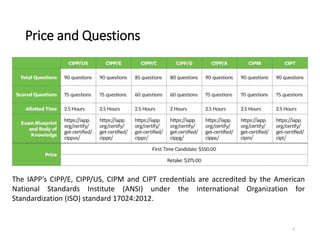
The document provides information about certification programs offered by the International Association of Privacy Professionals (IAPP). It describes the different certification options (CIPP, CIPM, CIPT), their target audiences and topics covered. Testing is available online or at conferences, and certification must be renewed every two years by completing continuing education credits. Sample exam questions and training courses are available for purchase through the IAPP store. Free resources also include a certification handbook and privacy term glossary.