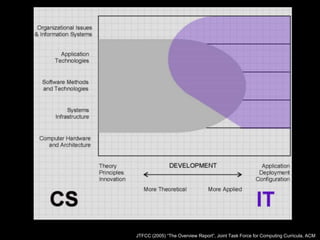
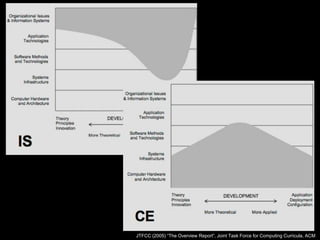
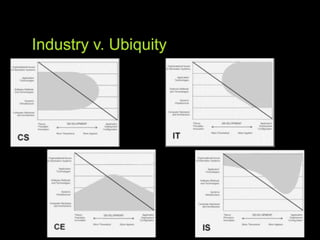
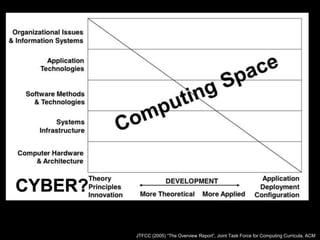
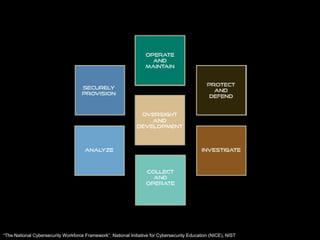
This document discusses cybersecurity as a discipline and proposes frameworks for defining the cybersecurity workforce. It summarizes a report that defines cybersecurity as an interdisciplinary field involving technology, people, processes, and risk management. It also outlines frameworks developed by the National Initiative for Cybersecurity Education (NICE) and ACM/IEEE that define the cybersecurity workforce using categories, specialty areas, and typical tasks and skills. The NICE framework establishes seven categories and thirty-one specialty areas to describe all cybersecurity work.