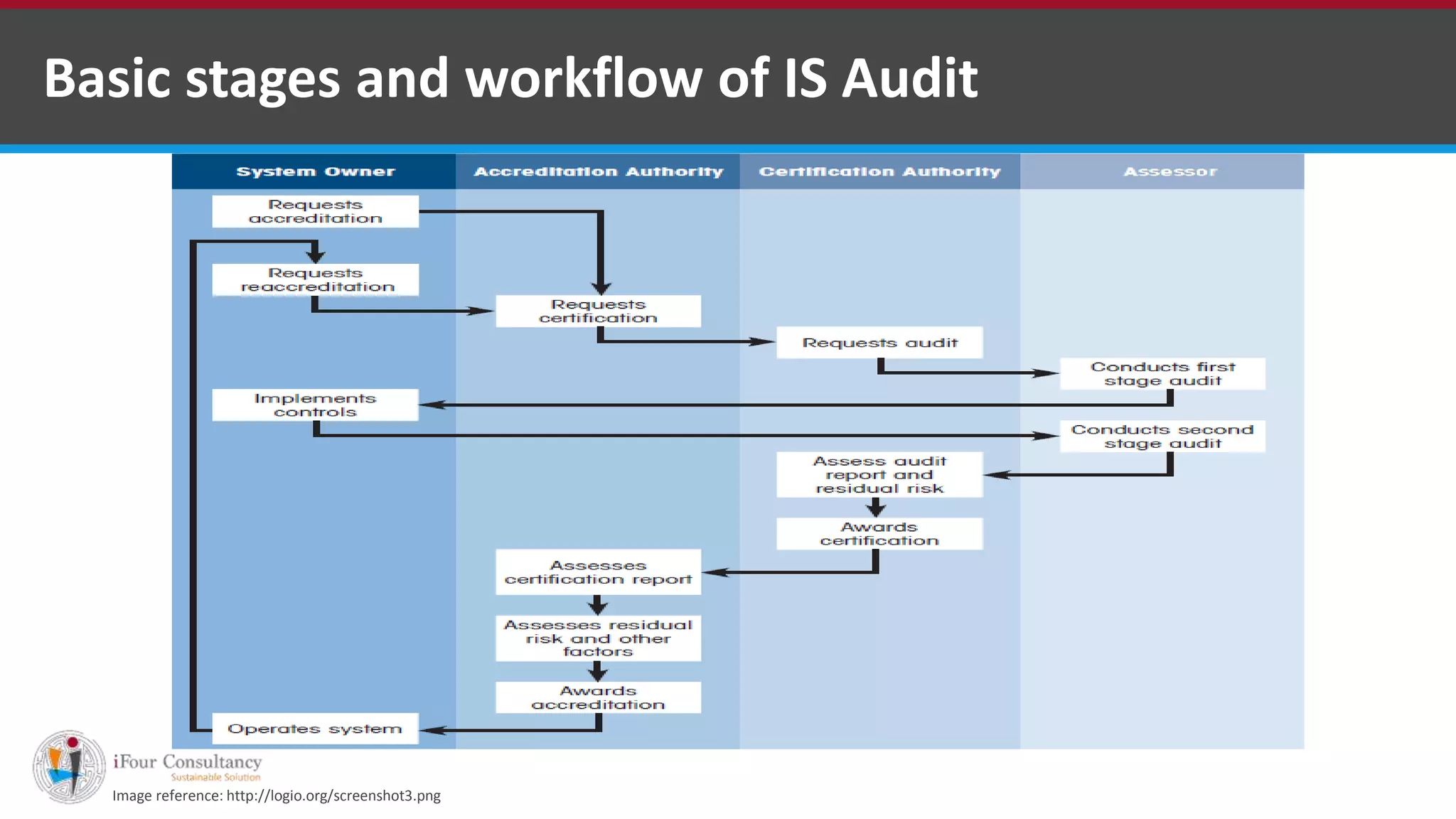
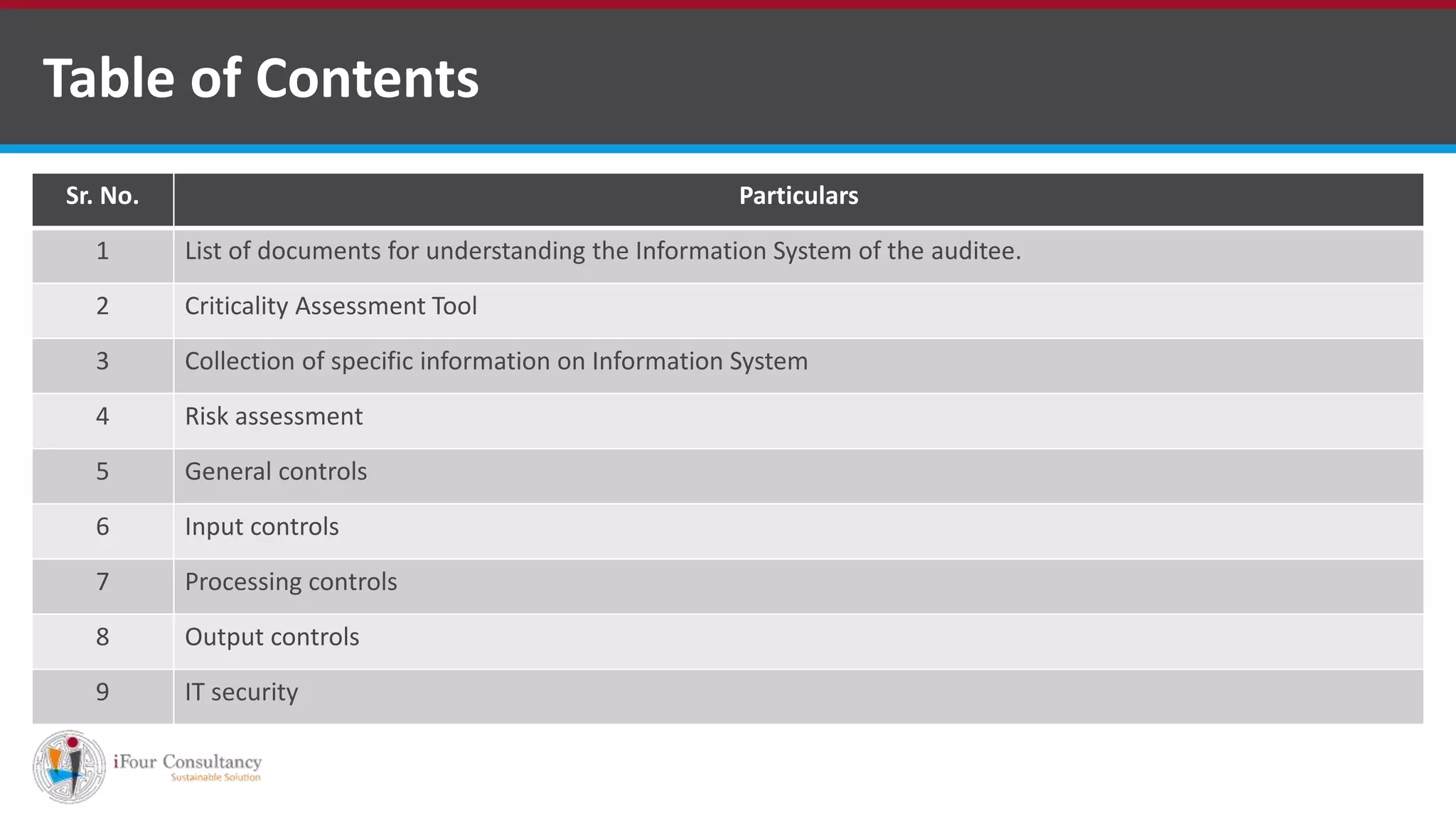
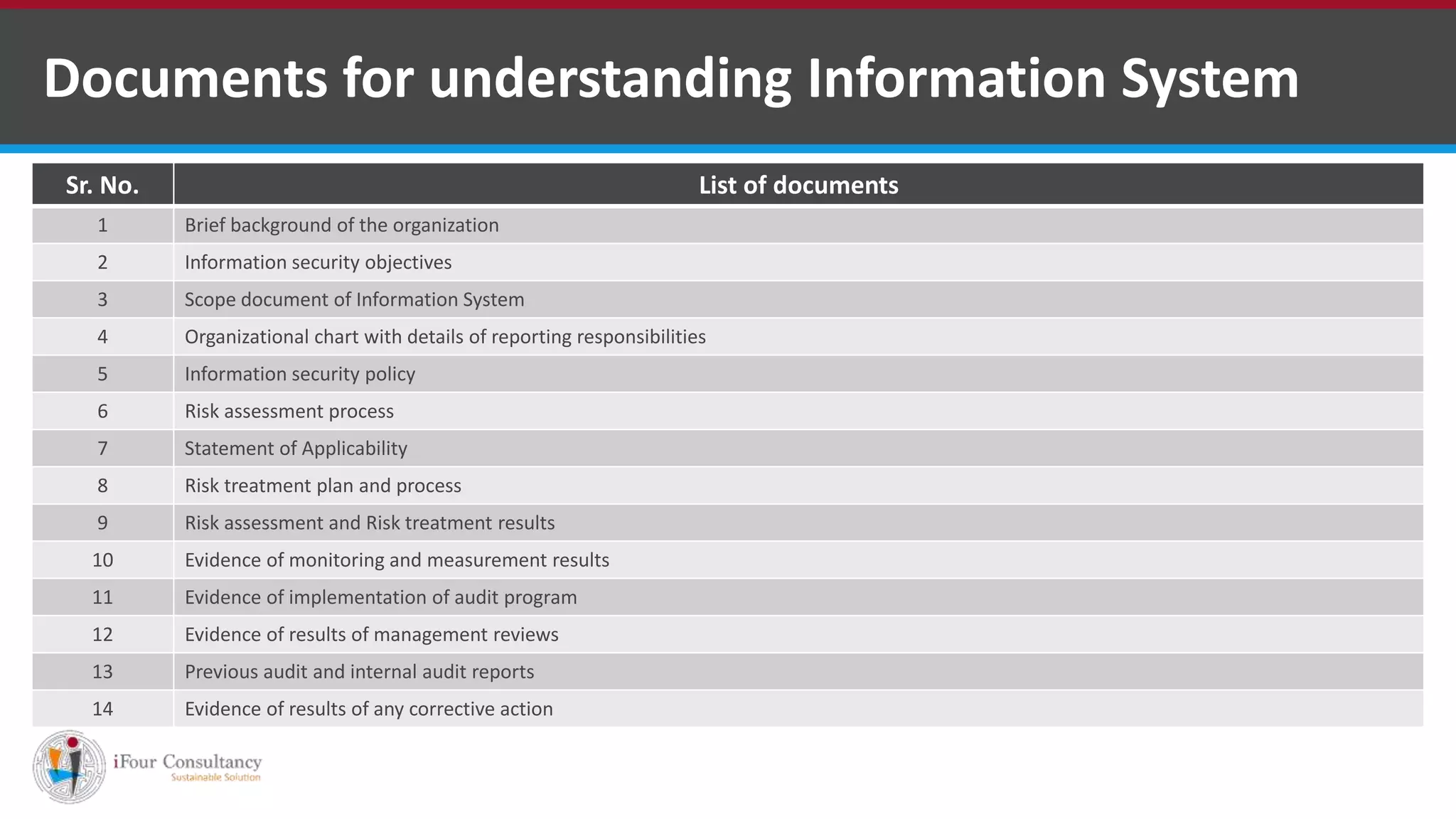
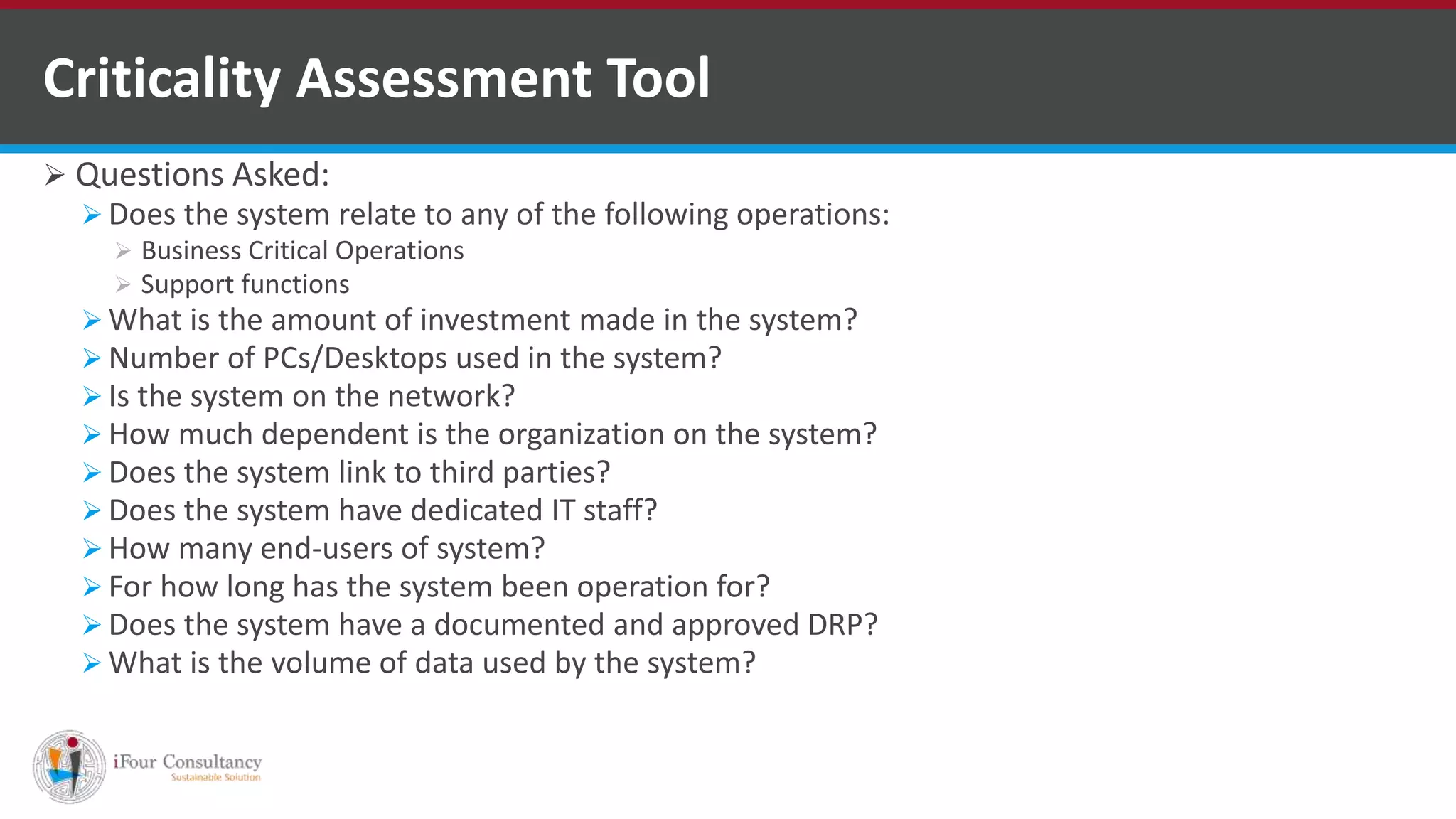
The document outlines the stages and workflow of an information security audit, including understanding the auditee's information system, assessing risk, and reviewing general, input, processing, and output controls. It provides details on collecting information about the system, assessing risks related to management, HR policies, security, and physical/logical access. Finally, it lists various sections to consider for reviewing IT security, such as security policies, asset classification, access control, and business continuity management.