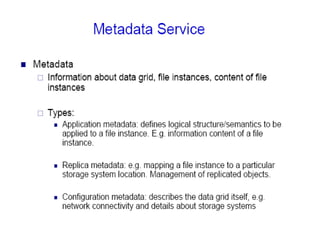
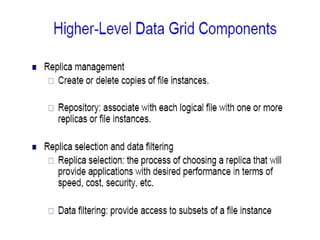
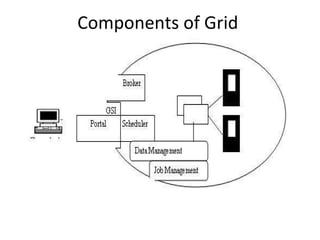
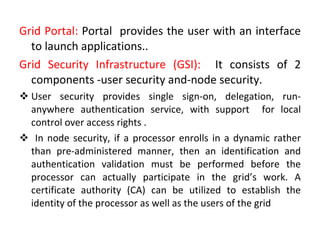
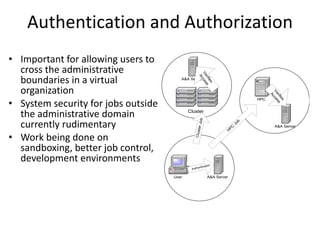
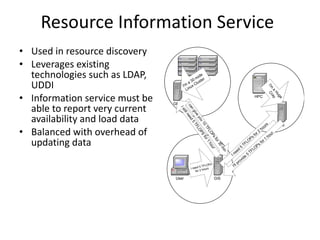
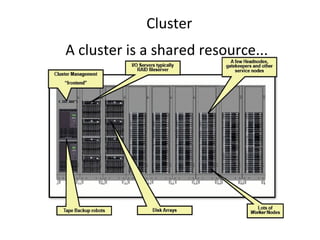
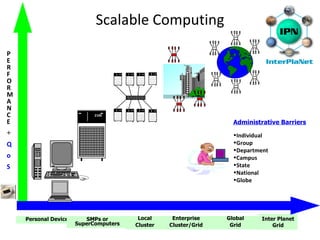
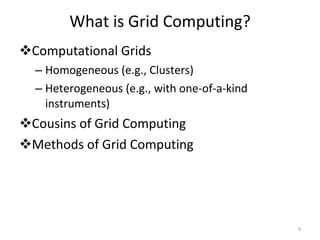
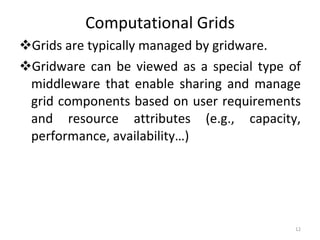
Grid computing allows for sharing and coordination of distributed computer resources to address large-scale computation problems. It enables dynamic, scalable, and inexpensive access to computing power by connecting computers and other resources together with open standards. Key aspects of grid computing include dependable, consistent, pervasive, and inexpensive access to high-end computational capabilities through coordination of distributed and often heterogeneous resources not subject to centralized control.

















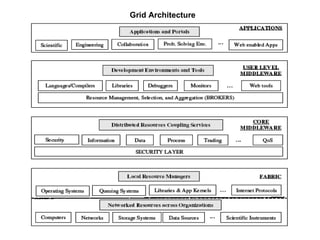
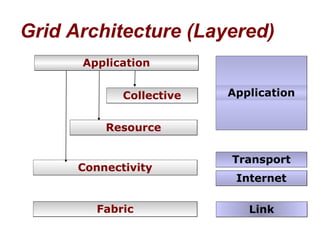
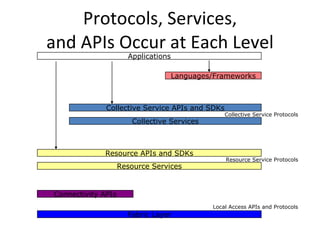



![The connectivity layer defines core protocols required for Grid-specific network transactions. This layer includes the IP protocol stack (system level application protocols [e.g. DNS, RSVP, Routing], transport and internet layers), as well as core Grid security protocols for authentication and authorization.](https://image.slidesharecdn.com/inroductiontogridcomputingbygargishankarverma-110401210152-phpapp01/85/Inroduction-to-grid-computing-by-gargi-shankar-verma-35-320.jpg)