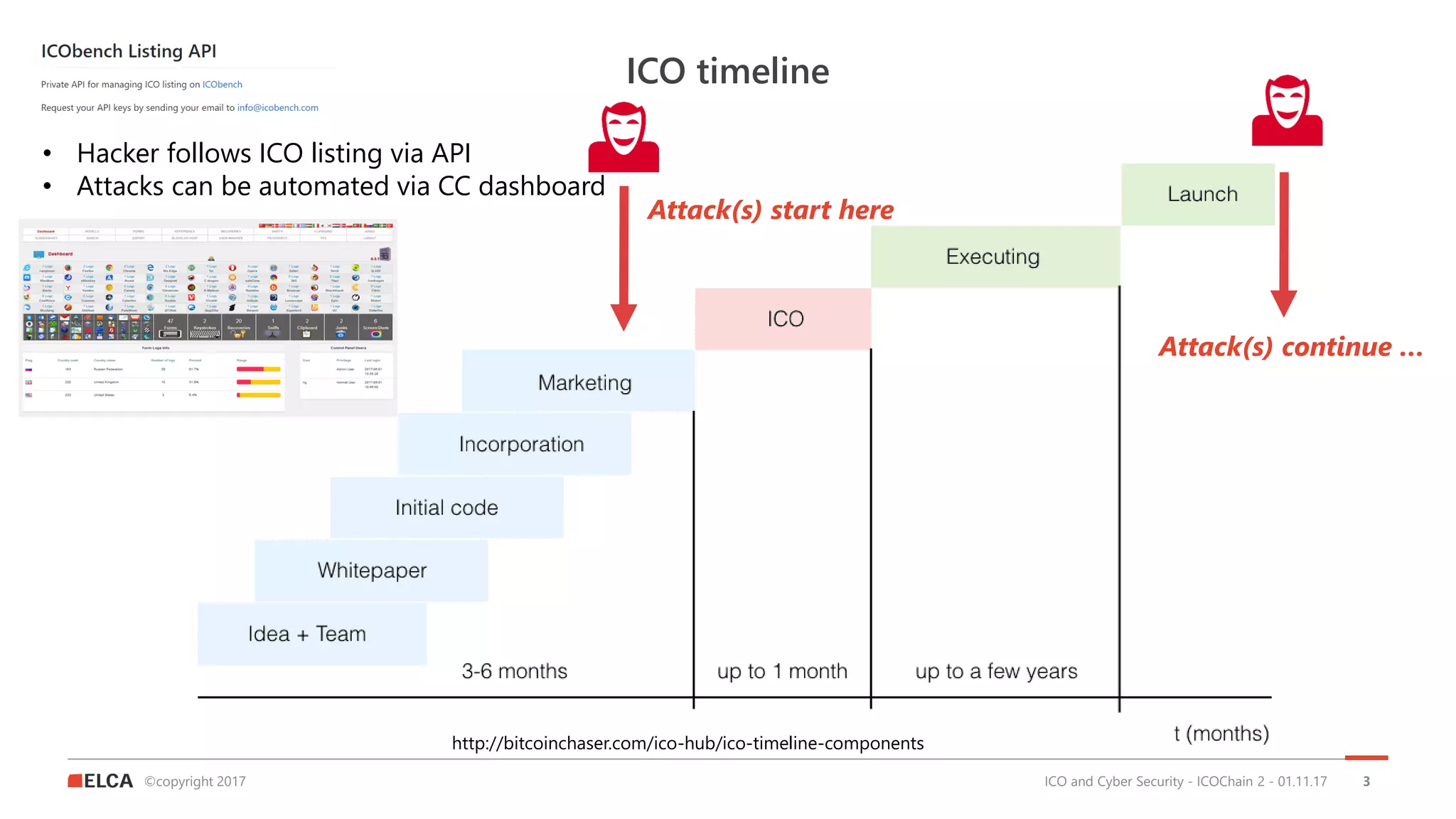
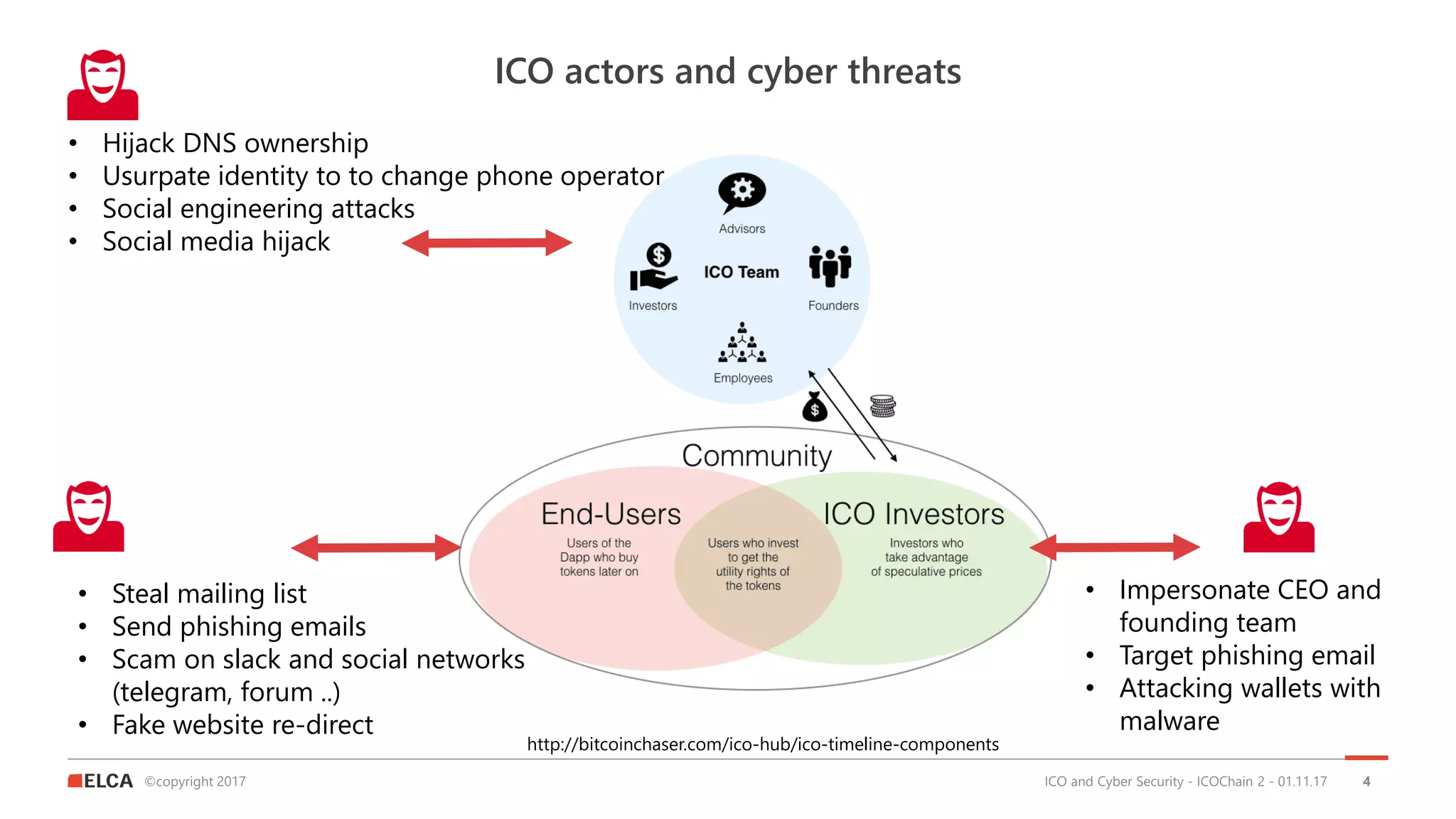
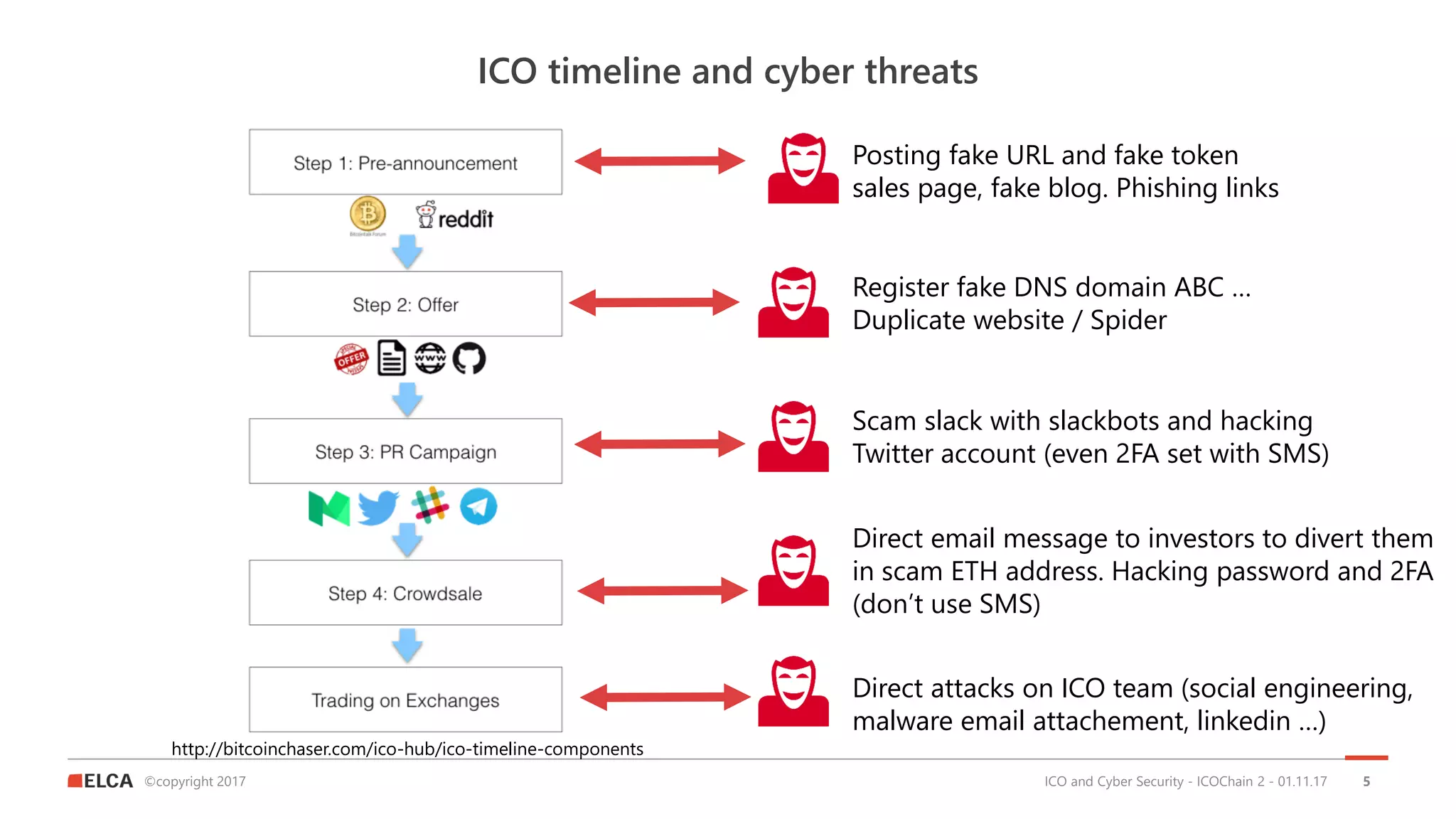
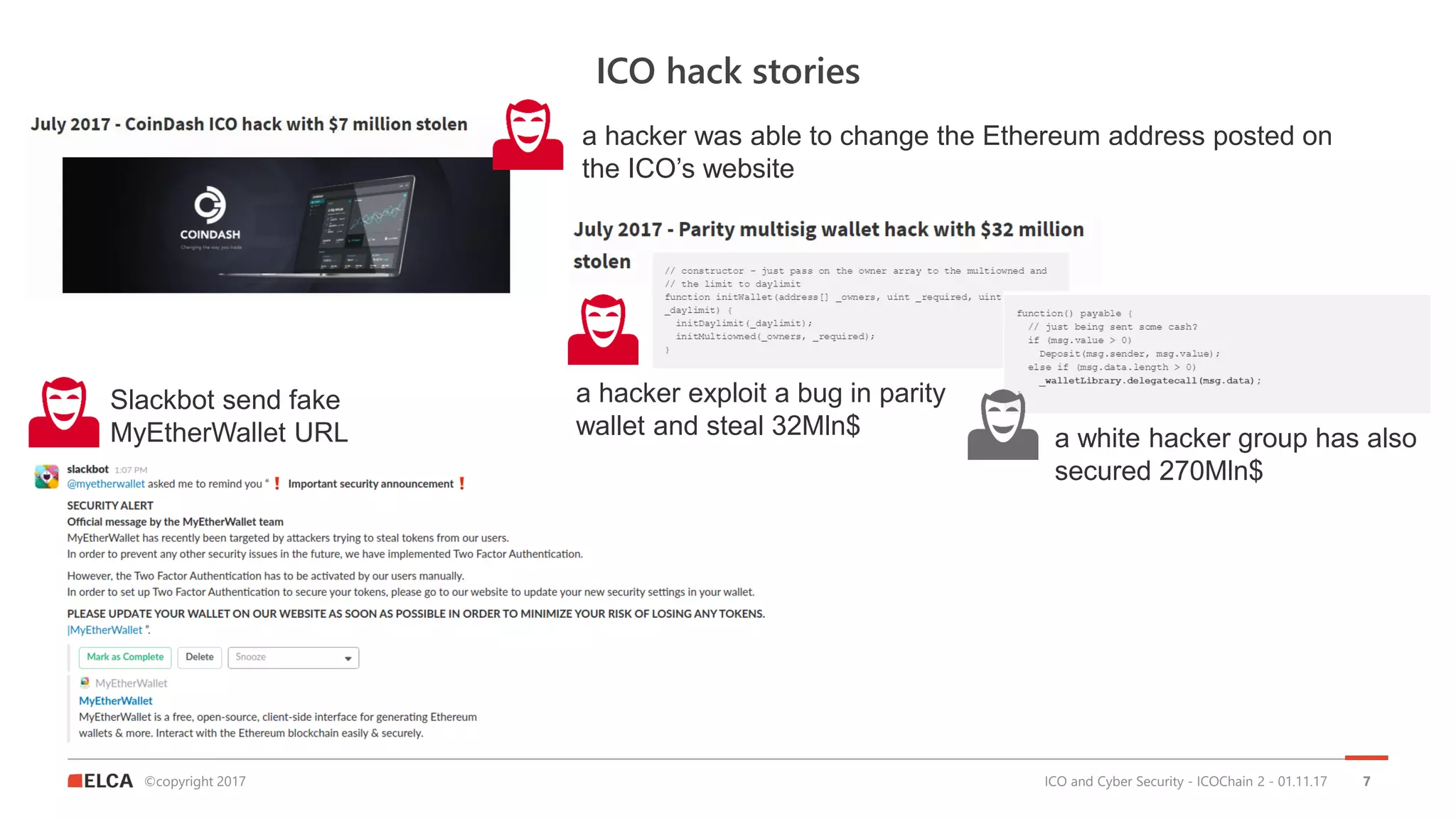
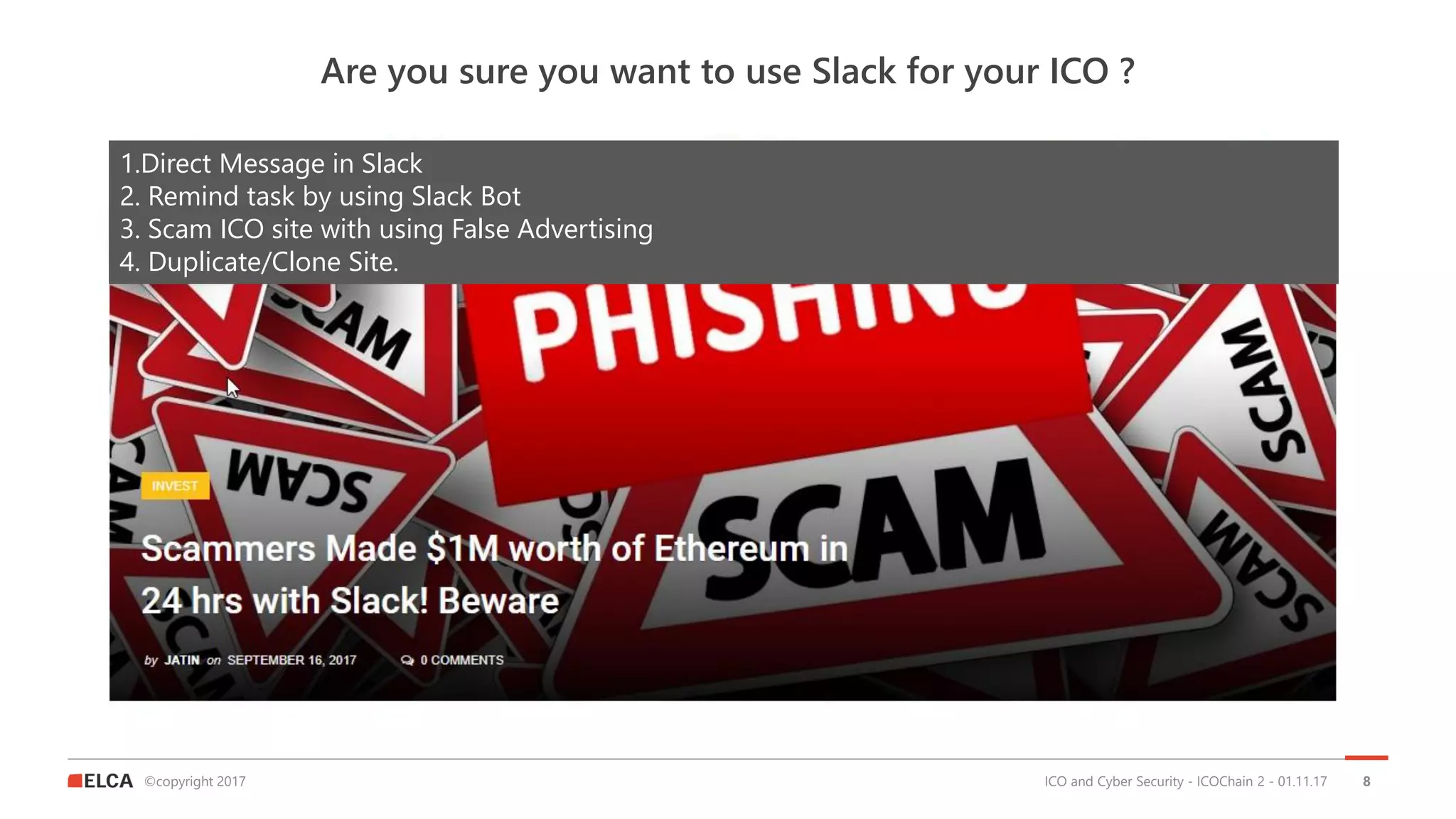
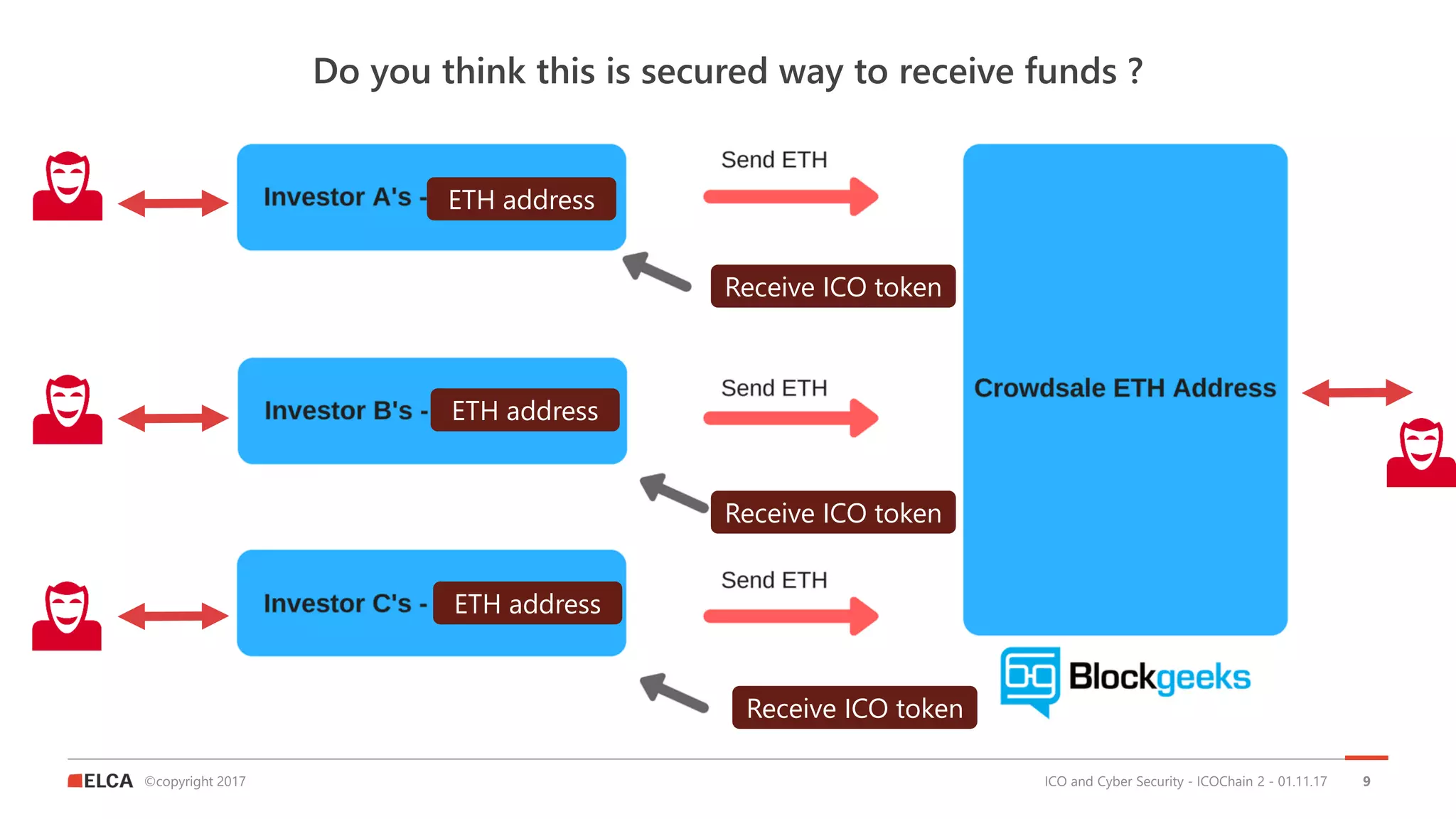
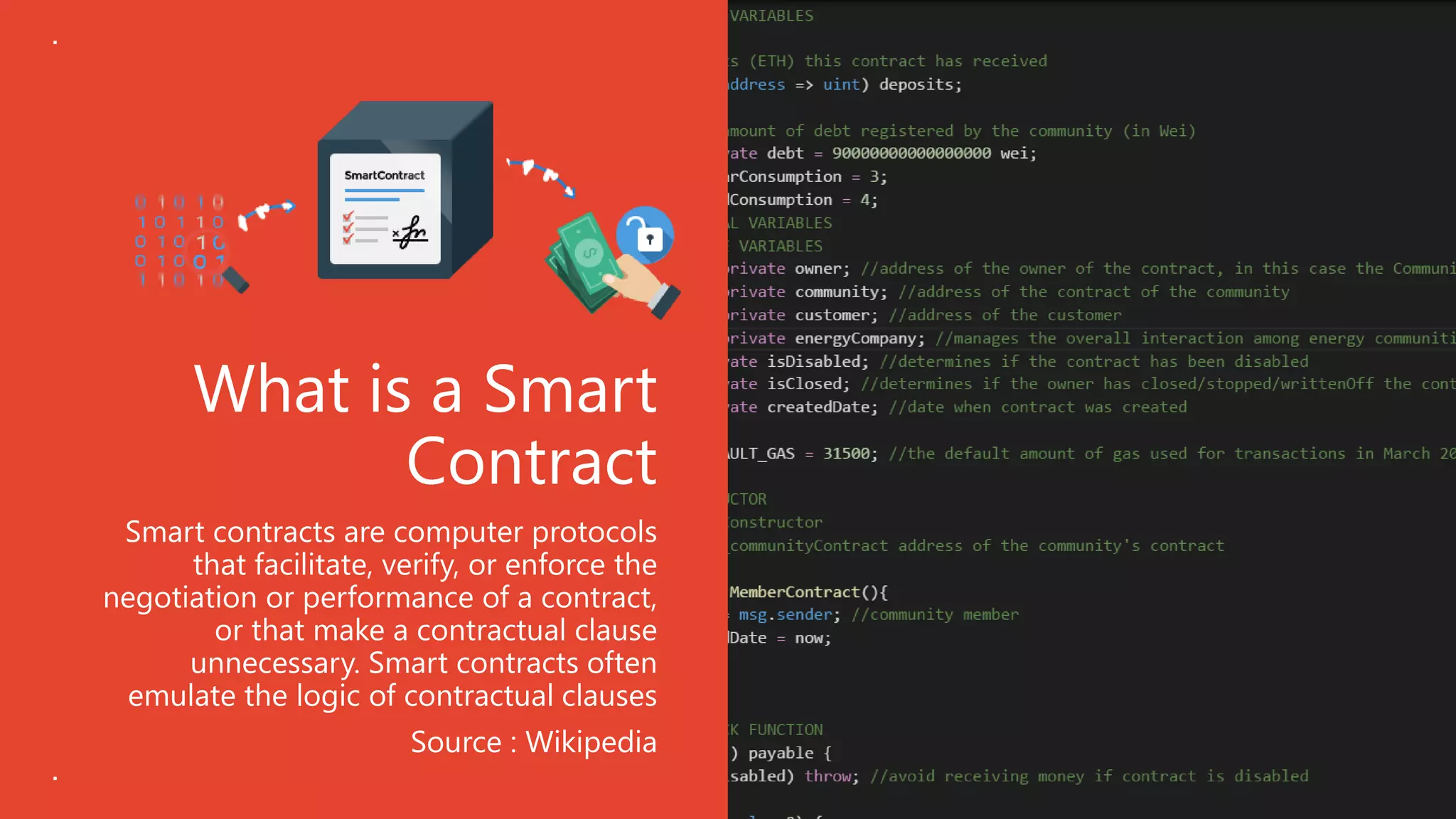
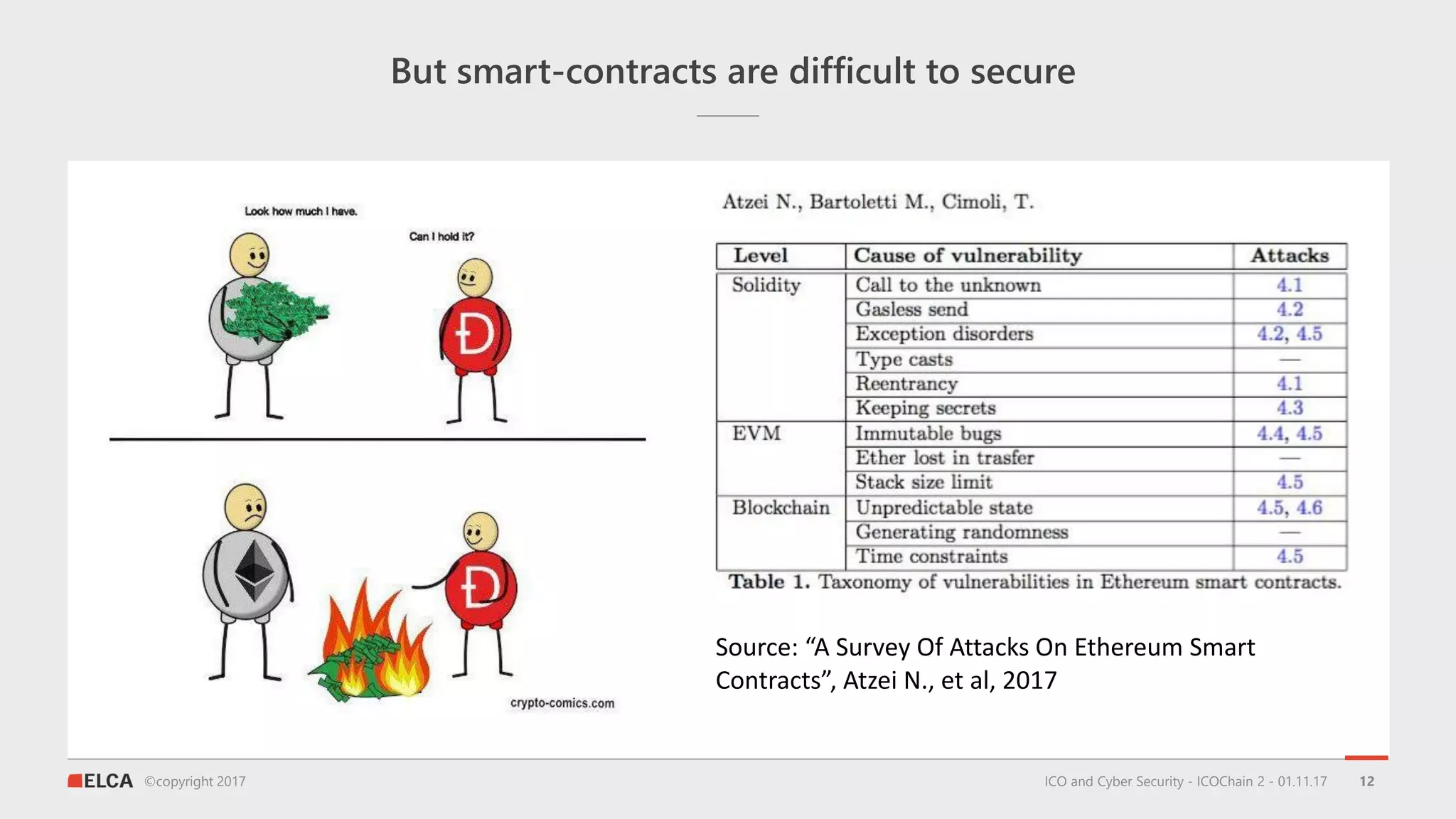
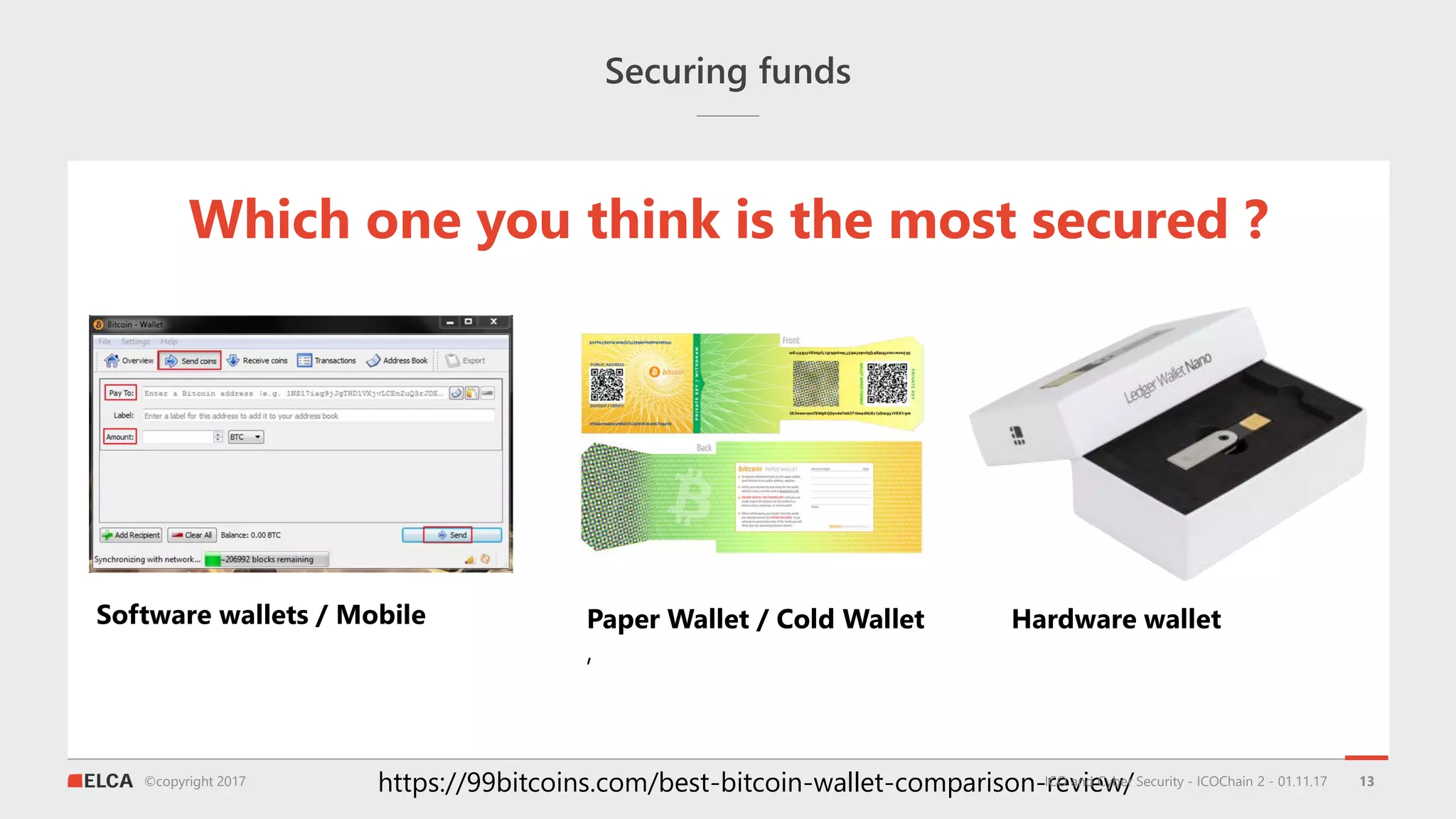
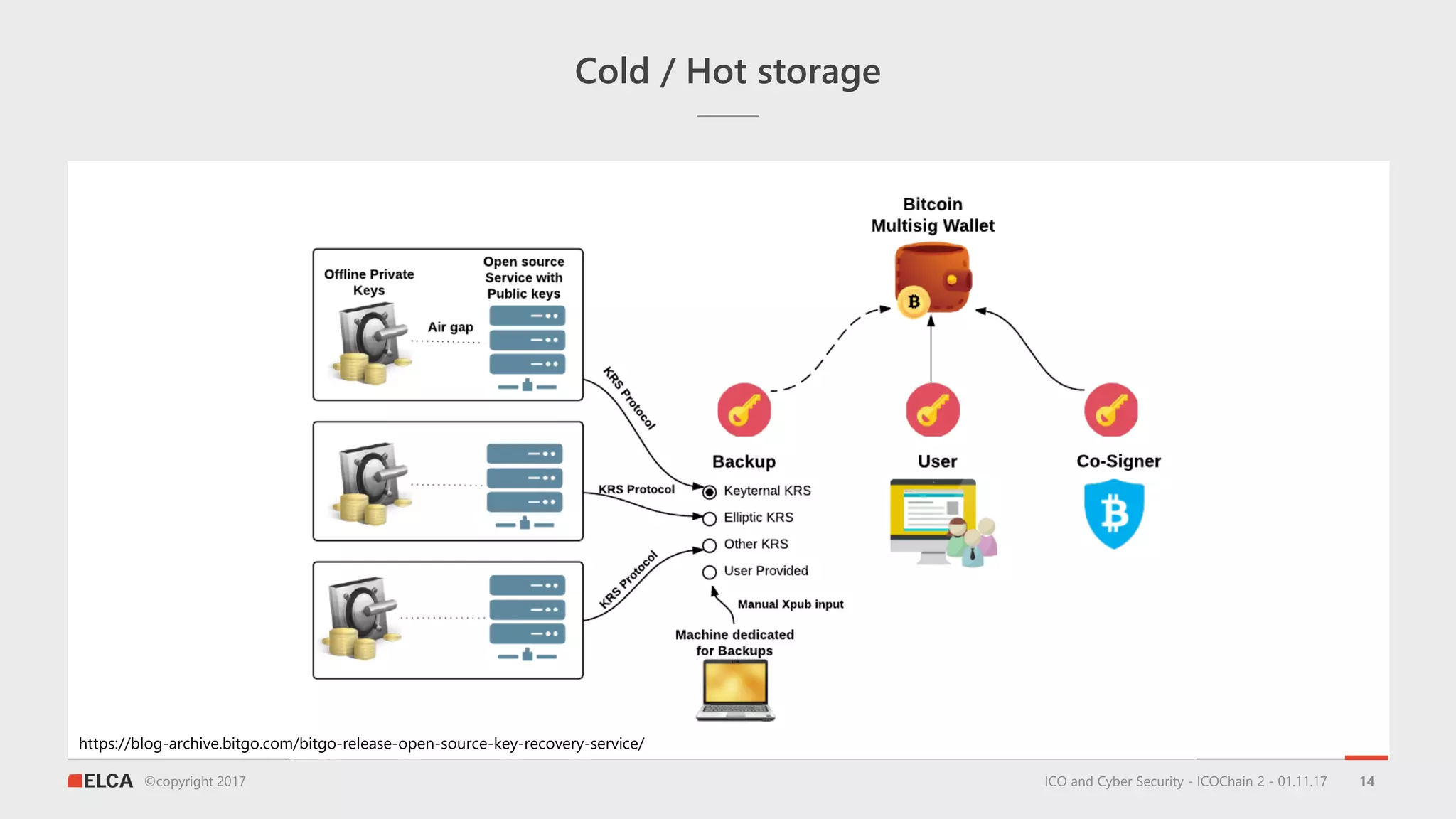
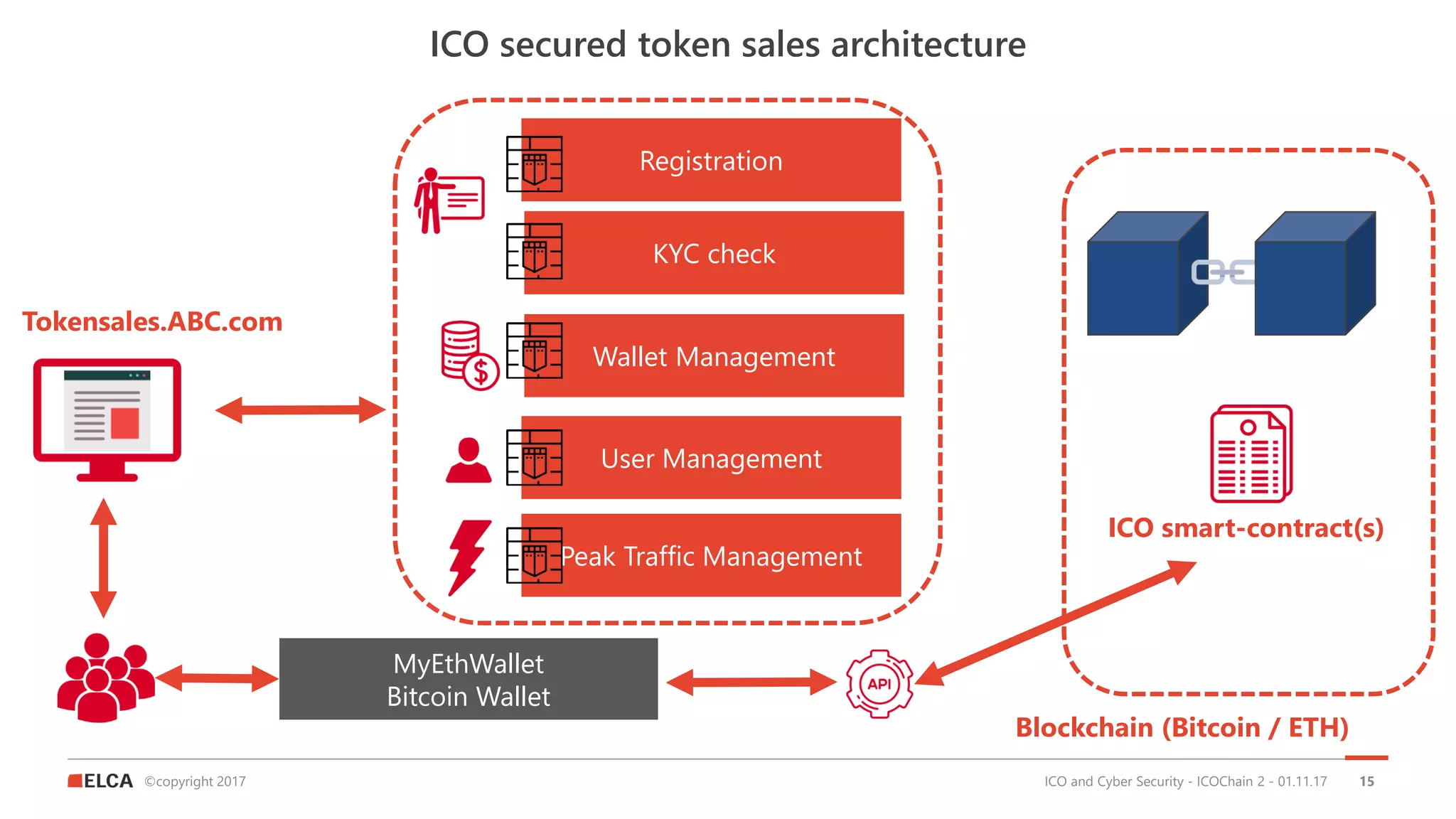
The document discusses the timeline and cyber threats associated with Initial Coin Offerings (ICOs), highlighting various attack methods such as phishing, social engineering, and malware targeting. It emphasizes the importance of securing ICOs through best practices, including the use of smart contracts, cold storage for funds, and auditing procedures. Additionally, a top ten checklist for ICO security is provided, which includes recommendations for password management, two-factor authentication, and KYC compliance.