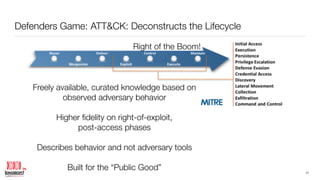
The document presents Joe Klein's extensive background in cybersecurity and technology, emphasizing the importance of implementing IPv6 standards in procurement to ensure readiness for this complex transition. It discusses cybersecurity challenges, including the defender's dilemma and strategies for enhancing detection and response capabilities against intruders. The paper also highlights past research on IPv6 scanning and the relevance of addressing technical debt in cybersecurity measures.