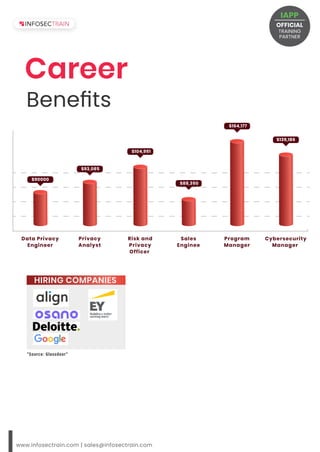
The document outlines a Certified Information Privacy Manager (CIPM) training and certification program offered by InfosecTrain, an IAPP partner, which includes 32 hours of instructor-led training, exam vouchers, and post-training support. Targeted at professionals such as data protection officers and security managers, the course covers privacy program frameworks, governance models, and various operational lifecycle stages. It highlights career benefits related to data privacy roles, including salary expectations for positions like data privacy engineer and cybersecurity manager.