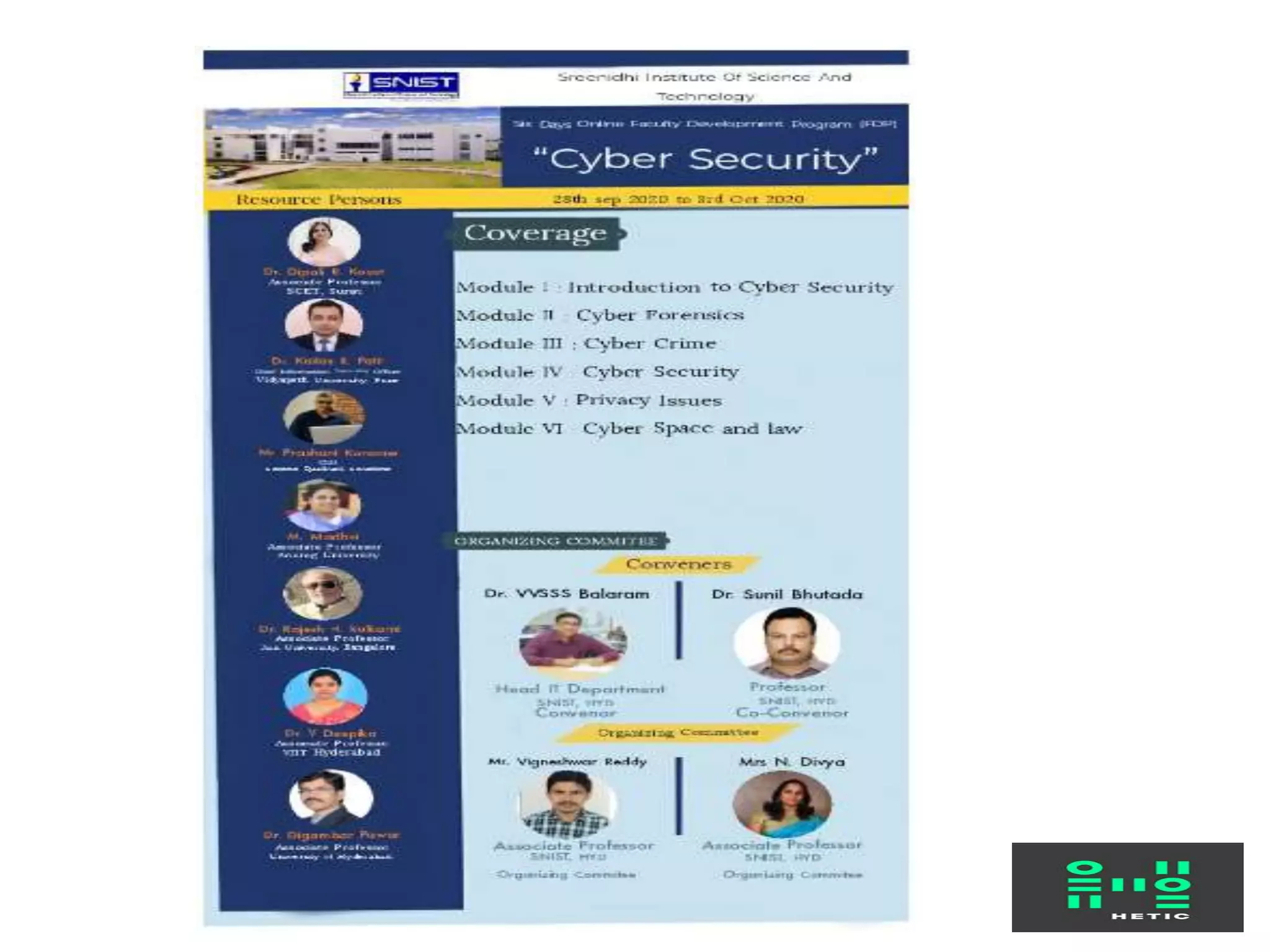
The document discusses several case studies related to intellectual property rights (IPR) and cyberspace:
1) A domain name dispute case involving trademark issues in cyberspace, with cybersquatting defined as registering domain names to profit from another's goodwill.
2) A 1999 case of passing off involving Yahoo! and trademark infringement.
3) A meta-tagging issue case where including other companies' names in website meta tags was found to infringe trademarks.
4) A copyright infringement case where one news site embedded and linked to pages from another news site without permission.