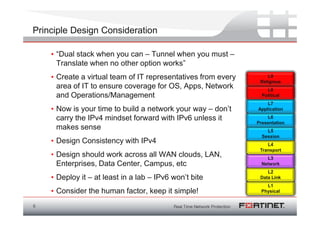
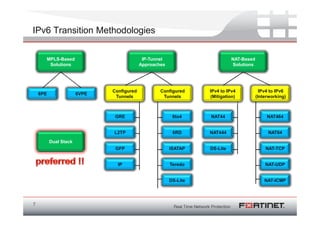
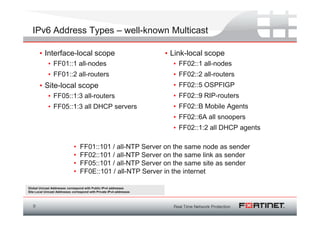
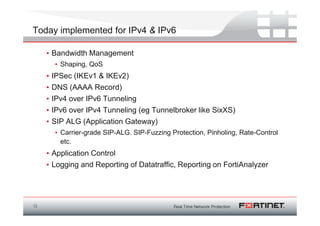
The document discusses the transition to IPv6 due to the exhaustion of IPv4 addresses, outlining the benefits of IPv6 including a larger address space, improved security, and better support for modern applications. It highlights the complexities and considerations involved in the migration, such as compatibility issues and the necessity of dual-stack systems. Additionally, it presents Fortinet's strategies for integrating IPv6 capabilities into their security features and emphasizes the importance of planning and infrastructure readiness for successful implementation.