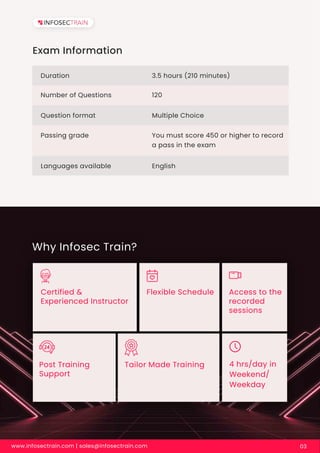
The Certified Data Privacy Solutions Engineer (CDPSE) certification validates the skills needed to assess and implement privacy solutions, addressing the technical skills gap within organizations. Infosec Train offers a training course led by experienced professionals, requiring candidates to have at least three years of relevant experience. The certification exam lasts 3.5 hours and consists of 120 multiple-choice questions, with a passing score of 450 or higher.