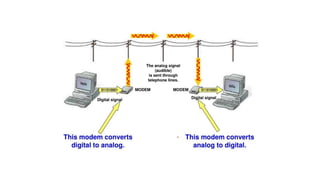
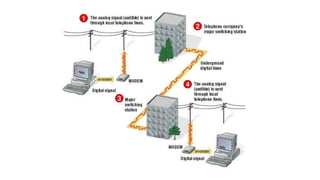
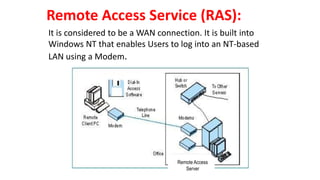
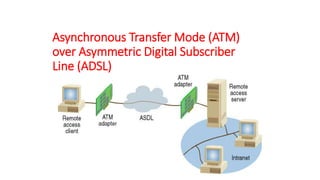
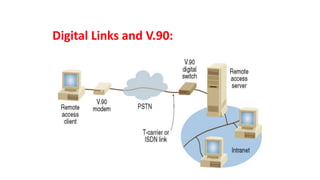
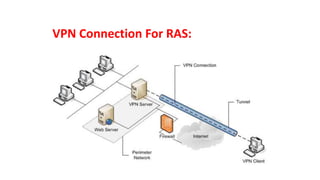
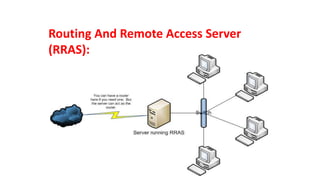
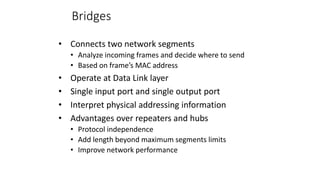
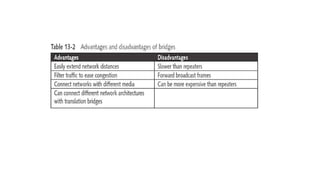
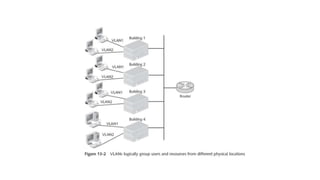
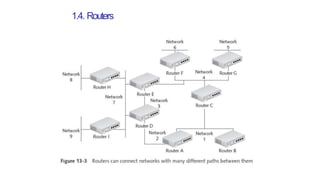
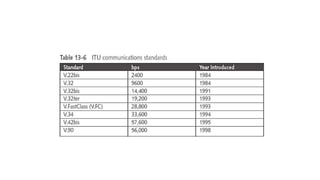
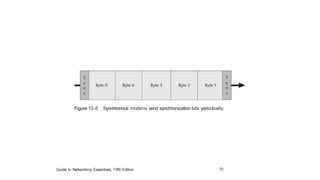
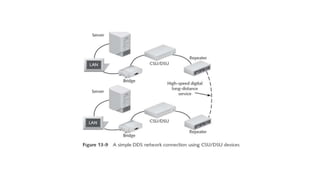
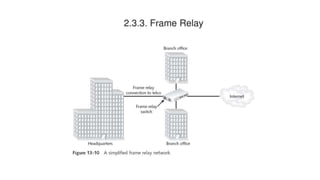
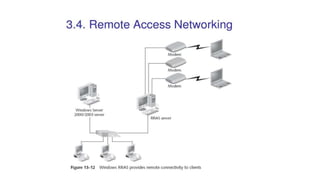
The document discusses various topics related to creating larger computer networks, including modems, digital telephone lines, remote access, and protocols like PPTP. Modems are primarily used to transfer files between computers by uploading and downloading. Digital telephone lines like DSL and cable modems provide higher speed data transmission compared to standard analog lines. Remote access allows employees to securely access a corporate network from outside using protocols like PPTP, which creates private "tunnels" within public networks like the Internet.