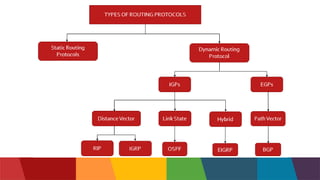
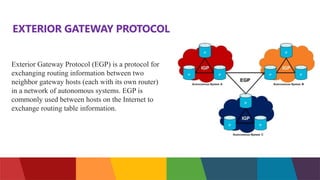
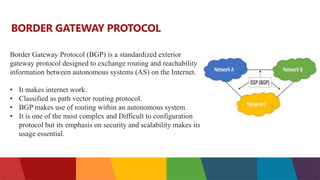
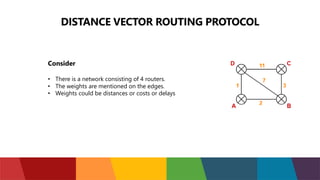
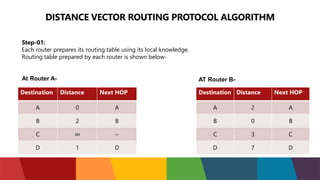
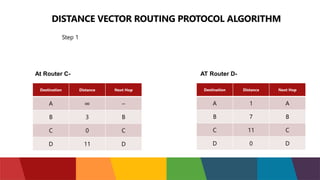
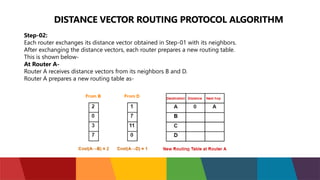
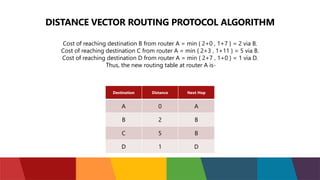
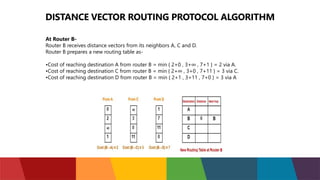
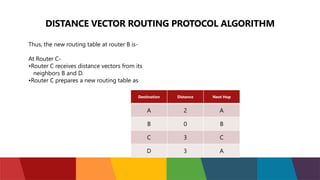
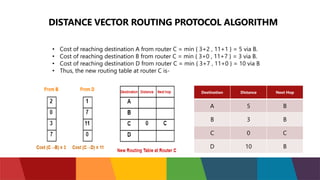
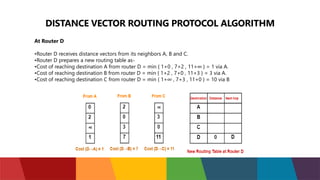
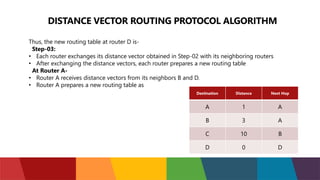
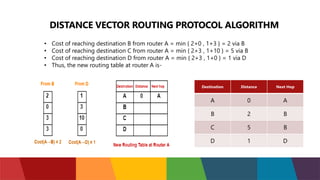
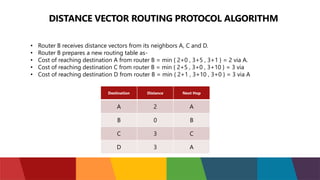
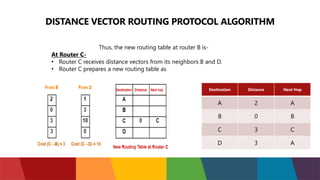
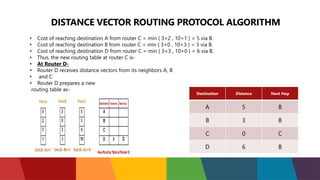
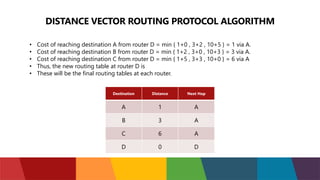
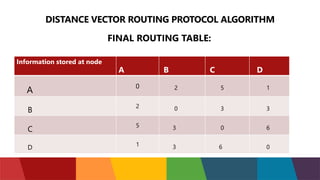
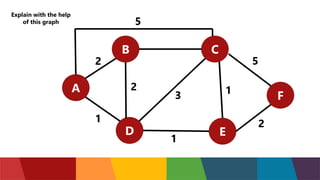
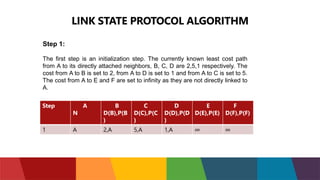
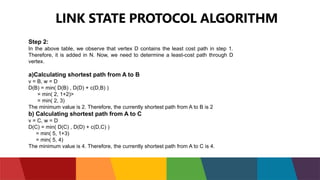
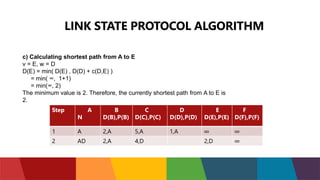
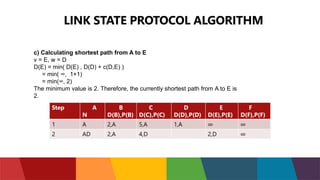
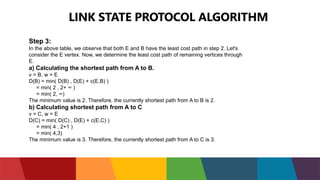
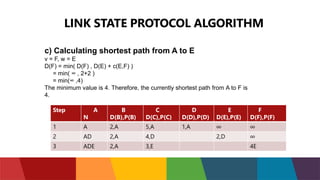
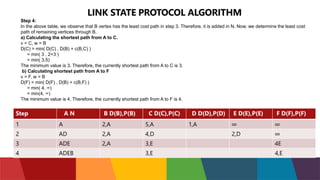
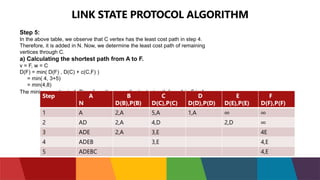
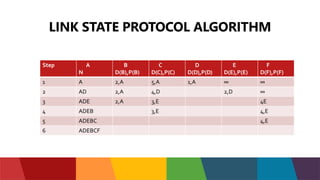
The document discusses different routing protocols used in computer networks. It begins with an introduction to routing protocols and their purpose of communicating between source and destination networks by updating routing tables. It then categorizes routing protocols as static or dynamic and discusses examples in each category. For dynamic routing protocols, it further divides them into interior gateway protocols used within an autonomous system and exterior gateway protocols used between autonomous systems. Specific dynamic interior routing protocols discussed in detail include distance vector protocols like RIP and link state protocols like OSPF.