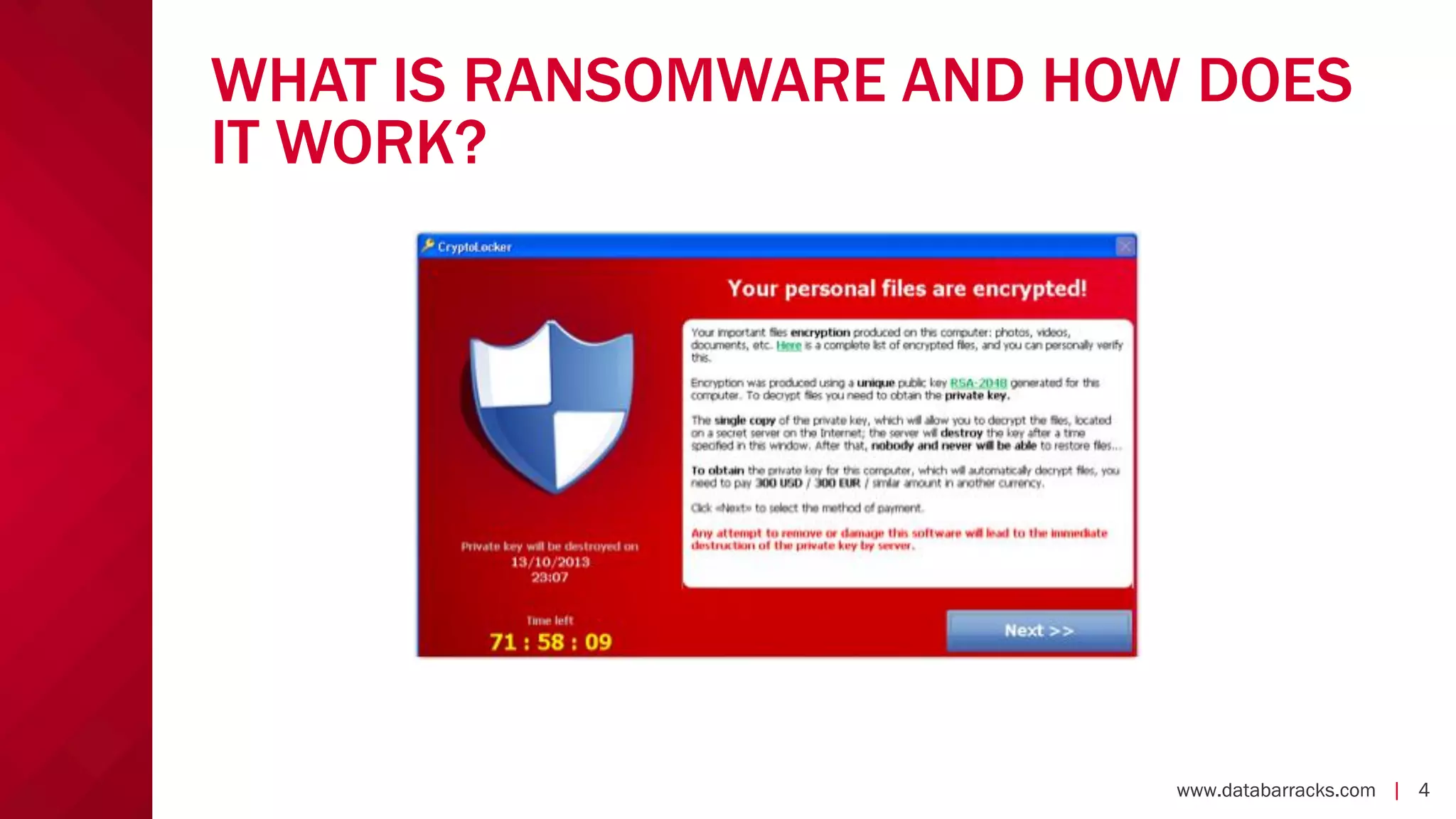
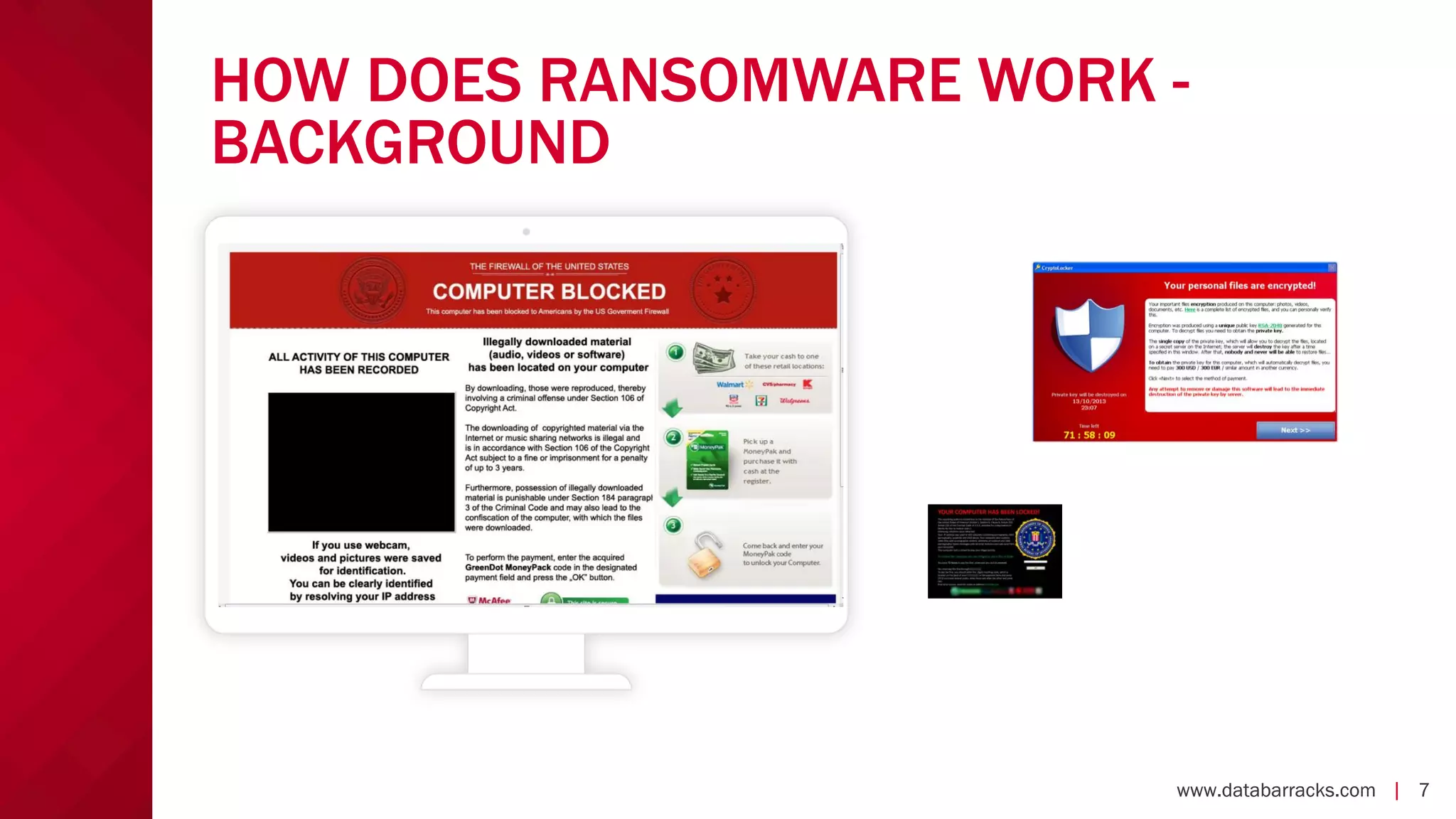
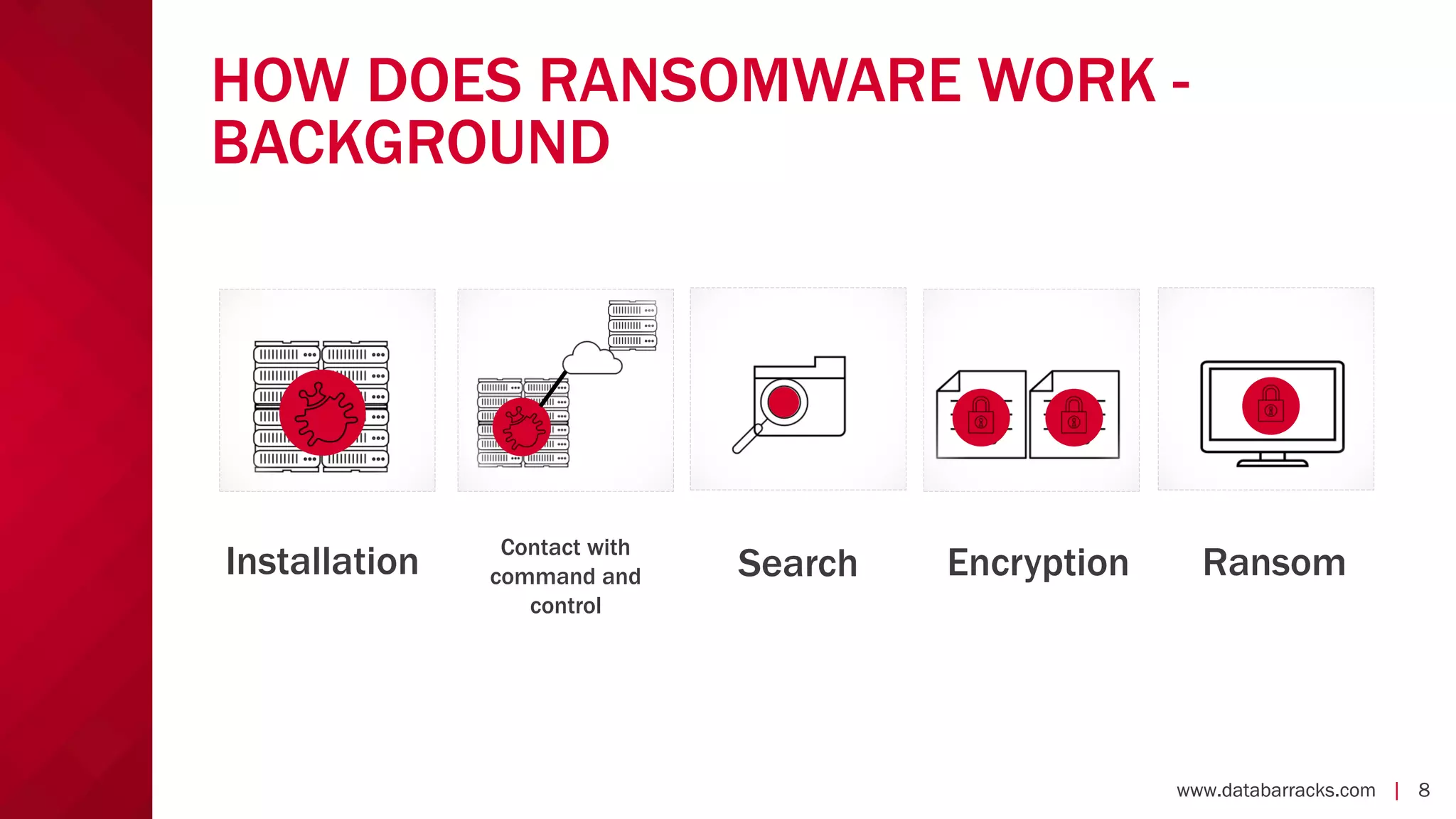
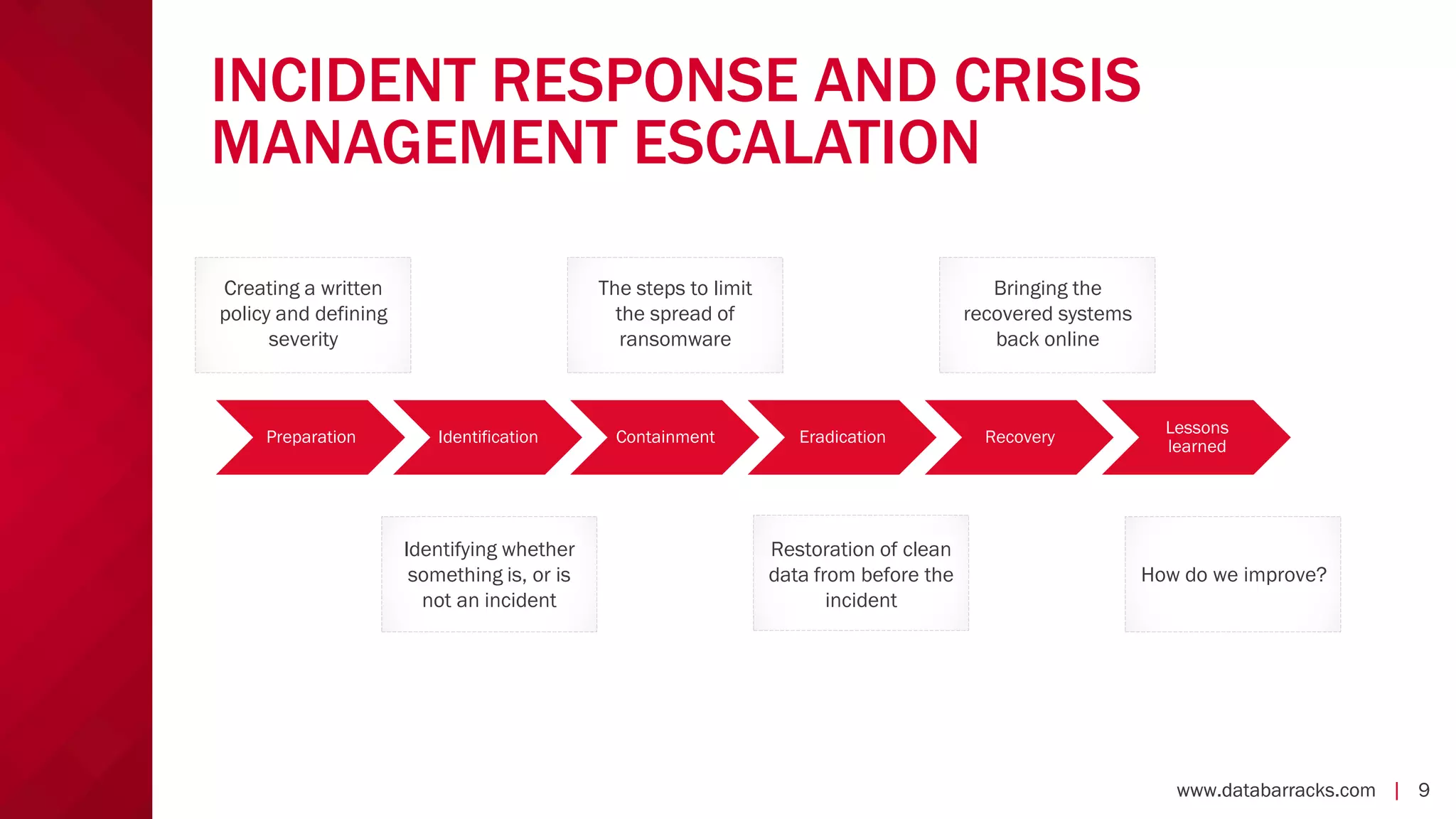
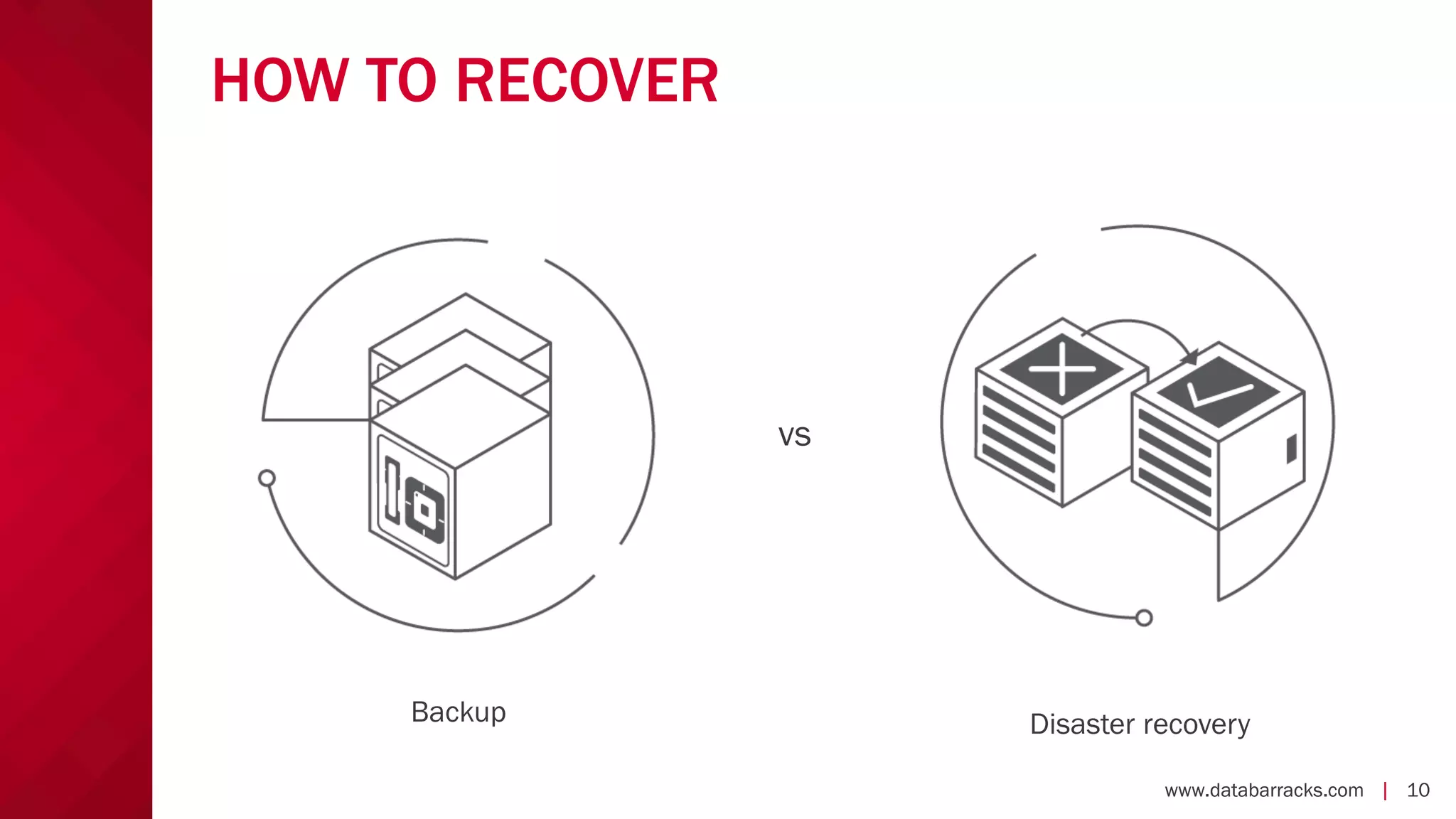
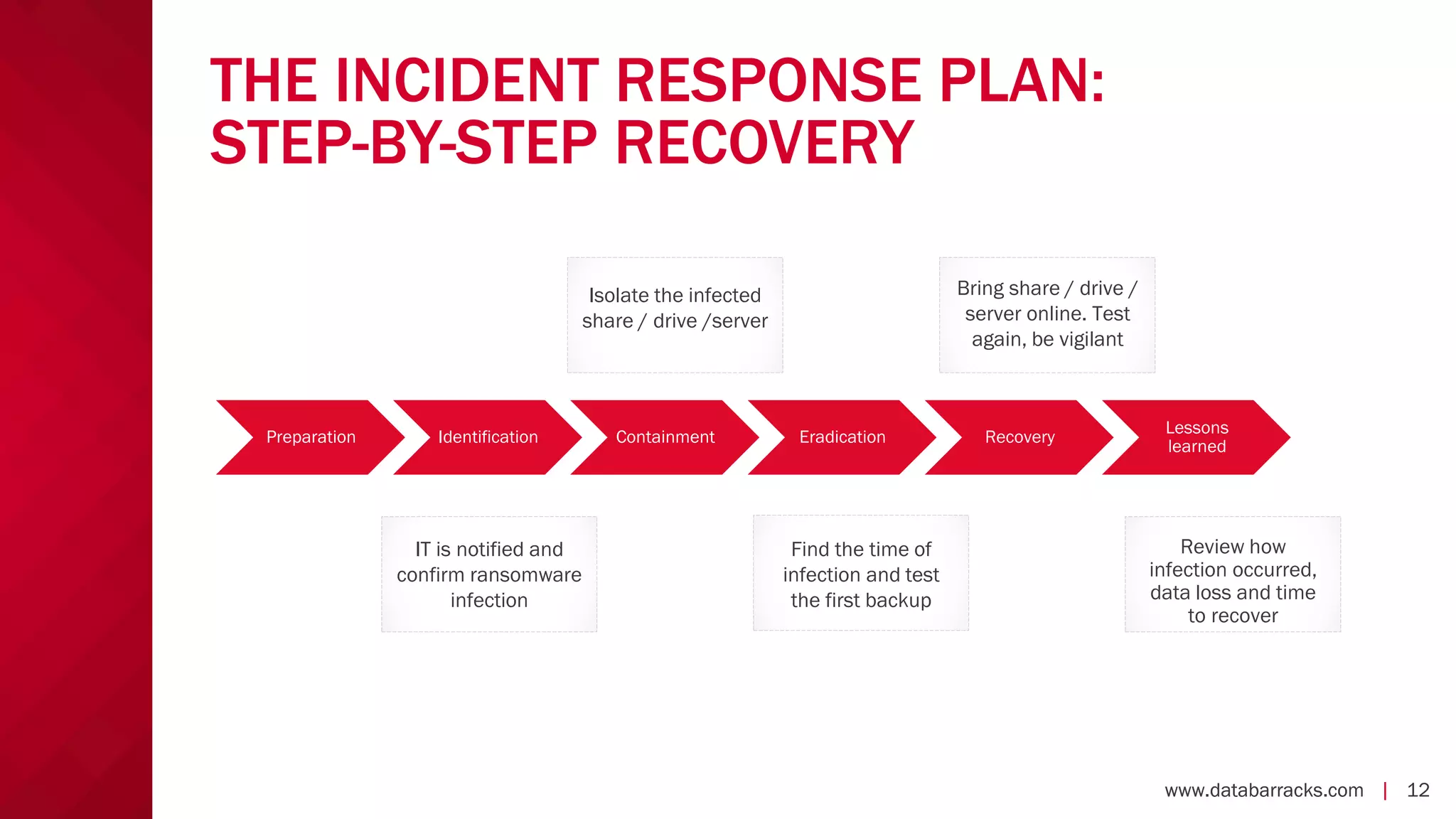
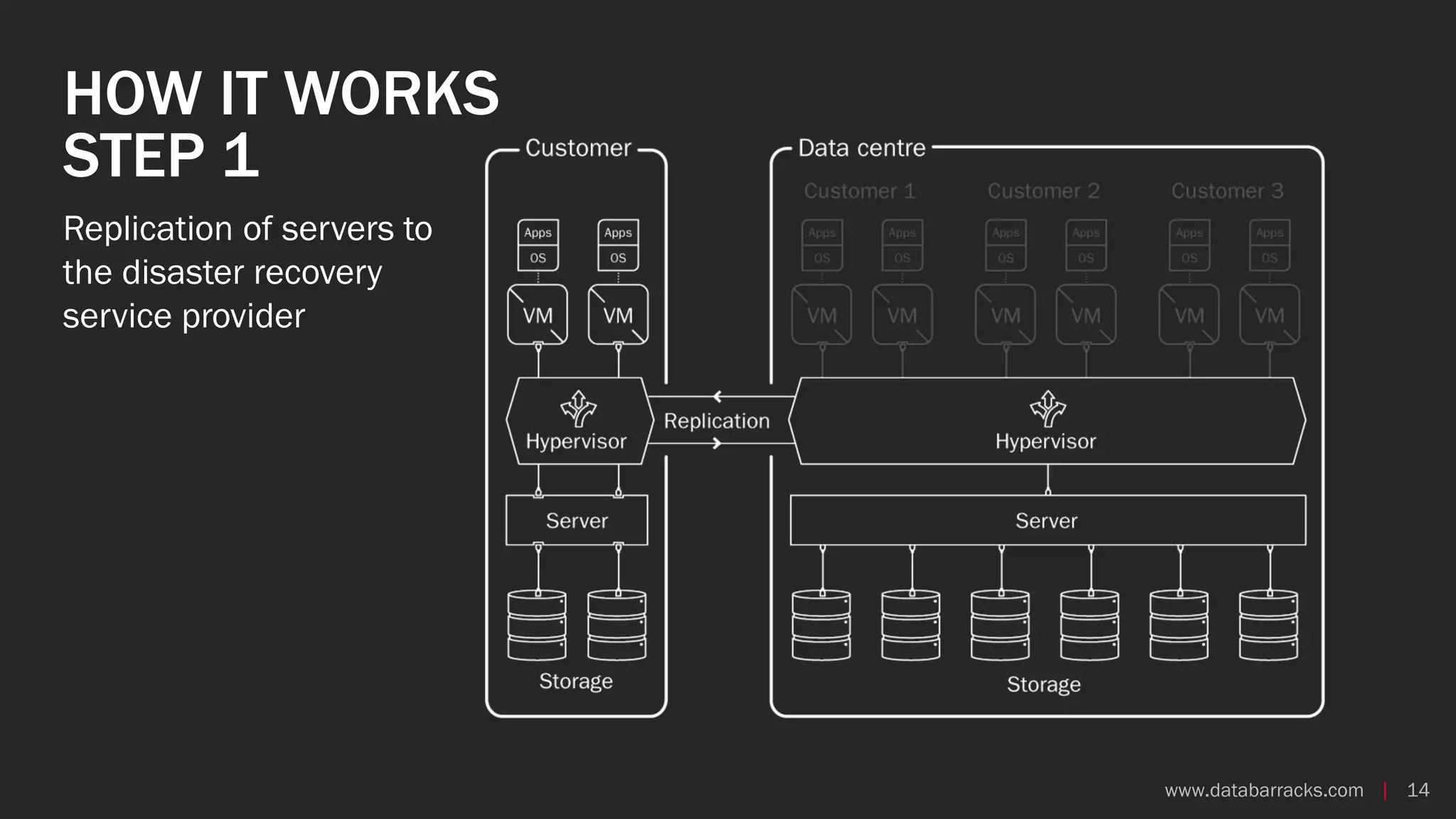
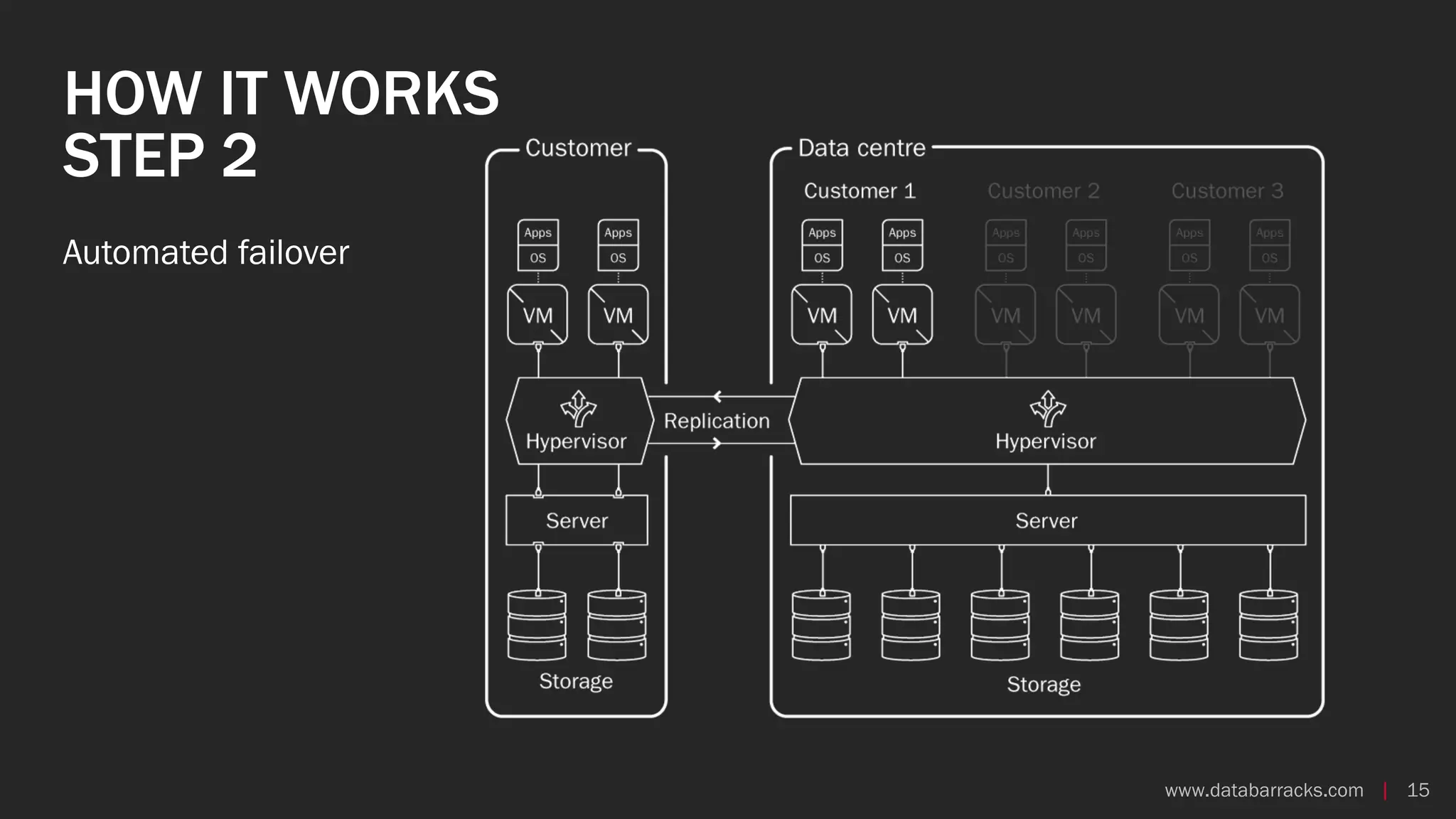
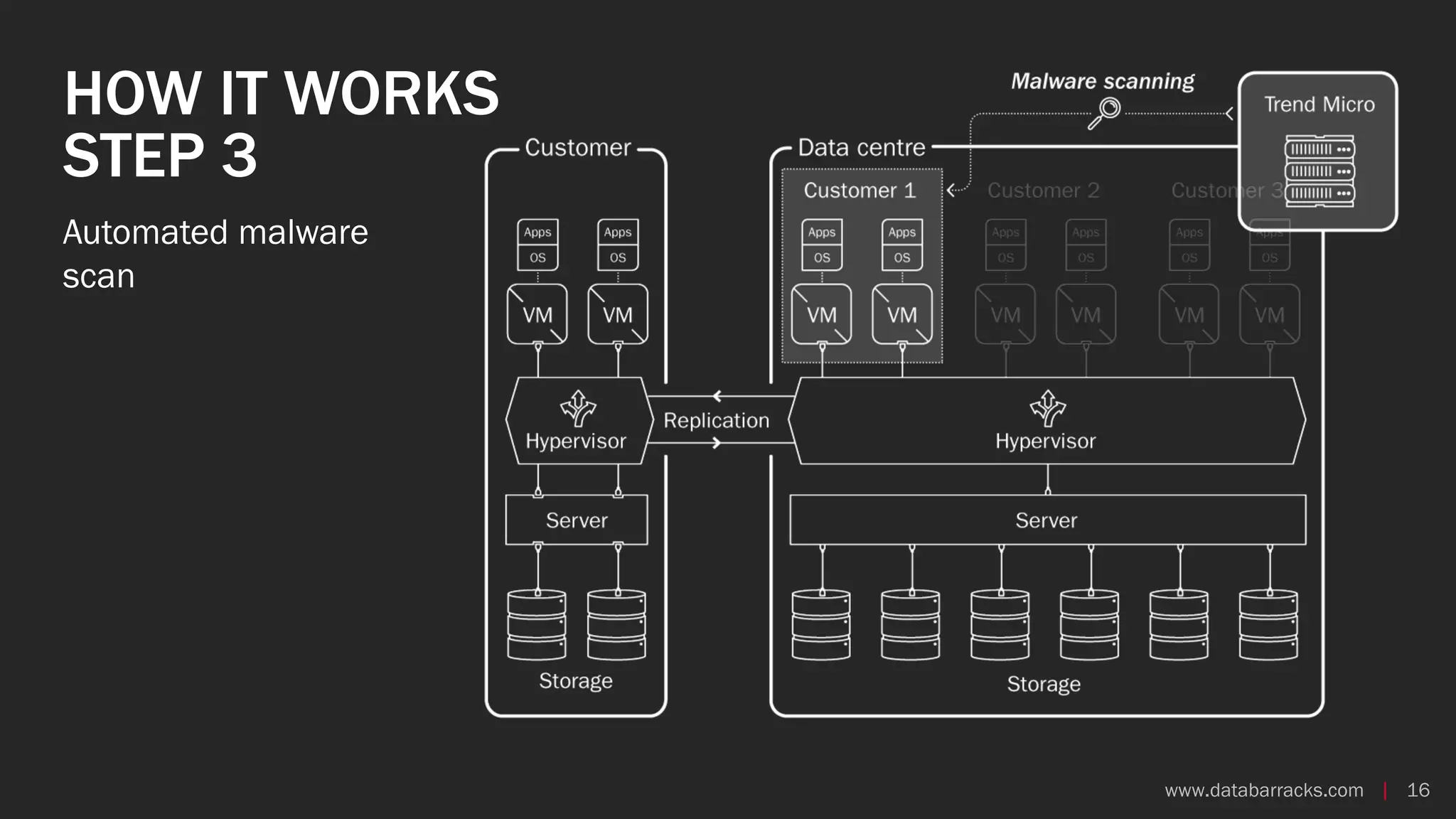
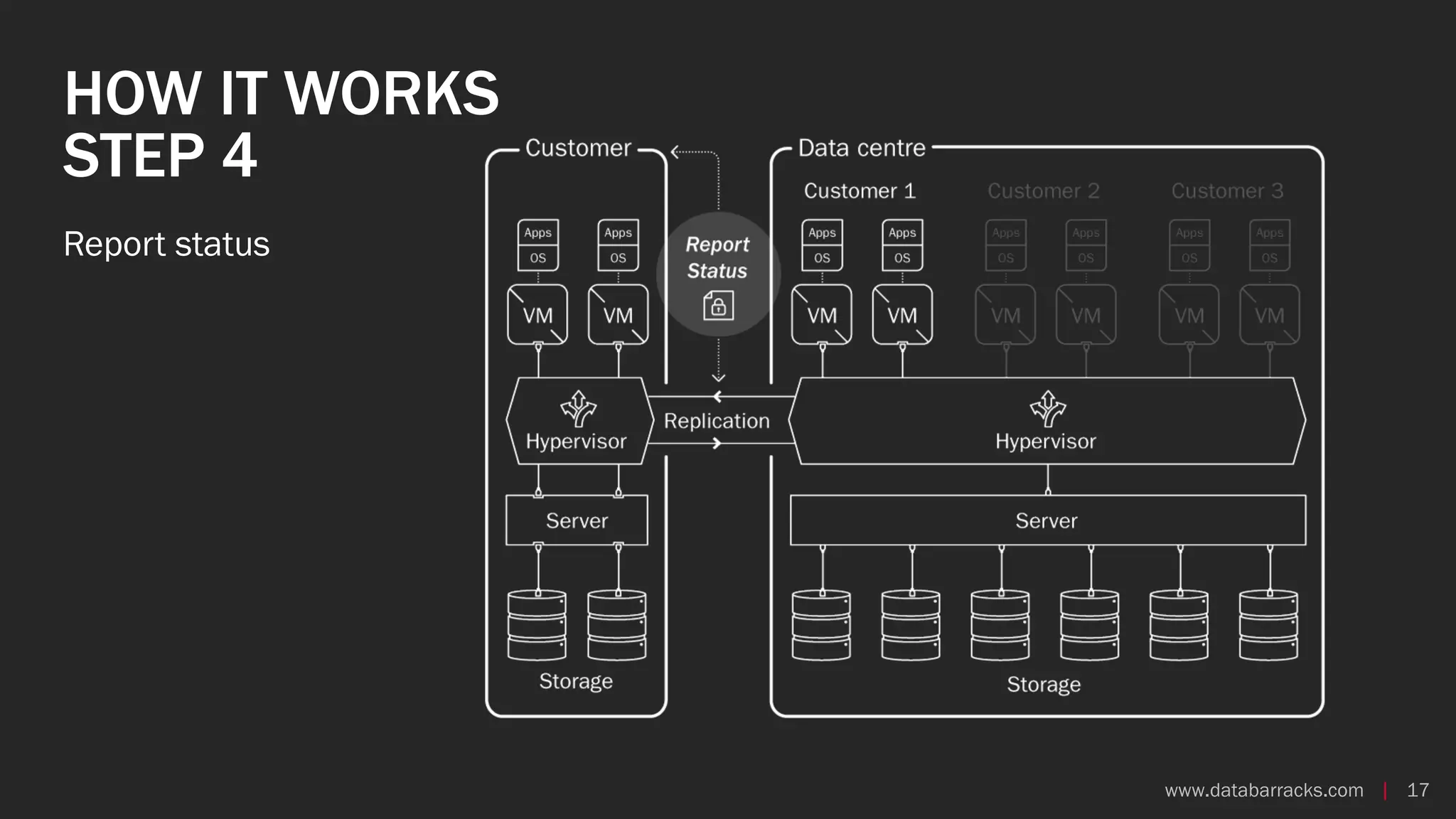
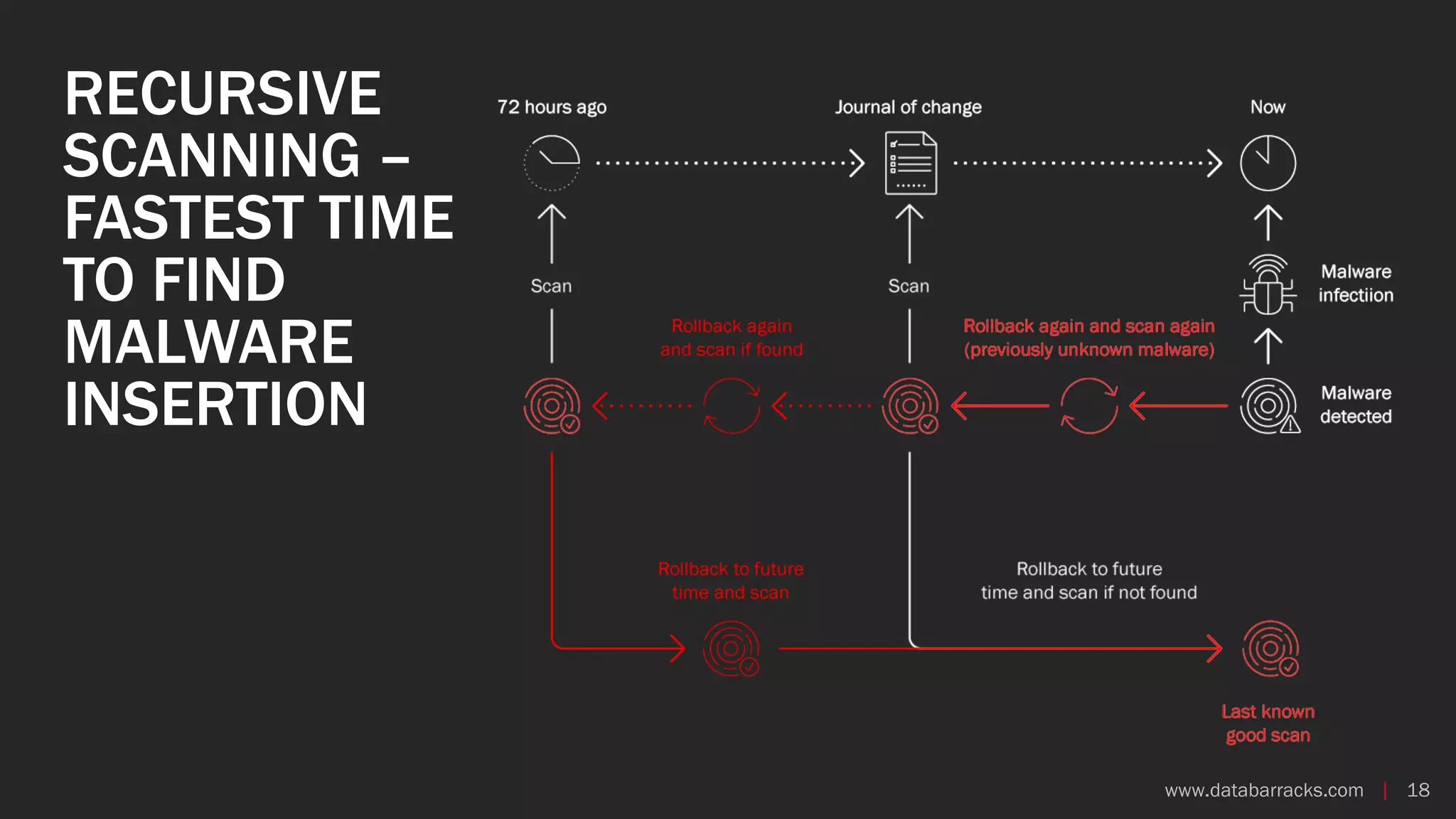
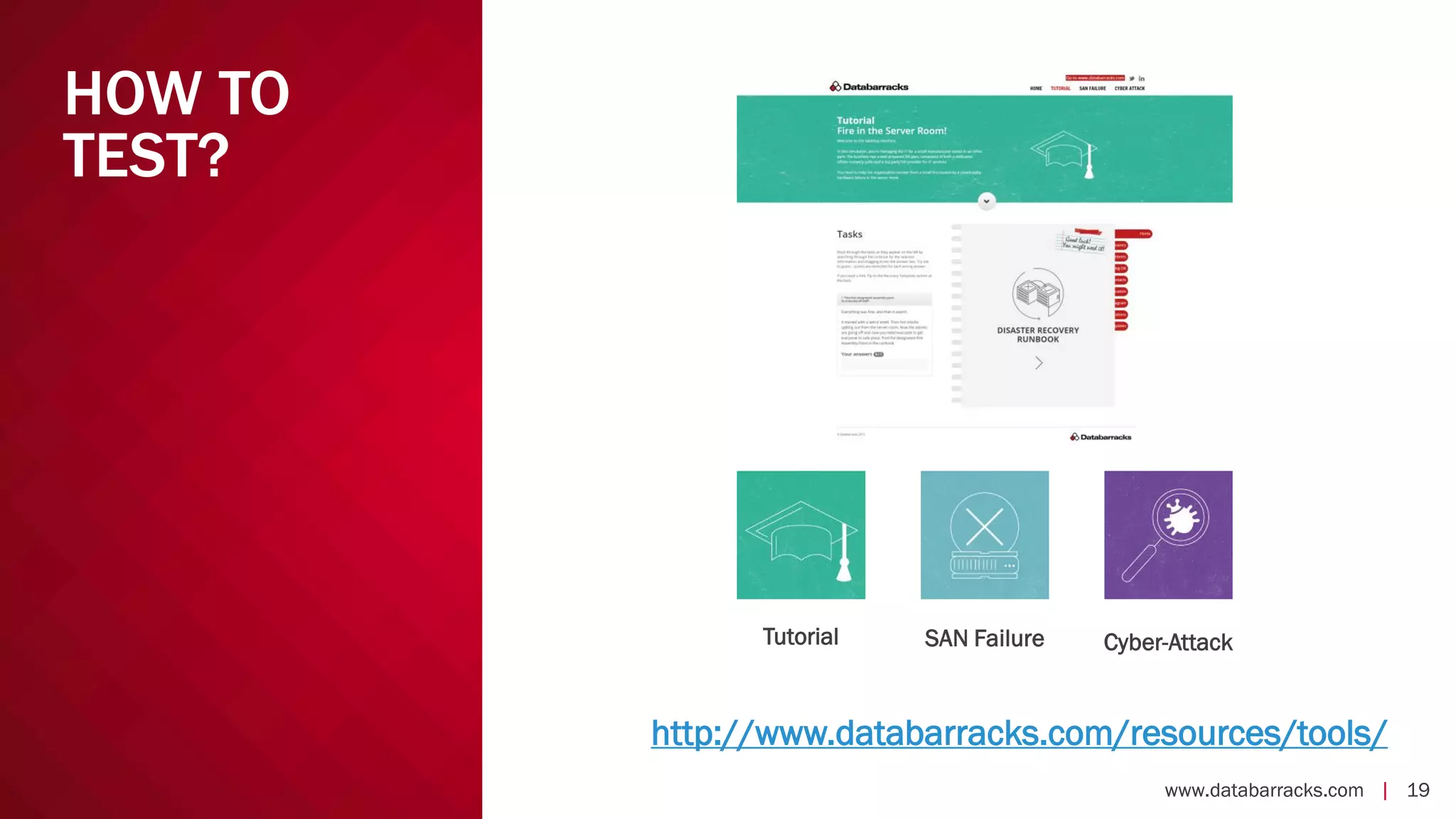
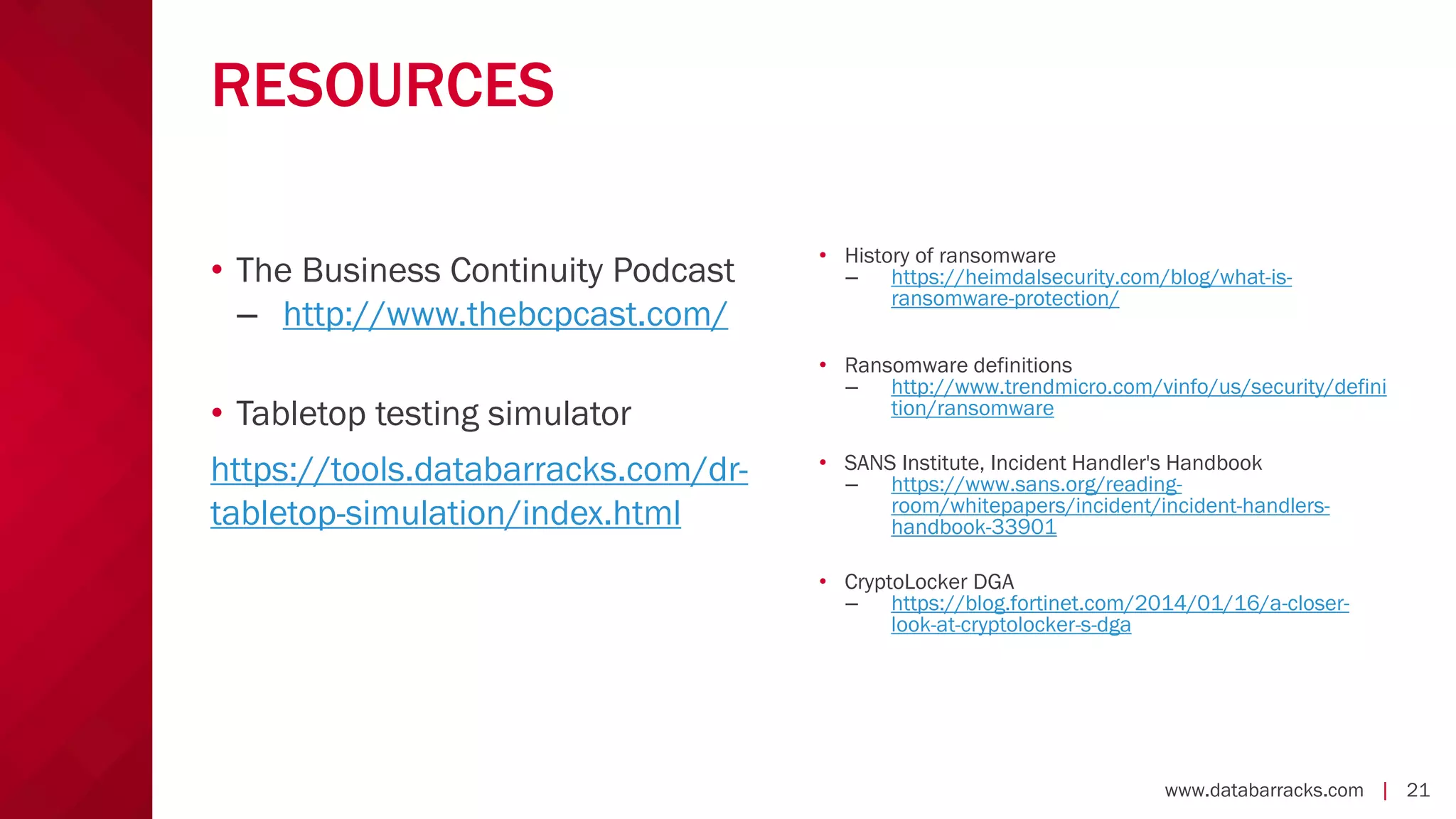
The document outlines key strategies for recovering from ransomware attacks, emphasizing the importance of having robust backup systems and incident response plans. It outlines the mechanisms of ransomware, the incident management process, and offers a step-by-step guide to effective recovery. Additionally, it provides resources for further information and recommendations for improving backup and recovery practices.