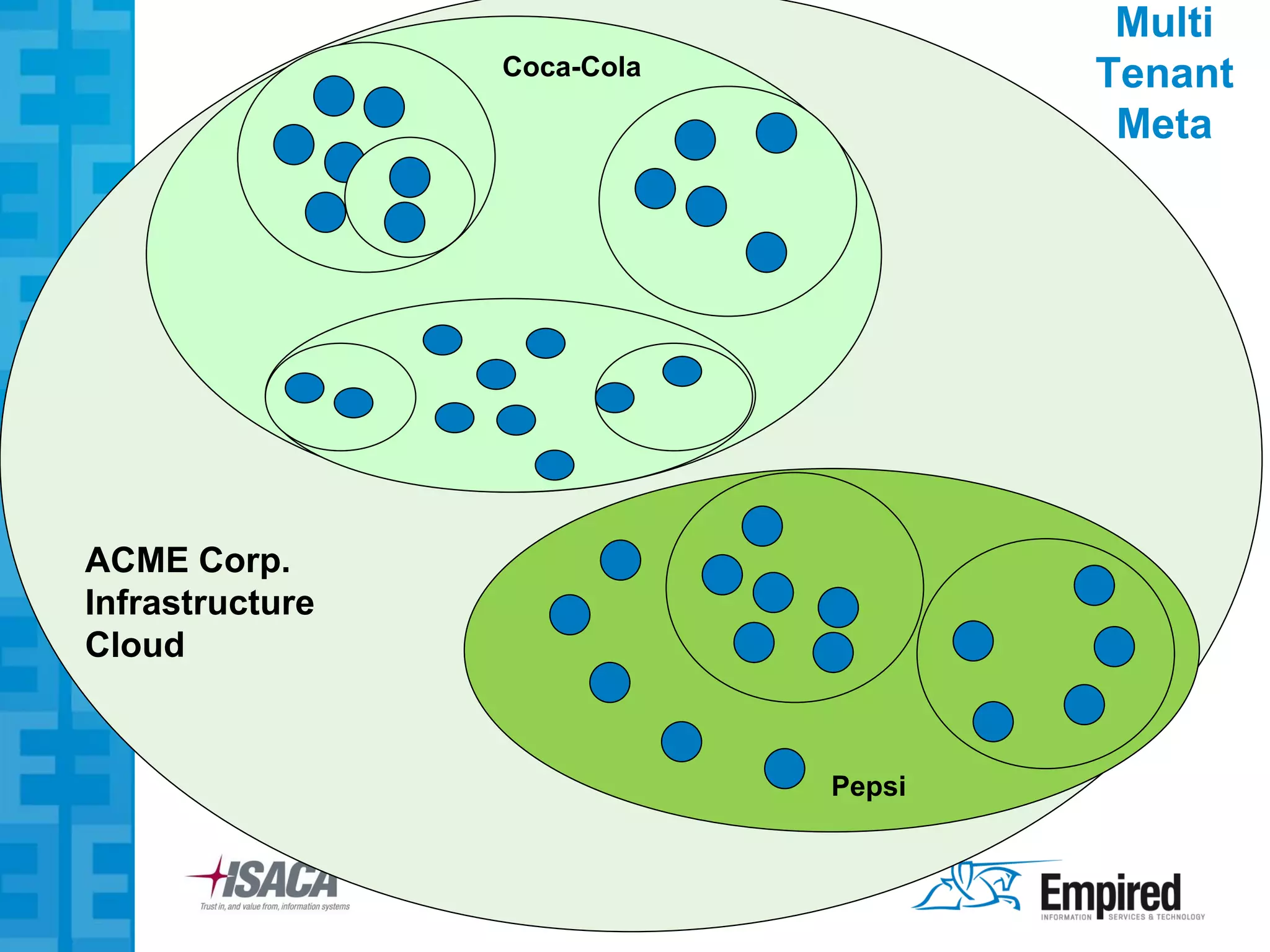
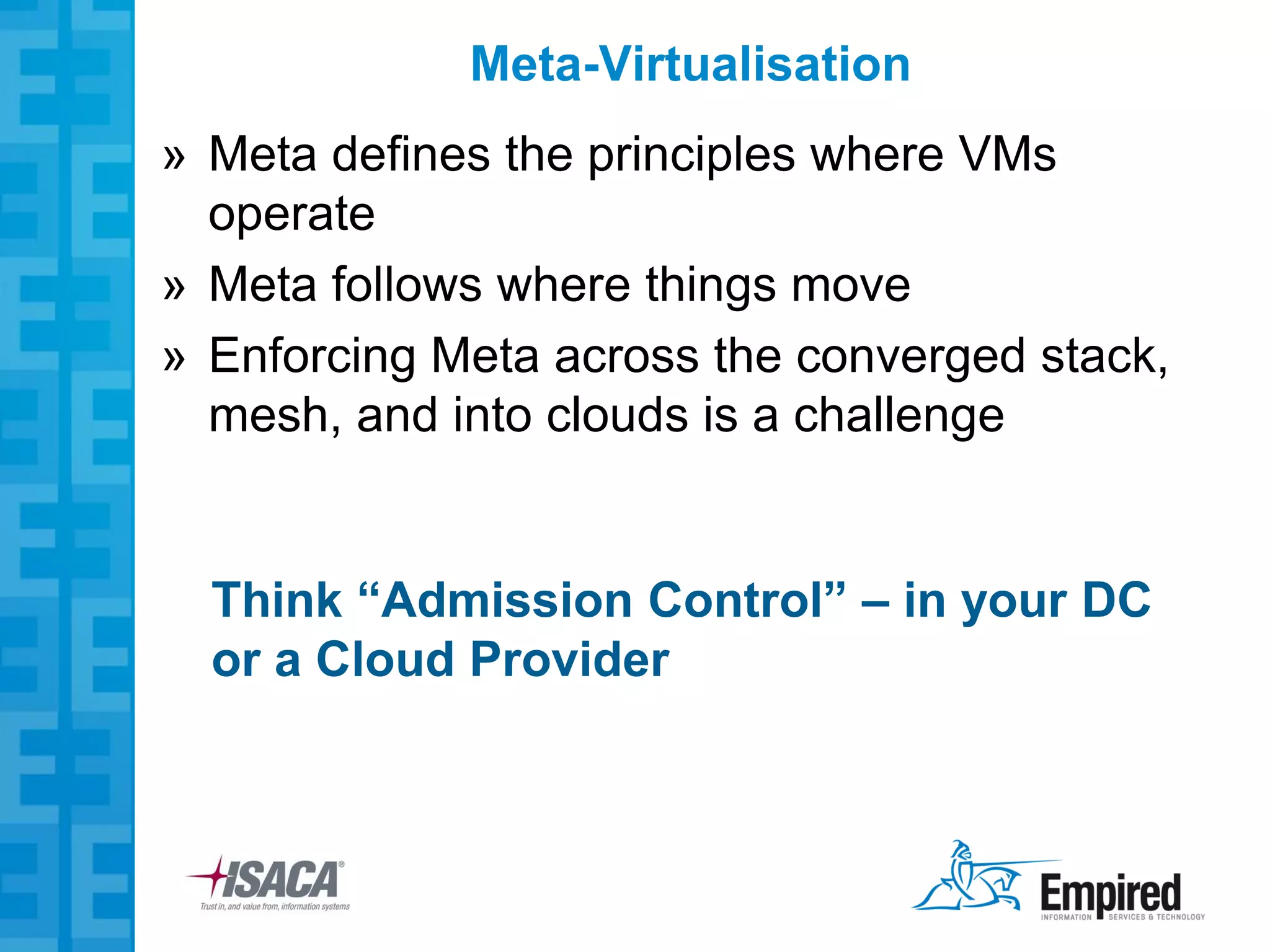
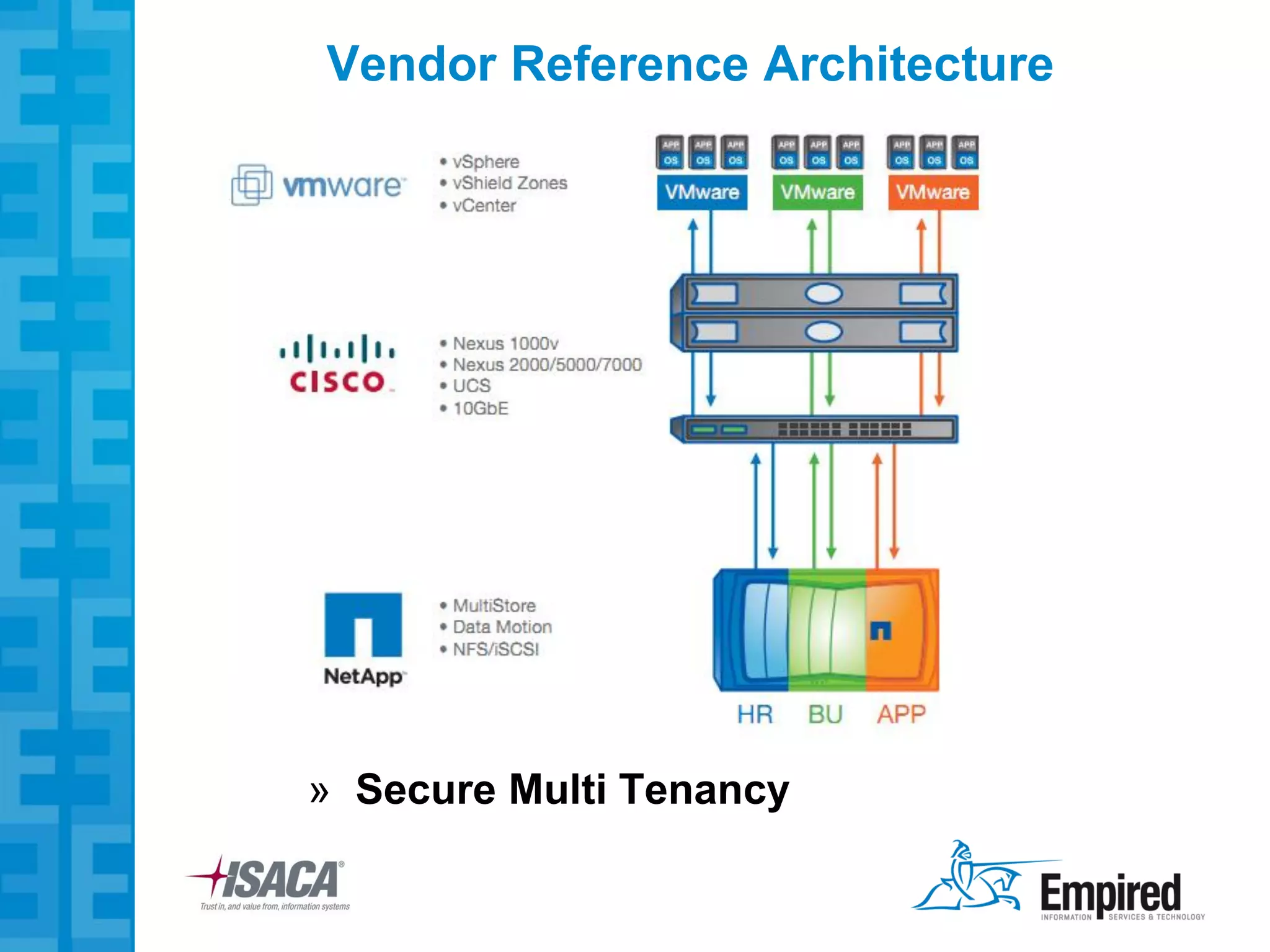
The presentation discusses new security considerations for virtualization as it moves beyond consolidation into cloud computing. It asks what IT professionals should consider when selling, designing, or auditing virtual infrastructure. While virtualization provides some security benefits, it also introduces risks if not implemented properly. Emerging technologies may help address these risks and enable more secure virtual and cloud environments through standards, encryption, and trusted execution. The presentation examines virtualization platforms and security across the infrastructure stack.