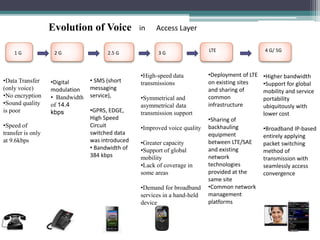
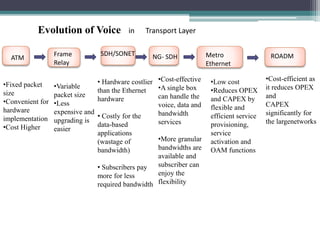
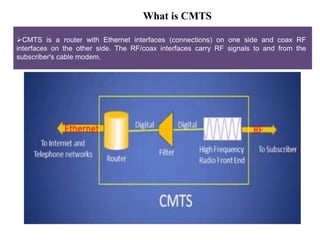
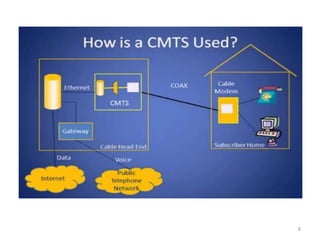
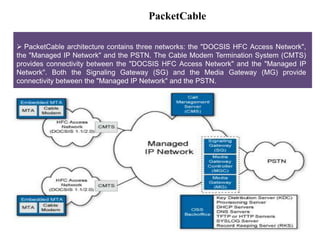
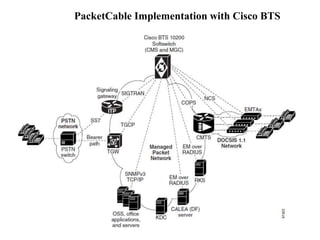
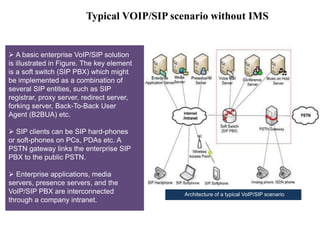
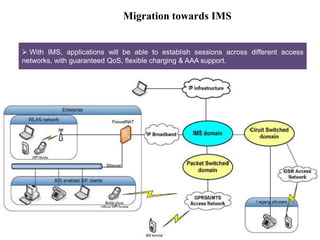
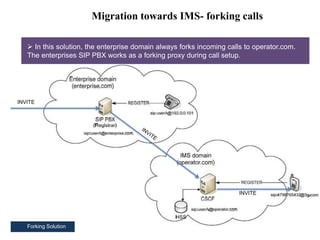
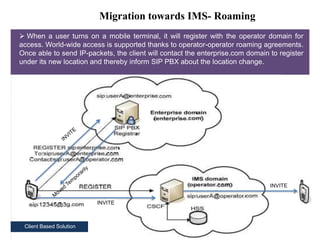
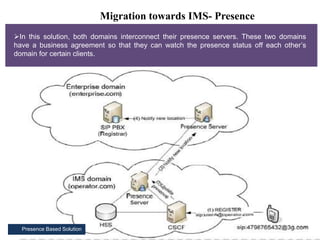
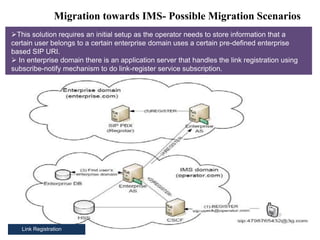
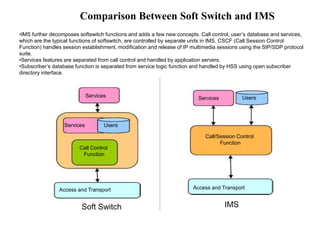
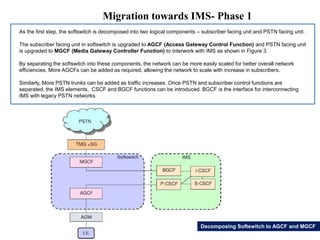
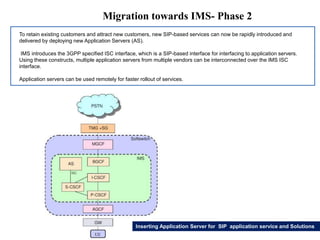
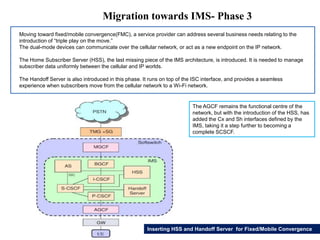
This document summarizes the evolution of telecommunications networks from 1G to 5G and the transition to an IP-based network using the IMS framework. It discusses the key technologies and standards used in each generation such as GSM, GPRS, EDGE, LTE. It also covers the evolution of the access, transport and session layers from circuit-switched to packet-switched networks. Finally, it proposes a three-phase approach to migrating an existing softswitch-based VoIP network to an IMS architecture by decomposing functions and introducing new IMS elements.