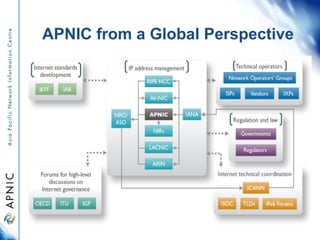
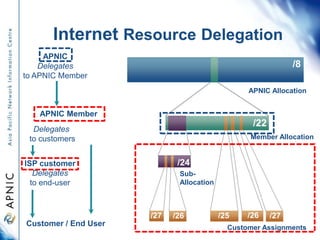
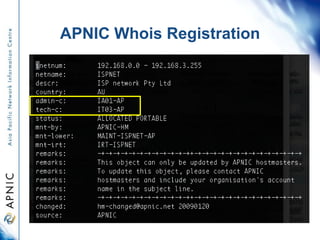
APNIC is the regional internet registry for Asia and the Pacific. It distributes internet resources like IP addresses and maintains the APNIC Whois database. While some abuse reports list APNIC as the source of addresses, APNIC does not operate networks or investigate abuse directly. It can provide contact information for the organization responsible but cannot reclaim addresses or stop abuse itself. The document outlines how to use the Whois database to identify contacts and proper procedures for reporting invalid information or abuse.