More Related Content
Similar to Ipv Technical White Paper Wp111504
Similar to Ipv Technical White Paper Wp111504 (20)
More from Erik Ginalick (20)
Ipv Technical White Paper Wp111504
- 1. IP VERSION 6
Technical information on IPv6 to help you better understand the important issues and
benefits for your business.
Internet Protocol version 6 (IPv6) is the successor to the current IPv4 Network layer protocol in use today
as the foundation for almost all Internet communication. When IPv4 was introduced in 1981, it was
believed that the approximately 4.3 billion addresses would last for the foreseeable future. However,
during the late 1980s, when the Internet began to experience explosive growth, it was clear a next-
generation addressing method would need to be created. Some steps were taken to slow down the use
of IPv4 addresses and enhance the scalability of IP networks in the 1990s, including the adoption of CIDR
(Classless Inter-domain Routing) and NAT (Network Address Translation). In 1998, IPv6 was created as
the long term solution to IPv4 address exhaustion.
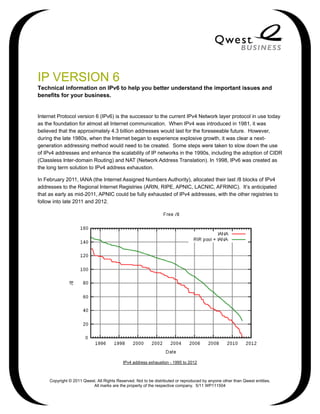
In February 2011, IANA (the Internet Assigned Numbers Authority), allocated their last /8 blocks of IPv4
addresses to the Regional Internet Registries (ARIN, RIPE, APNIC, LACNIC, AFRINIC). It’s anticipated
that as early as mid-2011, APNIC could be fully exhausted of IPv4 addresses, with the other registries to
follow into late 2011 and 2012.
IPv4 address exhaustion - 1995 to 2012
Copyright © 2011 Qwest. All Rights Reserved. Not to be distributed or reproduced by anyone other than Qwest entities.
All marks are the property of the respective company. 5/11 WP111504
- 2. IPv6 vs. IPv4 - Addressing
The most important enhancement of IPv6 compared to IPv4 is the much larger address space that’s
available with IPv6. Where an IPv4 address consists of 32 bits, IPv6 addresses are 128 bits long. This
equates to about 340 undecillion unique addresses with IPv6 compared to about 4.3 billion for IPv4. IPv6
addresses are written in hexadecimal format using eight groups of 16-bit hex values separated by colons:
2001:0db8:0000:0000:0000:0000:0000:0001
IPv6 addressing basics:
1. IPv6 addresses have two logical parts: a 64-bit network/subnet prefix and a 64-bit host
address/interface ID. (The host address can be automatically generated from the interface MAC
address.)
2. The 128-bit IPv6 address can be abbreviated with the following rules:
a. Rule one: Leading zeroes within a 16-bit value may be omitted.
b. Rule two: A single occurrence of consecutive groups of zeroes within an address may be
replaced by a double colon.
There are three broad classifications of IPv6 addresses based on networking methodologies:
1. Unicast - Identifies each network interface. An IPv6 packet sent to a Unicast address is
delivered to the interface identified by that address.
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 3. 2. Anycast – Identifies a set of interfaces. An IPv6 packet destined for an Anycast address is
delivered to one of the interfaces identified by the address, usually the nearest one to the source.
3. Multicast - Identifies a group or set of interfaces that may belong to the different nodes. An IPv6
packet delivered to a Multicast address is delivered to the multiple interfaces.
Note: Unlike IPv4, broadcast addresses are not implemented in IPv6.
Each IPv6 address has a scope, which specifies in which part of the network it is valid and unique. There
are reserved IPv6 addresses used for specific purposes:
• ::/128 An IPv6 address with all zeroes in it is referred to as an unspecified address and is used for
addressing purposes within a software.
• ::1/128 This is called the loop back address and is used to refer to the local host. An application
sending a packet to this address will get the packet back after it is looped back by the IPv6 stack.
The local host address in IPv4 was 127.0.0.1.
• 2001:db8::/32 This is a documentation prefix allowed in the IPv6. All the examples of IPv6
addresses should ideally use this prefix to indicate that it is an example.
• fec0::/10 This is a site-local prefix offered by IPv6. This address prefix signifies that the address is
valid only within the local organization. Subsequently, the usage of this prefix has been
discouraged by the RFC.
• fc00::/7 This is called the Unique Local Address (ULA). These addresses are routed only within a
set of cooperating sites. These were introduced in the IPv6 to replace the site-local addresses.
These addresses also provide a 40-bit pseudorandom number that reduces the risk of address
conflicts.
• ff00::/8 This prefix is offered by IPv6 to denote the multicast addresses. Any address carrying this
prefix is automatically understood to be a multicast address.
• fe80::/10 This is a link-local prefix offered by IPv6. This address prefix signifies that the address is
valid only in the local physical link.
Advantages of IPv6 over IPv4
The benefits of IPv6 over IPv4 are largely dependent on each end-user or enterprise applications. In
general, the following table is a comparison of some features of IPv6 and IPv4:
Benefit IPv6 IPv4
More Addresses 3.4×1038 = 340 undecillion addresses. 4.29 x 109 = 4.2 billion addresses.
Simplified Network IPv6 networks provide auto- Networks must be configured
Addressing configuration capabilities (SLAAC). manually or via DHCP.
Network Address Direct addressing is possible due to the Widespread use of NAT allows a
Translation (NAT) extensive address space. The need for single NAT address to potentially
Demise NAT is effectively eliminated. mask thousands of non-routable
addresses, compromising end-to-
end integrity.
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 4. Improved Security IPSEC is built into the IPv6 protocol. IPSEC was originally designed for
IPv6 and back ported for IPv4. The
elimination of NAT makes IPSEC
simpler and more efficient.
Fragmentation IPv6 routers do not perform Fragmentation and reassembly
fragmentation, done only by the hosts. occurs at the router = inefficient use
of resources and degraded
performance.
Minimum MTU 1280 Bytes 576 Bytes
Path MTU Discovery Highly recommended Not widely used
Control Protocols Single Control Protocol: ICMPv6 Multiple Control Protocols: ARP,
ICMP, IGMP
Transitioning to IPv6
While the much larger IPv6 numbering system is meant to one day completely replace IPv4, this will take
many years to accomplish. In the meantime, much of the Internet will run IPv4 and IPv6 simultaneously.
This is necessary to ensure all users, regardless of the protocol version they are using, will be able to
interact with all content on the Internet. New network deployments or applications that have IP
addressing requirements beyond the current available IPv4 supply will ultimately be required to deploy
IPv6 only networks due to the pending exhaustion of IPv4 address space.
It’s equally important that businesses and organizations make their services and online content available
to both IPv4 and IPv6 users to ensure maximum visibility is maintained. Until IPv6 completely replaces
IPv4, there are numerous transition and translational methods available to enable IPv6-only hosts to
reach IPv4 content and services, allow isolated IPv6 hosts and networks to reach the IPv6 Internet over
the existing IPv4 infrastructure, as well as allowing IPv4 hosts to reach IPv6-only content and services.
With this in mind, the Internet Engineering Task Force (IETF) has defined several mechanisms to allow
co-existence between IPv6 networks and legacy IPv4 networks, as well as making the transition from
IPv4 to IPv6. There are three broad categories that contain these transition mechanisms:
• Dual-stack IPv4/IPv6
• Tunneling
• Protocol Translation
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 5. Dual-Stack
Dual-stack nodes have the ability to send and receive both IPv4 and IPv6 packets. They can directly
interoperate with IPv4 nodes using IPv4 packets, and also directly interoperate with IPv6 nodes using
IPv6 packets. The dual-stack approach is the preferred method for phasing in IPv6 into existing networks.
Procuring new devices or upgrading existing devices to support dual-stack greatly assists in providing a
nimble environment for transitioning to IPv6.
Dual-stacked hosts connected to a dual-stack network enables networks to gradually migrate from IPv4 to
IPv6 in a controlled manner, which allows legacy IPv4 applications and devices to operate side-by-side
with newly transitioned IPv6 nodes on the same dual-stack network.
Tunneling
Unlike the dual-stack approach, tunneling encapsulates IPv6 packets inside IPv4 packets to be carried
across an existing IPv4 infrastructure. Tunneling allows IPv6 endpoints or IPv6 “islands” to communicate
with each other across an IPv4 network. There are two types of tunneling to enable the communication
between those IPv6 endpoints, Automatic and Configured.
Automatic tunnels are dynamically created between the two endpoints. There are several methods of
automatic tunneling including 6to4, Teredo, ISATAP and a hybrid of configured and automatic tunneling
called Tunnel Broker. 6to4 is the most commonly used automatic tunneling method. In 6to4, tunnel
endpoints are determined by using a well-known IPv4 anycast address on the remote side, and
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 6. embedding IPv4 address information within IPv6 addresses on the local side. Note that does not facilitate
interoperation between IPv4-only hosts and IPv6-only hosts but rather is a transparent mechanism used
as a transport layer between IPv6 nodes.
(6to4 - http://en.wikipedia.org/wiki/6to4)
Configured tunnels, as the name implies, are tunnels that are explicitly configured by the network
administrator.
Regardless of the tunneling method used, they should only be considered a temporary transition method
and not as a permanent migration strategy to IPv6.
Protocol Translation
Translation services translate an existing protocol to another. It is anticipated that following the
exhaustion of IPv4 addresses, new networks and hosts added to the Internet may have only IPv6
connectivity. In order to accommodate backwards compatibility to existing IPv4-only resources, IPv6
transition mechanisms need to be deployed.
The most common translation methods in use today are NAT64 and DNS64. With NAT64, the NAT64
server is the endpoint for at least one IPv4 address and a 32-bit IPv6 network (64:FF9B::/96). The IPv6
client embeds the IPv4 address and sends the packets to the resulting address. The NAT64 server then
creates a NAT-mapping between the IPv6 and the IPv4 address, allowing them to communicate with each
other.
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 7. .
(NAT64 - http://en.wikipedia.org/wiki/IPv6_transition_mechanisms#NAT64)
DNS64 refers to a DNS server that when asked for a domains' IPv6 AAAA record, creates an AAAA
record from the A record, if no AAAA record exists. The first part of the resolved IPv6 address points to an
IPv6/IPv4 translator (NAT64 device) and the second part embeds the IPv4 address from the A record.
There are two issues with the DNS64 translation mechanism:
• It only works for cases where DNS is used to find the remote host address, if IPv4 literals are
used the DNS64 server will never be involved, and therefore, no translation will take place.
• Since the DNS64 server returns records not specified by the domain owner, DNSSEC validation
will fail.
Factors When Adopting IPv6
There are several factors to be considered prior to making the move into the IPv6 arena, such as:
• IPv6 address space – IPv6 address space can be obtained directly from a Regional Internet
Registry (RIR) such as ARIN, RIPE, APNIC, LACNIC or AFRINIC. Addresses are also available
from many Internet Service Providers.
• IPv6 connectivity (native or tunneled) – Native connectivity via dual-stack or a dedicated
connection is needed in order to access IPv6 services and content. Alternately, tunneled service
can be obtained from many providers, although should only be considered on a temporary basis.
• Operating systems, software, and network management tool upgrades – IPv6 support
should be considered when procuring new network hardware or software.
• Router, firewall, and other hardware upgrades – New hardware purchases may be required to
support both IPv4 and IPv6, or firmware updates to support both may be needed.
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 8. • IT staff and customer service training – It’s important that network administrators, IT staff,
Engineering planning and design staff, and ultimately, the end user are trained in the use and
support of IPv6. Self-training and formal training should be considered.
Qwest and IPv6
Qwest has been involved with IPv6 since 1999, when we acquired our first IPv6 address allocation from
Abilene in the form of a /35. Today, we’ve obtained two /32 networks from ARIN in addition to another /32
from APNIC in order to roll out IPv6 services to our customers and within the network infrastructure.
In 2000, Qwest built an IPv6 test network using both Native and Tunneled connectivity across multiple
PoP’s across the country to gain experience with operating an IPv6 network, as well as provisioning and
supporting beta customers for the IPv6 trial.
When moving from the dedicated IPv6 test network to a production network in 2007 and 2008, the
decision was made to go with the dual-stack design across the existing IPv4 infrastructure, thereby
making the end design for IPv6 exactly the same as IPv4 and providing a seamless transition by not
requiring separate interfaces for IPv4 and IPv6 services. Several objectives were developed to ensure a
phased, controlled approach in order to allow systems and the network to evolve, such as:
• Enable IPv6 on the production IP backbone in order to provide transit IPv6 services
• Enable IPv6 equivalents of existing IPv4 enterprise services
Internet Port – Public IPv6 connectivity to on-net and peer networks
Private Port – IPv6 Layer 3 VPN
• Gain operational experience to minimize both operational and capital costs as well as gain
developmental experience to support applications on IPv6
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 9. • Provide services to meet government mandated IPv6-ready dates
• Implement IPv6 so as not to affect or degrade the performance of the existing IPv4 network and
services
Today, the Qwest Edge, Core and Border routers are IPv6 enabled in nearly every IP PoP location for
end-to-end v6 connectivity across the Qwest backbone and beyond, with more being added every week.
Our native IPv6 connectivity for end-users ranges from T1 to Nx10GigE port speeds on both the public
Internet and Private MPLS VPN services, using dedicated and dual-stack access methods.
The Qwest DNS platform is also IPv6 enabled to support the IPv6 AAAA records, as well as the
QwestControl portal for customer circuit management.
Conclusion
The exhaustion of IPv4 addressing is inevitable and no longer a matter of “if”, but rather “when” they will
become no longer available. Enterprises and organizations must begin to weigh the impacts of that
exhaustion with their own system and network migration timelines to ensure a seamless transition and
continued availability to both IPv4 and IPv6 only users.
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504
- 10. Why Qwest
Qwest is committed to the evolution of IP services to IPv6, whether in a public or private network
environment, as well as the potential in the benefits that IPv6 can bring. We have invested time, money
and effort into testing the features and capabilities of IPv6 and will continue to do so as we continue to roll
out additional IPv6 capabilities and services throughout the Qwest Global Network. Qwest is ready to help
you gain the benefits of IPv6 using our experience and talent to make the transition easy and complete.
Qwest Professional Services can conduct an assessment of your IPv6 needs, plan the transition, and
implement the change for you. Contact a Qwest sales representative for complete details.
References:
• Wikipedia - http://en.wikipedia.org/wiki/IPv6
• IPv6.com - http://www.ipv6.com
• ARIN – http://www.arin.net
Copyright © 2011 Qwest. All Rights Reserved. All marks are the property of the respective company. 5/11 WP111504