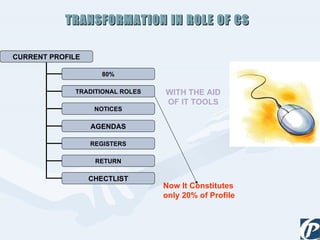
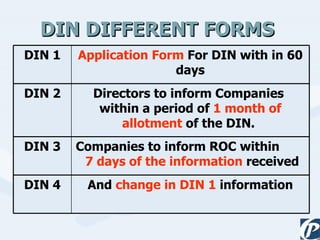
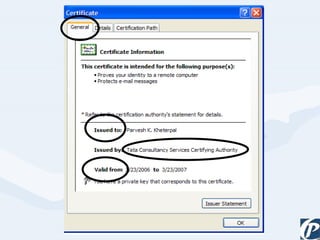
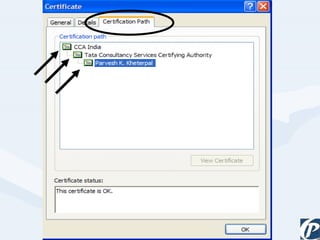
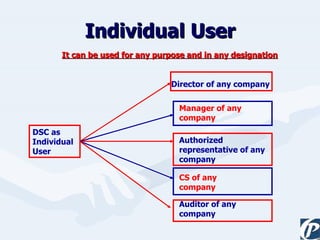
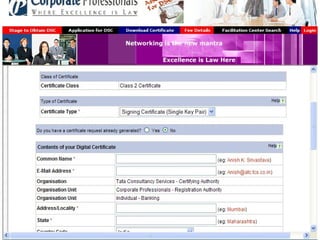
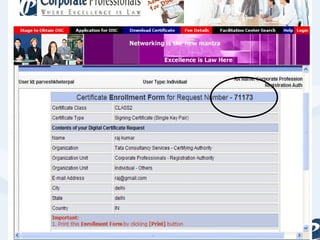
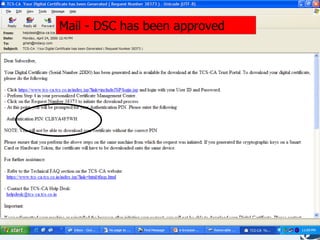
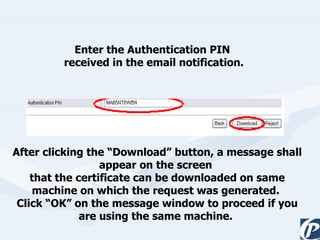
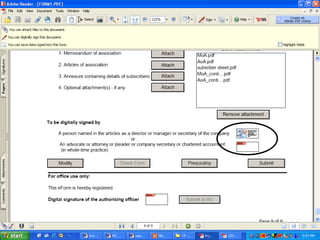
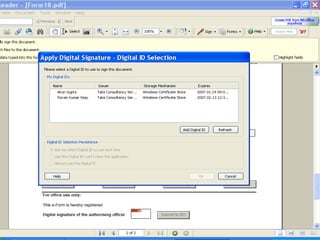
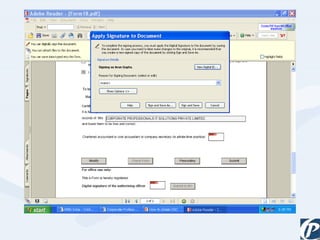
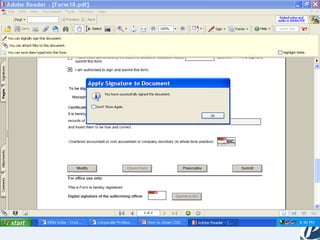
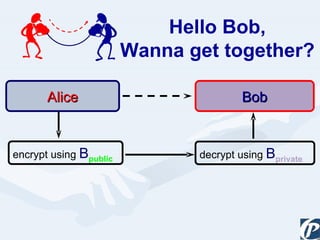
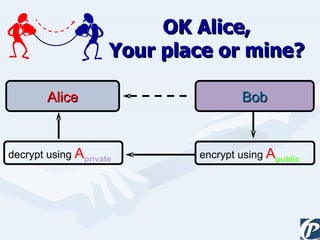
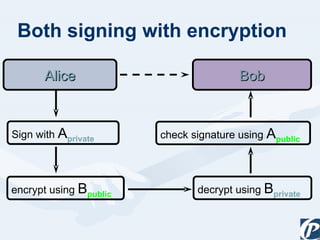
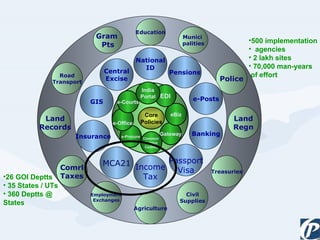
The document discusses the role of information technology in transforming the role of company secretaries. It explains how IT tools can help company secretaries reduce traditional administrative tasks from 80% to 20% of their role, and instead focus more on strategic activities like problem solving, management, and research. IT enables tasks like online filing of forms and returns, online secretarial audits, and video conferencing for meetings. This transformation allows company secretaries to take on more value-added work and opportunities.


![[email_address] Why IT e-governance Challenges for CS e - transformation Opportunities for CS](https://image.slidesharecdn.com/csit-120229040428-phpapp01/85/Information-Technology-Company-Secretary-3-320.jpg)