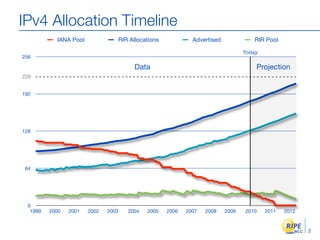
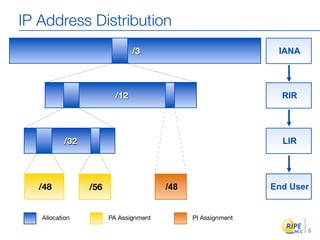
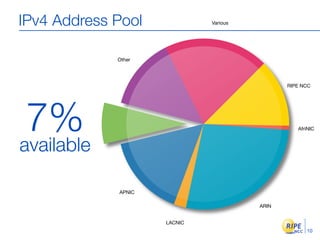
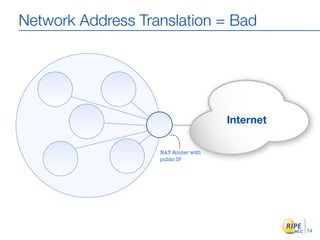
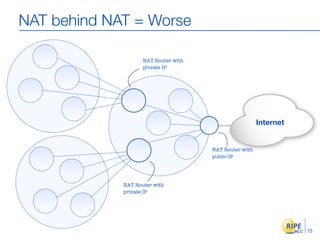
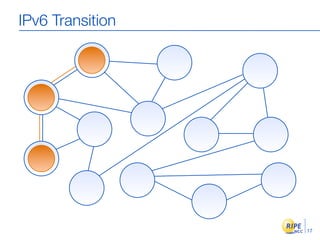
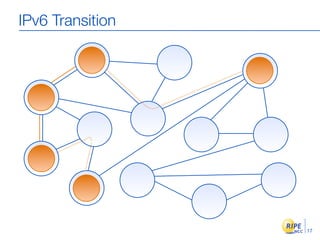
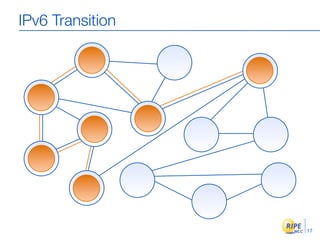
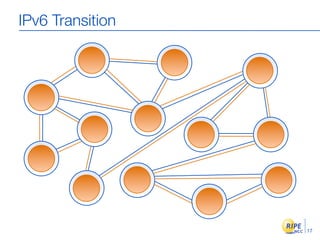
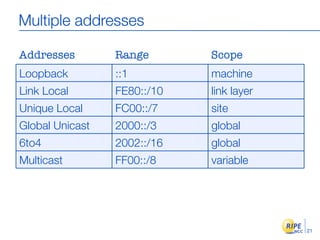
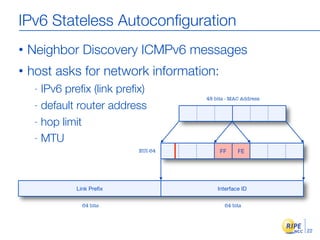
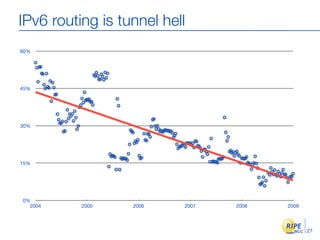
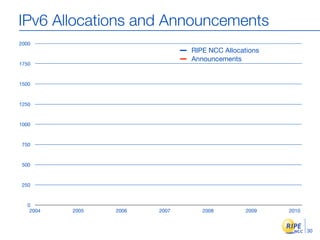
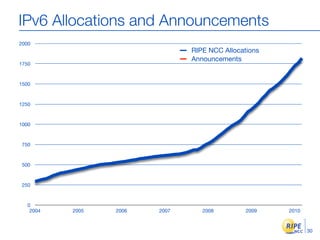
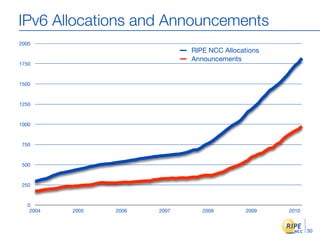
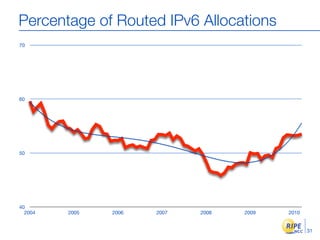
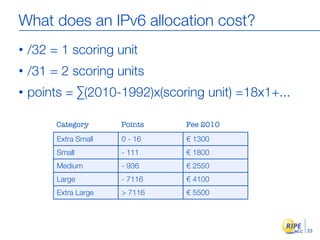
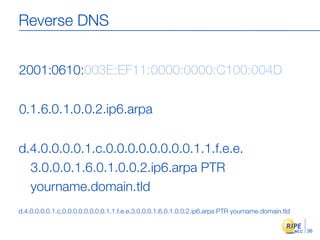
IPv6 adoption is increasing due to the depletion of available IPv4 addresses. The document discusses IPv6 allocation timelines, the need to reach more internet users, and transition techniques from IPv4 to IPv6 like dual stacking and tunneling. It provides guidance on obtaining IPv6 allocations and assignments, addressing and routing, and a phased approach to deployment within an organization.