ECSM 2021 - Sfaturi pentru a te proteja în mediul online
•
0 likes•14 views
Sfaturi pentru a te proteja în mediul online - Luna europeană a securității cibernetice 2021 Think Before U Click
Report
Share
Report
Share
Download to read offline
Recommended
ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media 

Ce faci dacă ți-au fost sparte conturile de social media - Luna europeană a securității cibernetice 2021
Think Before U Click
ECSM - Ce faci dacă ți-au fost compromise conturile bancare

Ce faci dacă ți-au fost compromise conturile bancare - Luna europeană a securității cibernetice 2021
Think Before U Click
Cybersecurity Awareness

This is a basic presentation about cybersecurity to share awareness about various security threats and how you can protect yourself from them. In the preview window the formatting is off, but when downloaded it can be viewed with no problems. This is for my Info Security Policy Management class at Governors State University.
14 tips to increase cybersecurity awareness

We used this presentation within our company to increase the cybersecurity awareness of our employees. These 14 tips should help everybody to protect themselves against the most obvious cyber attacks.
Preventions of Email Hacking

How to prevent from email hacking.
email, email prevention, email prevention techniques, how hack email, how to make email secure, strategy of email prevention
CDSE Cybsecurity Awareness Posters

These are from the Center for Development of Security Excellence (CDSE) and are free to use. See cdse.edu for more info.
Phishing & Cyber Attack Awareness

It is important to be aware and to know when you are falling victim to a phishing and cyber attack. Here's how you can determine a phishing scam or a cyber attack and what to do to prevent the intruders and in case of a breach.
Recommended
ECSM 2021 - Ce faci dacă ți-au fost sparte conturile de social media 

Ce faci dacă ți-au fost sparte conturile de social media - Luna europeană a securității cibernetice 2021
Think Before U Click
ECSM - Ce faci dacă ți-au fost compromise conturile bancare

Ce faci dacă ți-au fost compromise conturile bancare - Luna europeană a securității cibernetice 2021
Think Before U Click
Cybersecurity Awareness

This is a basic presentation about cybersecurity to share awareness about various security threats and how you can protect yourself from them. In the preview window the formatting is off, but when downloaded it can be viewed with no problems. This is for my Info Security Policy Management class at Governors State University.
14 tips to increase cybersecurity awareness

We used this presentation within our company to increase the cybersecurity awareness of our employees. These 14 tips should help everybody to protect themselves against the most obvious cyber attacks.
Preventions of Email Hacking

How to prevent from email hacking.
email, email prevention, email prevention techniques, how hack email, how to make email secure, strategy of email prevention
CDSE Cybsecurity Awareness Posters

These are from the Center for Development of Security Excellence (CDSE) and are free to use. See cdse.edu for more info.
Phishing & Cyber Attack Awareness

It is important to be aware and to know when you are falling victim to a phishing and cyber attack. Here's how you can determine a phishing scam or a cyber attack and what to do to prevent the intruders and in case of a breach.
Internet Safety for 1950s Adults and Beginners

Internet has permeated to every sphere of our lives. Facebook and WhatsApp have pervaded to every sphere of our lives.
Hoevver, the generation 1950s and earlier have to a lrge extent been unable to grapple with the complexities of this new medium.
Internet Safety for Elder Adults and Beginners is a quick step guide to such adults, to both simplify and yet make them aware of the consequences of their action.
The idea is not to create fear of the monster, but to get them relate the safety precautions to what they would take in offline world.
Would appreciate your suggestions. This is a crowd sourced effort and I am thankful to the contributors.
Email hacking

Email security is quintessential in information age. Every email-id user must know how to protect his or her account from getting hacked.
How to Avoid Crypto Scams - Crypto JBro

Crypto scams are on the rise and getting more sophisticated every day. This presentation shows you how to protect your cryptocurrency and personal information. Check out Crypto JBro on Youtube.
Junior secondary yr 7:8 aug 18 4.3 preview

Cyber Safety and Cyber Bullying Presentation aimed at years 7&8 who are just starting to navigate social media and deal with cyber bullying and sexting. This talk covers a broad range of topics from cyber security to avoid being hacked or scammed, through to making good choices with what you post online and helping with cyber bullying. I also cover sexting or sharing nudes and what the legal and real world consequences are, and dealing with strangers online. Where to get help and the importance of getting help and reporting.
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Supporting material for the Seminar on Internet Security presented at IIT Guwahati, August 8th 2012.
Passwords for sale

In the last years we are reading more and more news about massive (millions) breach of passwords in web services as communities, emails services, cloud services and others.
Hackers simply are obtaining money stealing passwords and selling or misusing them.
This presentation is focus on how to protect our accounts and with this also keep sure our digital identity, our image and also our money safe from hackers businesses.
Internet Security

A brief introduction on Internet Security.
After viewing this presentation you would able to find answer for the below questions... !!!
How are credit cards getting hacked ?
How are emails getting hacked?
How are computers getting hacked ?
Regards
Avnish
Email Security Awareness

Security awareness class I teach with tips to protect yourself from some common email dangers & scams.
Don't ask, don't tell the virtues of privacy by design

A very light intro talk on privacy, identity, and designing with the latter to preserve the former.
Probably makes no sense at all without the audio so if it whet's your appetite dig through my other decks on these topics. Most of those have code in for the more technically minded.
Getting inside the cybercriminal's m ind 

An infographic on how you can beat cybercriminals at their own game.
https://houseofit.com.au/cyber-criminals-work-get-to-know-them-by-tapping-their-modus/
Internet Safety & Cyber chip presentation

This presentation gives valuable information about how to earn the BSA cyber chip.
Net 213 Policy Primer

A superficial take on Twitter's terms of service, in order to create awareness among younger internet users about the importance of actively participating in the well-being of their rights and privacy.
How to incrementally improve Sanctions Screening with AI

Artificial intelligence has proven its efficiency on the fight against financial crime, but so far has seen limited use in sanctions filtering due to the strong requirements for explainability and guaranteed compliance. Discover how an incremental introduction of artificial intelligence can help overcome these difficulties and improve your processes without introducing new risks.
Dos and don's on social media

Dos and don's on social media, social rules, facebook, twitter, instagram, youtube
More Related Content
What's hot
Internet Safety for 1950s Adults and Beginners

Internet has permeated to every sphere of our lives. Facebook and WhatsApp have pervaded to every sphere of our lives.
Hoevver, the generation 1950s and earlier have to a lrge extent been unable to grapple with the complexities of this new medium.
Internet Safety for Elder Adults and Beginners is a quick step guide to such adults, to both simplify and yet make them aware of the consequences of their action.
The idea is not to create fear of the monster, but to get them relate the safety precautions to what they would take in offline world.
Would appreciate your suggestions. This is a crowd sourced effort and I am thankful to the contributors.
Email hacking

Email security is quintessential in information age. Every email-id user must know how to protect his or her account from getting hacked.
How to Avoid Crypto Scams - Crypto JBro

Crypto scams are on the rise and getting more sophisticated every day. This presentation shows you how to protect your cryptocurrency and personal information. Check out Crypto JBro on Youtube.
Junior secondary yr 7:8 aug 18 4.3 preview

Cyber Safety and Cyber Bullying Presentation aimed at years 7&8 who are just starting to navigate social media and deal with cyber bullying and sexting. This talk covers a broad range of topics from cyber security to avoid being hacked or scammed, through to making good choices with what you post online and helping with cyber bullying. I also cover sexting or sharing nudes and what the legal and real world consequences are, and dealing with strangers online. Where to get help and the importance of getting help and reporting.
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Supporting material for the Seminar on Internet Security presented at IIT Guwahati, August 8th 2012.
Passwords for sale

In the last years we are reading more and more news about massive (millions) breach of passwords in web services as communities, emails services, cloud services and others.
Hackers simply are obtaining money stealing passwords and selling or misusing them.
This presentation is focus on how to protect our accounts and with this also keep sure our digital identity, our image and also our money safe from hackers businesses.
Internet Security

A brief introduction on Internet Security.
After viewing this presentation you would able to find answer for the below questions... !!!
How are credit cards getting hacked ?
How are emails getting hacked?
How are computers getting hacked ?
Regards
Avnish
Email Security Awareness

Security awareness class I teach with tips to protect yourself from some common email dangers & scams.
Don't ask, don't tell the virtues of privacy by design

A very light intro talk on privacy, identity, and designing with the latter to preserve the former.
Probably makes no sense at all without the audio so if it whet's your appetite dig through my other decks on these topics. Most of those have code in for the more technically minded.
Getting inside the cybercriminal's m ind 

An infographic on how you can beat cybercriminals at their own game.
https://houseofit.com.au/cyber-criminals-work-get-to-know-them-by-tapping-their-modus/
Internet Safety & Cyber chip presentation

This presentation gives valuable information about how to earn the BSA cyber chip.
Net 213 Policy Primer

A superficial take on Twitter's terms of service, in order to create awareness among younger internet users about the importance of actively participating in the well-being of their rights and privacy.
How to incrementally improve Sanctions Screening with AI

Artificial intelligence has proven its efficiency on the fight against financial crime, but so far has seen limited use in sanctions filtering due to the strong requirements for explainability and guaranteed compliance. Discover how an incremental introduction of artificial intelligence can help overcome these difficulties and improve your processes without introducing new risks.
What's hot (20)
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Internet Security - Naga Rohit S [ IIT Guwahati ] - Coding Club & DefCon DC91...
Don't ask, don't tell the virtues of privacy by design

Don't ask, don't tell the virtues of privacy by design
How to incrementally improve Sanctions Screening with AI

How to incrementally improve Sanctions Screening with AI
Similar to ECSM 2021 - Sfaturi pentru a te proteja în mediul online
Dos and don's on social media

Dos and don's on social media, social rules, facebook, twitter, instagram, youtube
Heads up!

All product and company names mentioned herein are for identification and educational purposes only and are the property of, and may be trademarks of, their respective owners.
DIgital Citizenship for Parents of Middle School Students

This is the keynote that was presented at the parent night about digital citizenship.
MindMake - Online Safety Talking to your Kids Parental Control

A great document by On Guard On-Line about the conversation parents need to have with their kids about being online.
http://get.mindmake.com/parentalcontrols/
Social Media Safety Presentation

A presentation on how to protect yourself while using Social Media created for Partners in Rehab Thunder Bay.
Girls security abuse - social media - security tips.arise raabi - pdf

Password strength is a measure of the effectiveness of a password against guessing or ... Using strong passwords lowers overall risk of a security breach, but strong .... Very long lists of pre-computed password hashes can be efficiently stored using ..... Use a minimum password length of 8 or more characters if permitted.
Cyber Safety How Children Can Protect Themselves From Online Threats

Presentation given to teachers and adminstrators about how to teach children cybersafety.
Similar to ECSM 2021 - Sfaturi pentru a te proteja în mediul online (20)
DIgital Citizenship for Parents of Middle School Students

DIgital Citizenship for Parents of Middle School Students
MindMake - Online Safety Talking to your Kids Parental Control

MindMake - Online Safety Talking to your Kids Parental Control
Girls security abuse - social media - security tips.arise raabi - pdf

Girls security abuse - social media - security tips.arise raabi - pdf
Cyber Safety How Children Can Protect Themselves From Online Threats

Cyber Safety How Children Can Protect Themselves From Online Threats
More from One-IT
Centralizator întrebări și răspunsuri Digitalizare IMM.doc

Ministerul Investițiilor și Proiectelor Europene publică un centralizator al întrebărilor adresate de către potențialii aplicanți și răspunsurile formulateaferente apelului de proiecte numărul 1 – Digitalizarea IMM-urilor – grant de până la 100.000 euro pe întreprindere care să sprijine IMM-urile în adoptarea tehnologiilor digitale, din cadrul Investiției I3 – Scheme de ajutor pentru sectorul privat, Componenta C9 – Suport pentru sectorul privat, cercetare, dezvoltare și inovare, finanțat prin PNRR.
Sursa: https://mfe.gov.ro/pnrr-digitalizarea-imm-urilor-apelul-nr-1-centralizatorul-intrebarilor-adresate-de-potentialii-aplicanti-si-raspunsurile-la-acestea/
Ghid final Digitalizare IMM

Ghid final Digitalizare IMM, publicat de Ministerul Investițiilor și Proiectelor Europene în 15 decembrie 2022.
Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf

Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis - ce conține detalii privind departajarea proiectelor cu punctaje egale și detalii privind soldul balanței comerțului cu bunuri și servicii aferent anului 2021, comunicat de INS și BNR.
Ghidul solicitantului 4.1.1. BIS.pdf

Ghidul aferent acțiunii 4.1.1. BIS – „Investiții în retehnologizare acordate IMM-urilor din domeniul industriei alimentare și al construcțiilor, în vederea refacerii capacității de reziliență”
Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx

Ghidului solicitantului 4.1.1. BIS - varianta intermediară, rezultată în urma consultării publice - publicată de Autoritatea de Managment pentru Programul Operațional Competitivitate din cadrul Ministerului Investițiilor și Proiectelor Europene
Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022

Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022, publicată în Monitorul Oficial vineri, 19 august 2022
Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf

Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis, publicată în Monitorul Oficial nr 720 din 18 iulie 2022, Partea I.
Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx

Ghidul solicitantului aferent actiunii 4.1.1 Investiții în activități productive, tip de proiect: „Investiții în retehnologizare acordate IMM-urilor din domeniul industriei alimentare și al construcțiilor, în vederea refacerii capacității de reziliență” – bis - în consultare publică
Procedura-femeia-antreprenor-2022.pdf

Procedura de implementare
a Programului Femeia Antrepenor 2022 - publicată în 11 august 2022, în Monitorul Oficial, Partea 1, nr. 799/11.08.2022.
Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...

Ghidul final al solicitantului Acțiunea 4.1.1 „Investiții în activități productive” - publicat în 3 august 2022
Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022

Ghidul consolidat aferent acțiunii 4.1.1. „Investiții în activități productive”
Cum te protejezi de tentativele de tip scam în business

Cum te protejezi de tentativele de tip scam în business - Luna europeană a securității cibernetice 2021
#Think Before U Click
ECSM 2021 - Cum previi atacurile de tip phishing

Cum previi atacurile de tip phishing - Luna europeană a securității cibernetice 2021
#Think Before U Click
ECSM 2021- Informații importante despre amprenta ta digitală

Informații importante despre amprenta ta digitală - Luna europeană a securității cibernetice 2021
#Think Before U Click
Ghidul digitalizarea IMM oipsi consultare publica

- informatii legate de programe finantare pentru digitalizare pe:
https://www.one-it.ro/digitalizare-imm/
Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...

Ghid POC Îmbunătățirea conținutului digital și a infrastructurii TIC sistemice în domeniul e-educație, e-incluziune, e-sănătate și e-cultură
www.one-it.ro/scoala-online
Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...

Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru accesare fonduri 1 miliard euro pentru PFA si IMM-uri
sursa:
http://mfe.gov.ro/consultare-publica-poc-ghidul-actualizat-pentru-sprijinirea-imm-urilor-in-vederea-depasirii-crizei-economice-generate-de-pandemia-covid-19/
One-IT - prezentare GDPR-ul si Protectia datelor personale

One-IT - prezentare GDPR-ul si Protectia datelor personale
- detalii pe:
www.one-it.ro
More from One-IT (20)
Centralizator întrebări și răspunsuri Digitalizare IMM.doc

Centralizator întrebări și răspunsuri Digitalizare IMM.doc
Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf

Corrigendum-ul la Ghidul solicitantului POC 4.1.1. Bis.pdf
Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx

Ghidul Solicitantului varianta intermediară 4.1.1 BIS.docx
Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022

Ordonanța 19/2022 cu privire la rectificarea bugetului de stat pe anul 2022
Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf

Ordonanța de Urgență 113/2022 privind acțiunea POC 4.1.1. Bis.pdf
Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx

Ghid 4.1.1 BIS Industrie alimentară și construcții - Consultare Publică.docx
Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...

Ghidul final al solicitantului Acțiunea 4.1.1 Investiții în activități produc...
Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022

Ghid actiunea 4.1.1 versiunea consolidata 18.02.2022
Cum te protejezi de tentativele de tip scam în business

Cum te protejezi de tentativele de tip scam în business
ECSM 2021- Informații importante despre amprenta ta digitală

ECSM 2021- Informații importante despre amprenta ta digitală
Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...

Ghid poc imbunatatirea continutului digital si a infrastructurii TIC sistemic...
Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...

Ghid cu contributie privata - Propunerea de ghid al solicitantului pentru acc...
One-IT - prezentare GDPR-ul si Protectia datelor personale

One-IT - prezentare GDPR-ul si Protectia datelor personale
Recently uploaded
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

Dr. Sean Tan, Head of Data Science, Changi Airport Group
Discover how Changi Airport Group (CAG) leverages graph technologies and generative AI to revolutionize their search capabilities. This session delves into the unique search needs of CAG’s diverse passengers and customers, showcasing how graph data structures enhance the accuracy and relevance of AI-generated search results, mitigating the risk of “hallucinations” and improving the overall customer journey.
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

Building better applications for business users with SAP Fiori.
• What is SAP Fiori and why it matters to you
• How a better user experience drives measurable business benefits
• How to get started with SAP Fiori today
• How SAP Fiori elements accelerates application development
• How SAP Build Code includes SAP Fiori tools and other generative artificial intelligence capabilities
• How SAP Fiori paves the way for using AI in SAP apps
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

91mobiles recently conducted a Smart TV Buyer Insights Survey in which we asked over 3,000 respondents about the TV they own, aspects they look at on a new TV, and their TV buying preferences.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Recently uploaded (20)
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf

Smart TV Buyer Insights Survey 2024 by 91mobiles.pdf
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
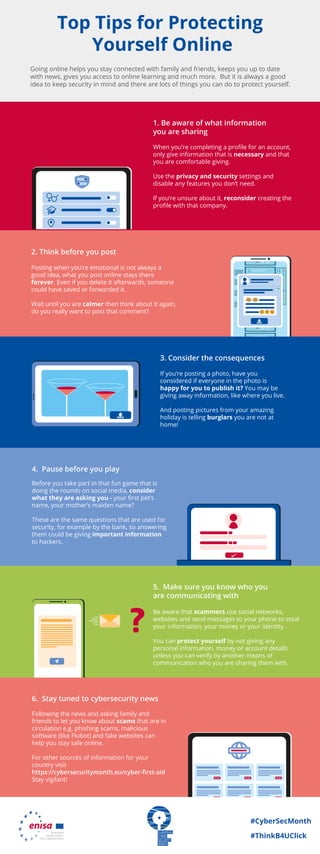
ECSM 2021 - Sfaturi pentru a te proteja în mediul online
- 1. #CyberSecMonth #ThinkB4UClick ? When you’re completing a profile for an account, only give information that is necessary and that you are comfortable giving. Use the privacy and security settings and disable any features you don’t need. If you’re unsure about it, reconsider creating the profile with that company. 1. Be aware of what information you are sharing Posting when you’re emotional is not always a good idea, what you post online stays there forever. Even if you delete it afterwards, someone could have saved or forwarded it. Wait until you are calmer then think about it again, do you really want to post that comment? 2. Think before you post If you’re posting a photo, have you considered if everyone in the photo is happy for you to publish it? You may be giving away information, like where you live. And posting pictures from your amazing holiday is telling burglars you are not at home! 3. Consider the consequences Before you take part in that fun game that is doing the rounds on social media, consider what they are asking you - your first pet’s name, your mother’s maiden name? These are the same questions that are used for security, for example by the bank, so answering them could be giving important information to hackers. 4. Pause before you play Following the news and asking family and friends to let you know about scams that are in circulation e.g. phishing scams, malicious software (like Flubot) and fake websites can help you stay safe online. For other sources of information for your country visit https://cybersecuritymonth.eu/cyber-first-aid Stay vigilant! 6. Stay tuned to cybersecurity news Be aware that scammers use social networks, websites and send messages to your phone to steal your information, your money or your identity. You can protect yourself by not giving any personal information, money or account details unless you can verify by another means of communication who you are sharing them with. 5. Make sure you know who you are communicating with Going online helps you stay connected with family and friends, keeps you up to date with news, gives you access to online learning and much more. But it is always a good idea to keep security in mind and there are lots of things you can do to protect yourself. Top Tips for Protecting Yourself Online
