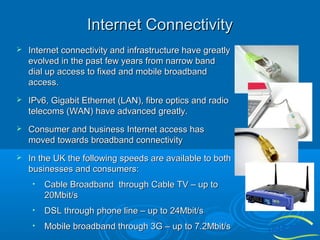
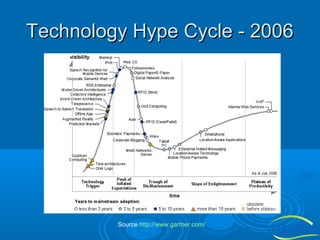
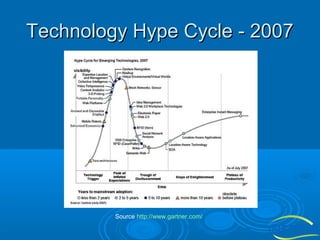
The document discusses the importance of technology in facilities management (FM), emphasizing efficient collaboration, automated monitoring, and improved communication among participants. It highlights challenges in integrating various FM platforms and the evolution of web applications, cloud computing, and the emerging semantic web. The document also touches upon the future of collaborative applications and the potential of the semantic web in enhancing data classification and user engagement.


![What is collaboration technology
A combination of technologies that
together create a single shared interface
between two or more interested individuals
(people), enabling them to participate in a
creative process in which they share their
collective skills, expertise, understanding of
knowledge (information), and thereby
jointly deliver the best solution that meets
their common goal(s). [Wilkinson 2005]](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-3-320.jpg)
![The need for FM collaboration
technology
Information sharing is not easy without the technology.
Adapted from [Wilkinson 2005]](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-4-320.jpg)
![The need for FM collaboration
technology
The technology offers a more efficient and less complex
way to manage communications.
Adapted from [Wilkinson 2005]](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-5-320.jpg)



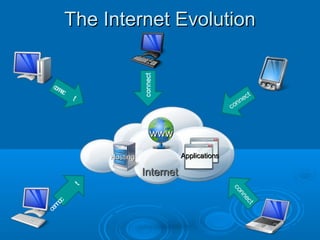





![Web 2.0
Web 2.0 is the network as platform,
spanning all connected devices; Web
2.0 applications are those that make
the most of the intrinsic advantages
of that platform: delivering software
as a continually-updated service that
gets better the more people use it,
consuming and remixing data from
multiple sources, including individual
users, while providing their own data
and services in a form that allows
remixing by others, creating network
effects through an "architecture of
participation," and going beyond the
page metaphor of Web 1.0 to deliver
rich user experiences.[O'Reilly
2005]
Source http://en.wikipedia.org/wiki/Web_2.0](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-15-320.jpg)
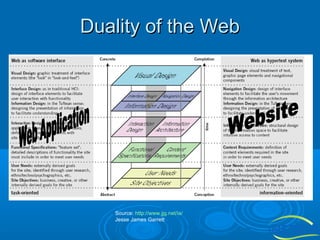
![Rich Internet Applications (RIAs)
RIAs were born out of Web 2.0 concepts and the
evolution of traditional Web applications.
RIAs are web applications that have the features and
functionality of traditional desktop applications.
RIAs typically run in a web browser, or do not require
software installation
Source [Dawelbeit 2008]
Source [http://www.fsi.co.uk/digital-dashboard-mid-32.html]](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-17-320.jpg)
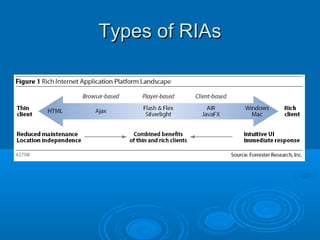
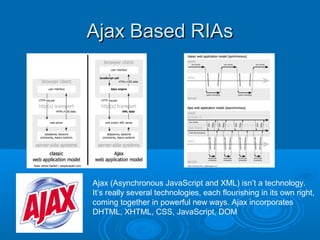


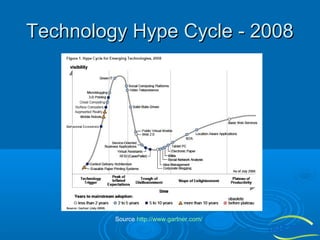
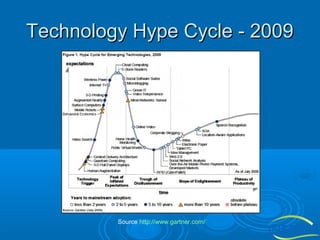
![The Future
Semantic Web (sometimes referred to as Web 3.0) the
meaning of data can be discovered by computers. This
envisaged data web would allow software (e.g.
intelligent agents) to find, process and associate data
from across the web to accomplish user goals.
The Semantic Web offers new opportunities for the
next generation of collaborative applications: it provides
a novel means to classify information items i.e. by
means of ontologies which formally represent the
consensual understanding of the application users
w.r.t. a particular domain of interest. Taking advantage
of this technology, the first promising implementations
of Semantic Web-based collaboration platforms such
as Semantic Web portals, semantic Wikis and blogs, to
name only a few, have been proposed. [http://stoc.agnbi.de/]](https://image.slidesharecdn.com/informationtechnologyforfacilitiesmanagement-140126043720-phpapp01/85/Information-Technology-for-Facilities-Management-28-320.jpg)

