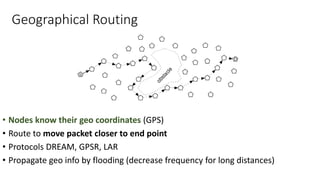
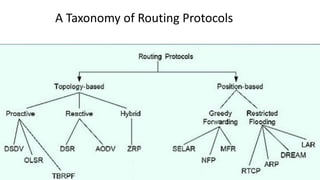
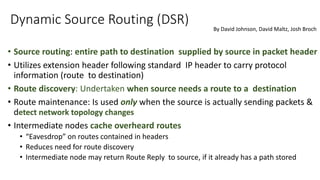
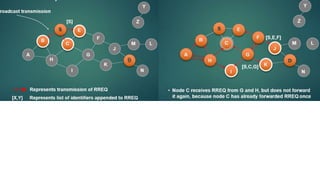
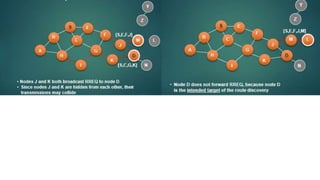
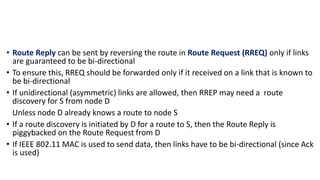
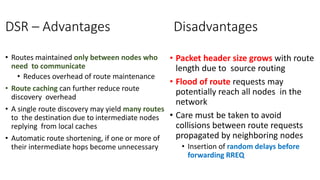
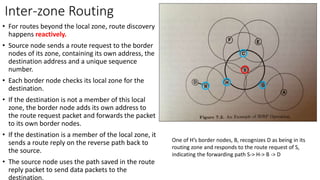
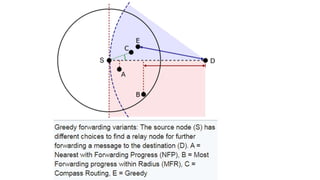
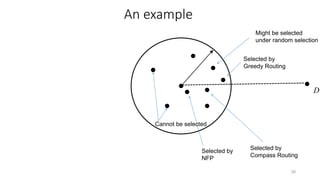
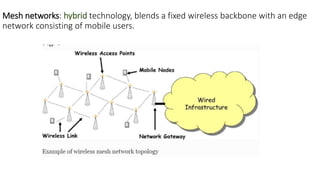
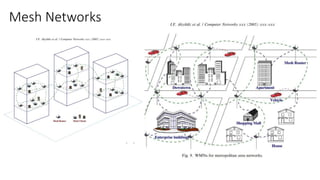
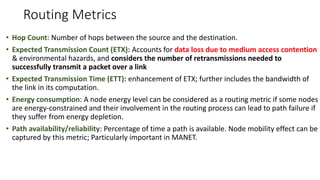
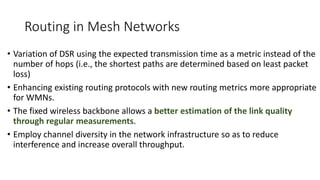
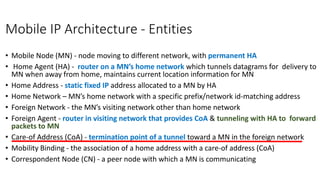
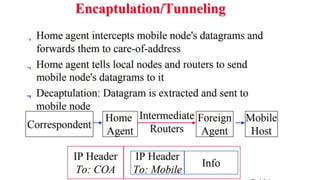
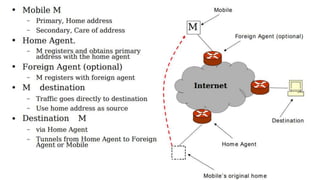
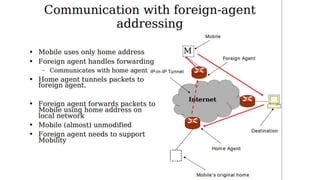
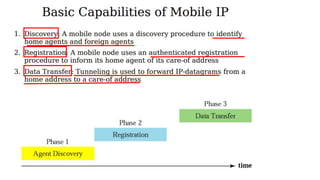
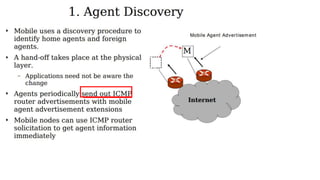
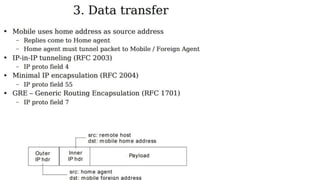
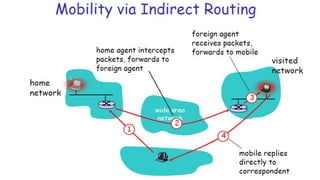
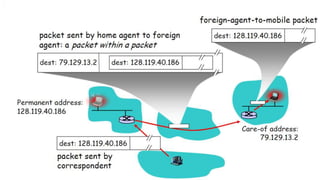
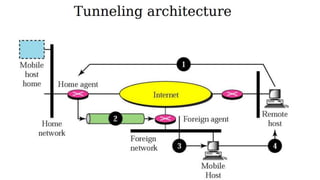
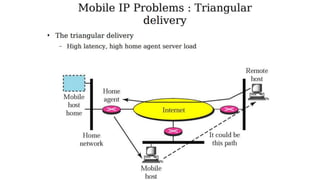
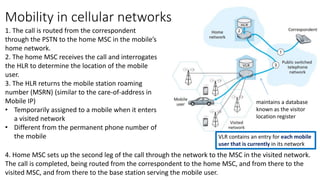
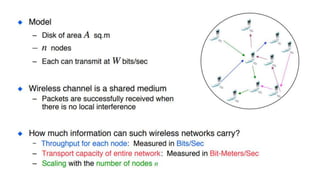
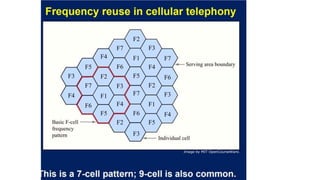
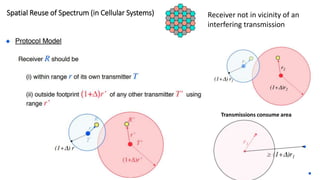
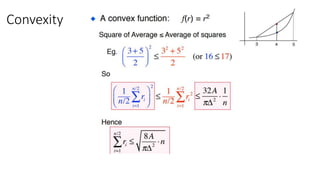
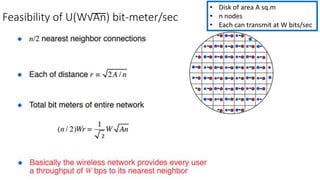
The lecture discusses routing in mobile wireless networks. It covers issues like limited transmission range, mobility-induced route changes, and security hazards in wireless transmissions. Various routing protocols are introduced, including proactive protocols that maintain routing information independently, on-demand protocols that discover routes only when needed, and hybrid approaches that combine the two. Specific protocols discussed include DSR, AODV, ZRP, LAR, and protocols for mesh and cellular networks. The tradeoffs between different routing approaches are also summarized.





![Routing Issues
• Which is the best path?
• Shortest path (fewest hops)
• Lowest latency
• Shortest weighted path (utilize available bandwidth, battery)?
• Who decides? Source, intermediate, or destination nodes?
Source (“path”) routing [Like airline travel]
• Source specifies entire route
• Intermediate nodes just forward to specified next hop
Destination (“hop-by-hop”) routing [Like postal service]
• Source specifies only destination in message header
• Intermediate nodes look at destination in header, consult internal tables to
determine appropriate next hop](https://image.slidesharecdn.com/mobileadhocroutingprotocols-230223063627-d0d95c31/85/MobileAdHocRoutingProtocols-pptx-6-320.jpg)