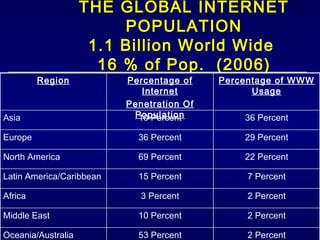
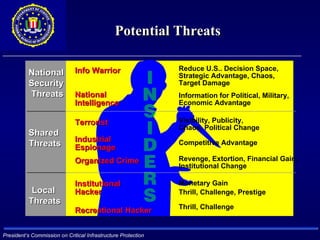
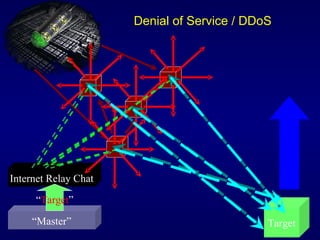
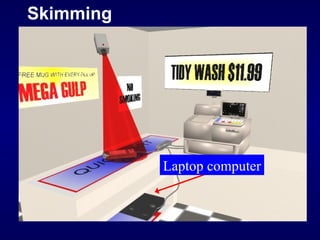
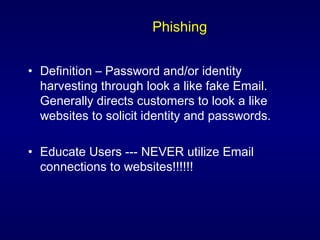
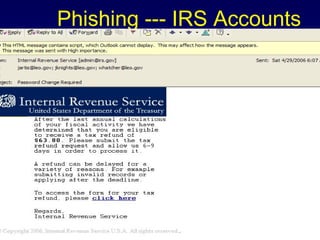
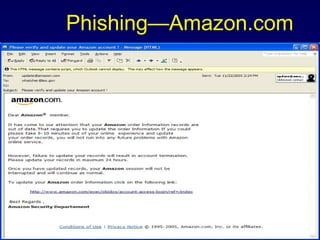
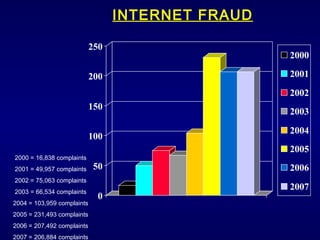
The document discusses cyber identity theft and computer crimes. It notes that the internet is increasingly being used by criminals internationally and domestically to commit traditional crimes like fraud. New techniques like botnets, which control thousands of infected computers, are being used for illegal activities like spamming and cyberattacks. The document provides tips on minimizing the risk of identity theft and advises what to do if one becomes a victim.
![Cyber Identity Theft Presentation [email_address]](https://image.slidesharecdn.com/Linkedinpub-123126210483-phpapp01/75/ID-Theft-1-2048.jpg)




















![Joint FBI/US-DHS Cyber Security Email request: [email_address]](https://image.slidesharecdn.com/Linkedinpub-123126210483-phpapp01/85/ID-Theft-35-320.jpg)
