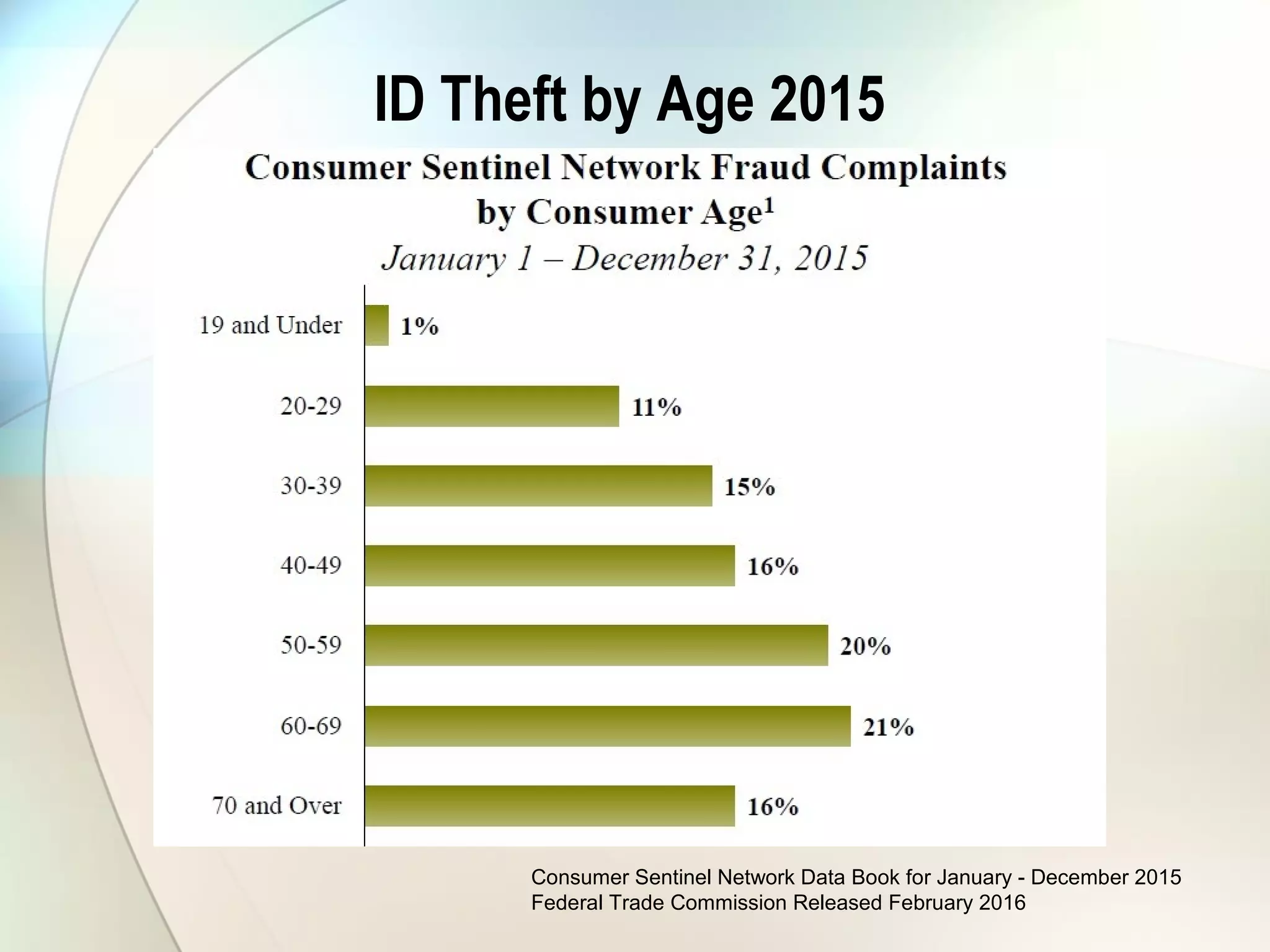
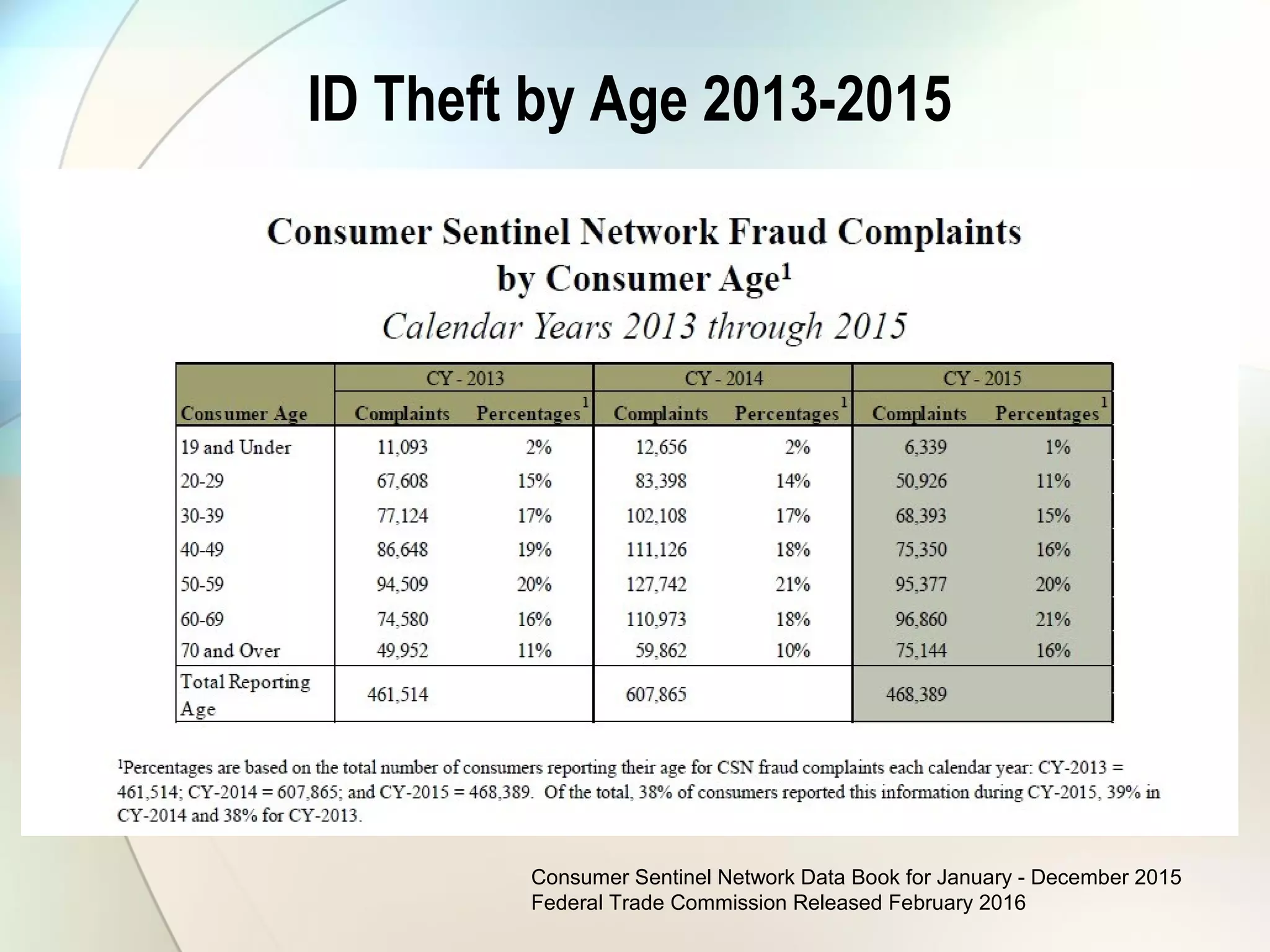
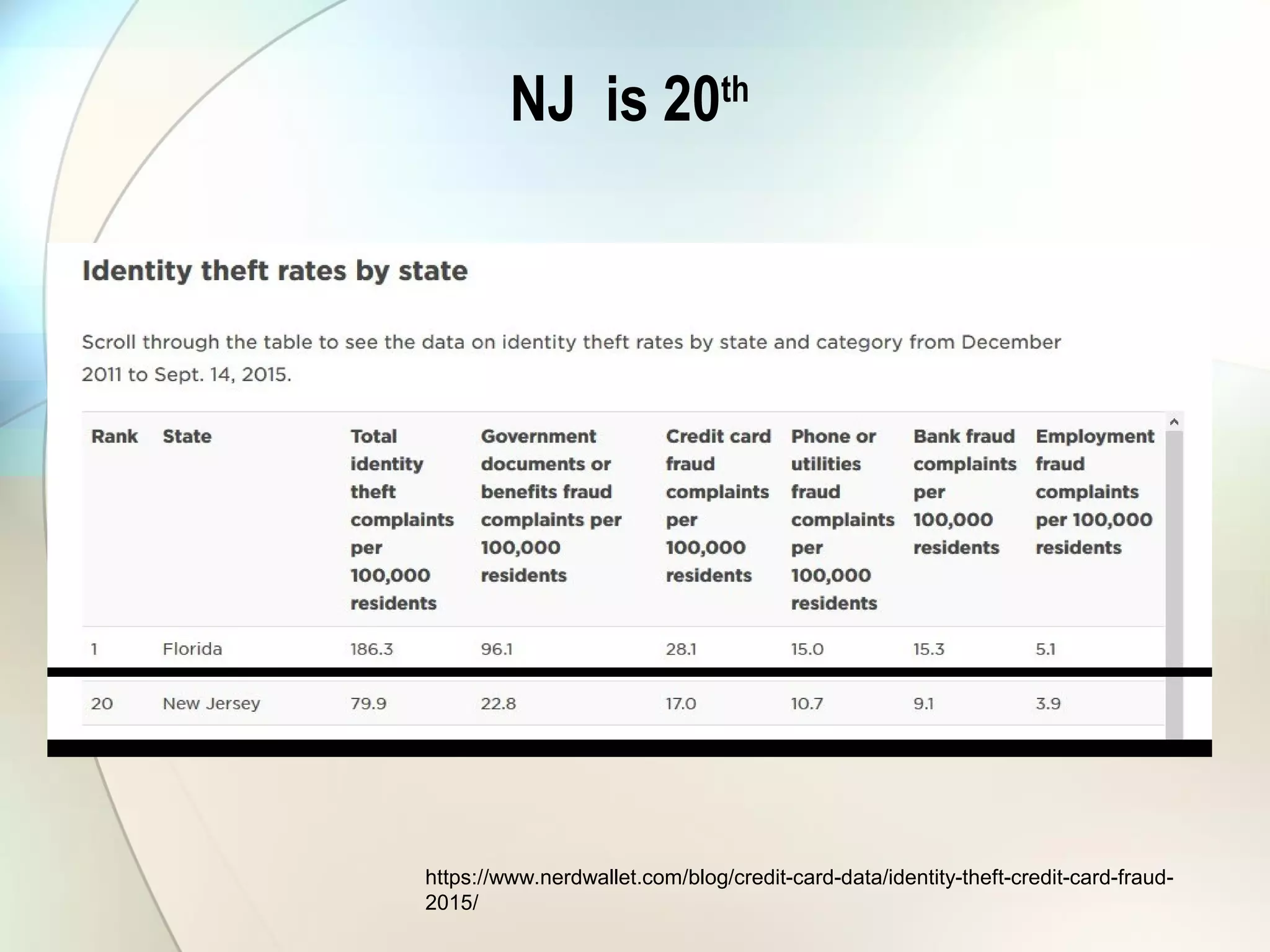
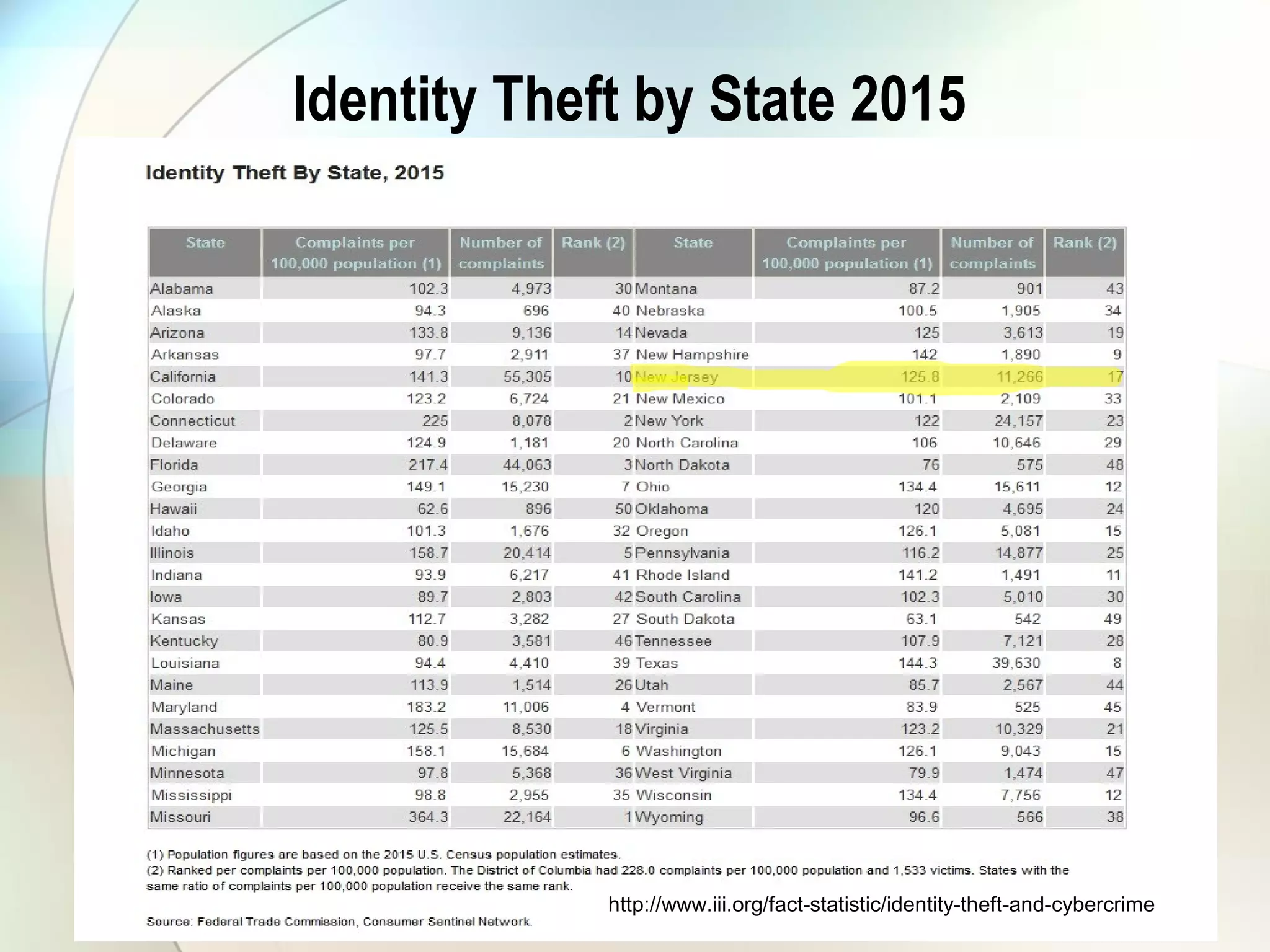
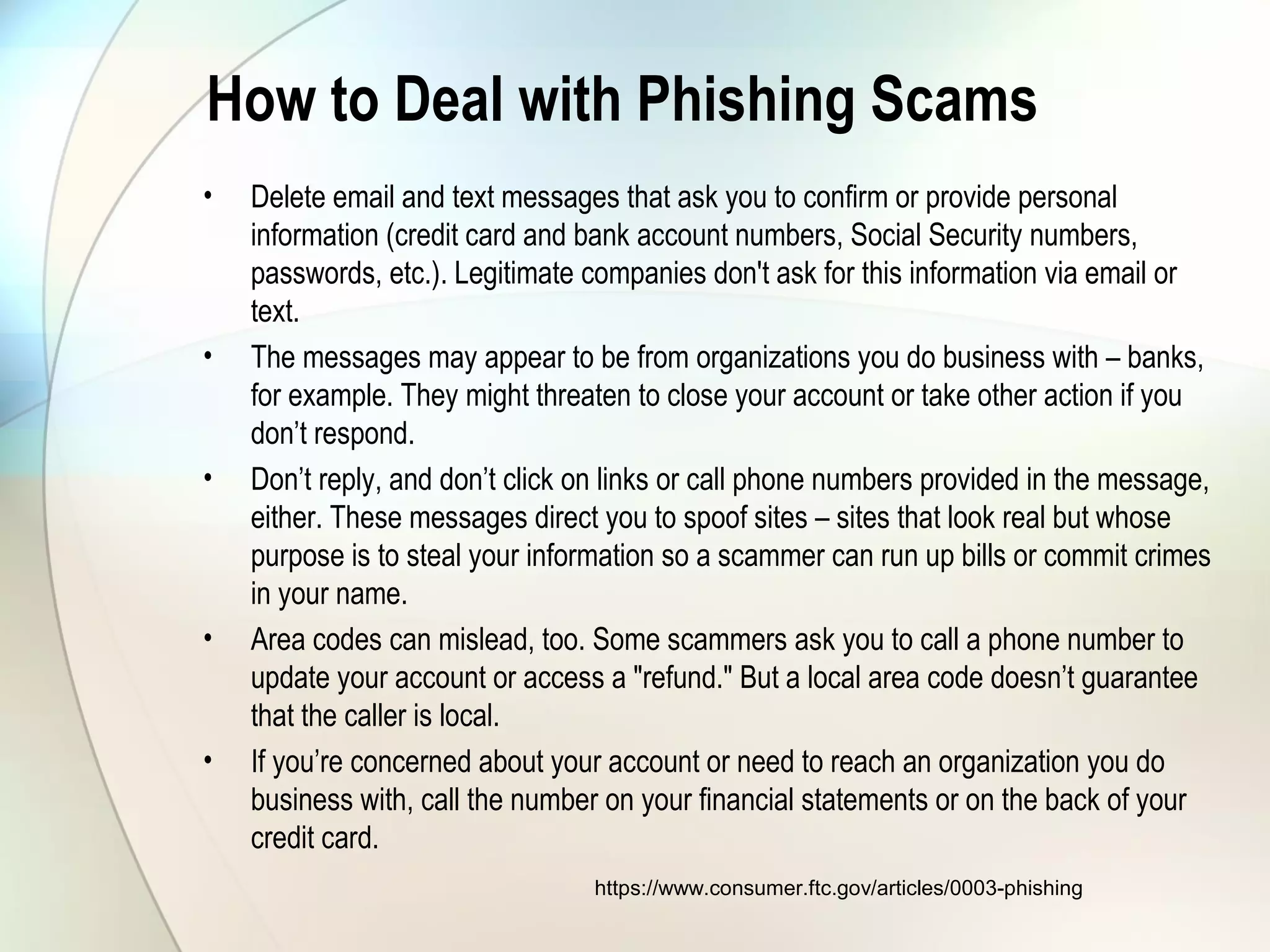
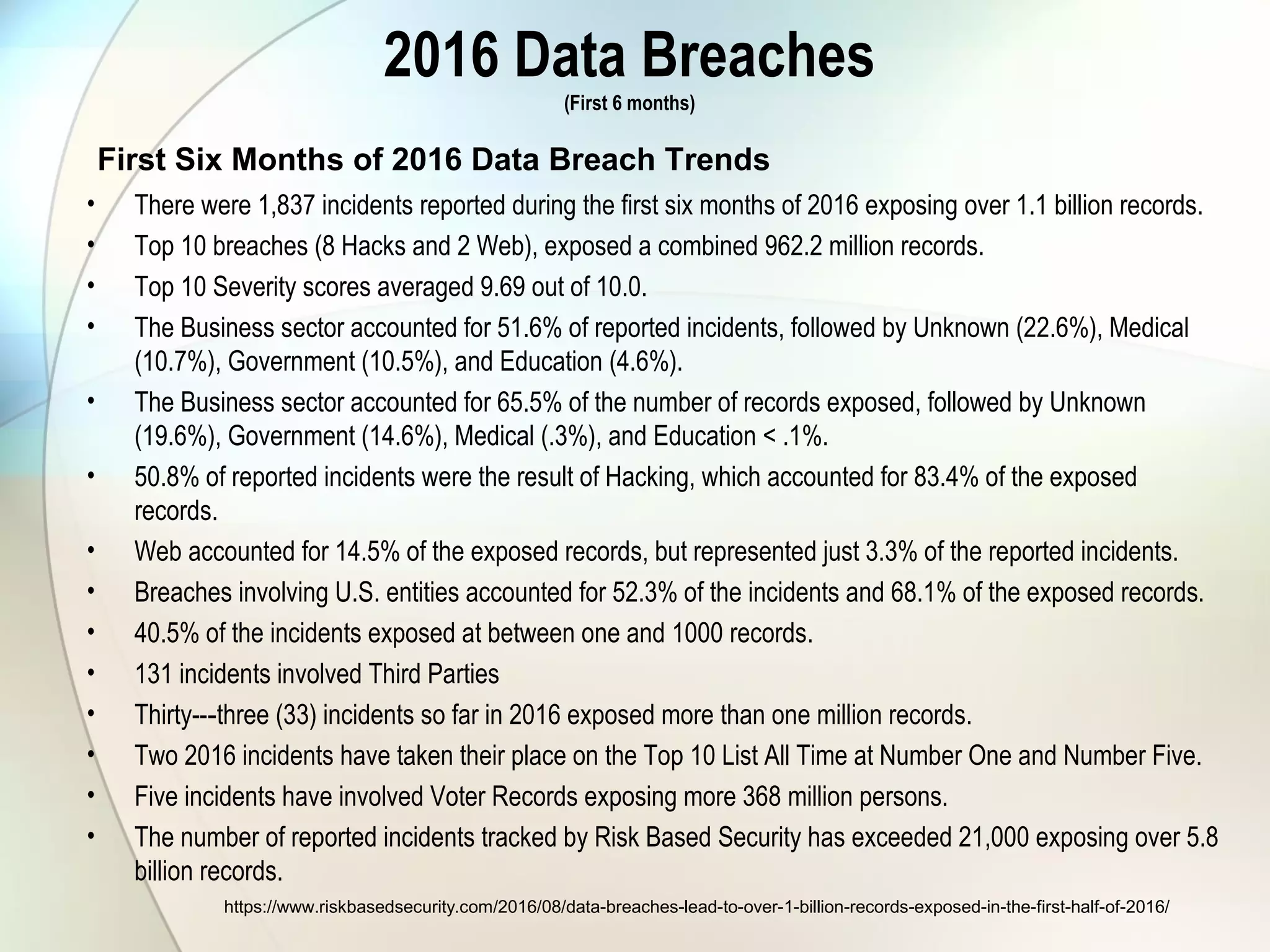
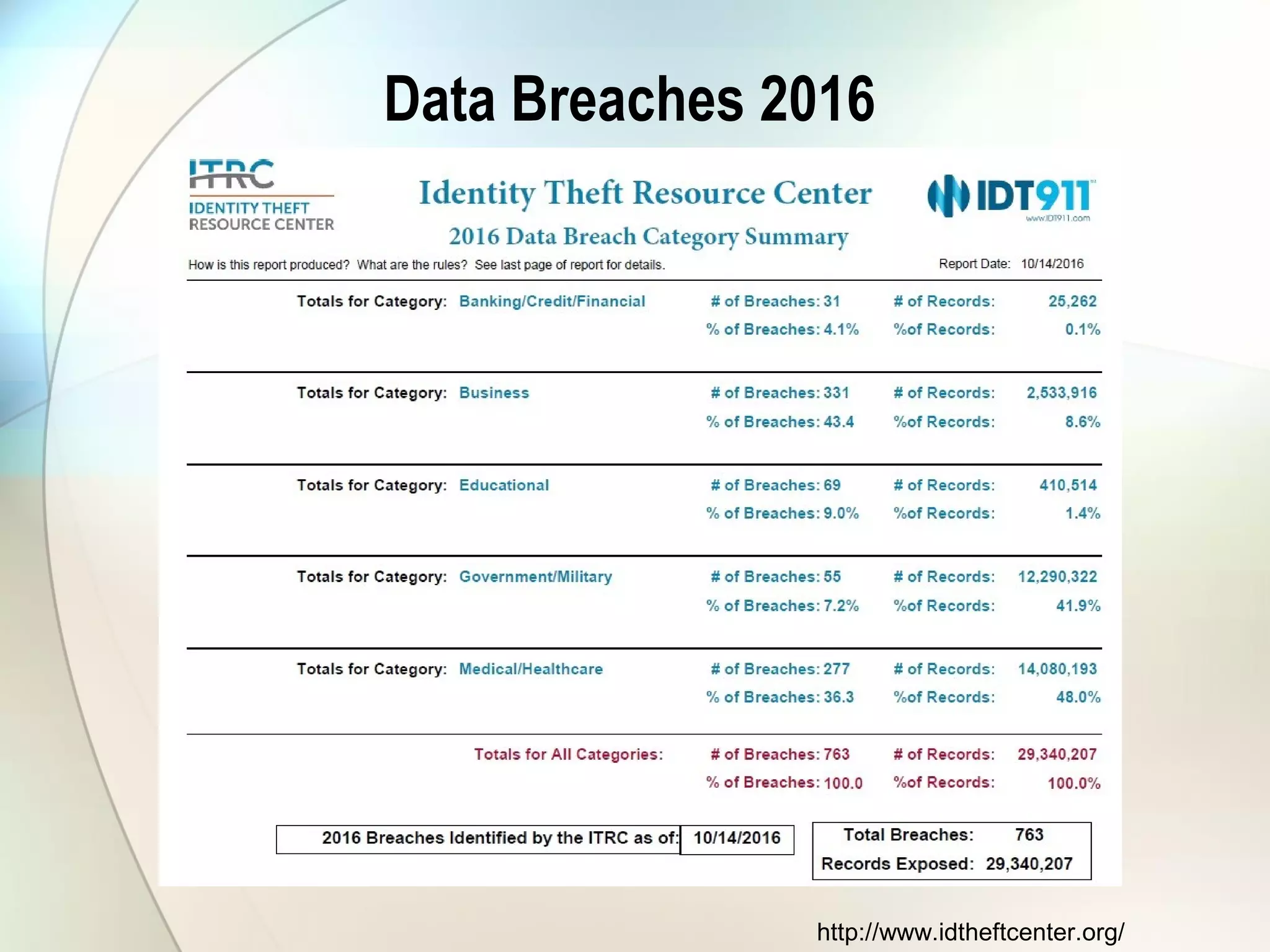
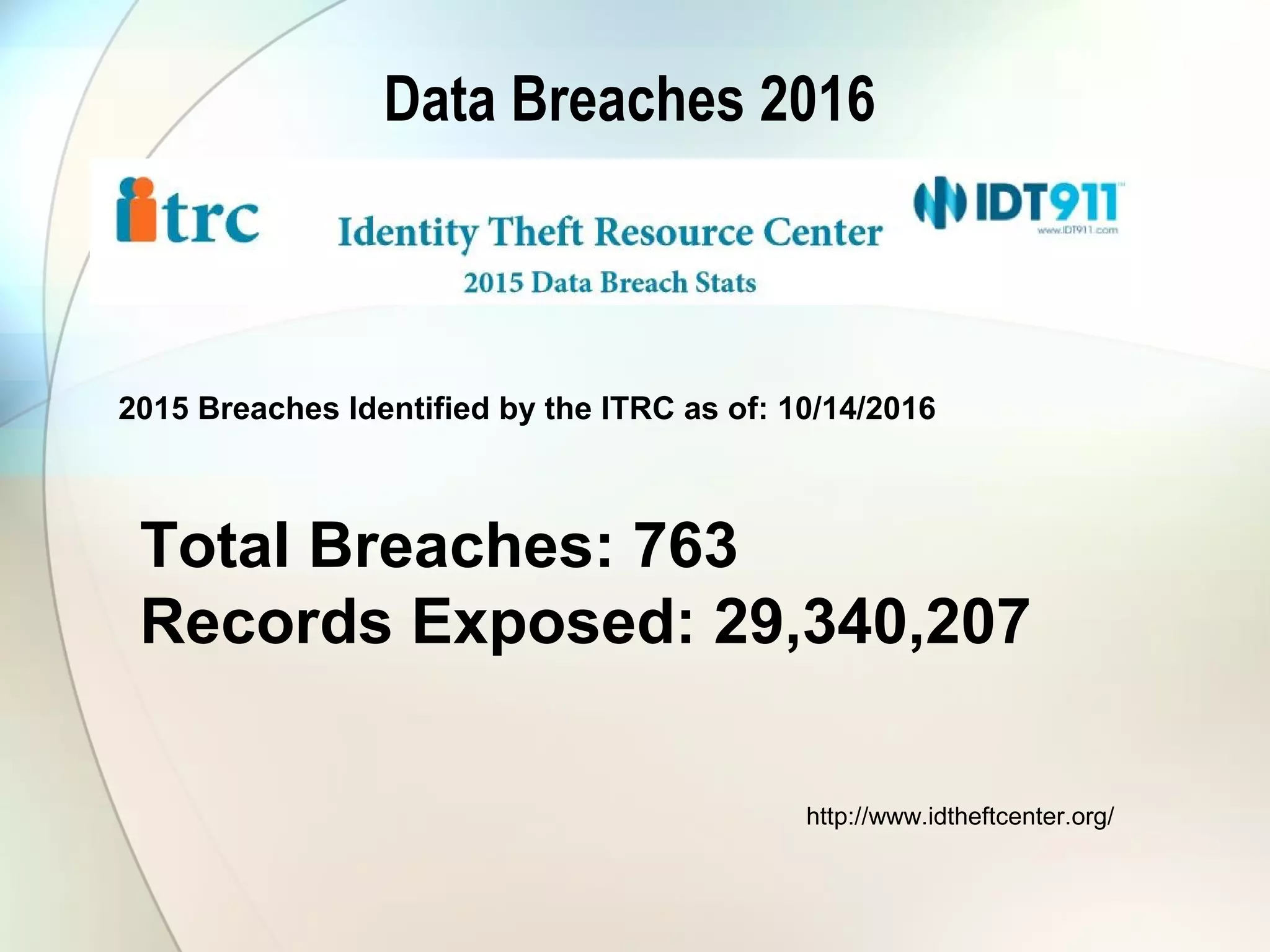
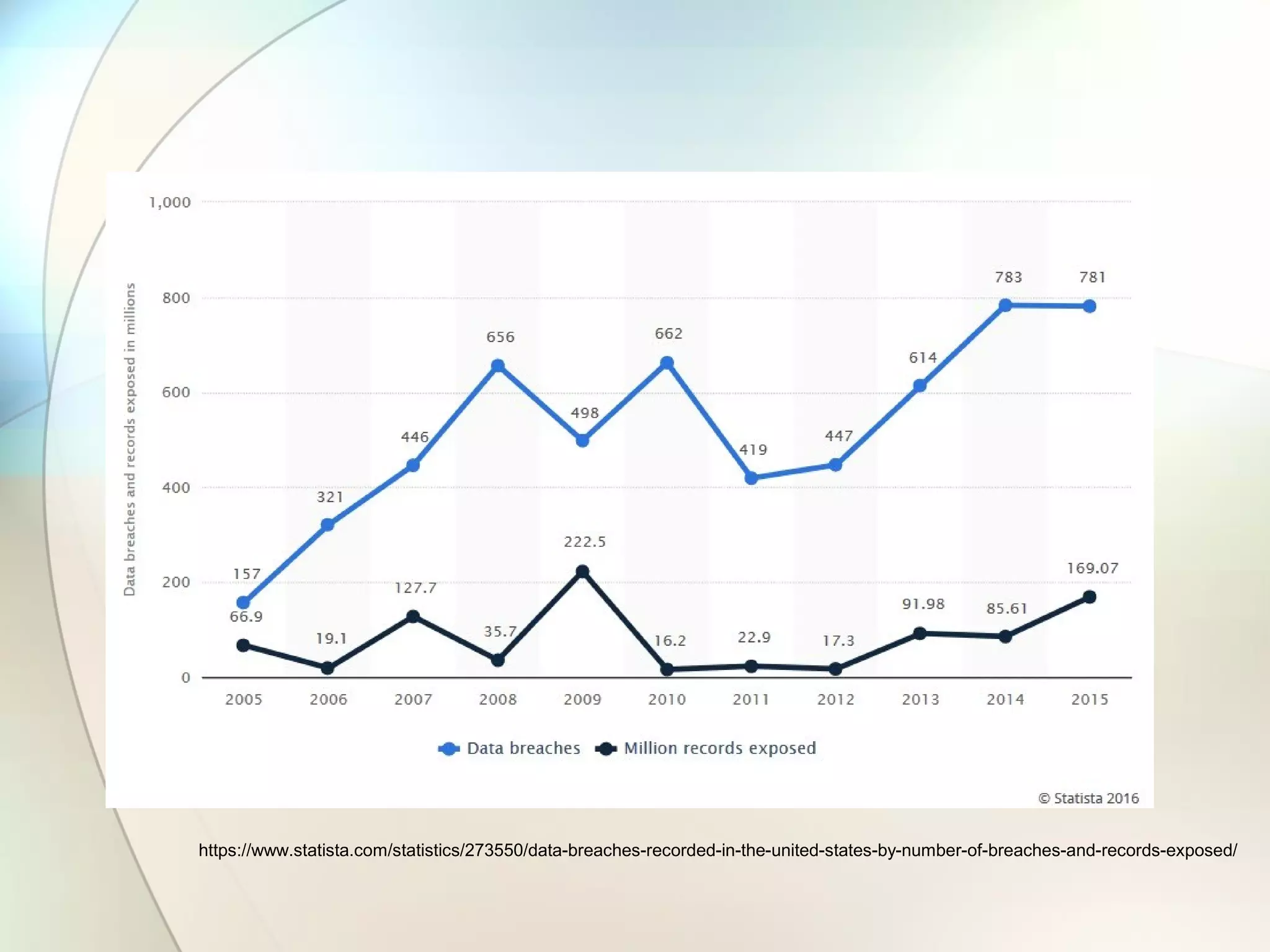
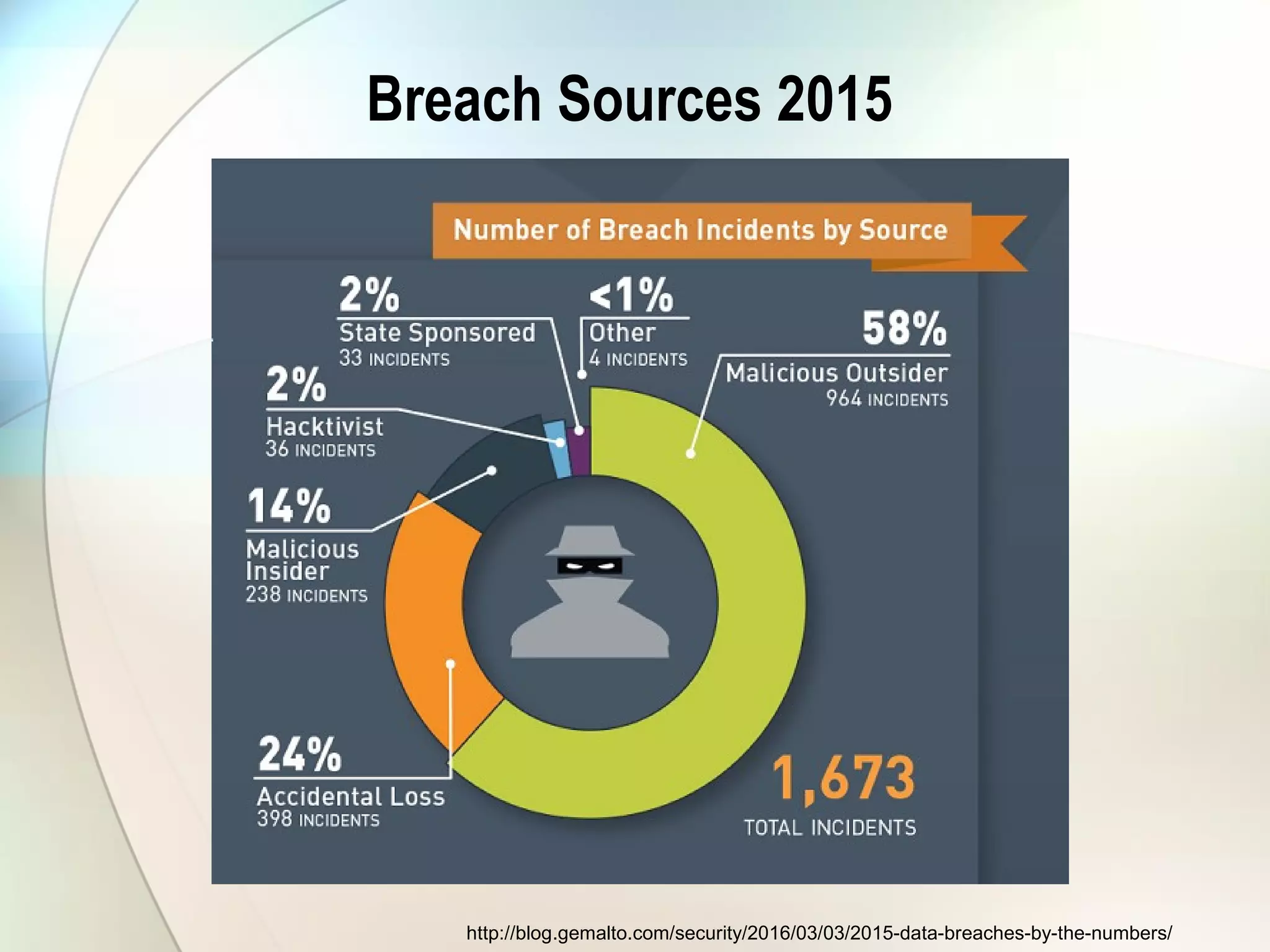
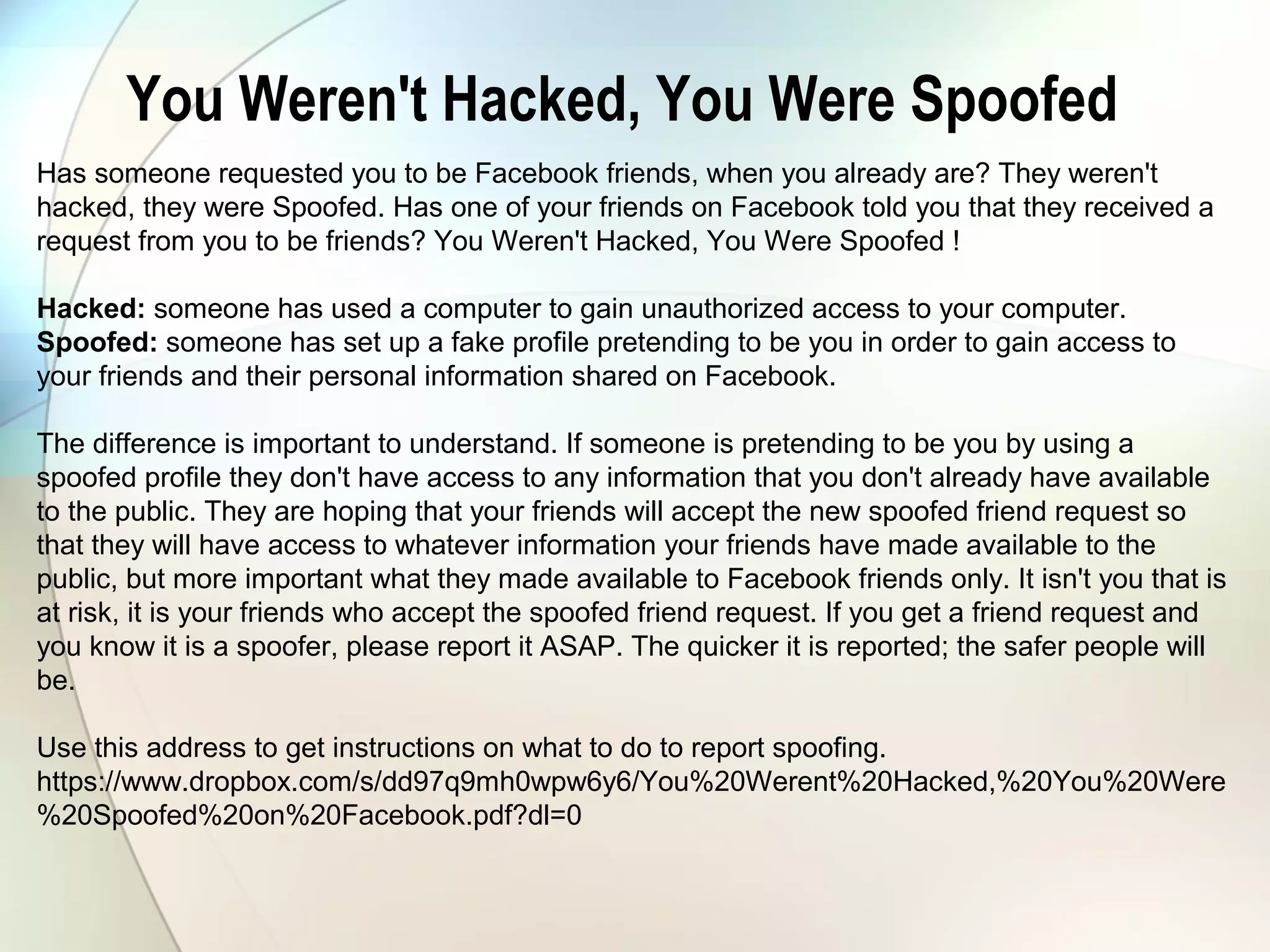
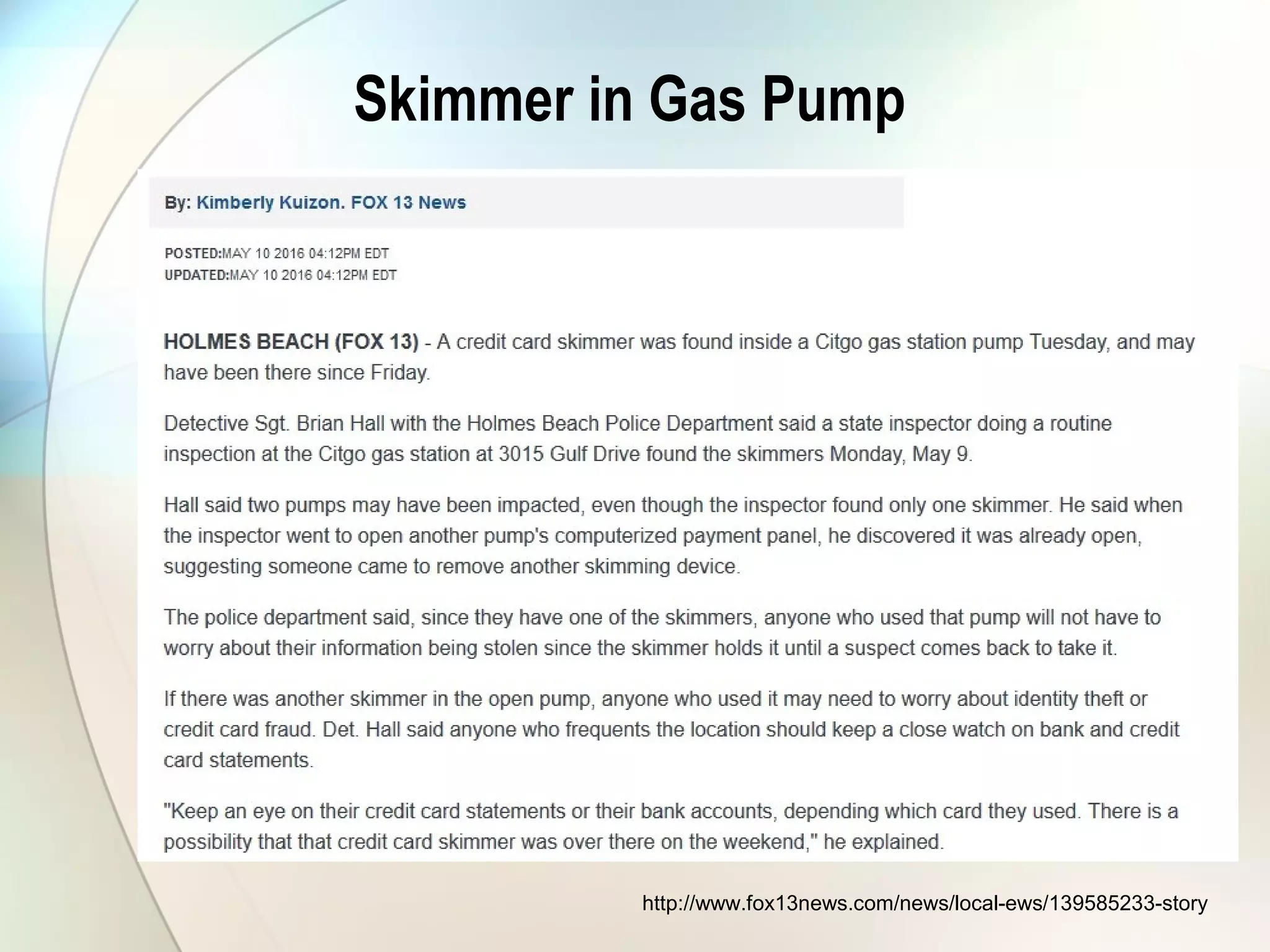
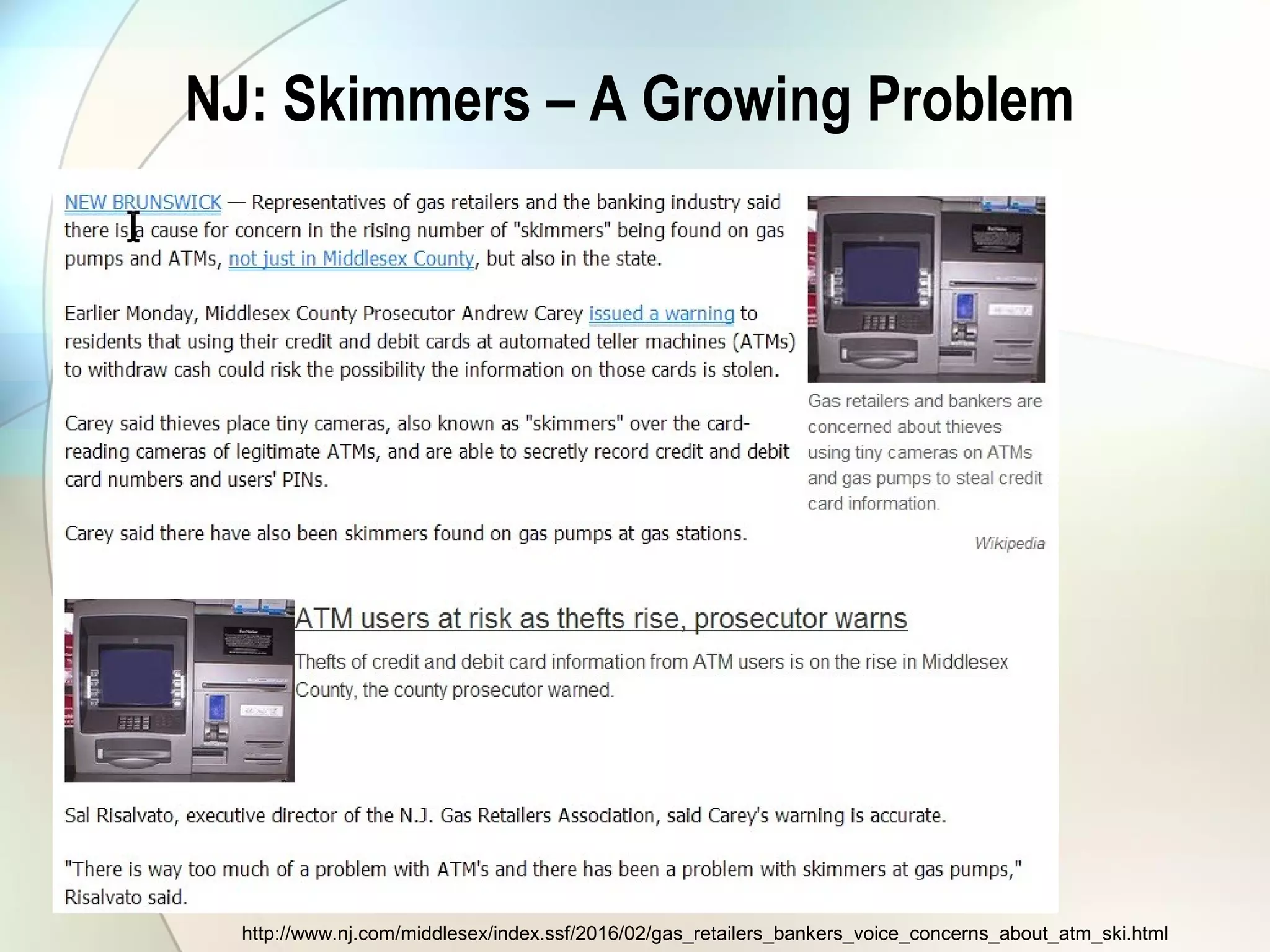
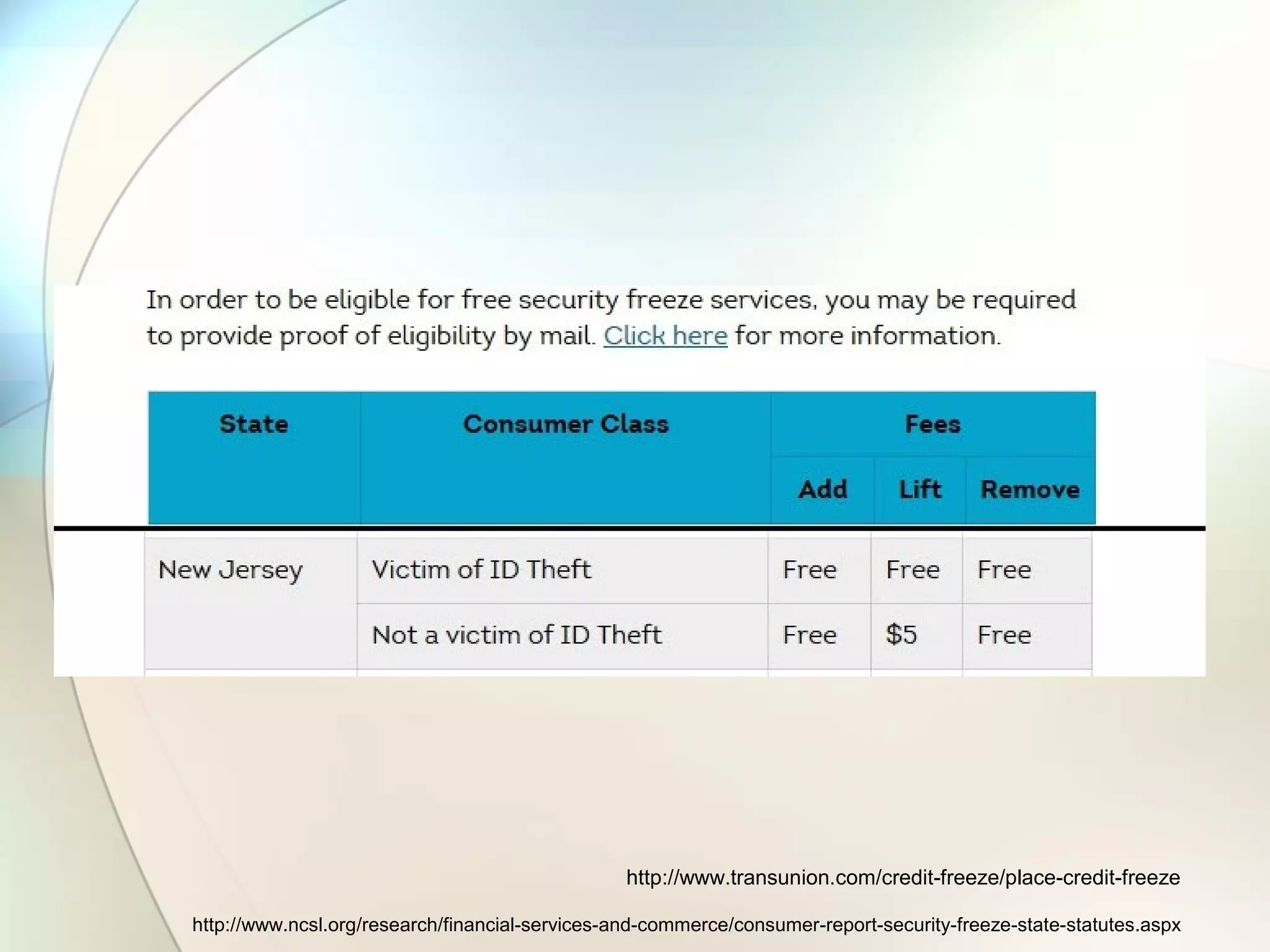
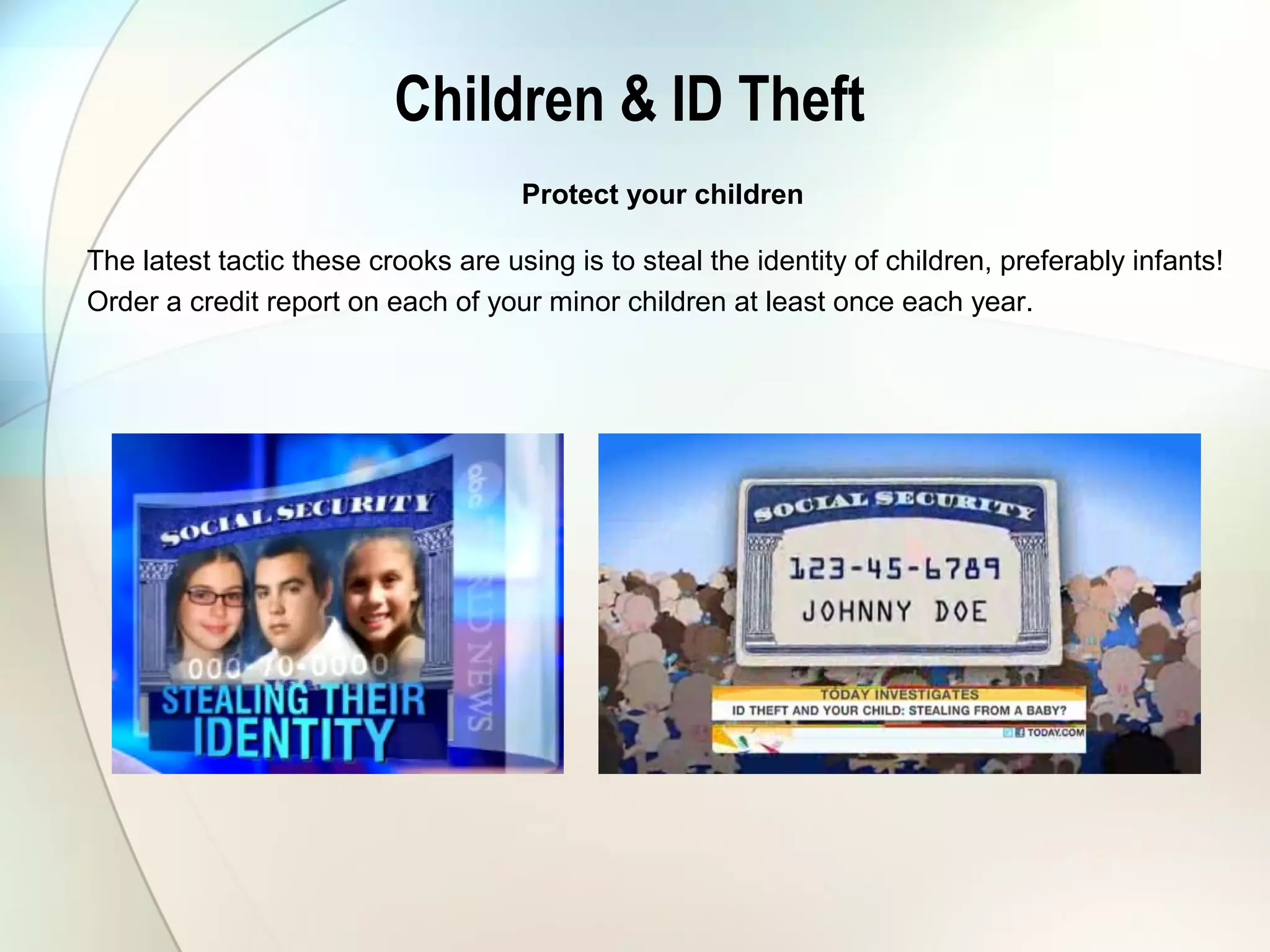
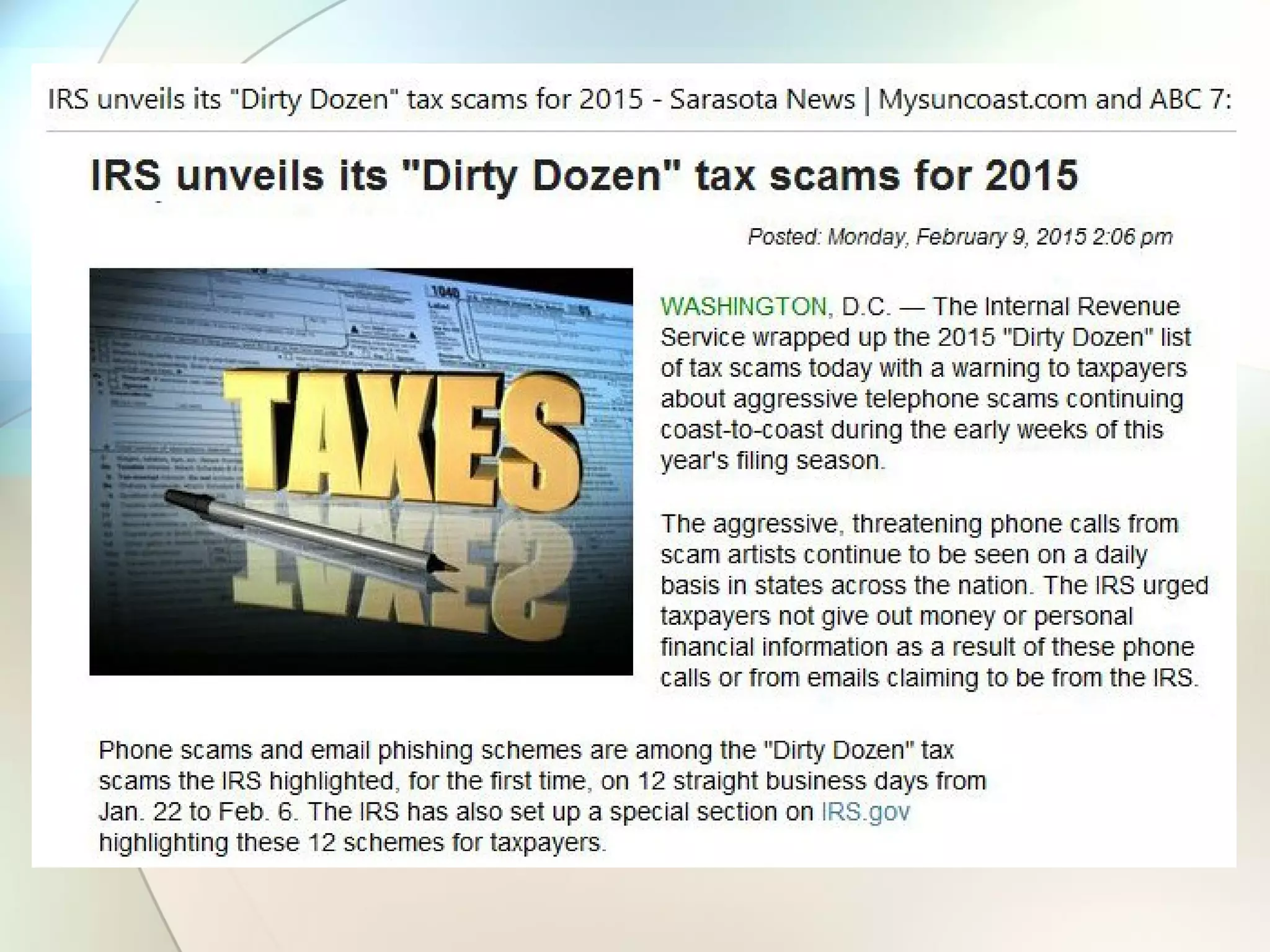
The document discusses identity theft and ways that thieves steal personal information. It begins with defining identity theft and the common types, including child identity theft, tax identity theft, medical identity theft, and senior identity theft. It then discusses how identity theft can occur through stealing wallets and mail, rummaging through trash, online methods like phishing and social media, and using stolen information to make purchases or apply for loans in the victim's name. The document provides tips on protecting yourself such as being wary of emails asking for personal information, not sharing sensitive data over email, and monitoring accounts regularly for unauthorized activity.