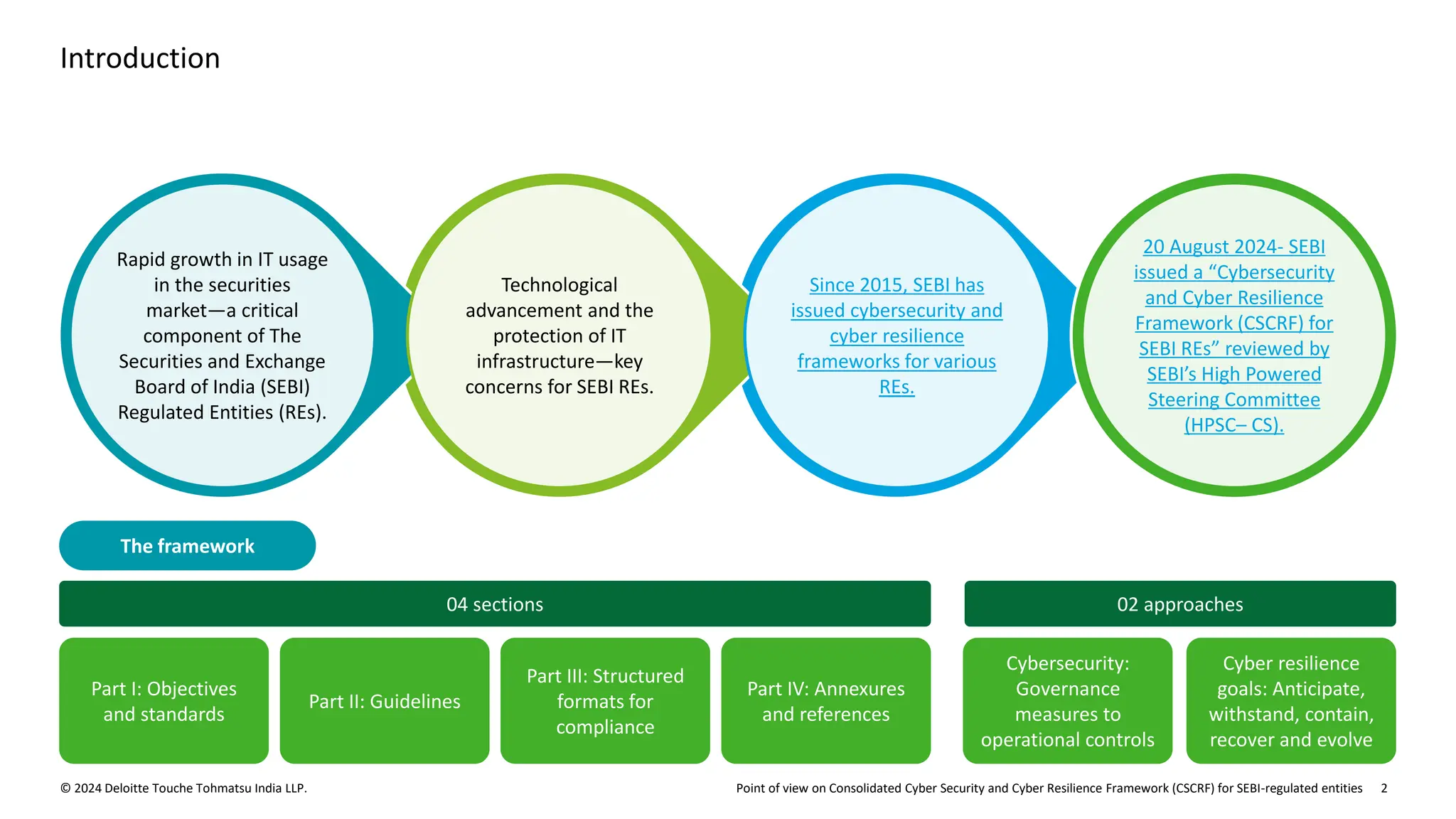
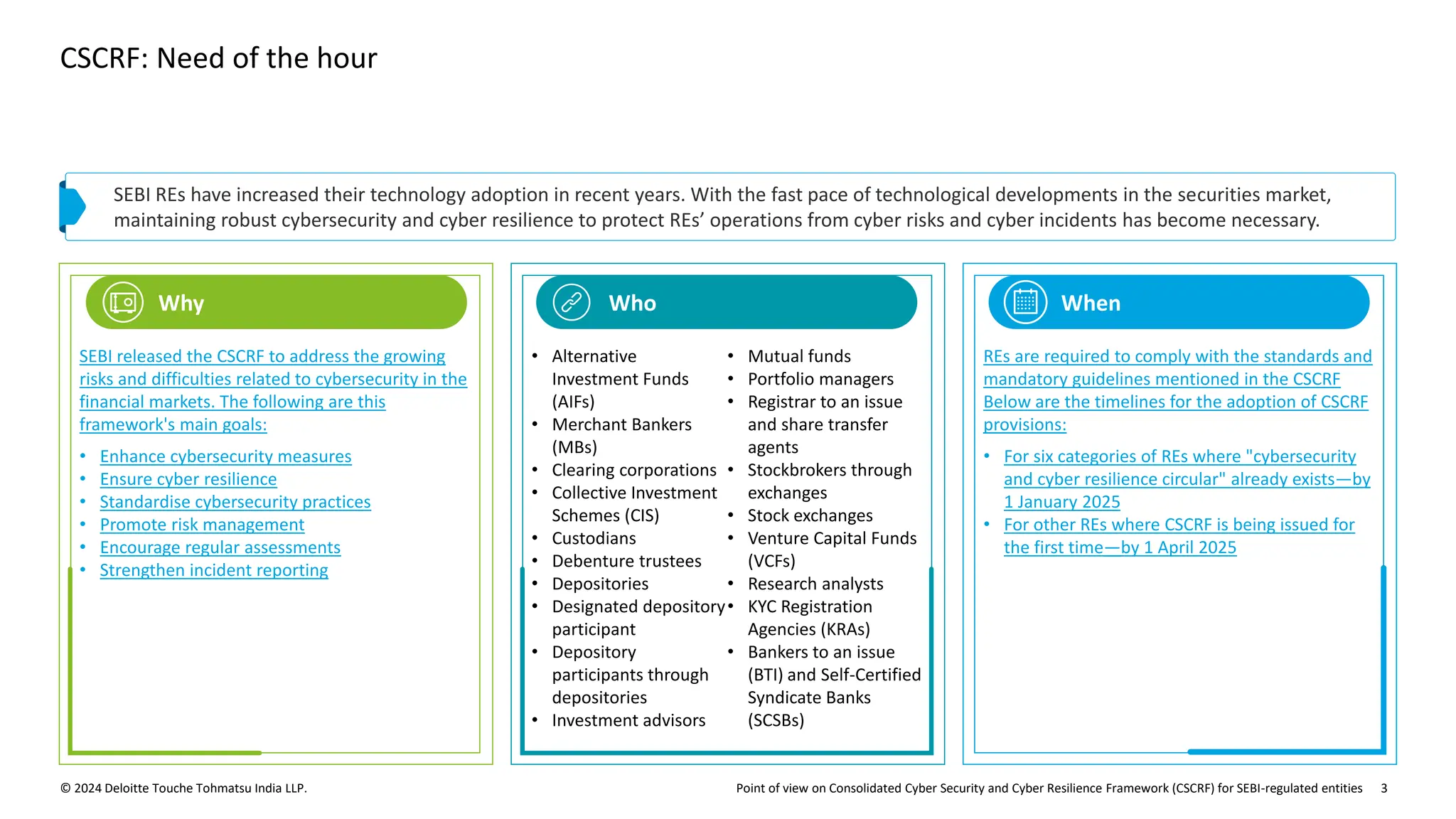
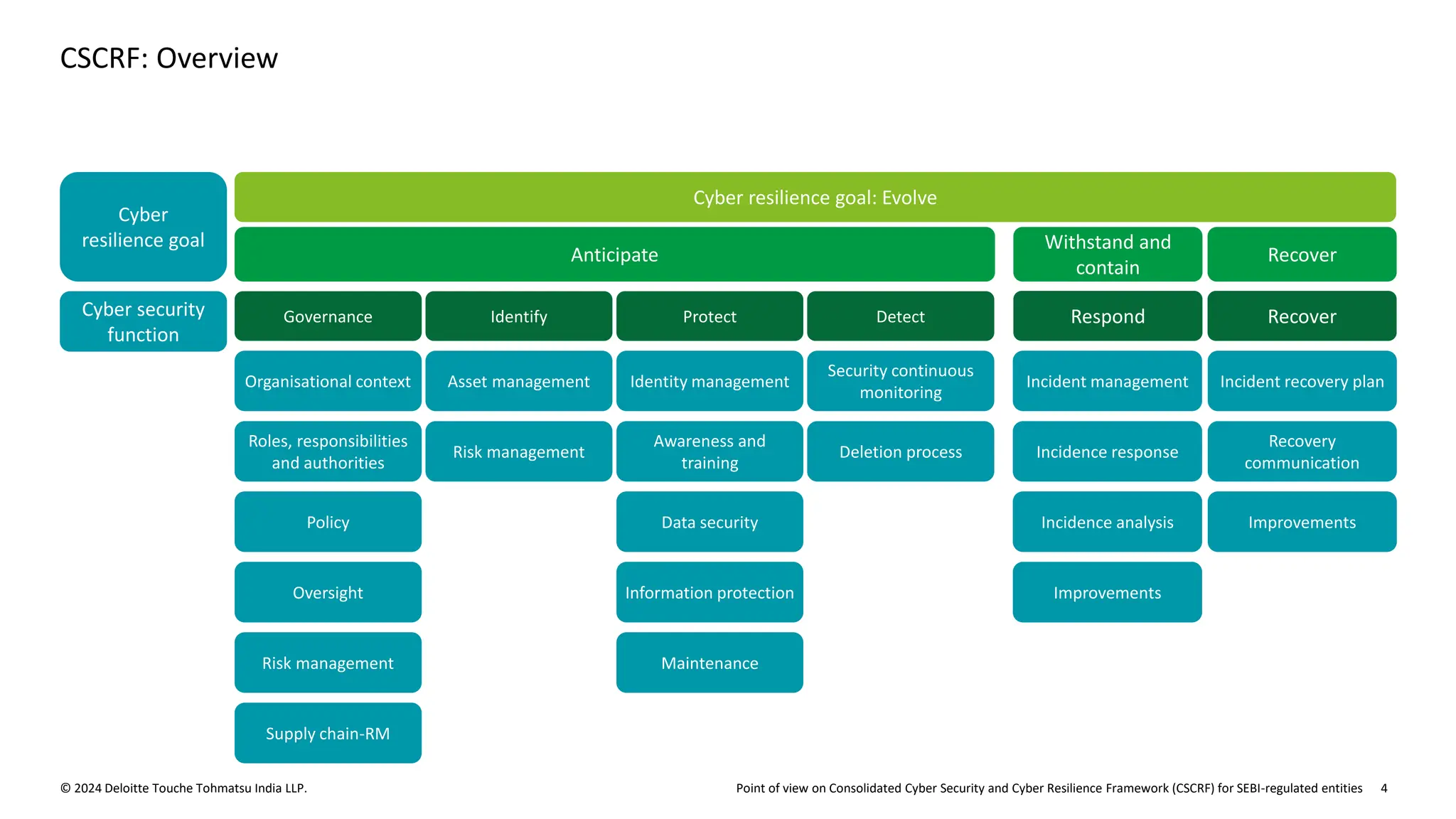
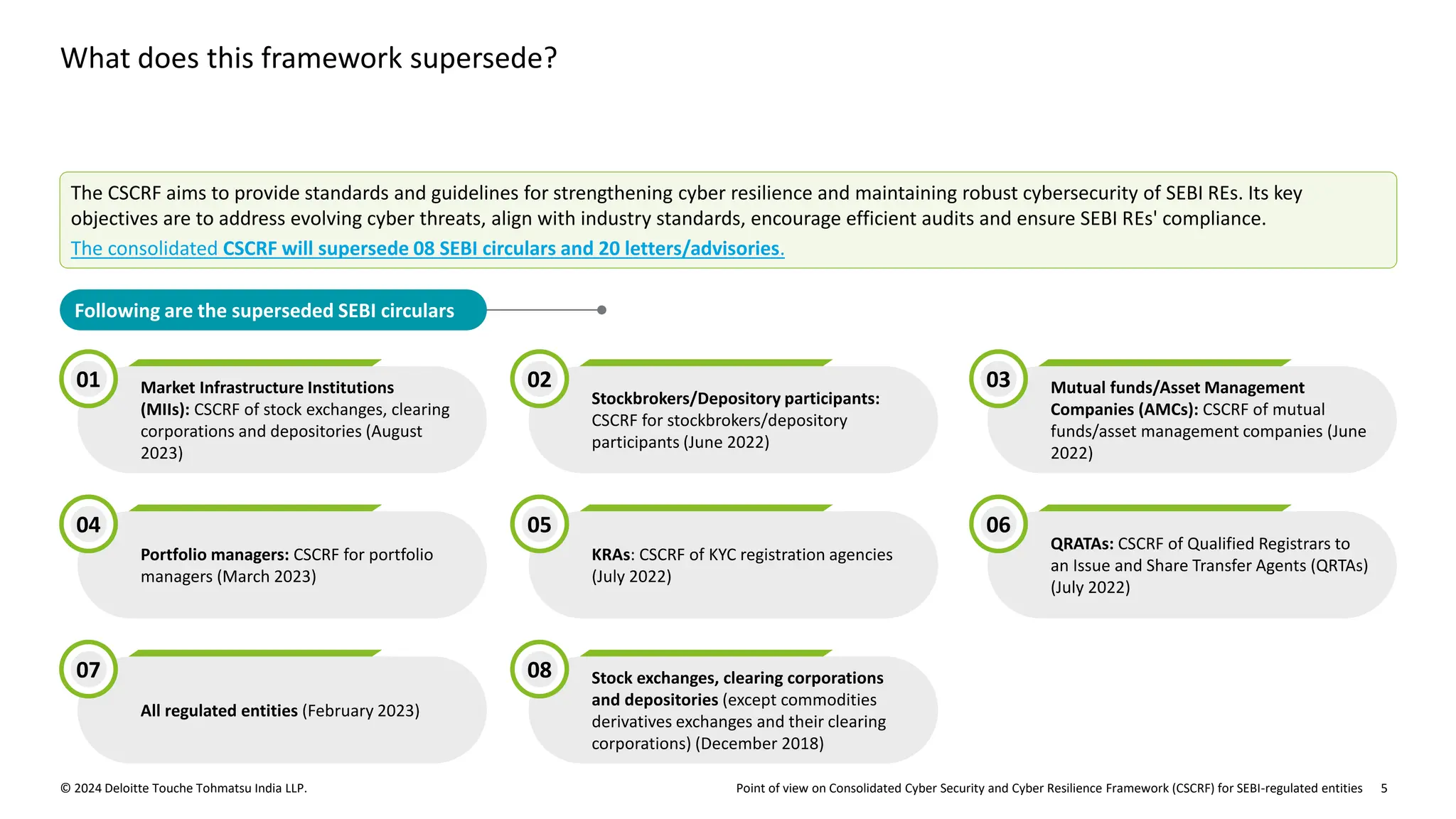
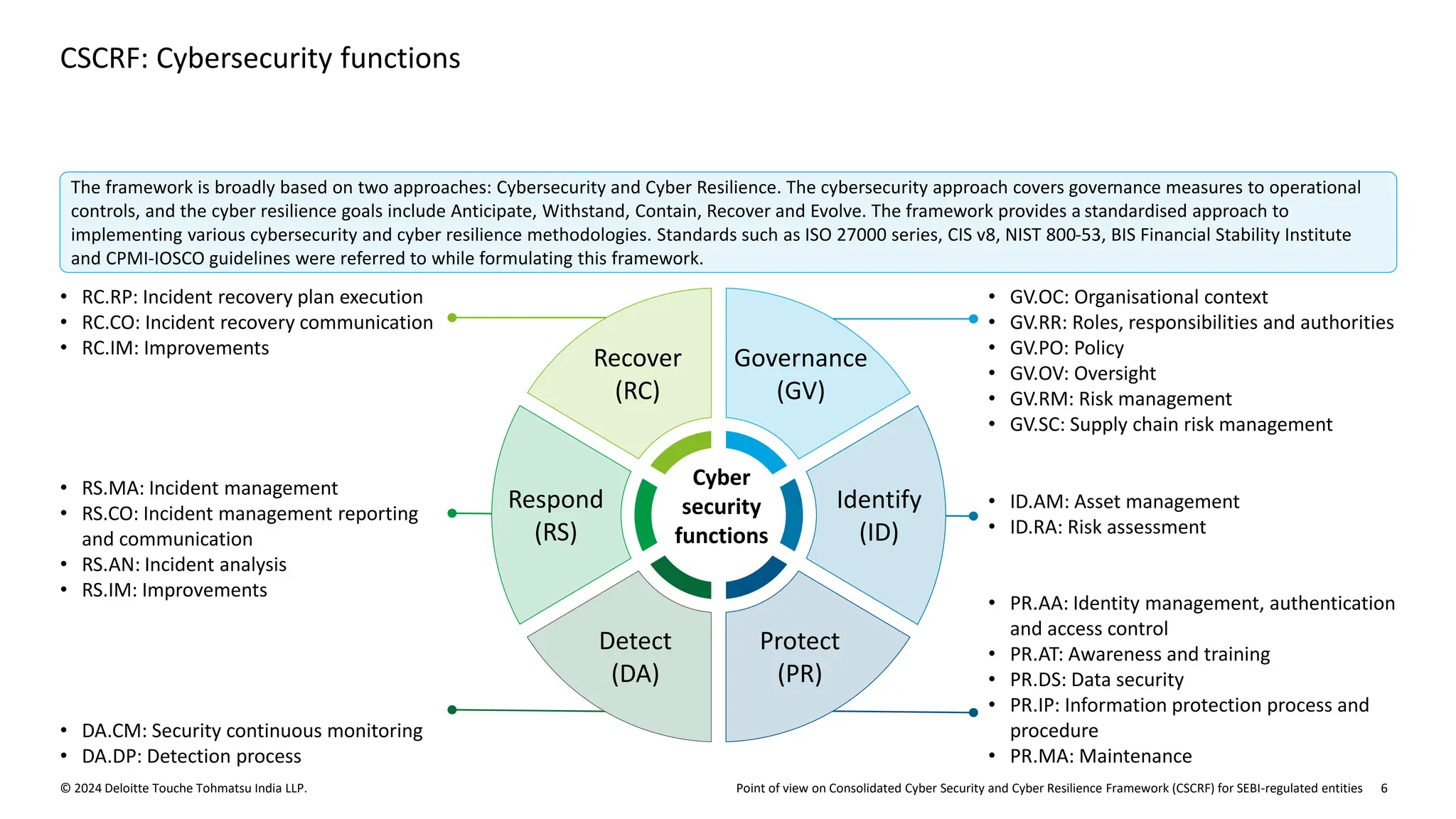
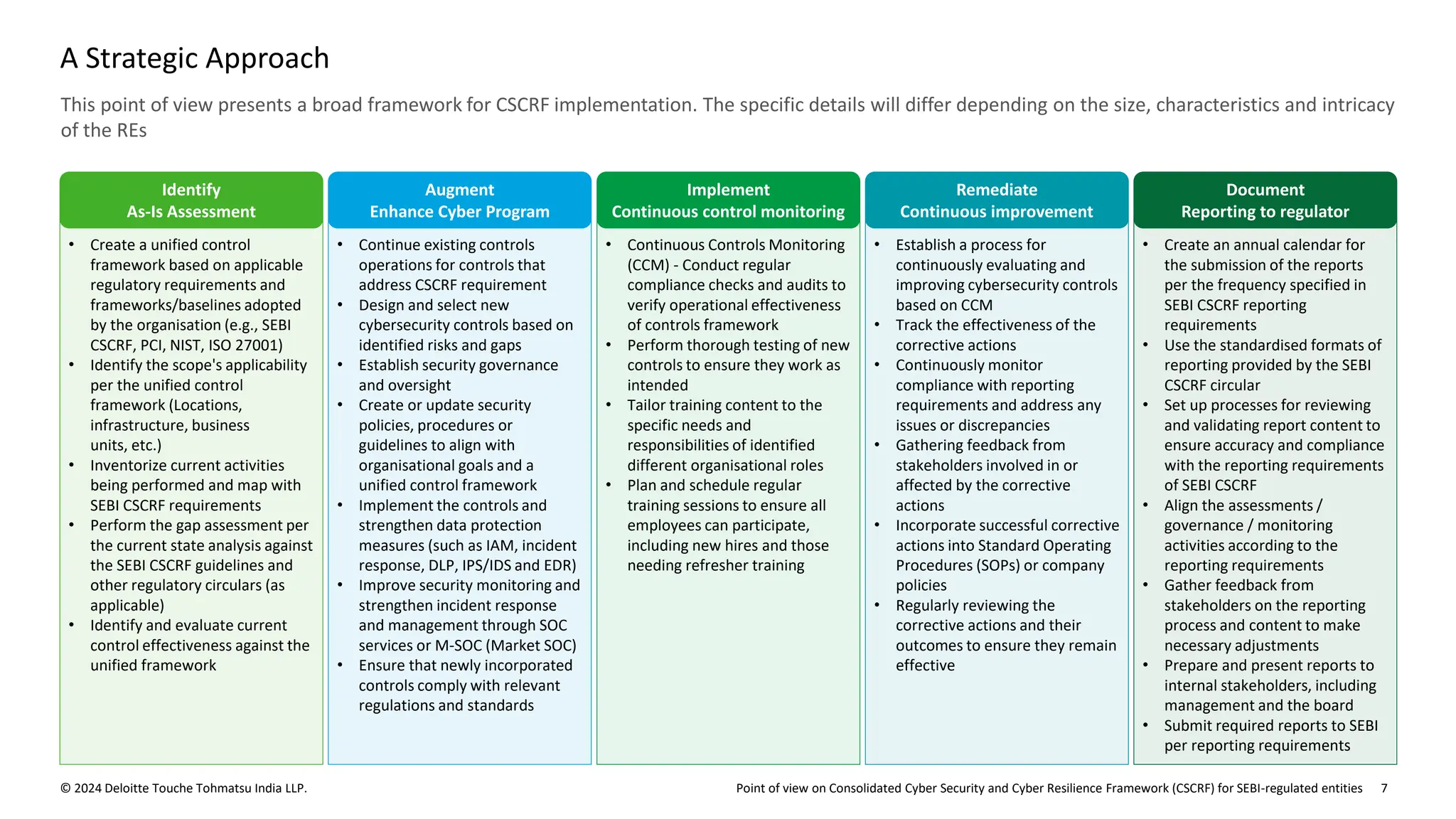
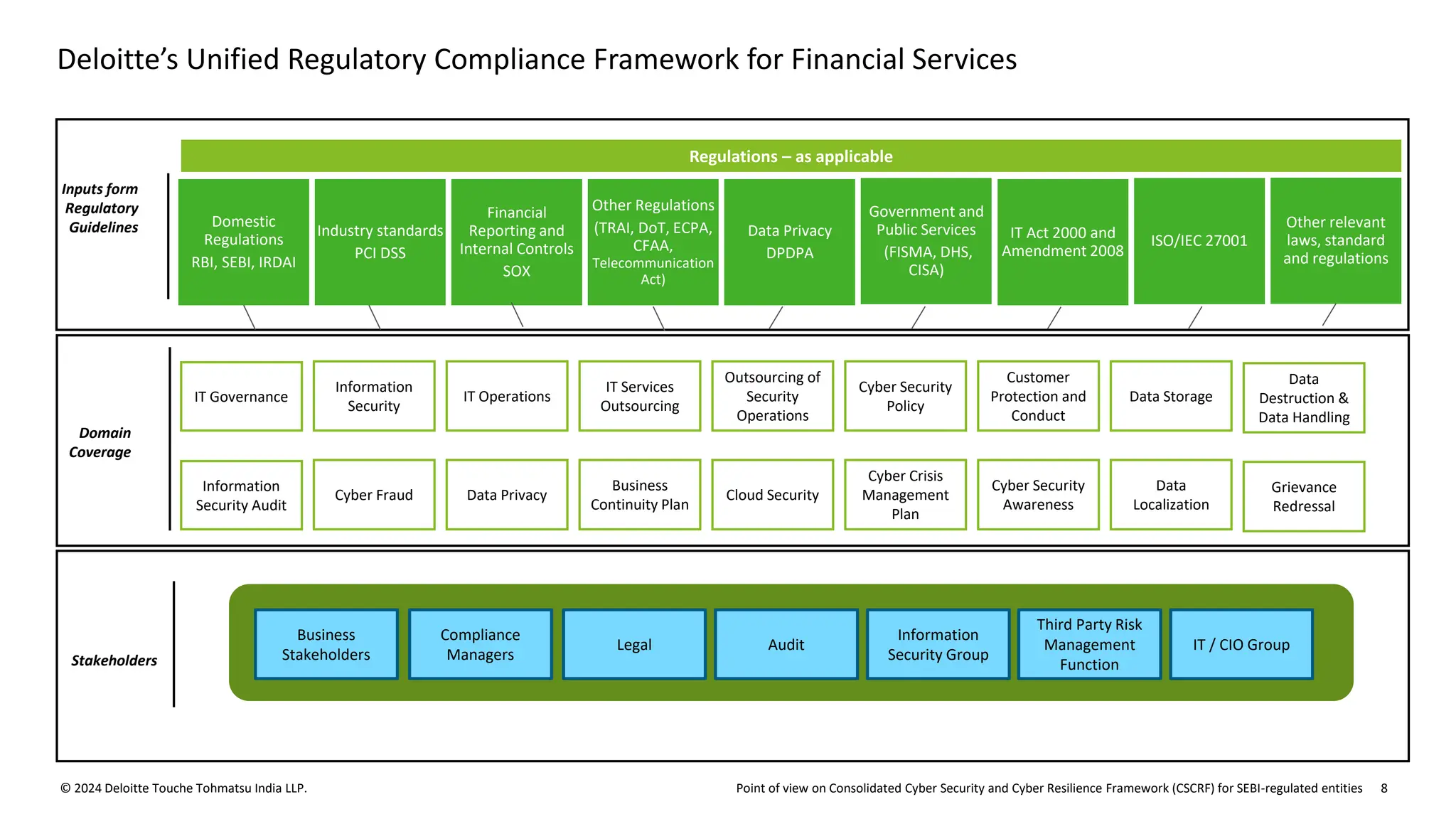
The document outlines the Cybersecurity and Cyber Resilience Framework (CSCRF) issued by SEBI for its regulated entities to enhance cybersecurity measures and ensure compliance with evolving cyber threats. It emphasizes the necessity for regulated entities to adopt robust cybersecurity practices by specific deadlines and provides a structured overview of compliance, governance, and operational controls. The CSCRF aims to standardize practices across various categories of financial institutions while superseding earlier circulars and guidelines.