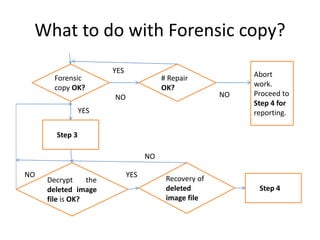
This document presents information on iOS forensics. It discusses the introduction to forensics as it relates to mobile devices, the procedure for a case study including creating a forensic copy and analyzing system files and catalogs to search for and recover deleted files like images. It notes the challenges of presenting digital evidence in court and concludes that the process allows recovery of deleted image files with timestamps in a forensically sound way, with opportunities for future research on newer iOS devices.