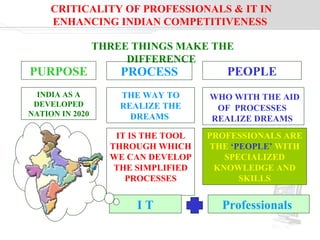
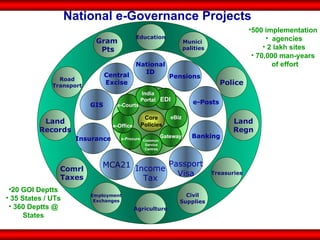
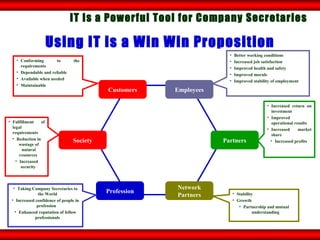
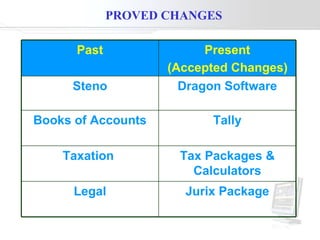
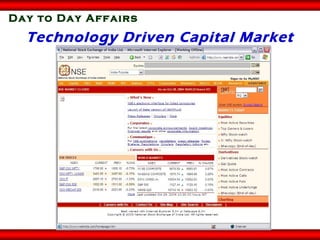
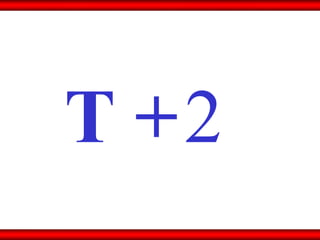
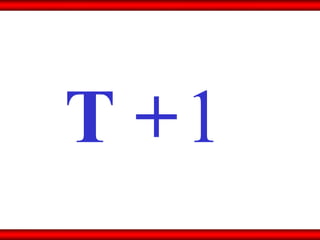
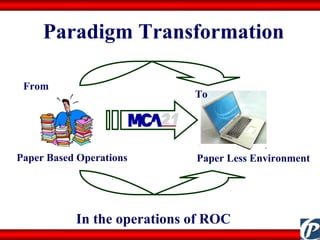
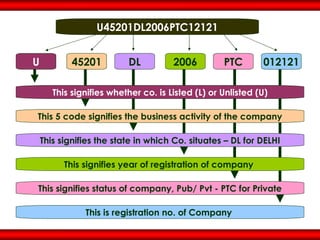
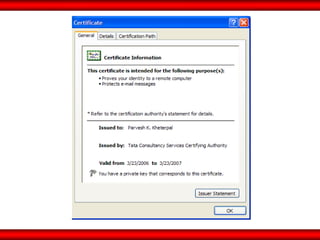
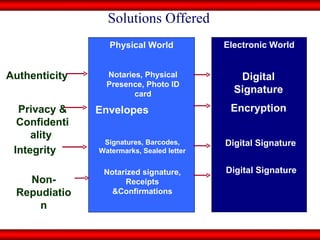
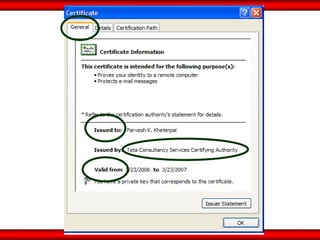
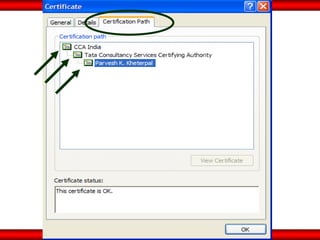
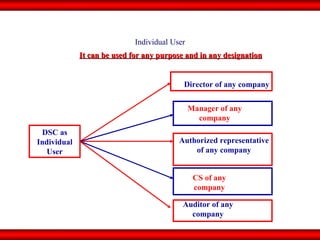
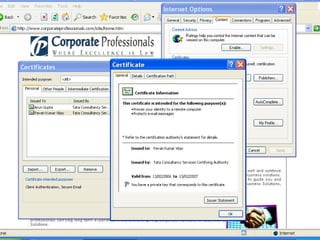
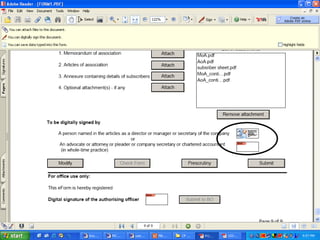
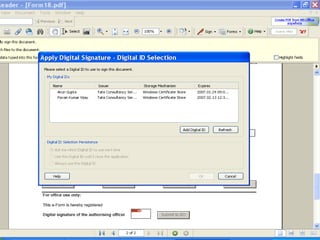
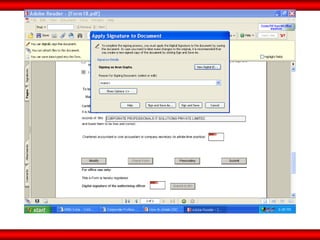
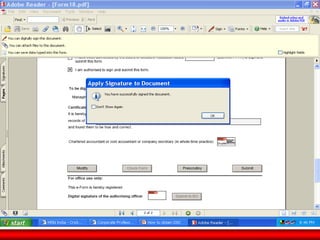
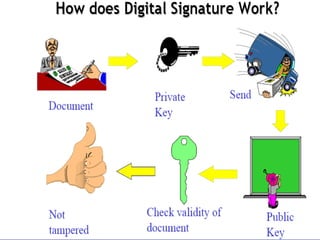
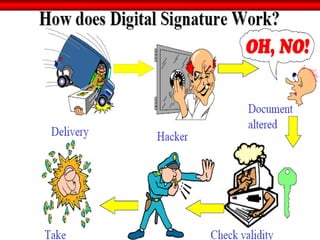
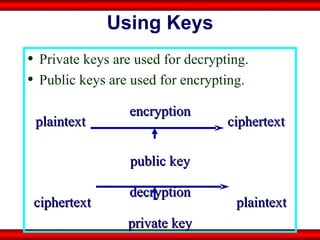
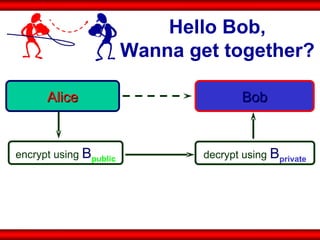
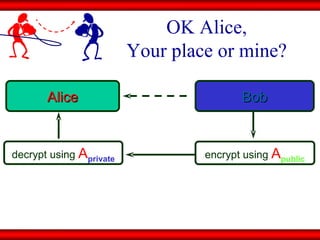
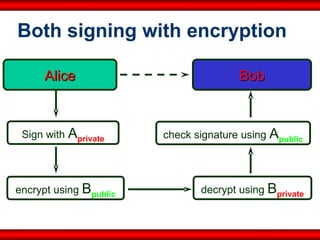
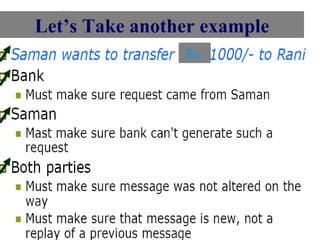
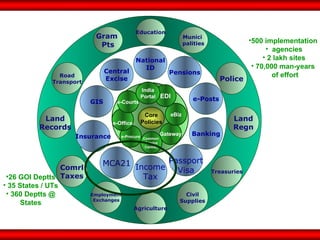
The document discusses the transformative role of information technology (IT) for company secretaries (CS) in India, highlighting its impact on e-governance and the transition from traditional practices to more strategic roles. It emphasizes the importance of IT in various sectors, including global trade, transparency, and efficiency within governmental functions, while also detailing the benefits of using digital signatures. The document outlines challenges and opportunities presented by IT for CS, advocating for a shift in mindset and the adoption of new technologies to enhance professional services.


![[email_address] Why IT e-governance Challenges for CS e - transformation Opportunities for CS Digital Signature Certificates Encryption & Decryption](https://image.slidesharecdn.com/csit14-03-08smtp-120229034432-phpapp01/85/Company-Secretary-and-Information-technology-6-320.jpg)