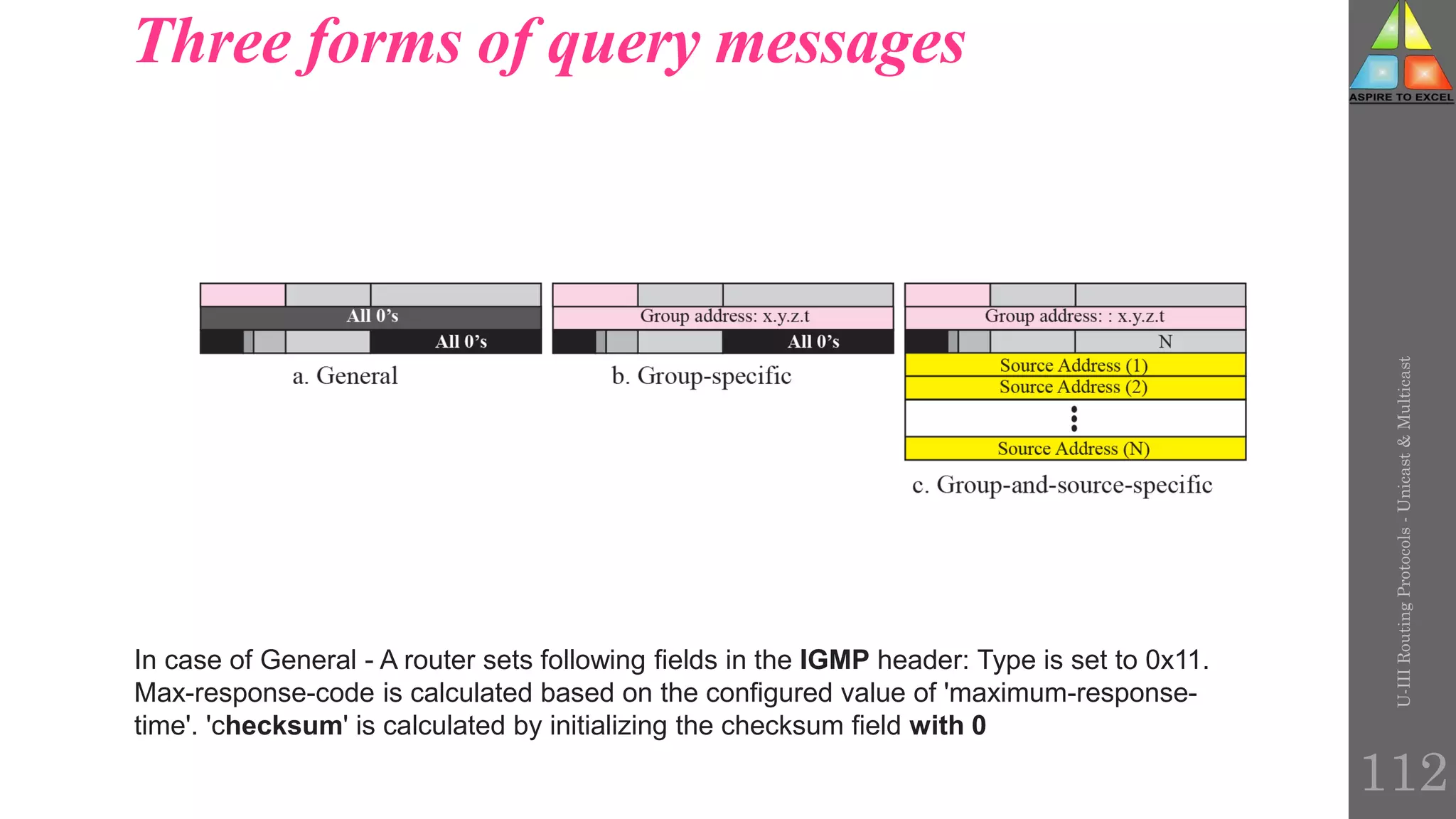
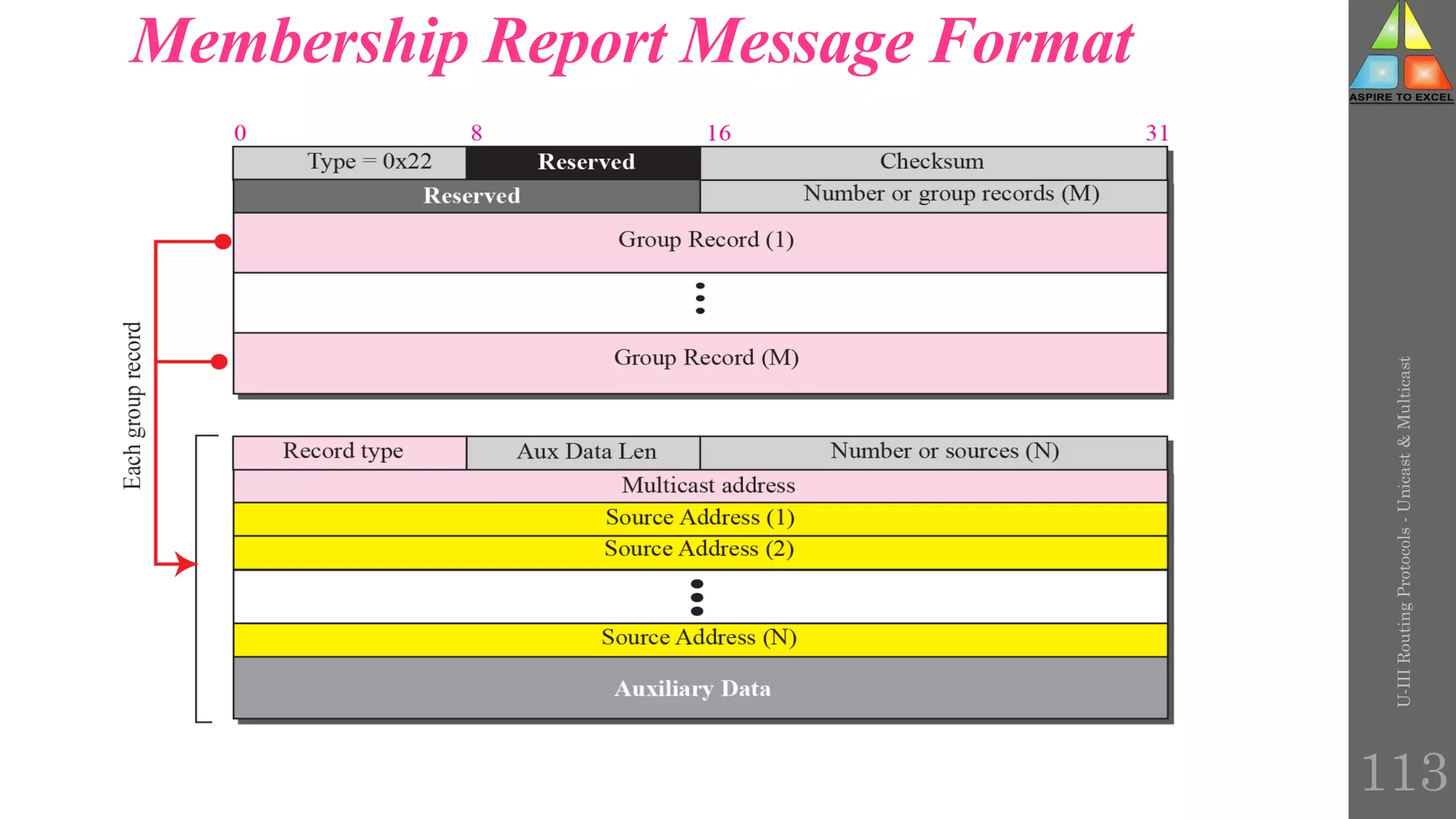
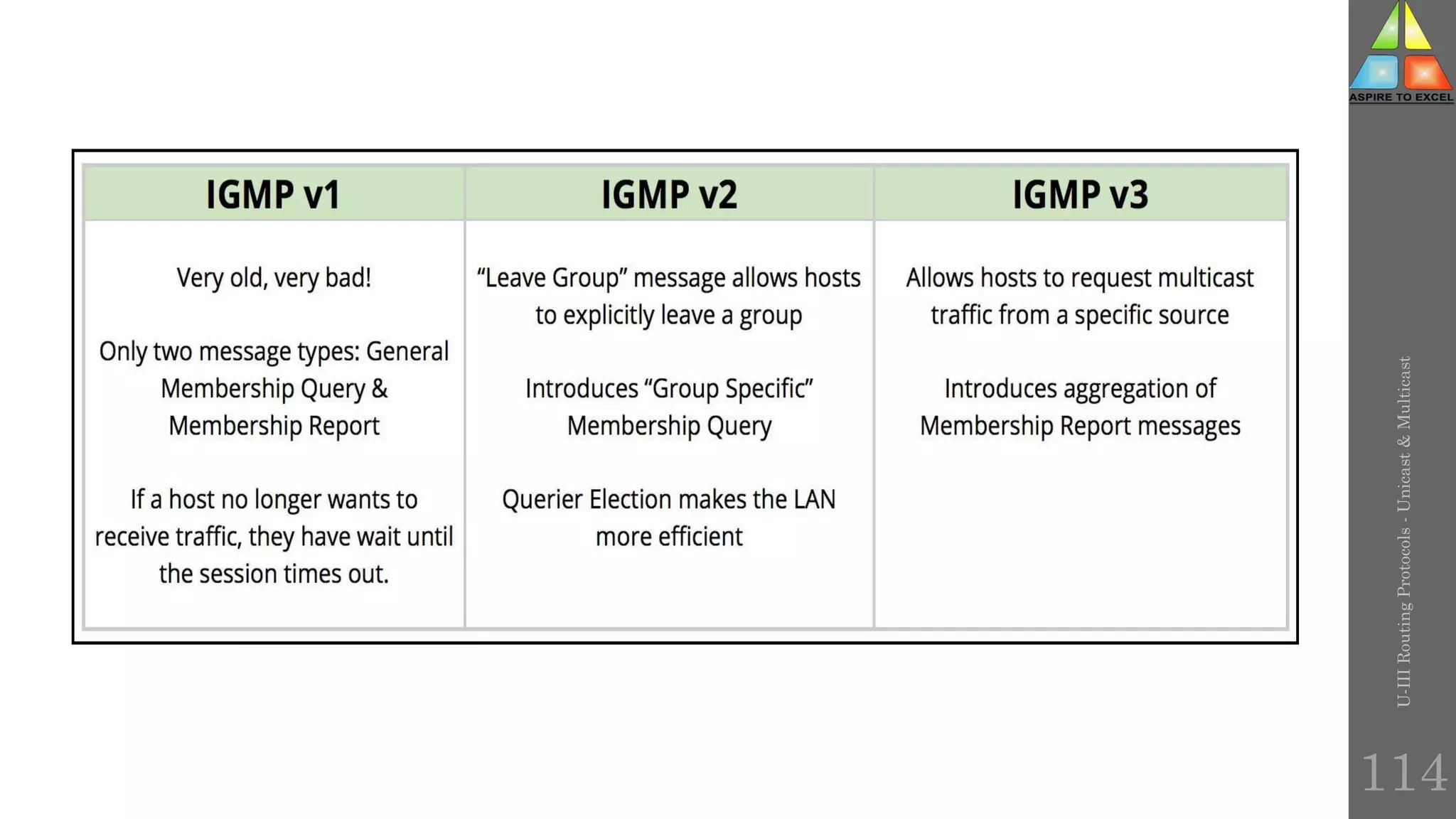
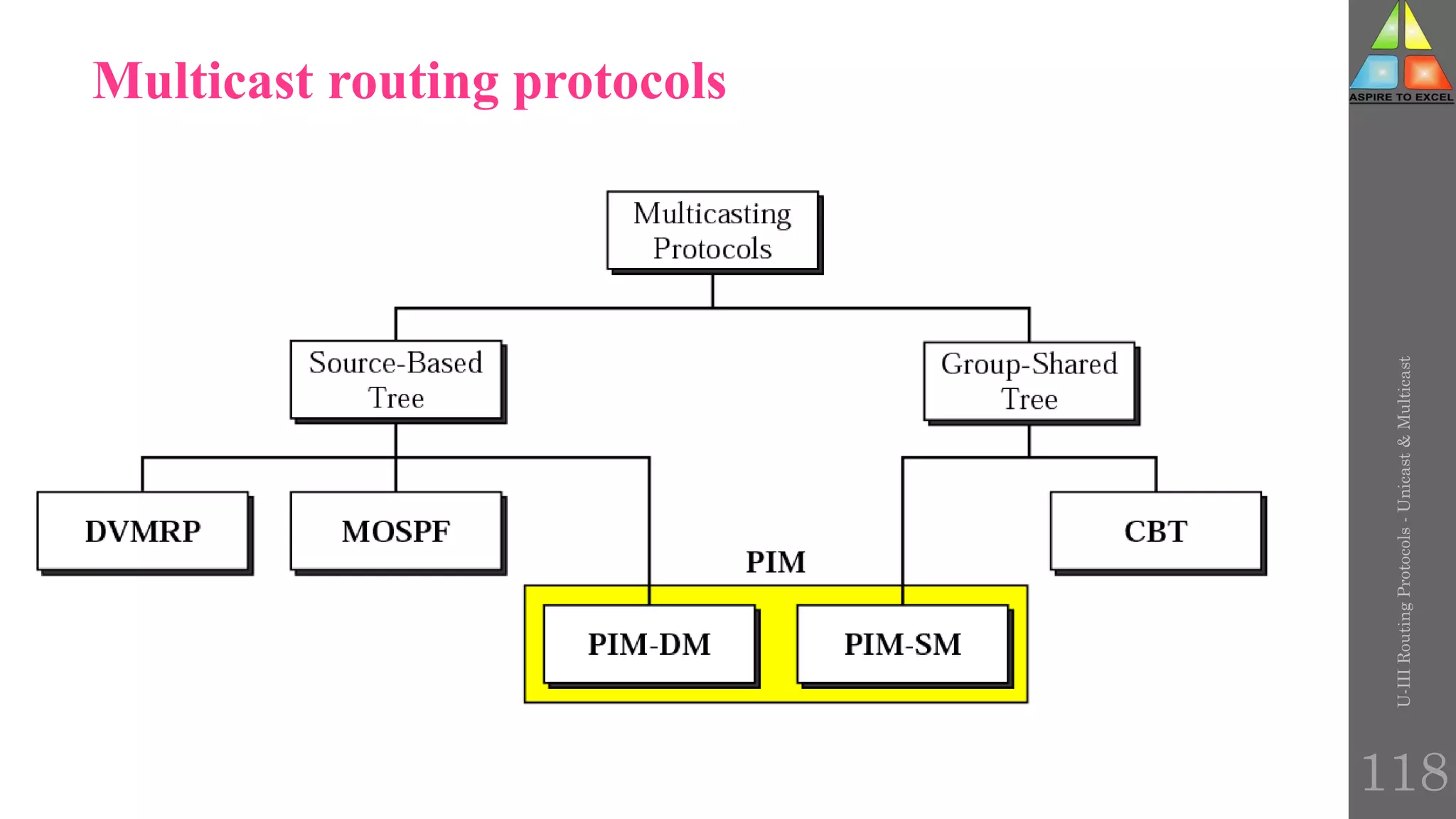
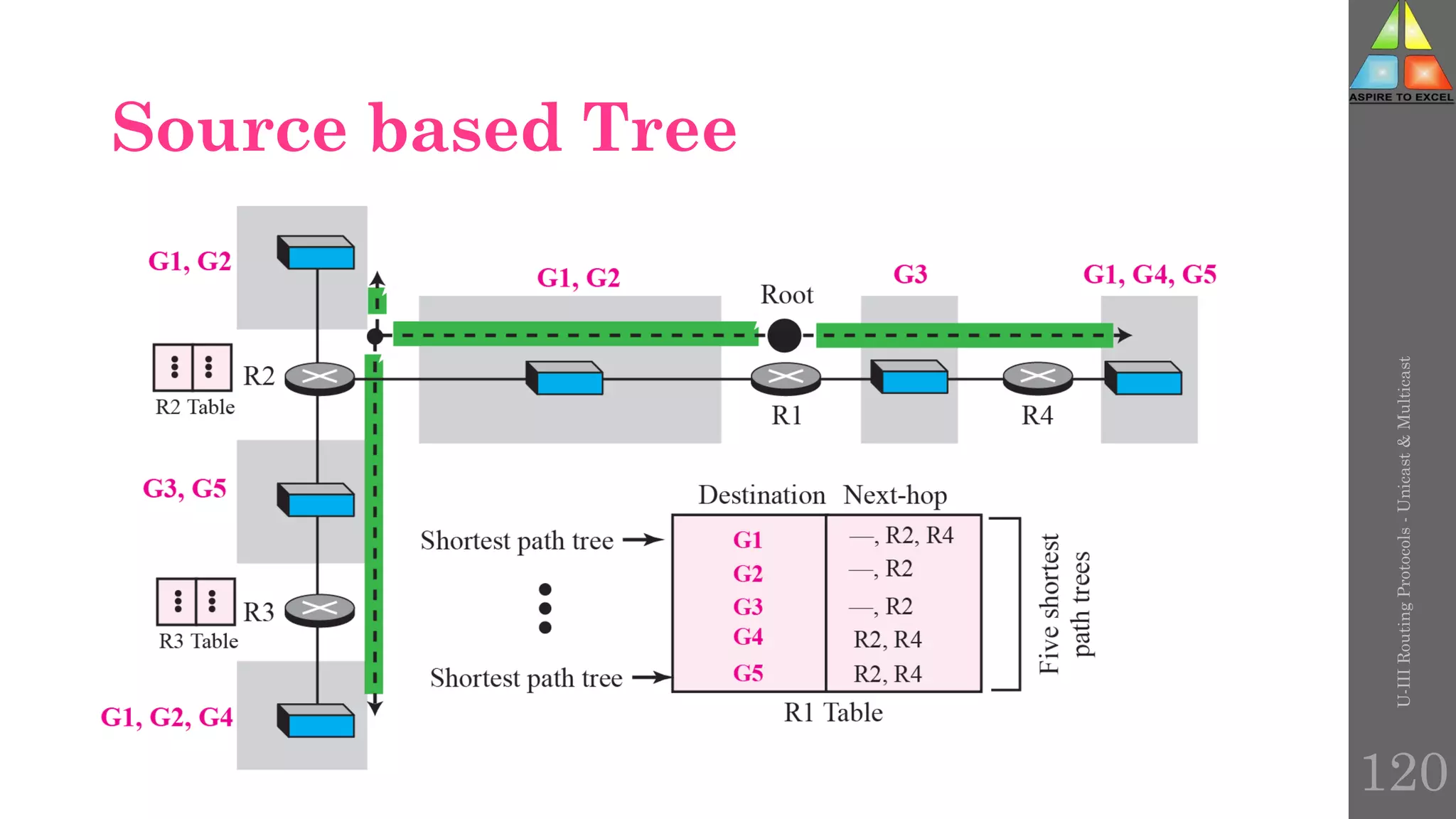
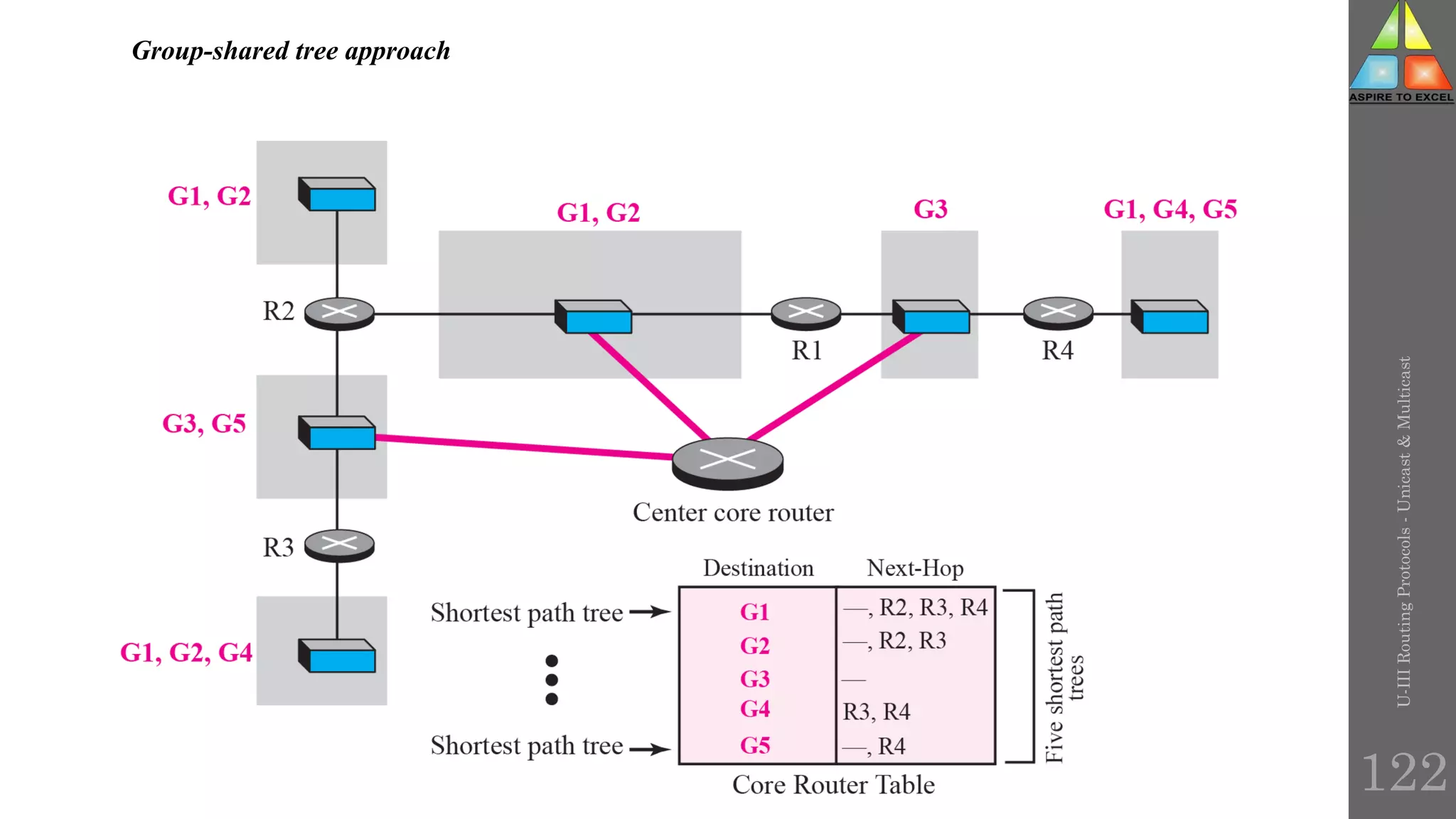
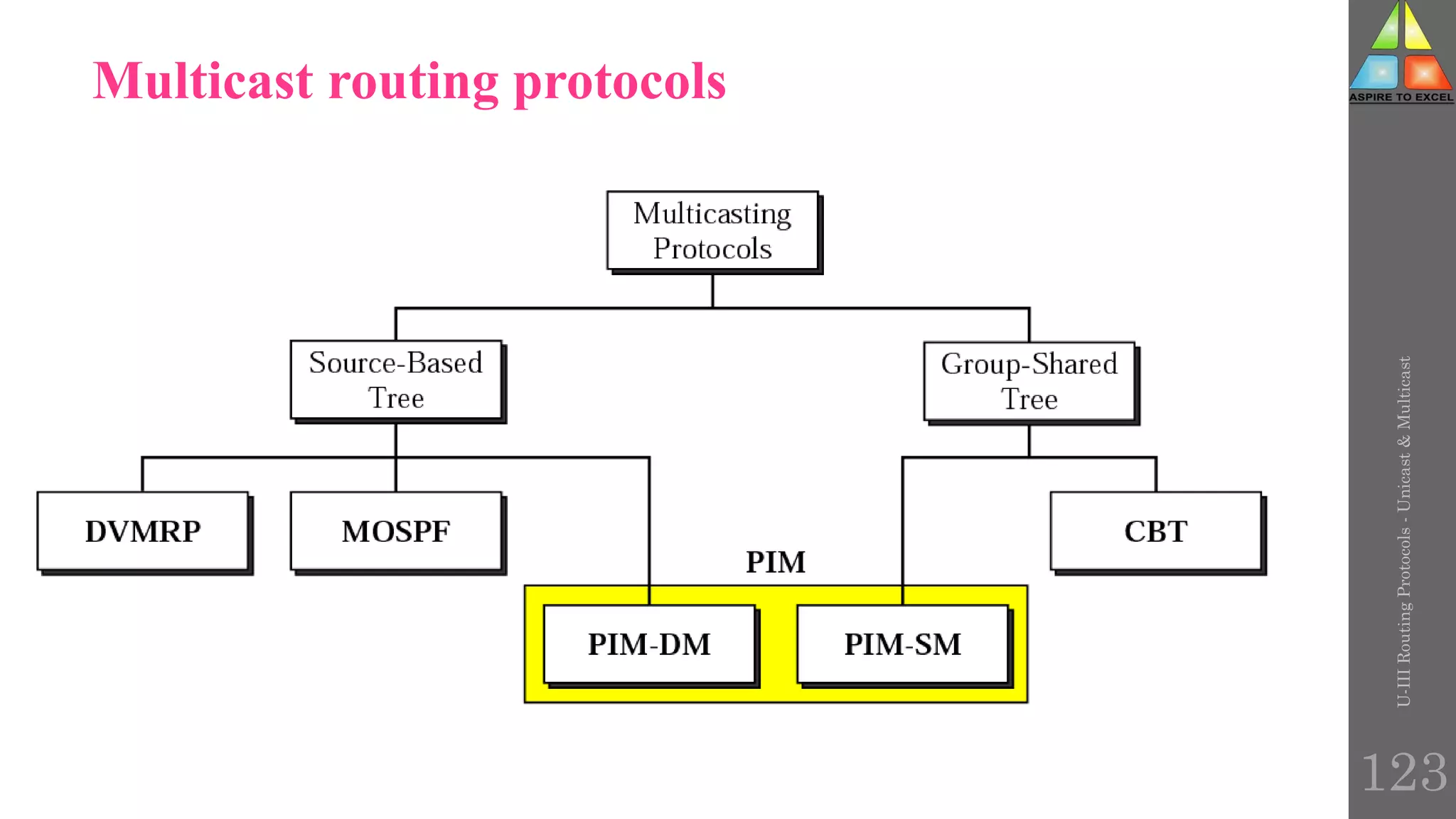
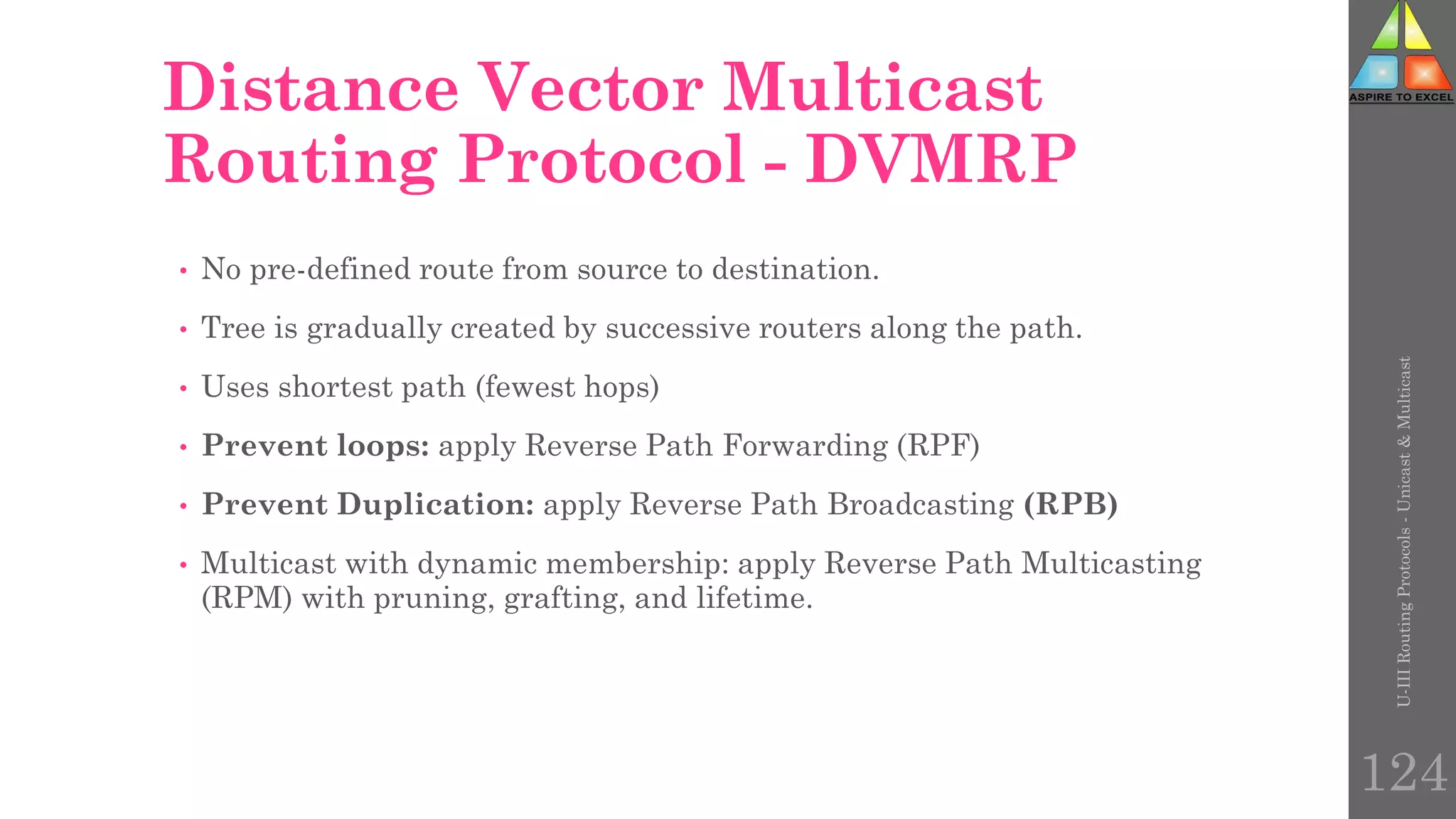
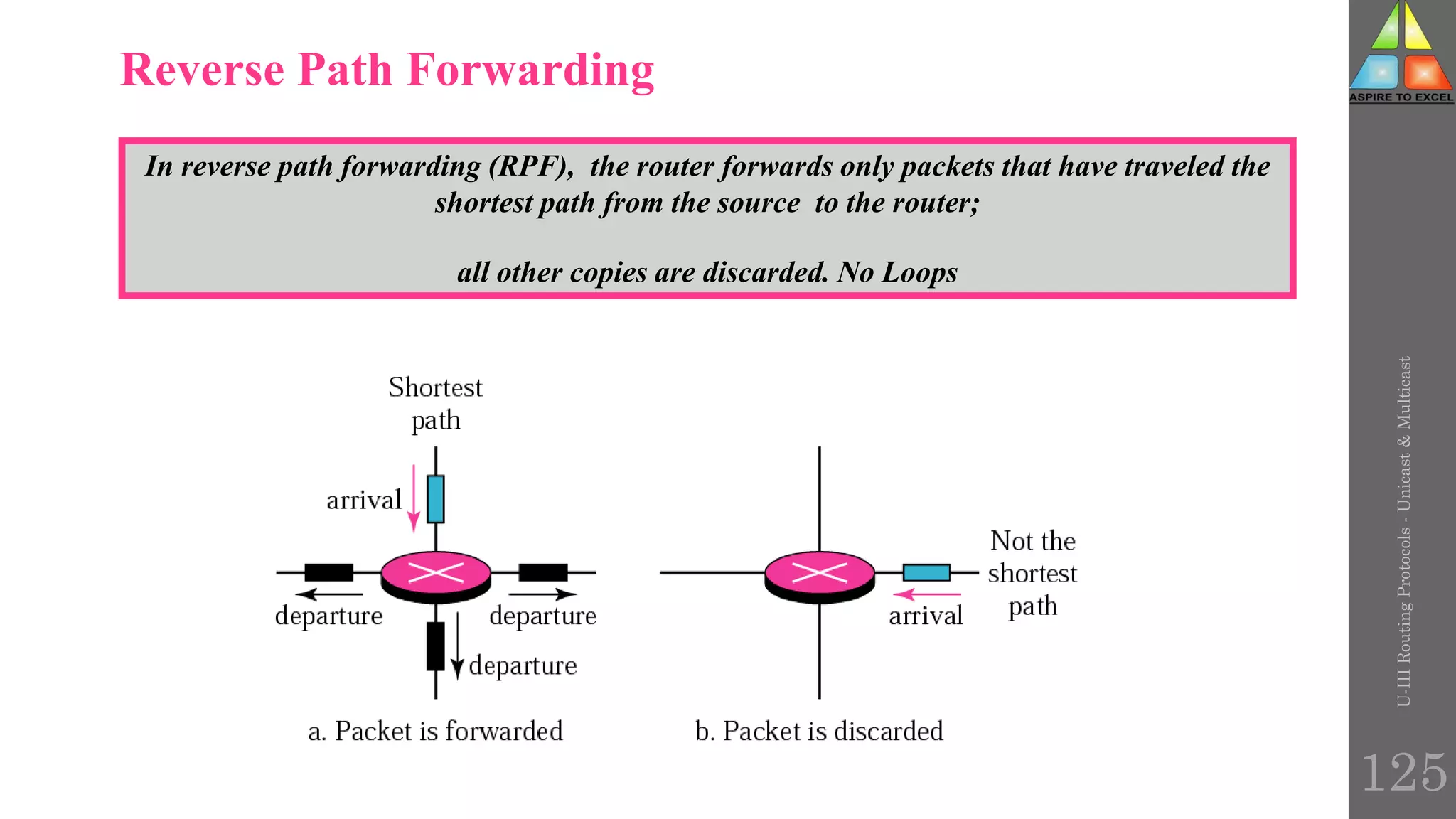
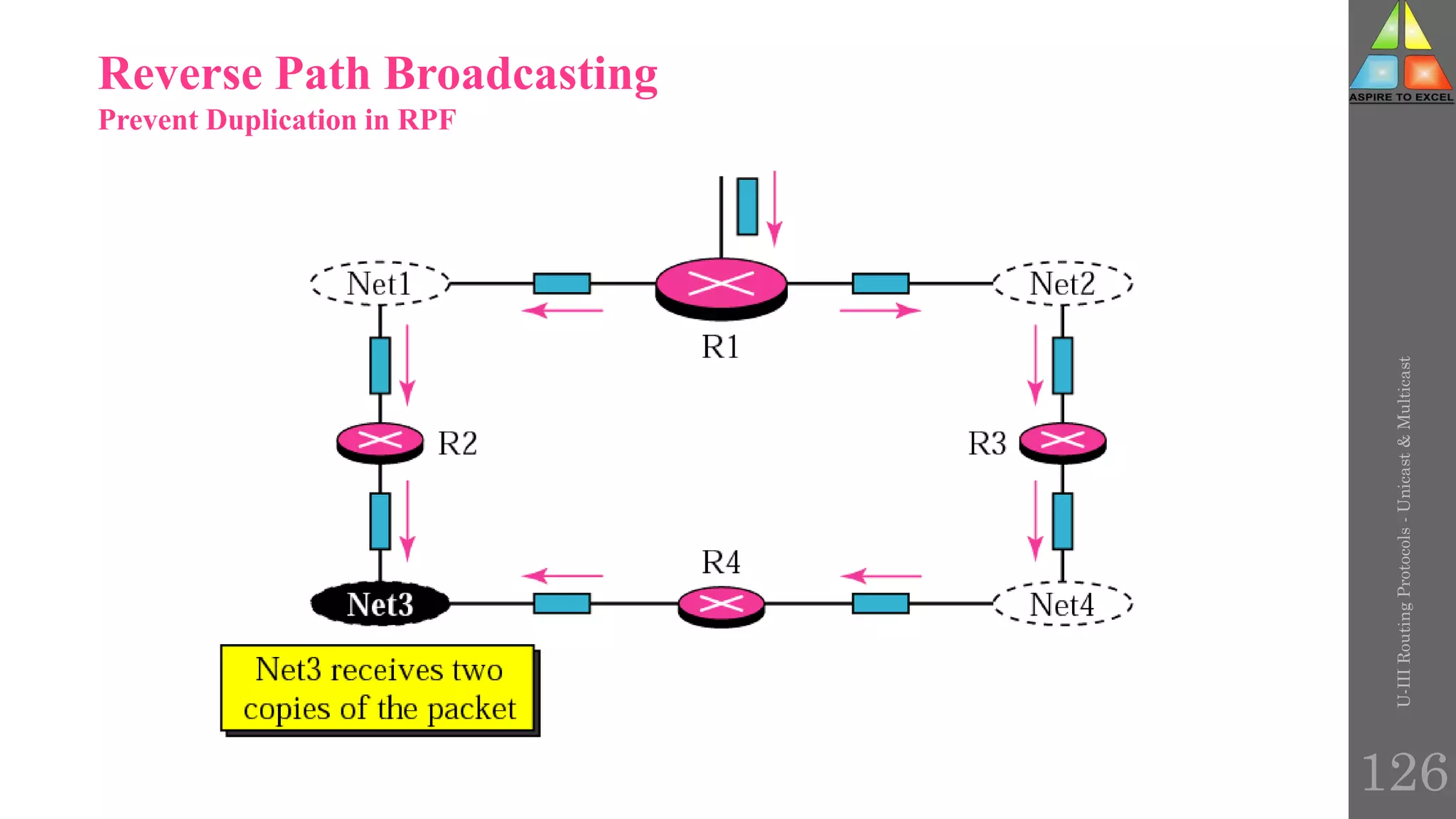
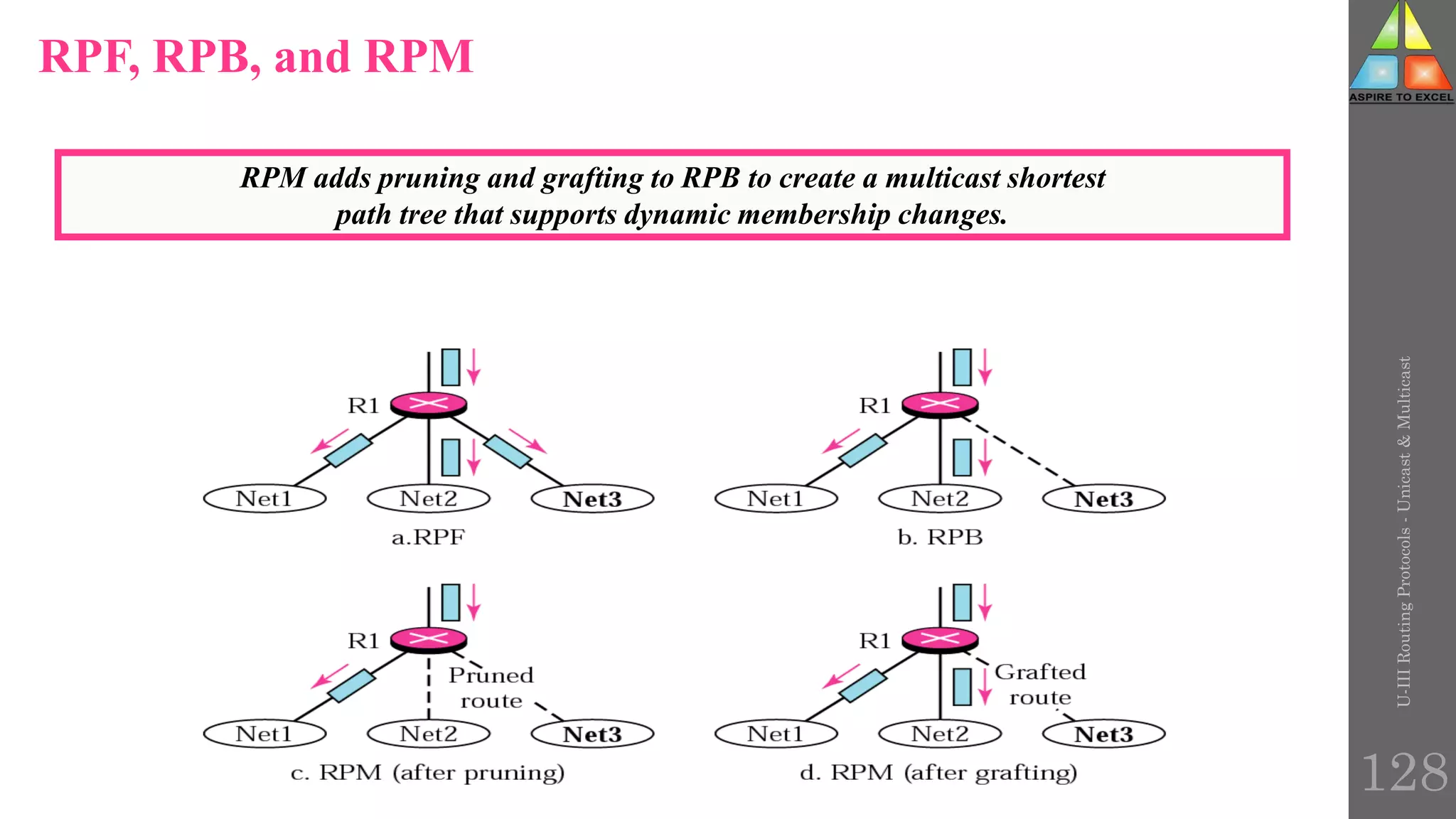
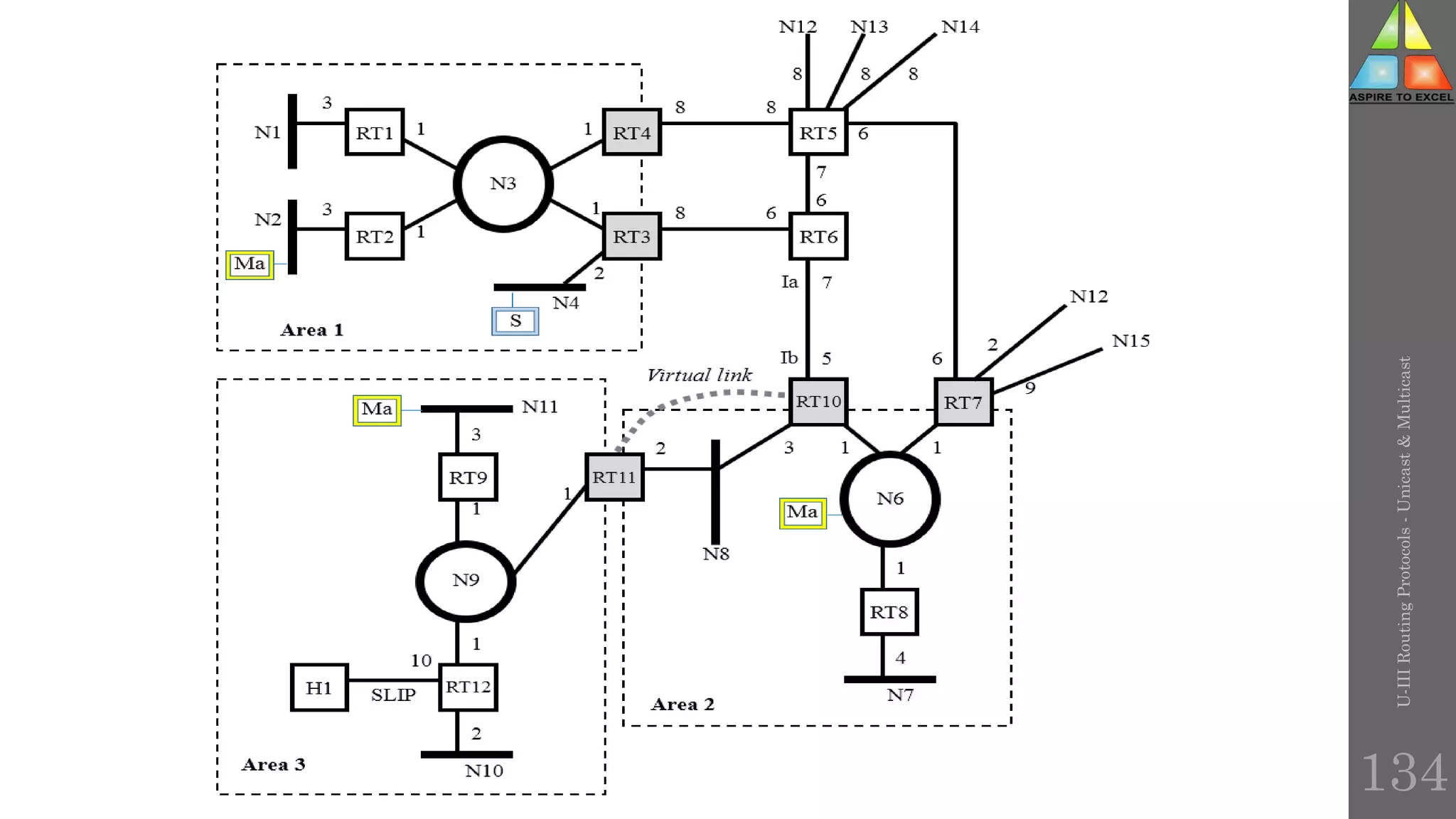
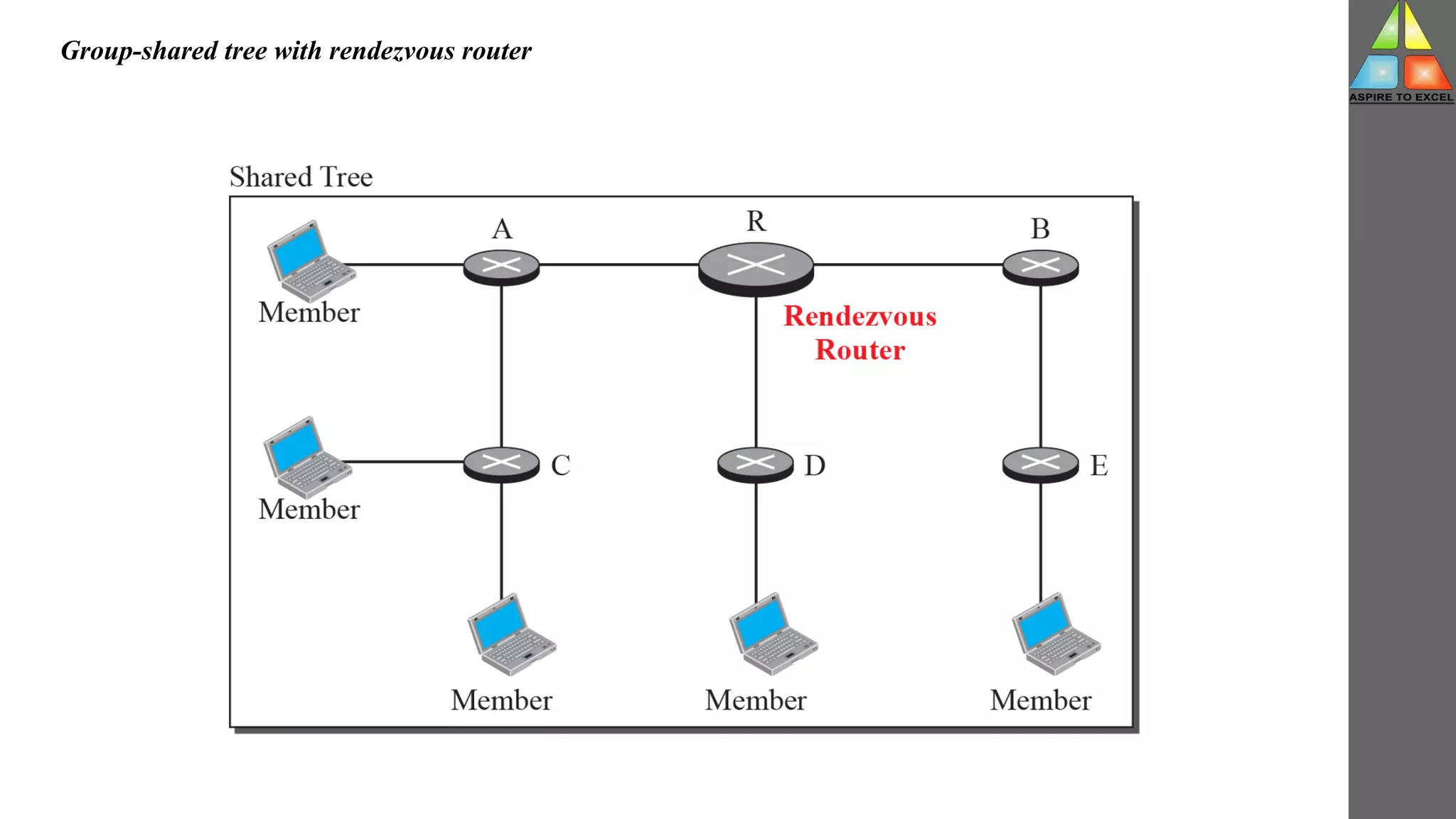
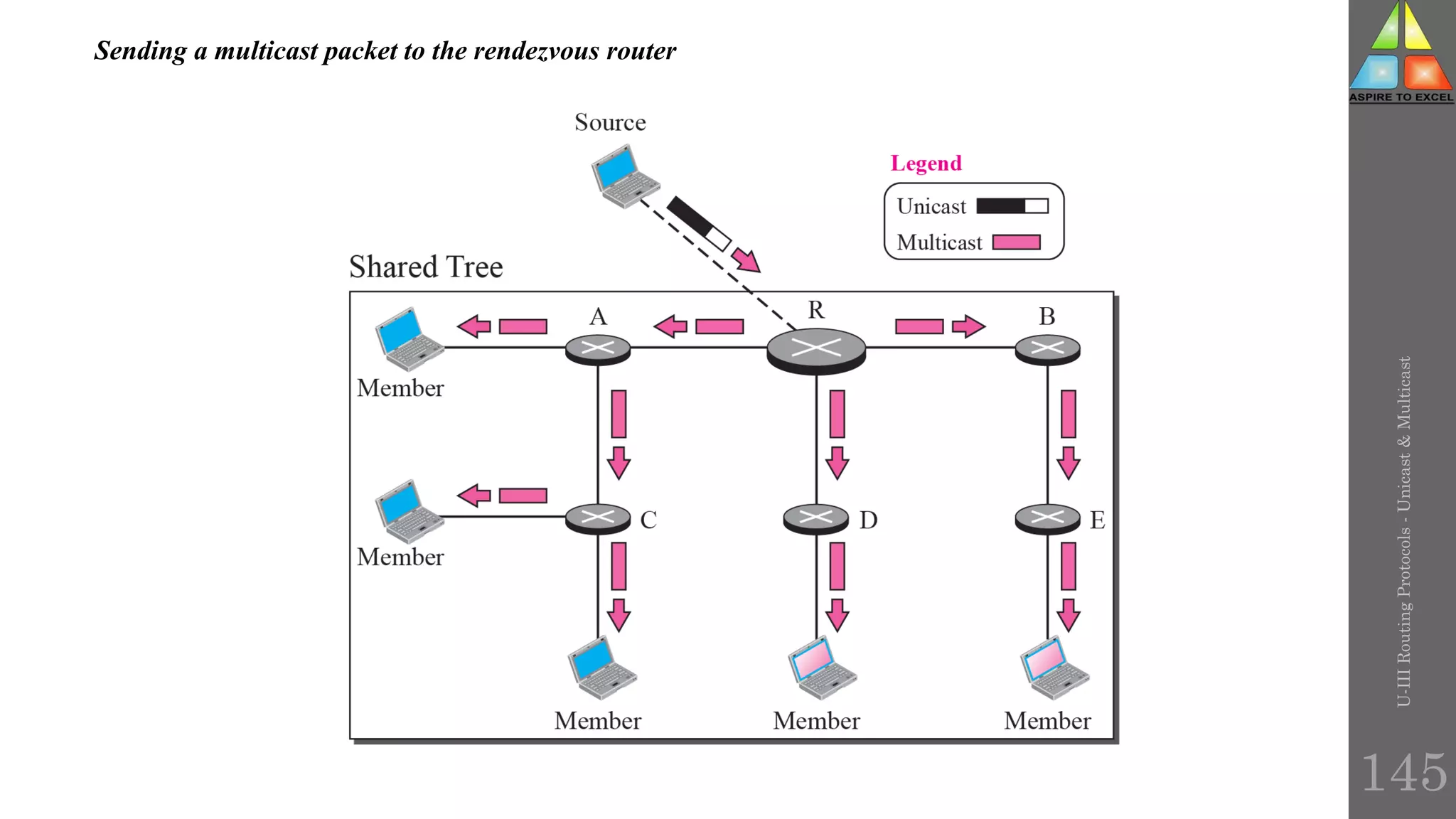
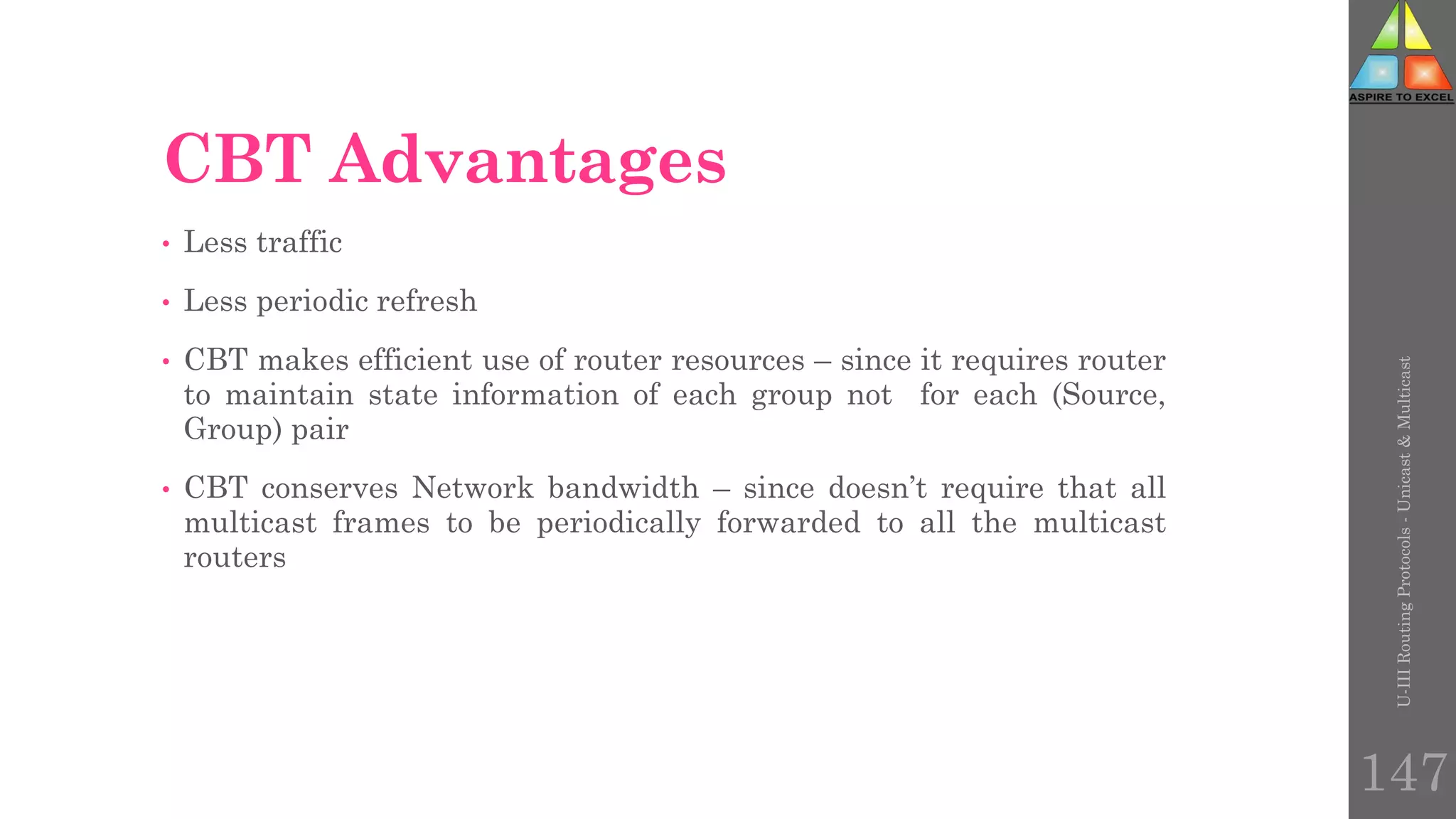
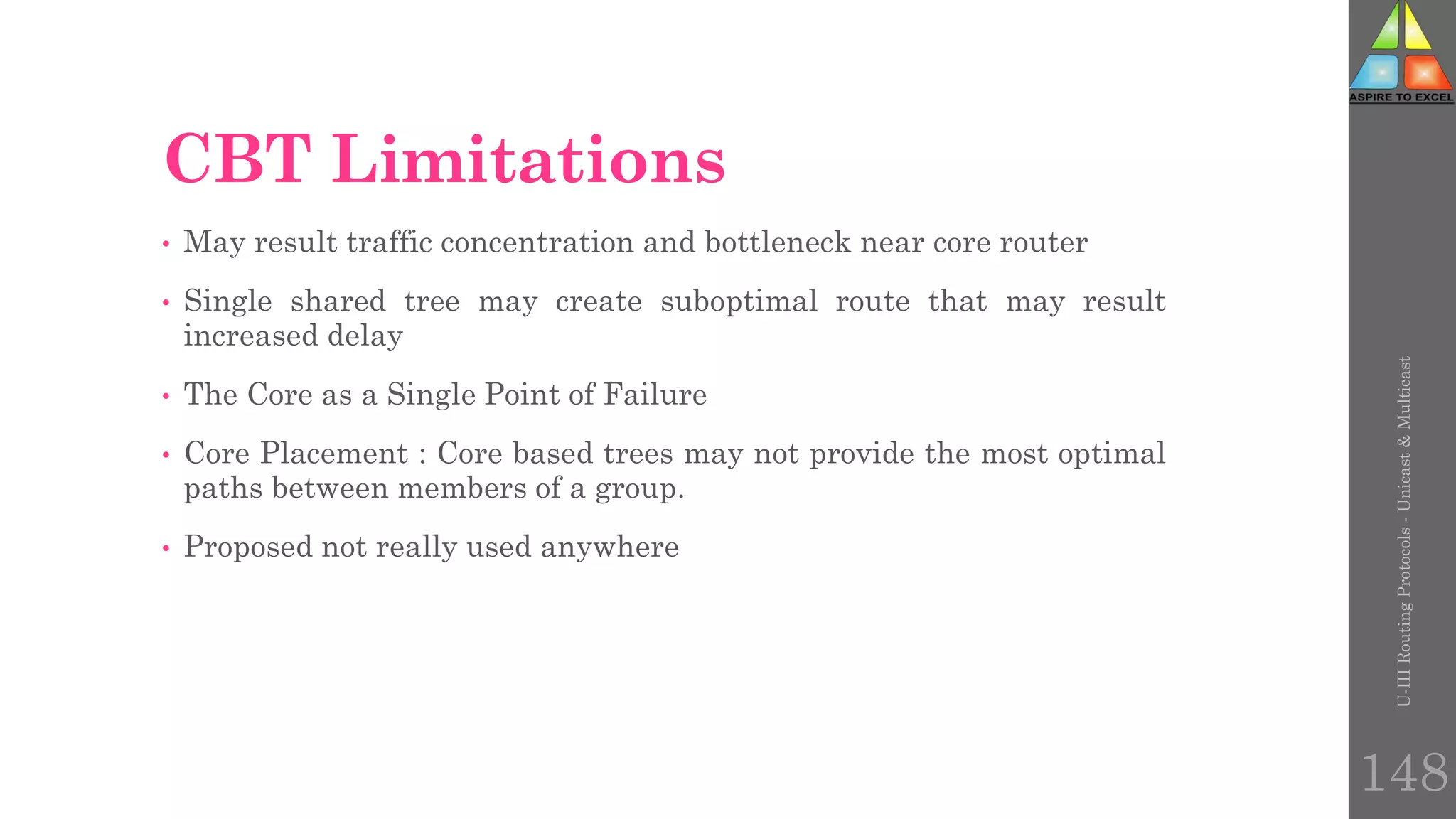
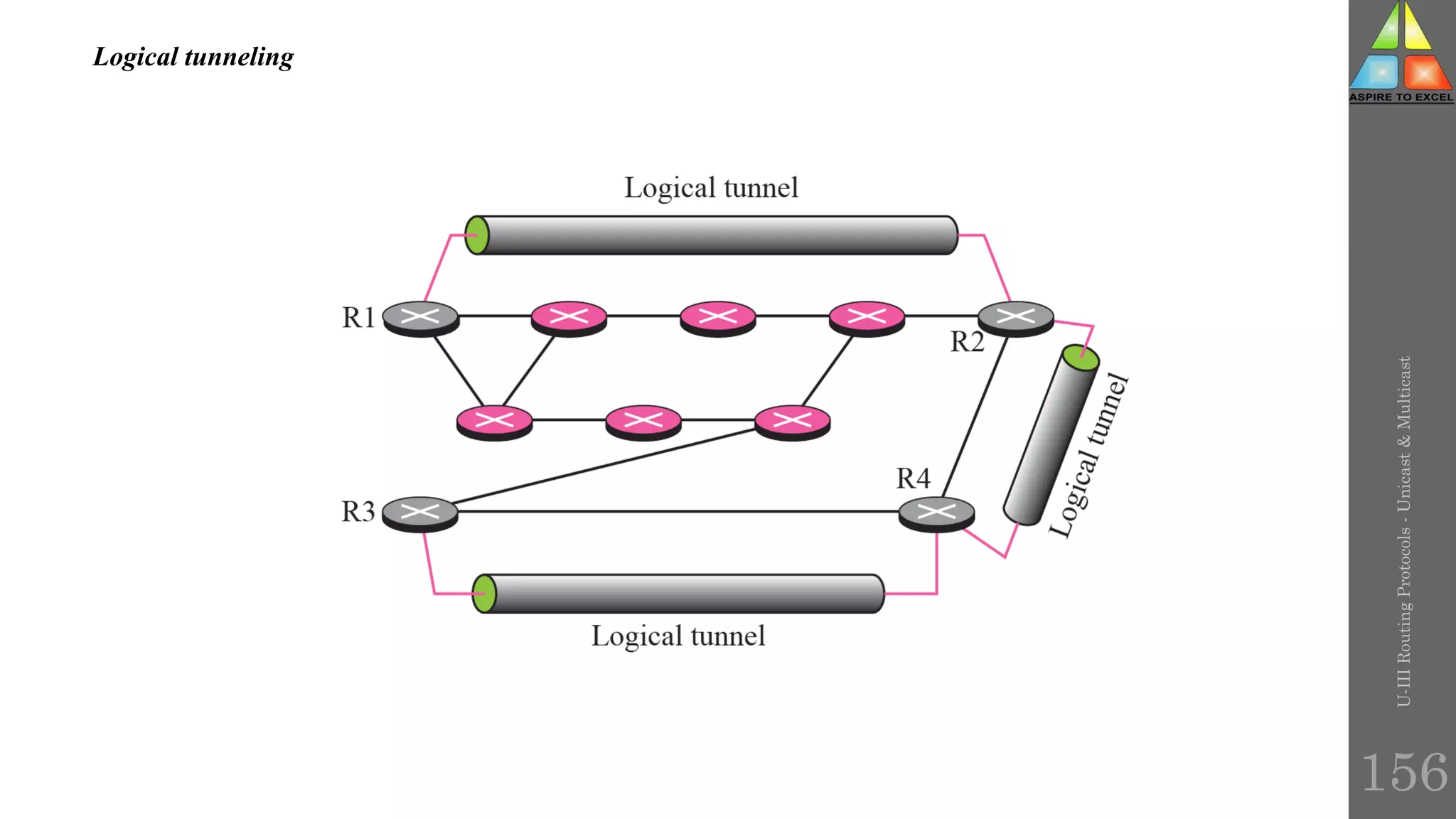
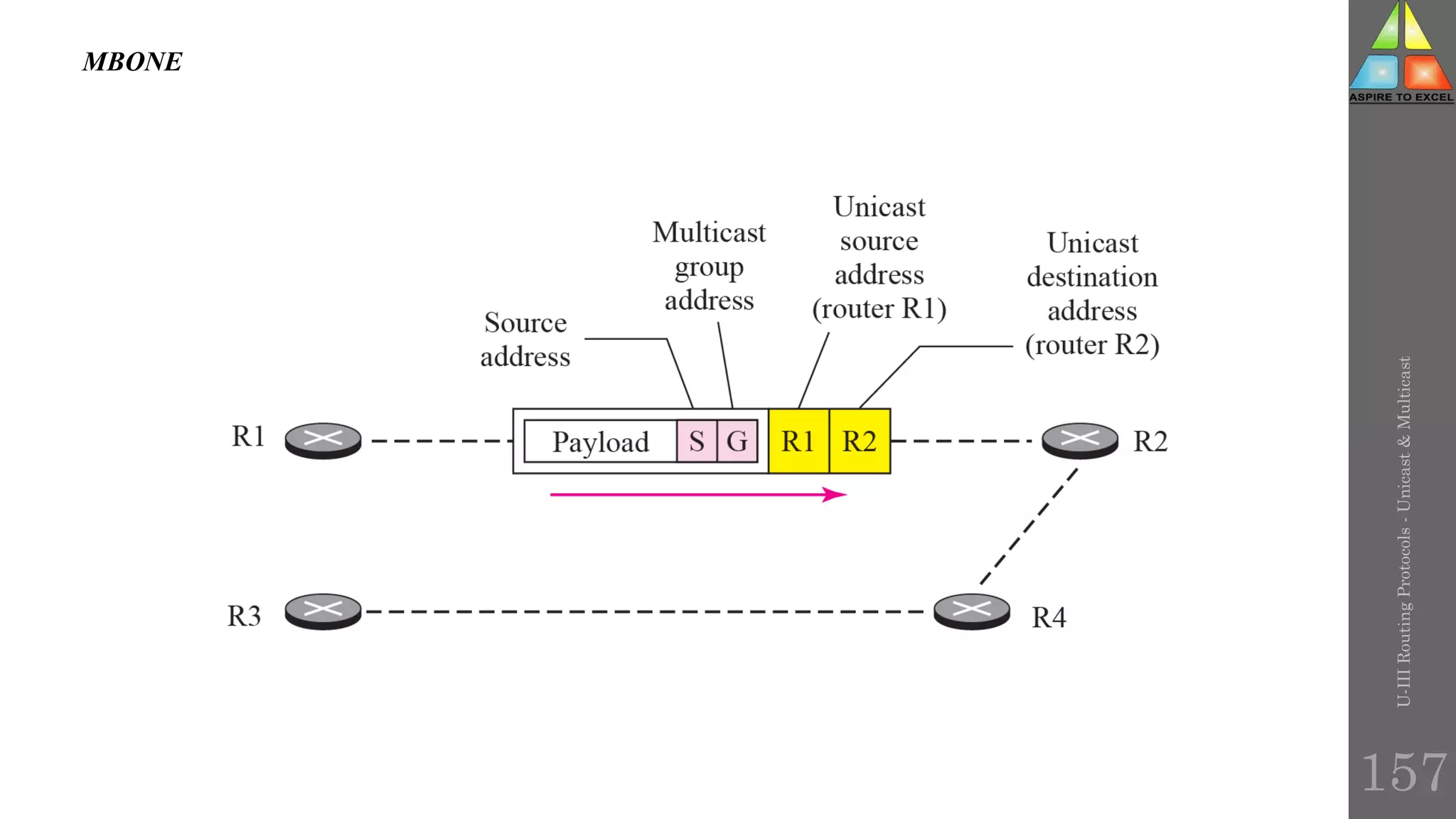
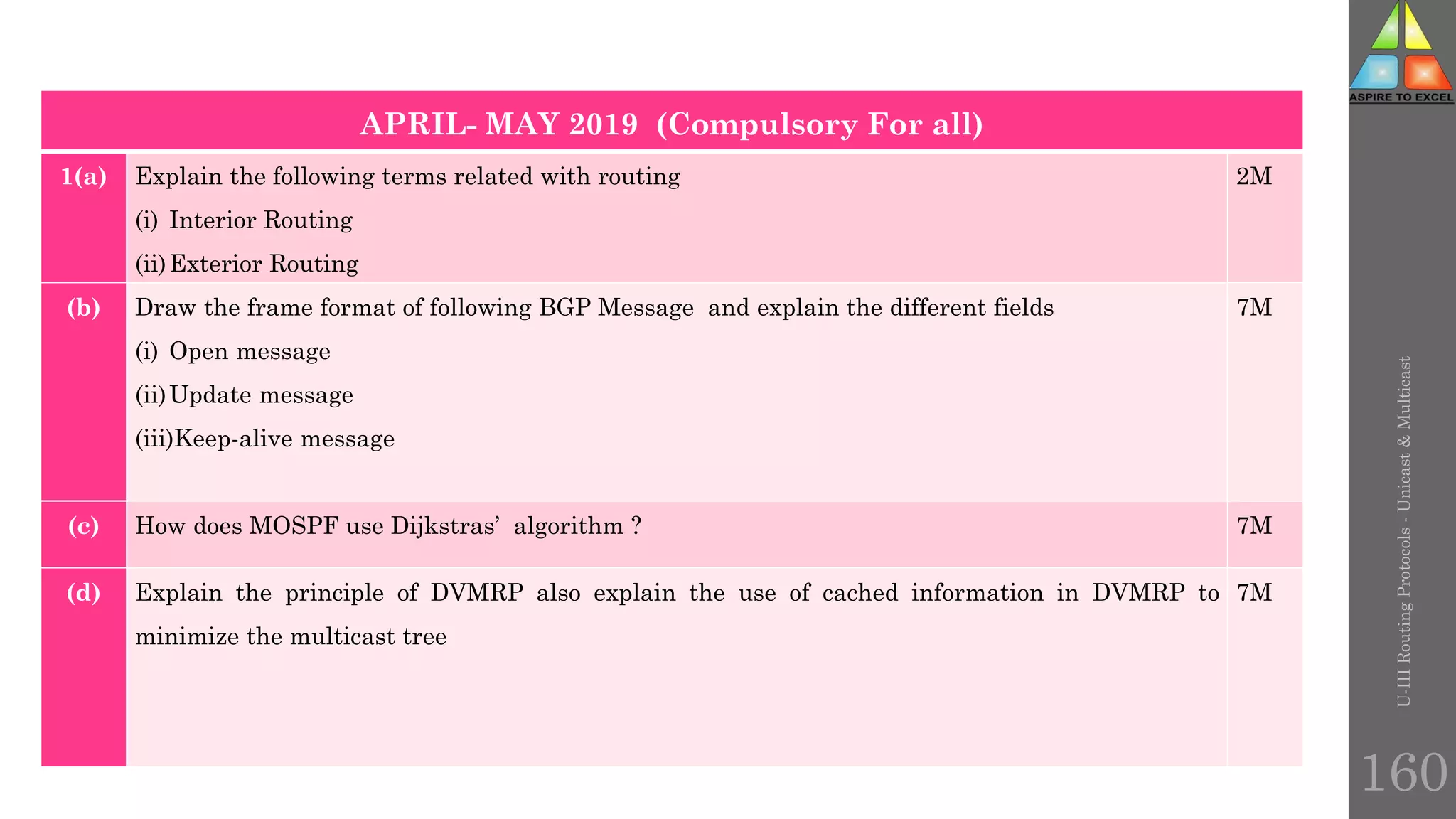
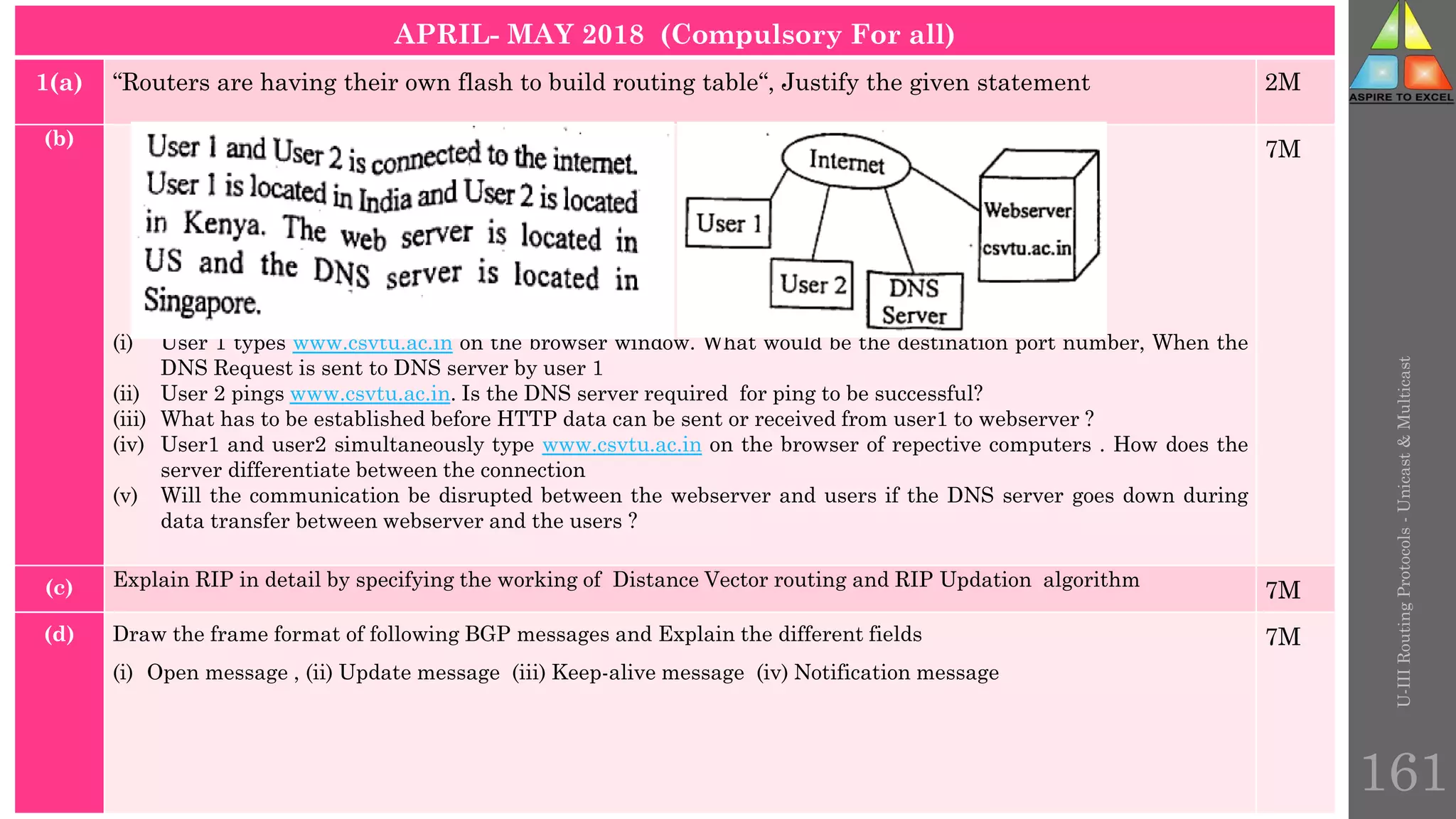
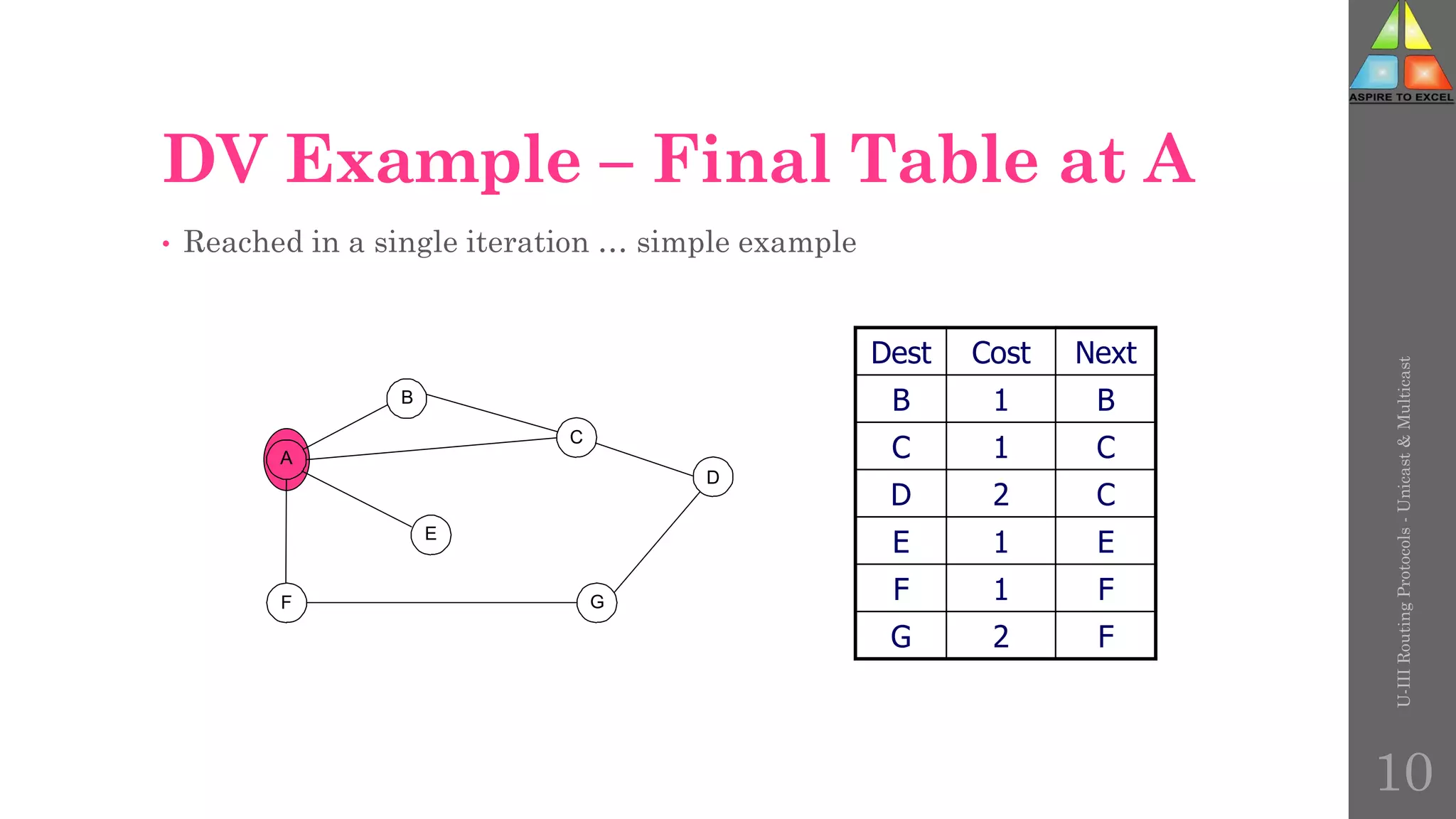
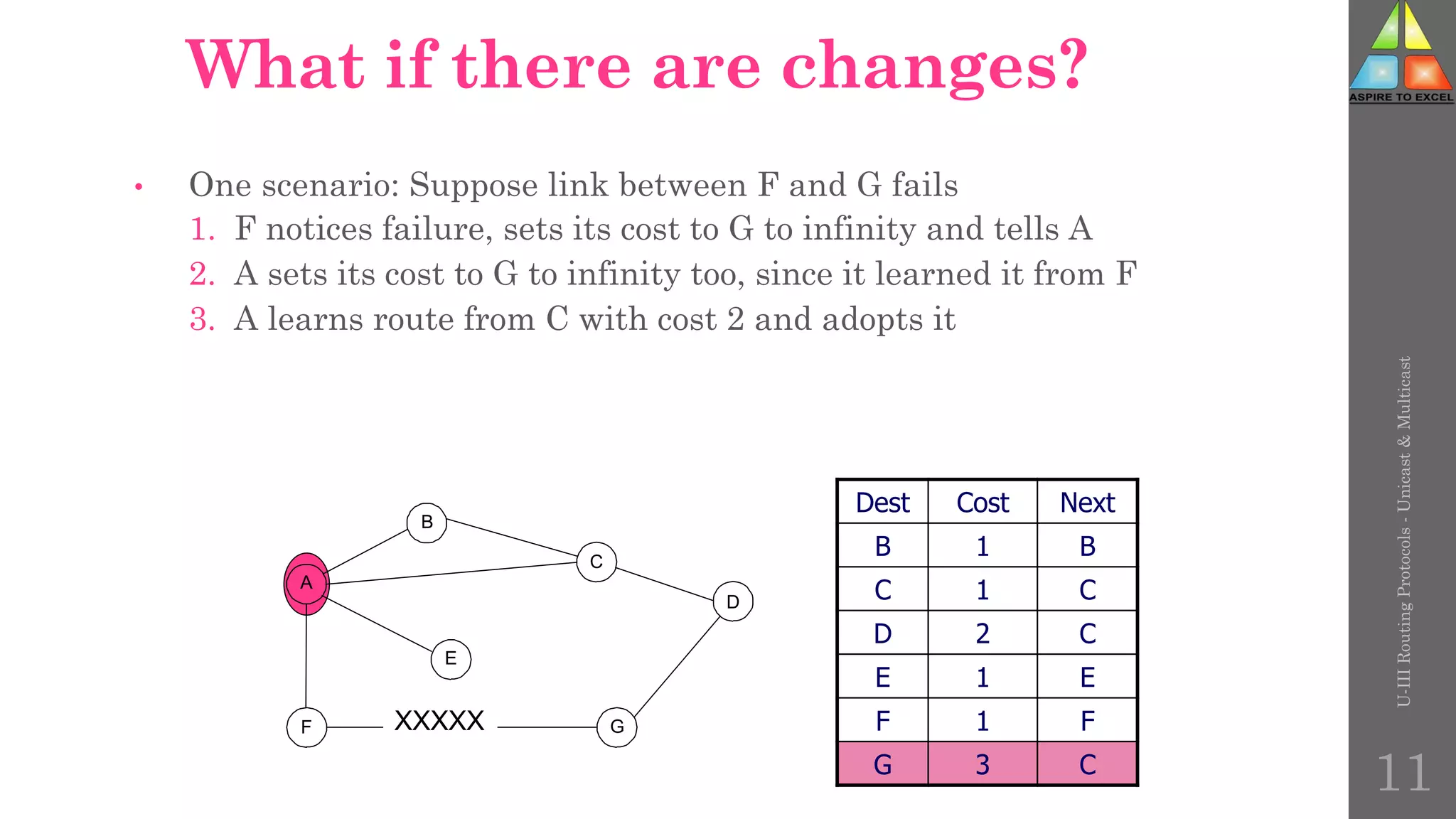
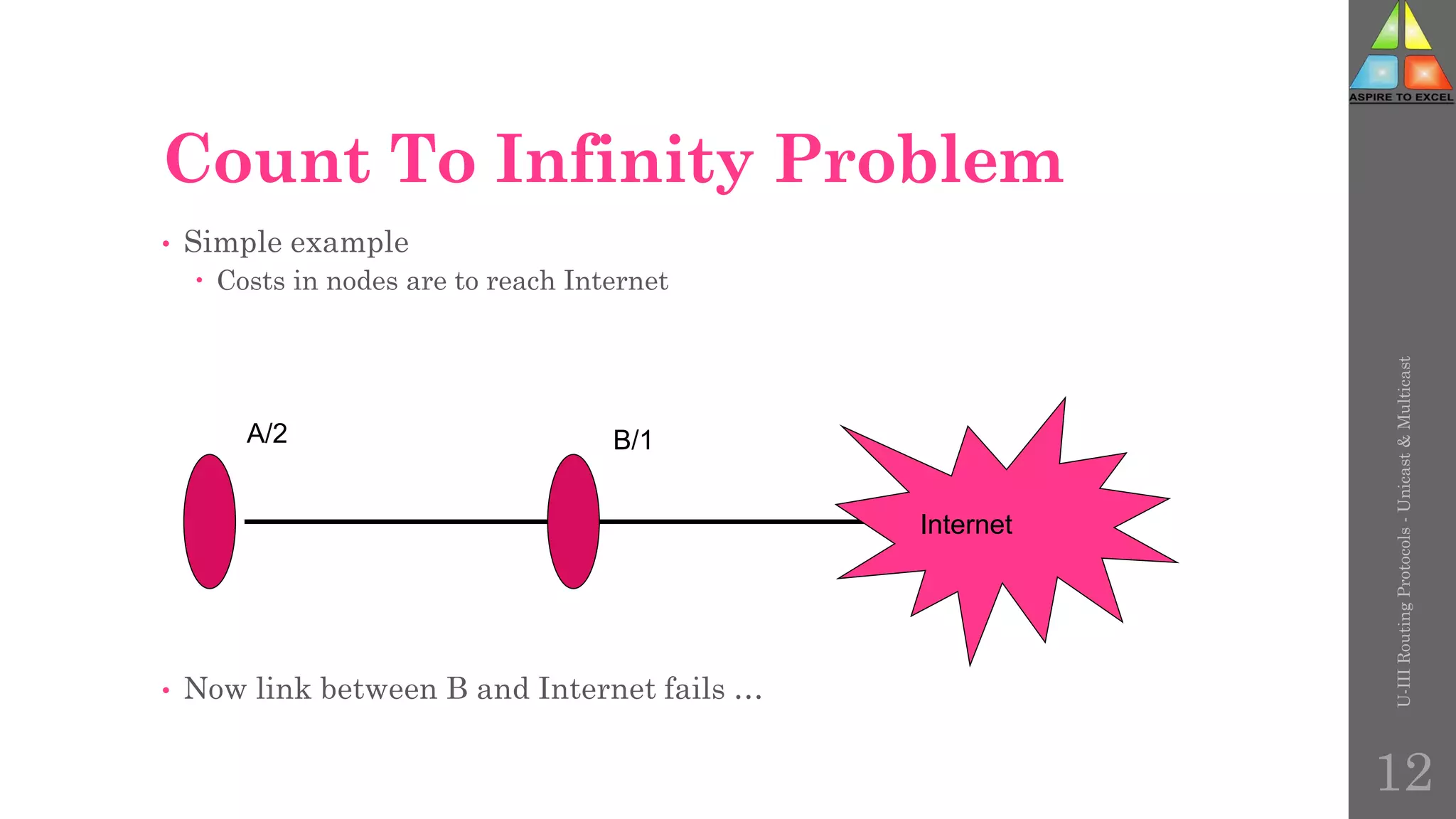
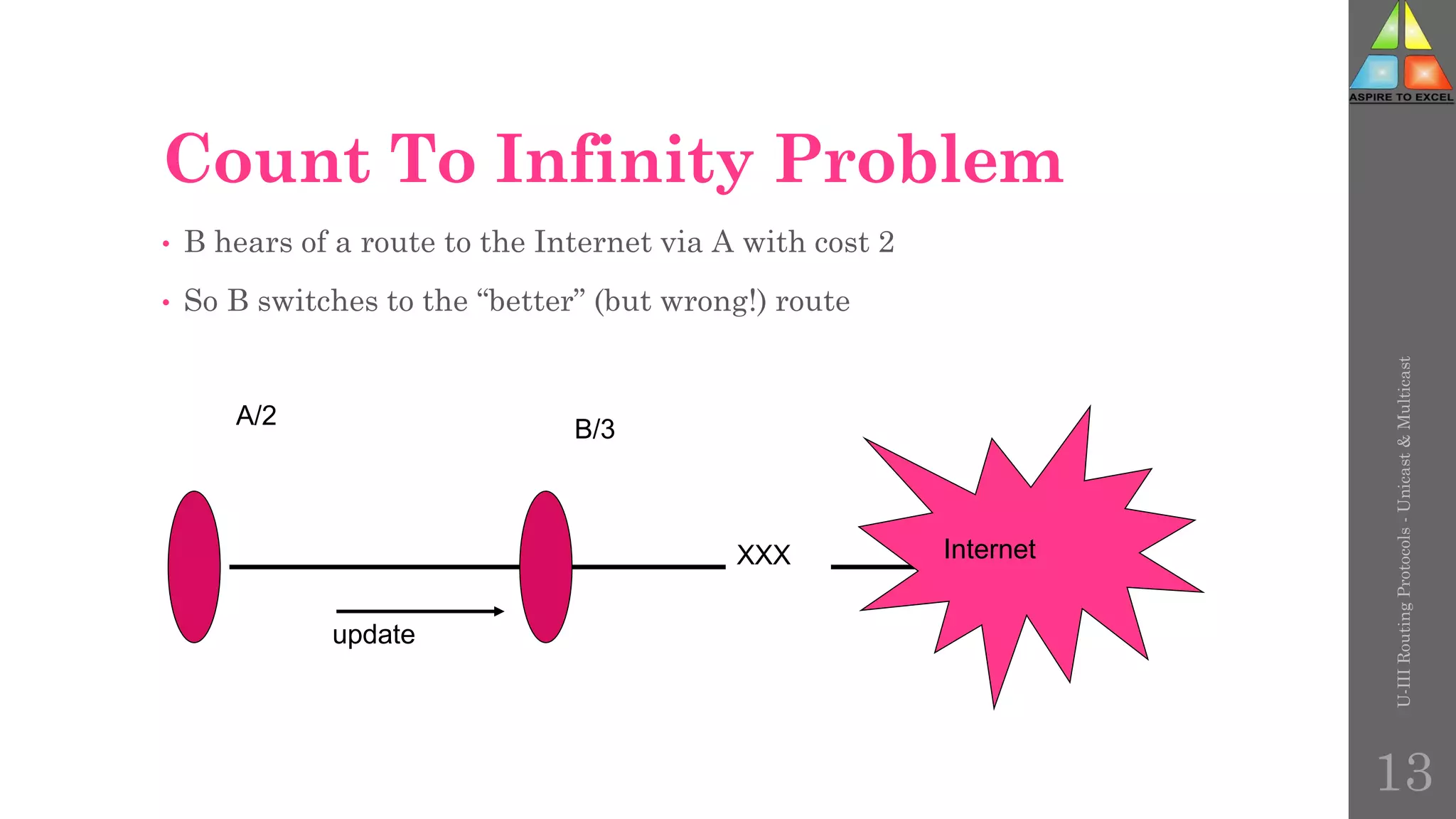
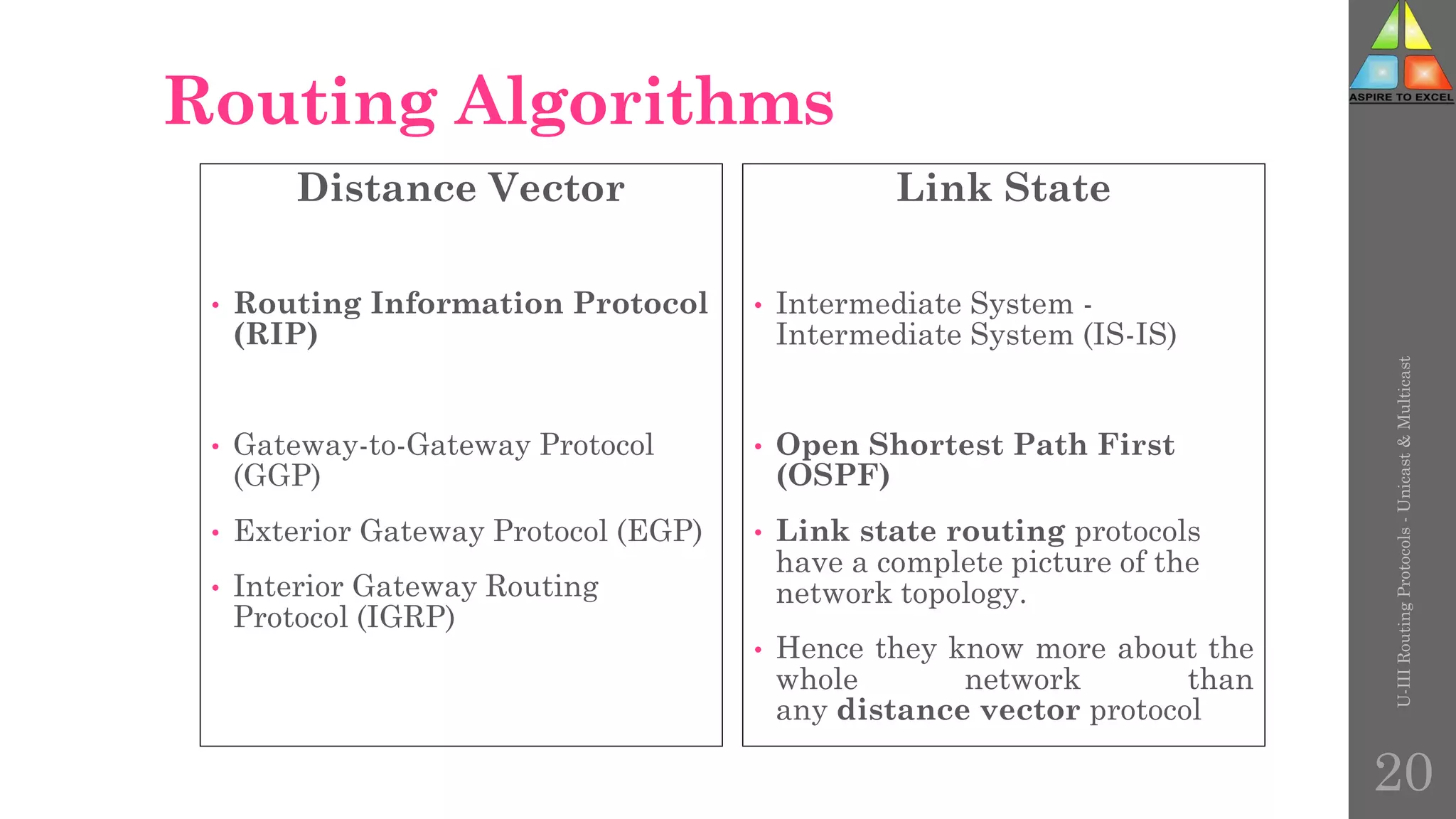
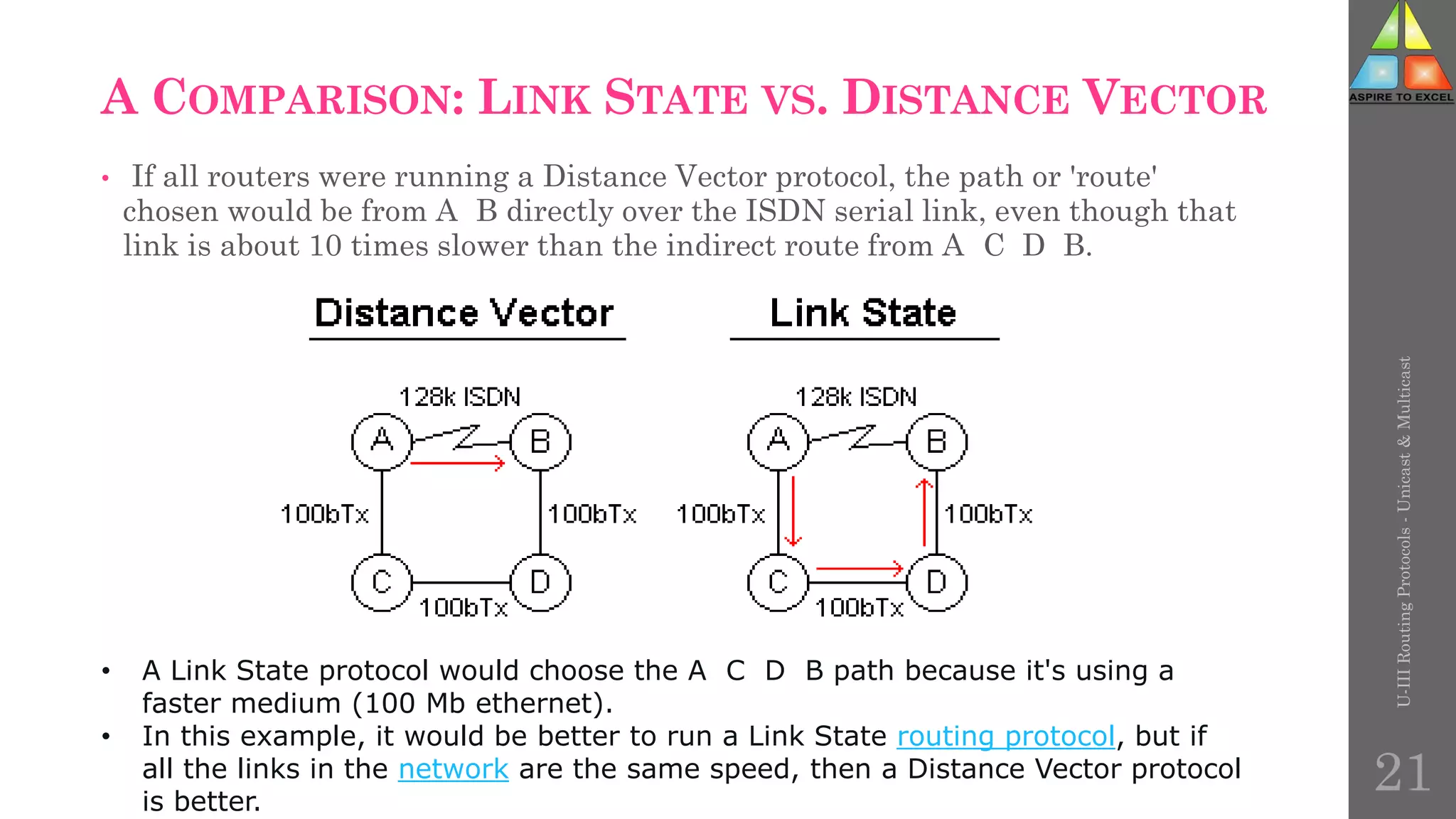
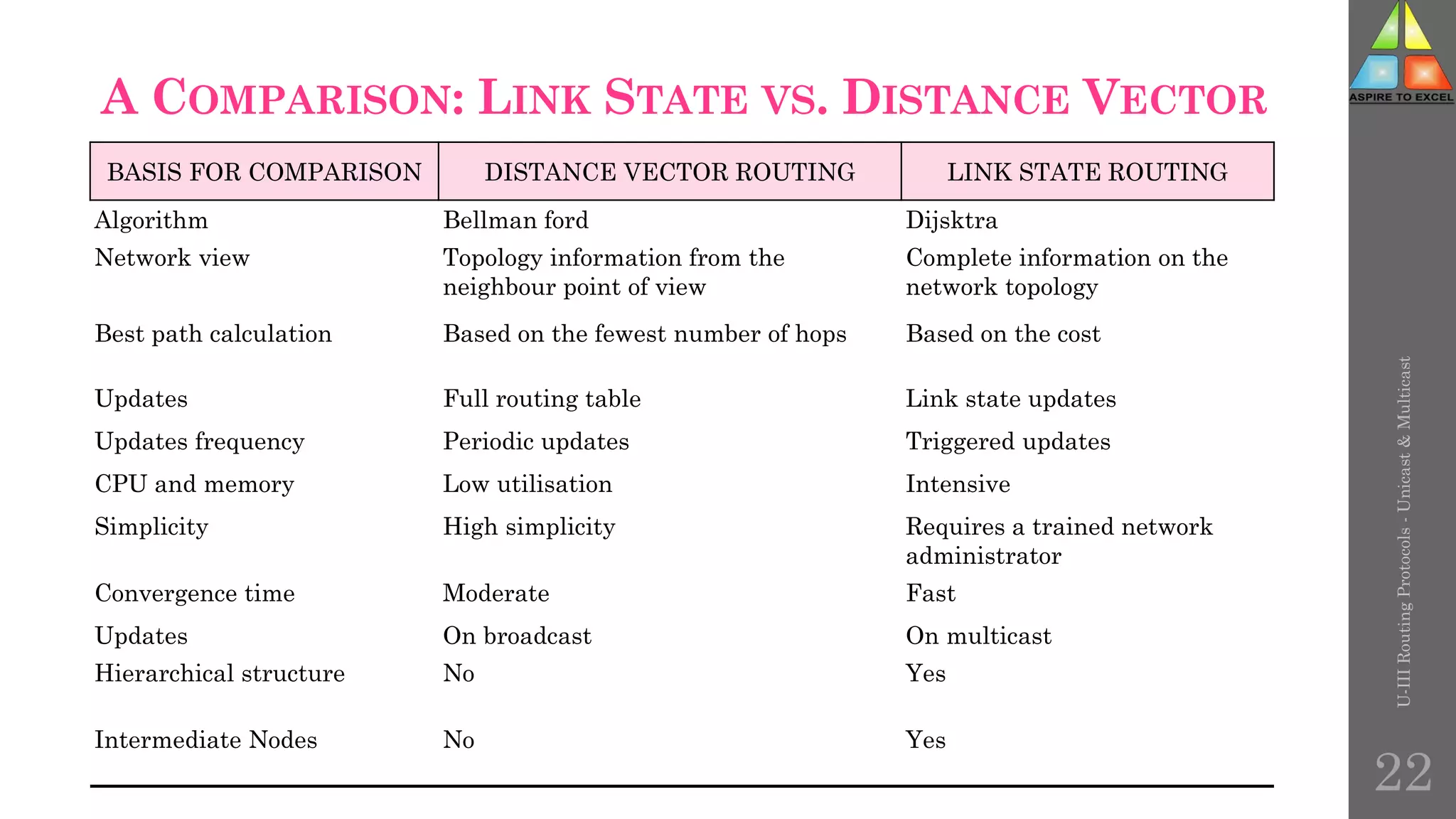
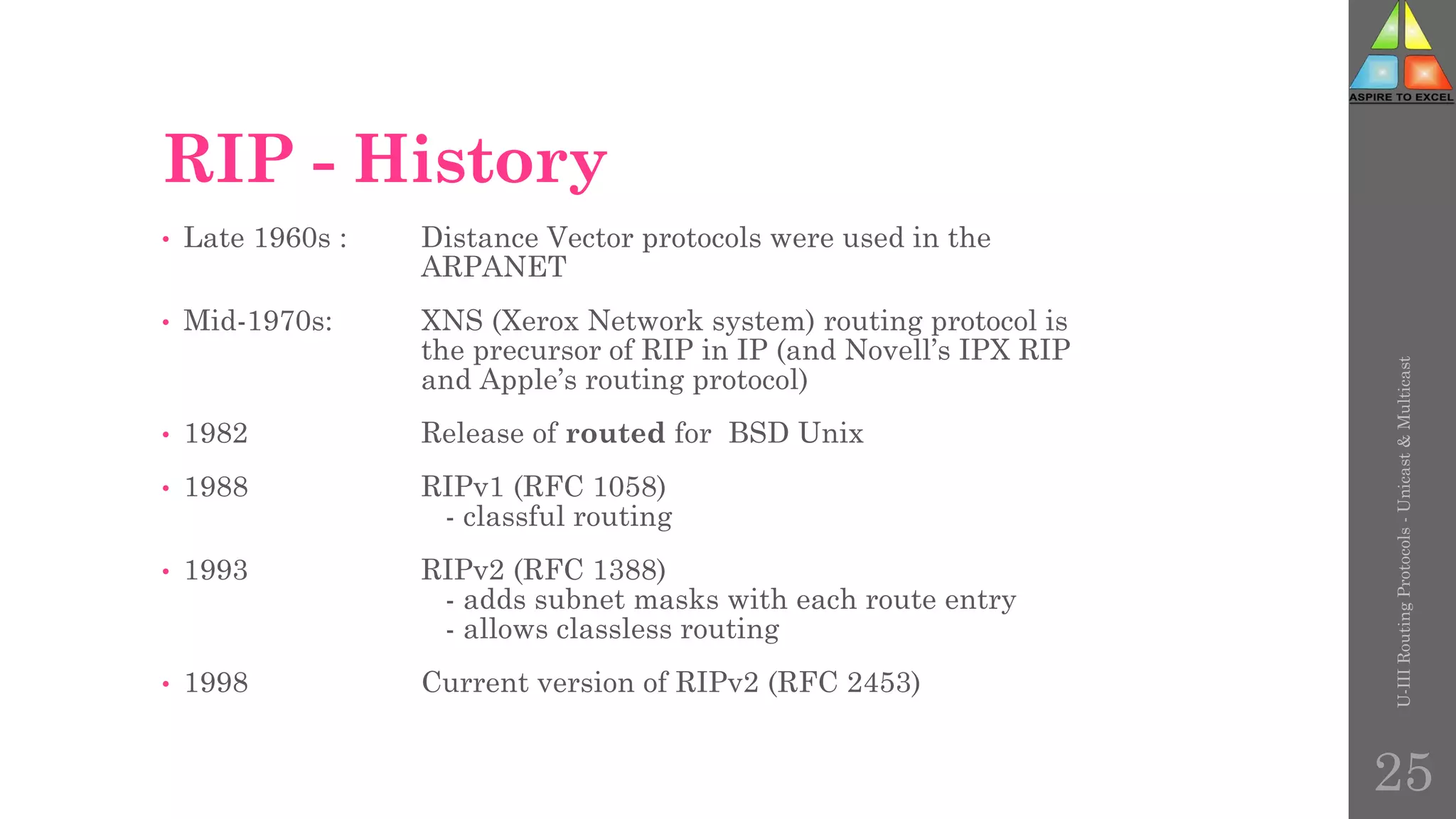
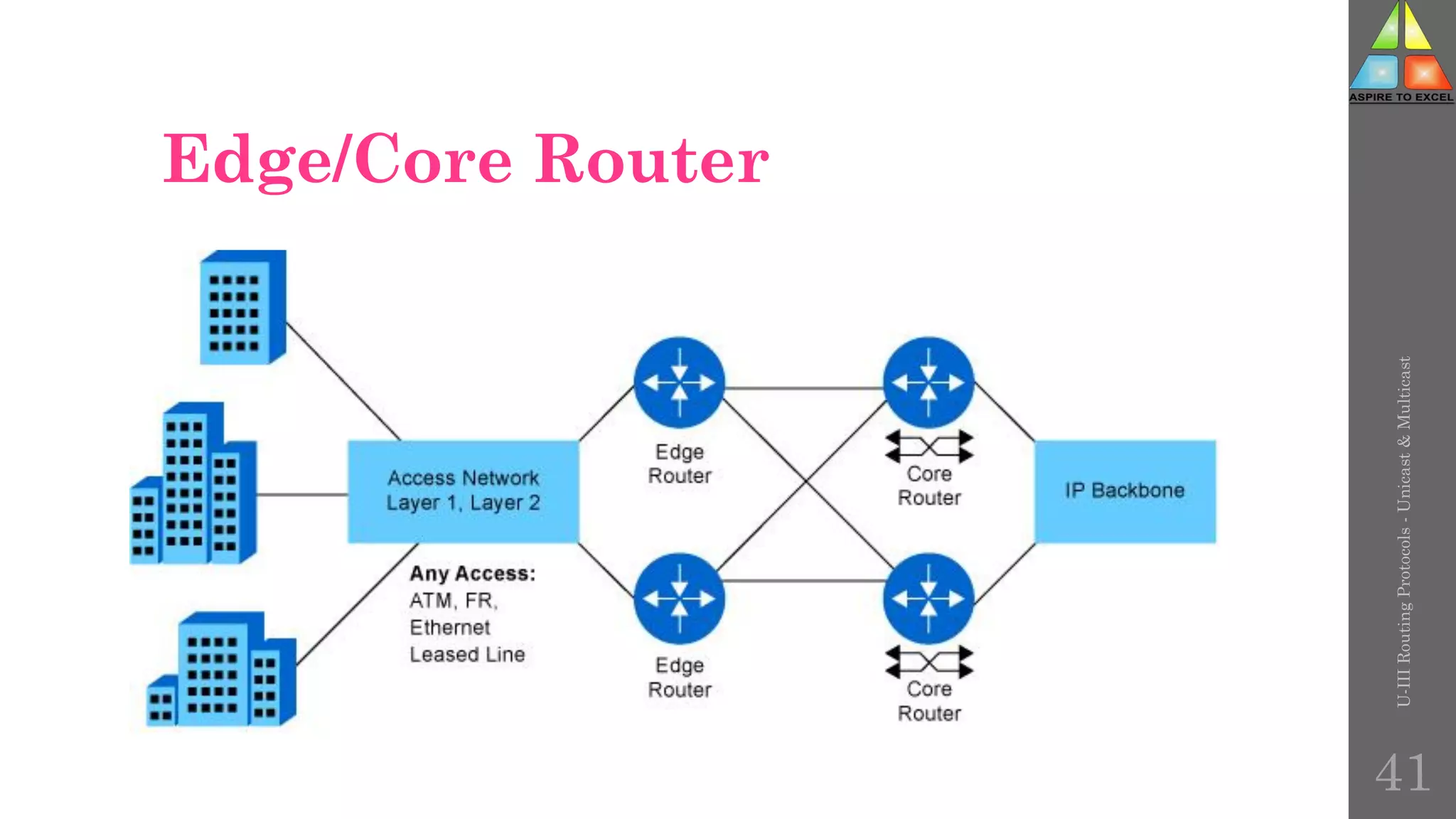
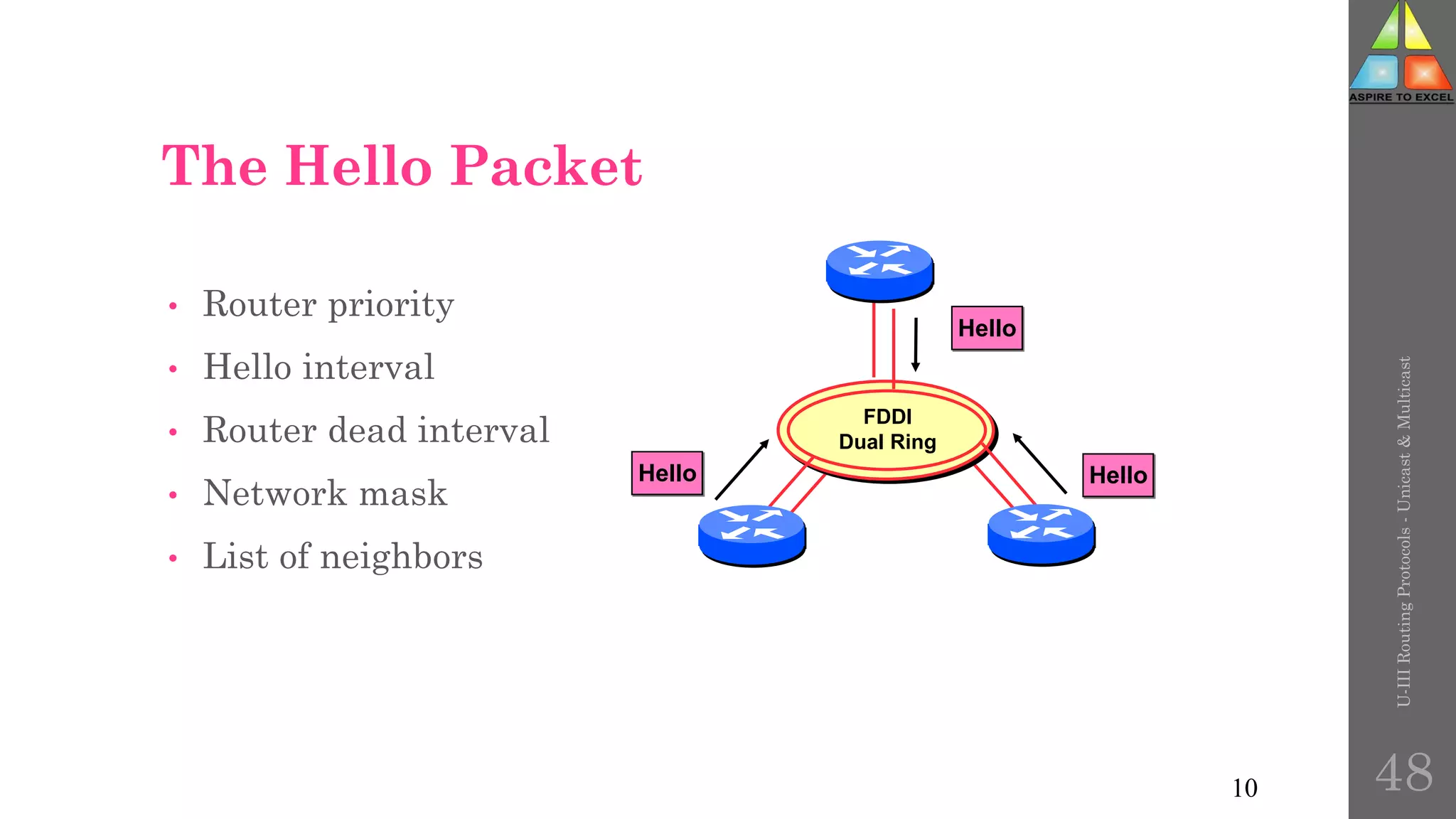
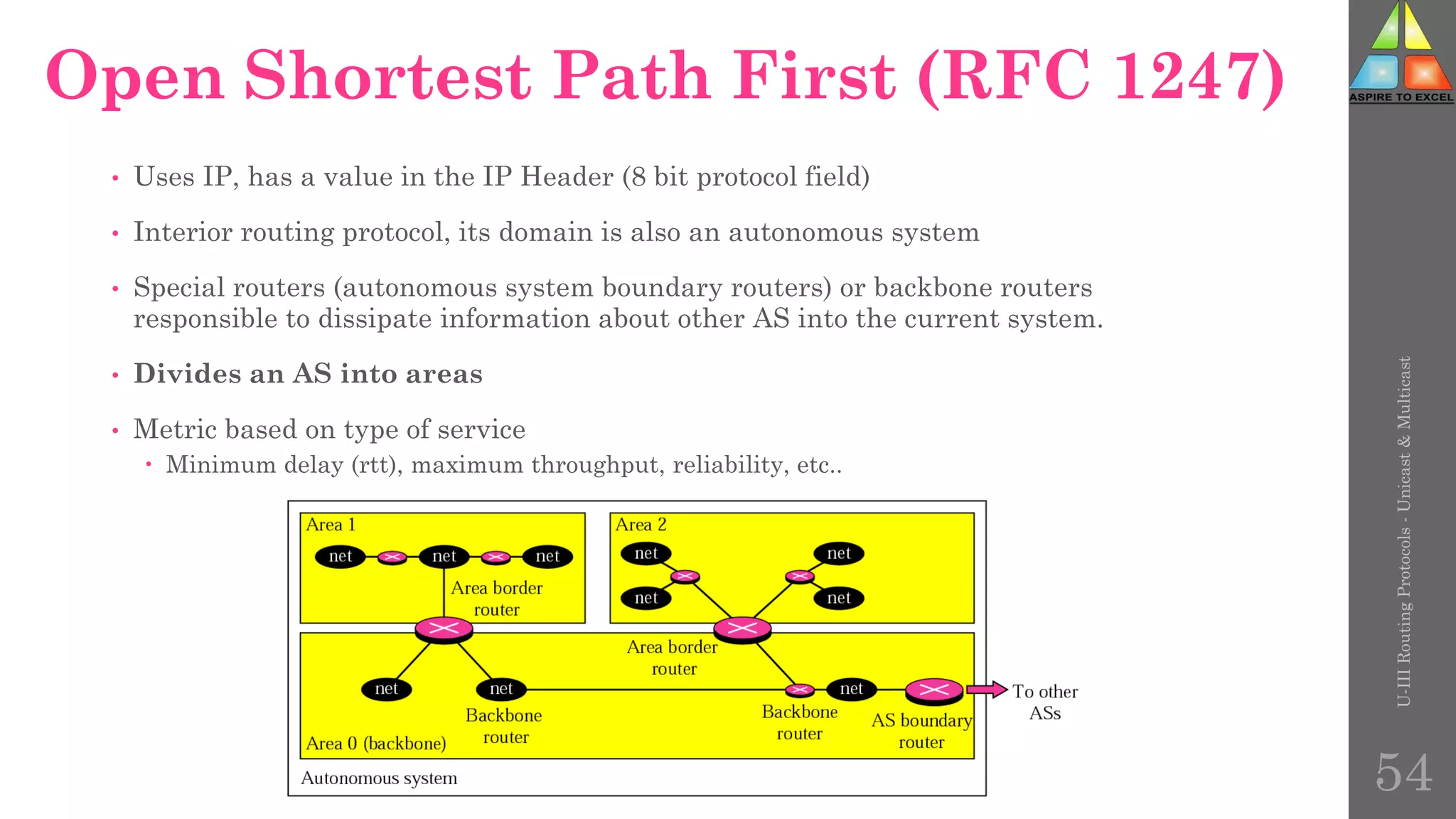
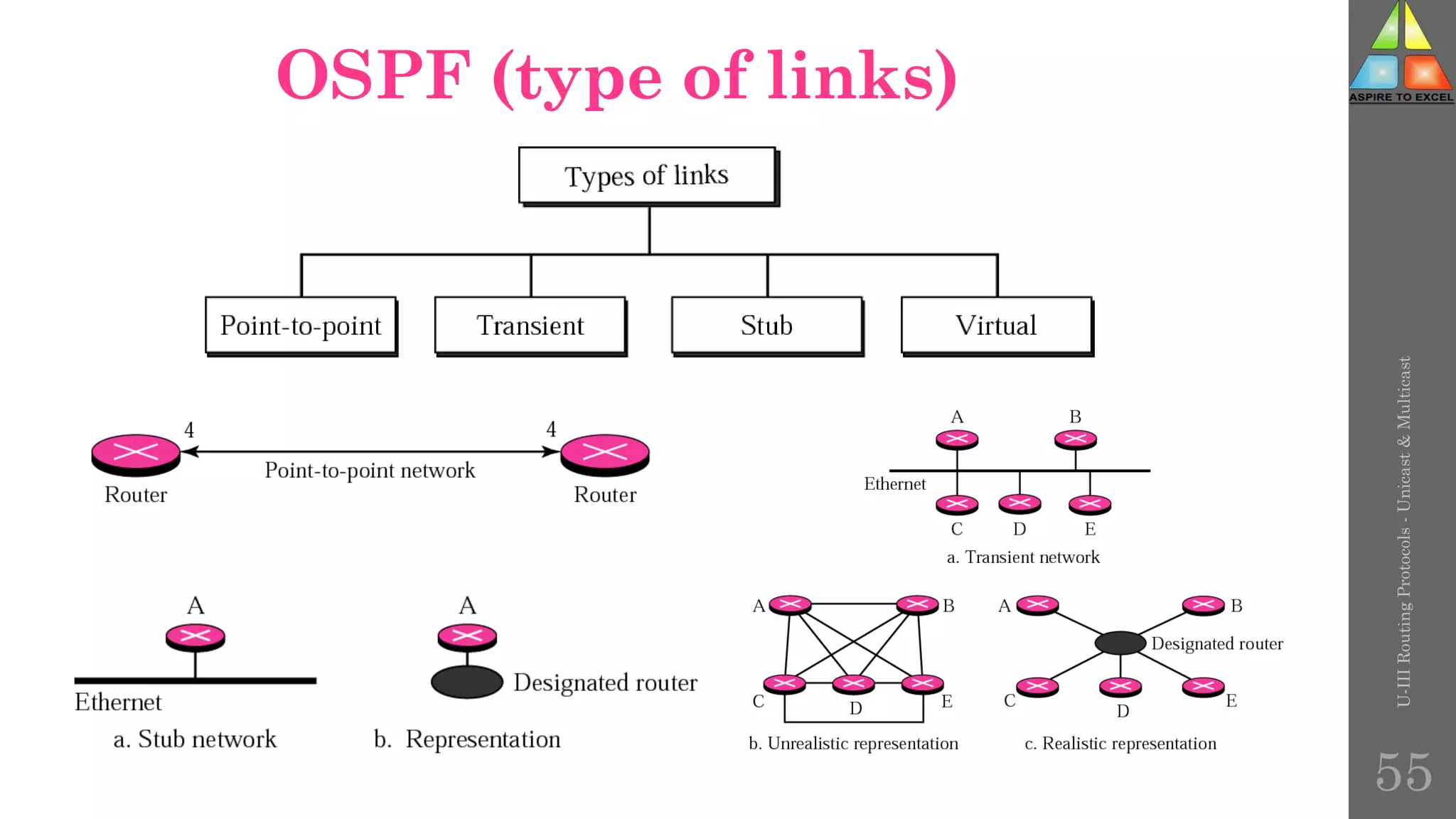
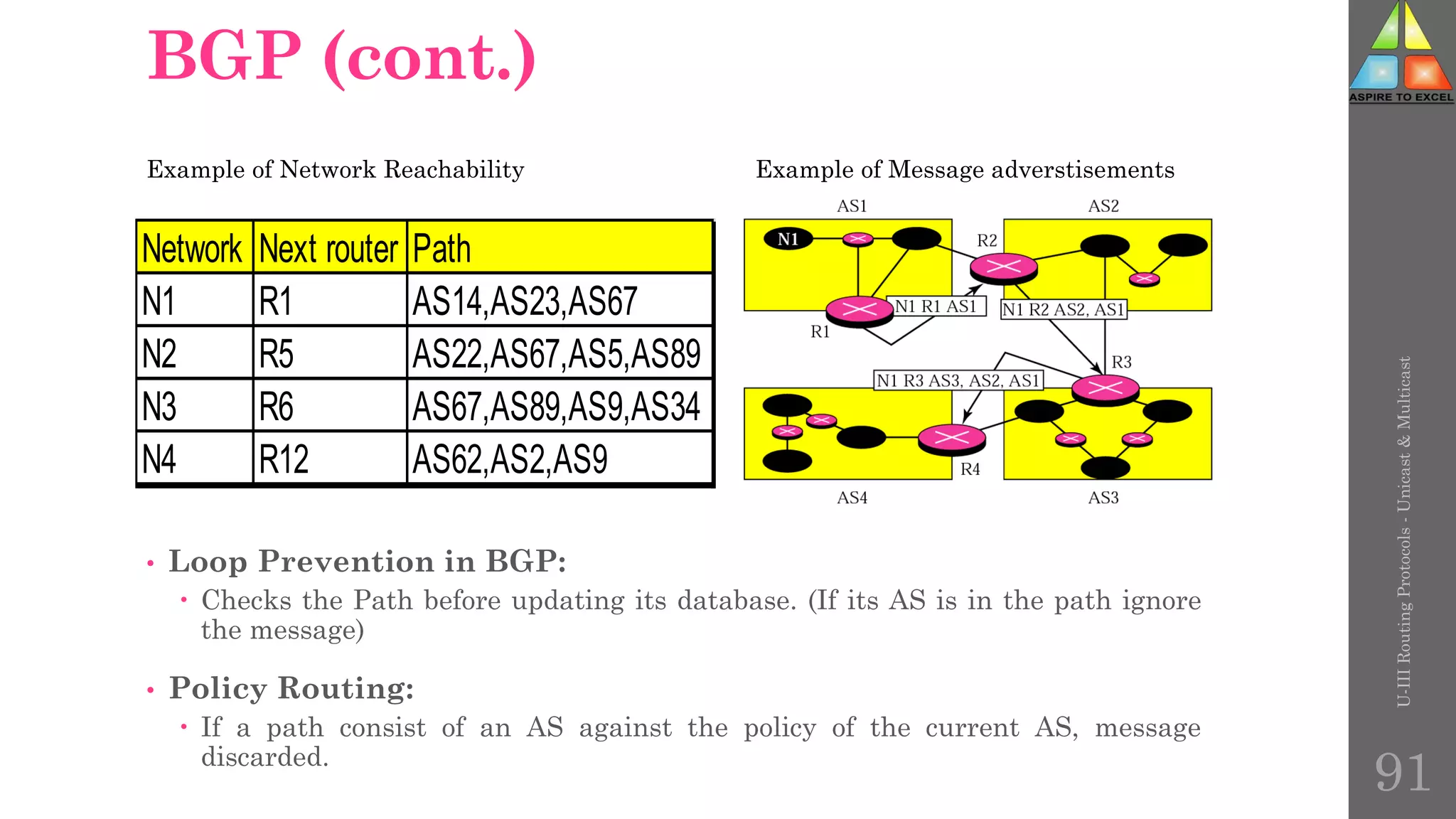
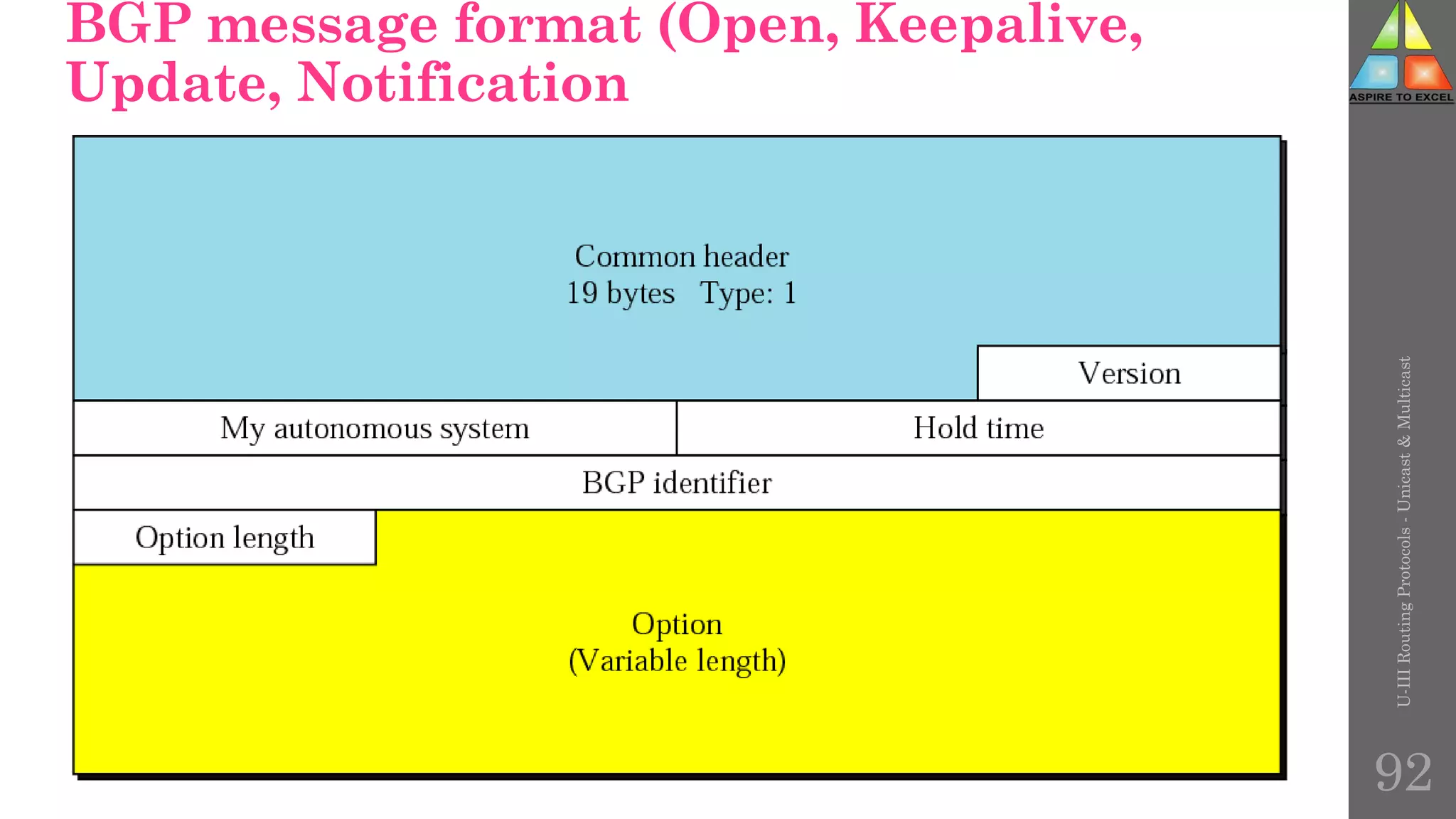
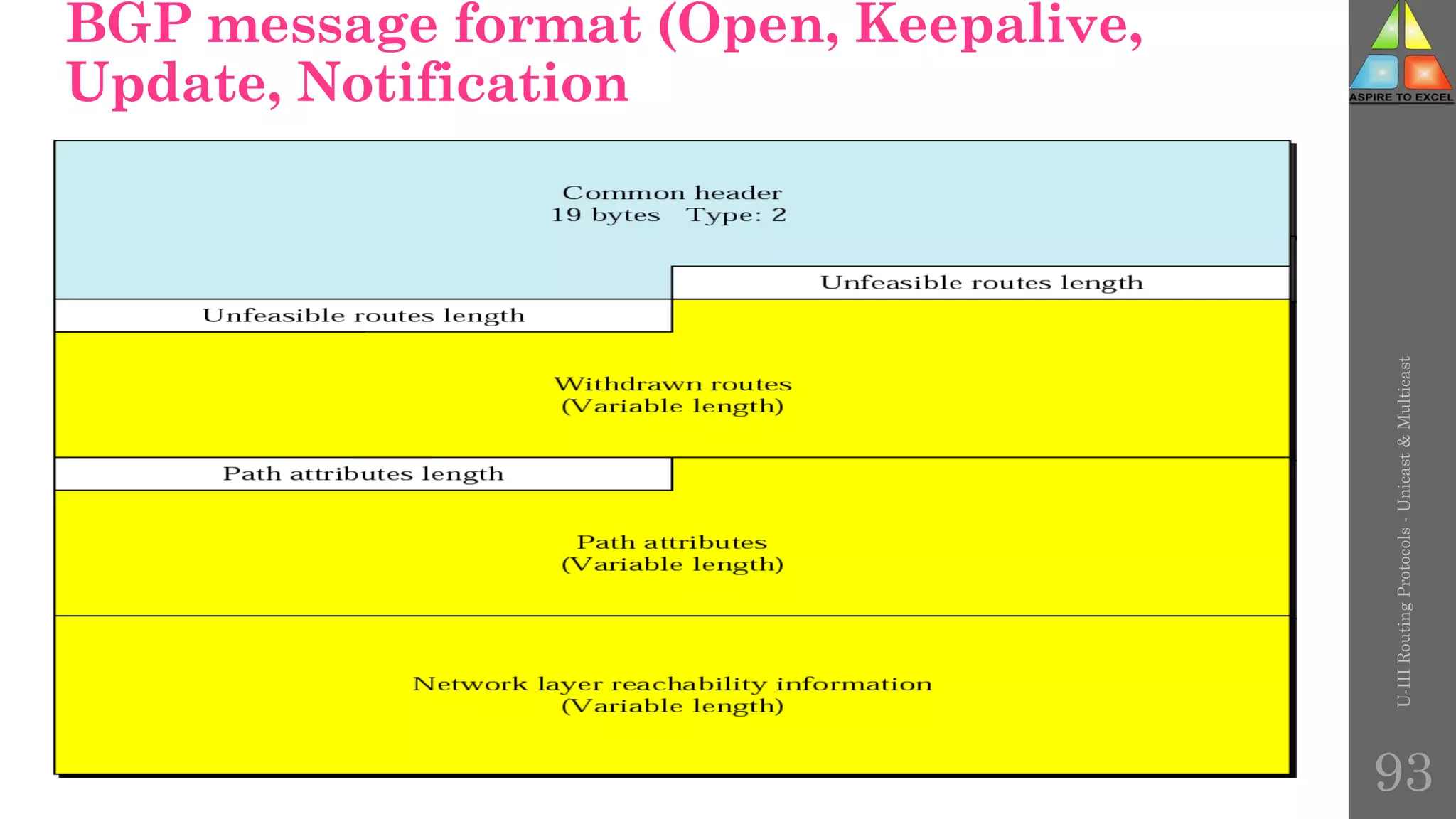
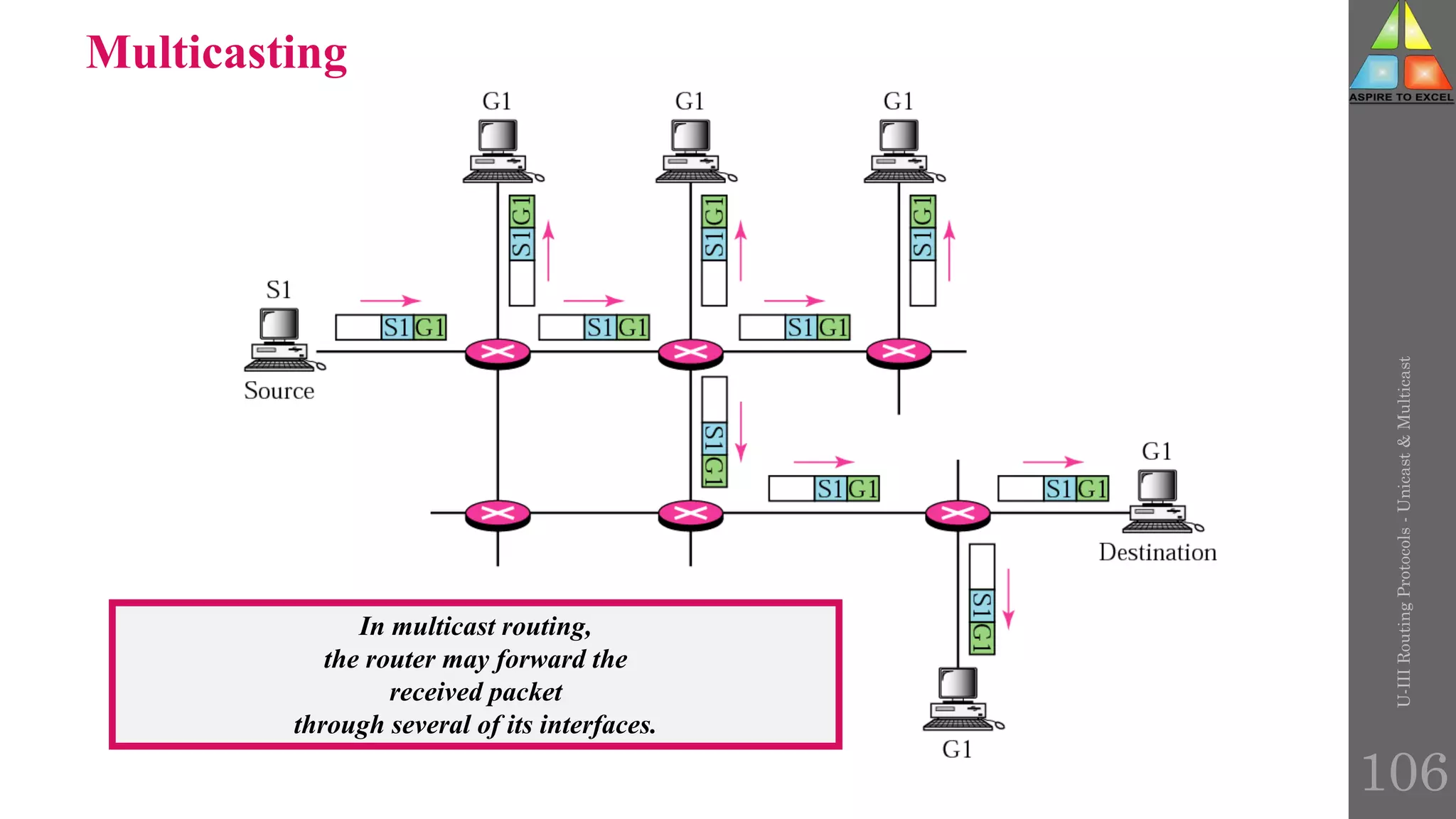
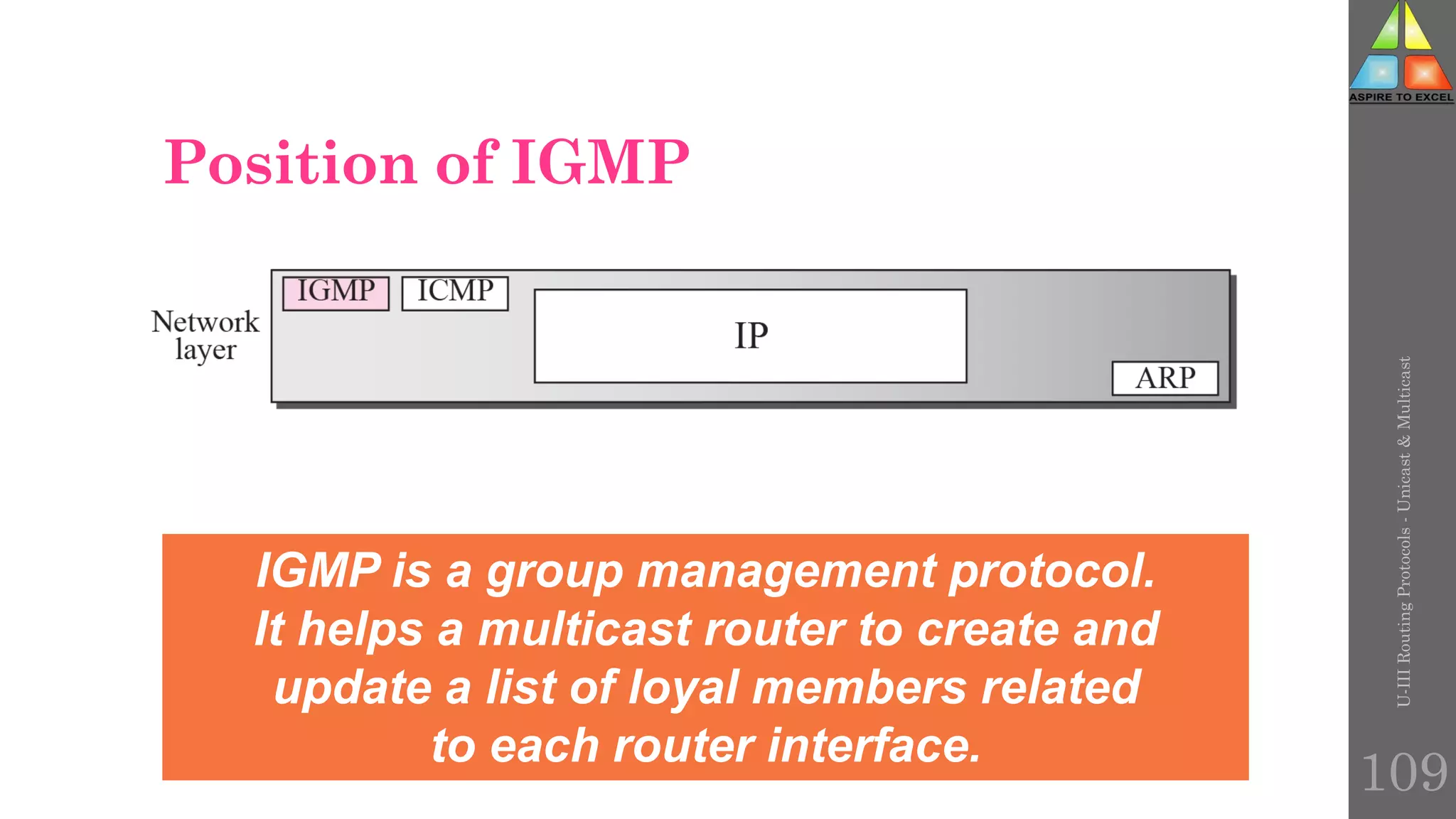
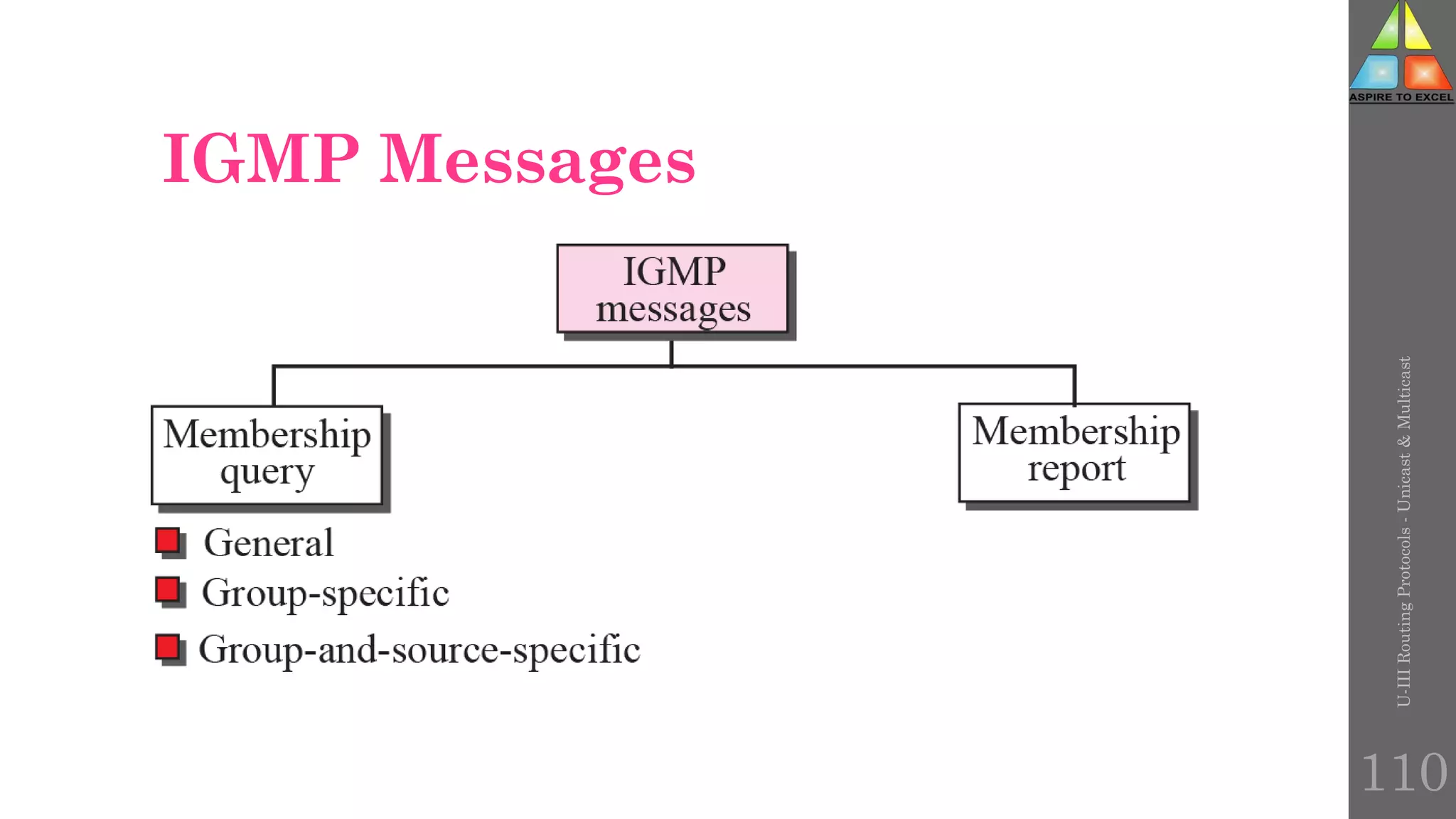
The document discusses routing protocols in networking, focusing on unicast and multicast mechanisms, and their implementation through distance vector and link state routing algorithms. It highlights the significance of protocols like RIP and OSPF, detailing their operational characteristics, advantages, and disadvantages, as well as issues like count-to-infinity and convergence times. Furthermore, it outlines routing procedures, message formats, and the importance of secure routing practices.




















![Functional Requirements(contd.)
• Routing Hierarchy
support large routing domains
• Separate internal and external routes
• Support of flexible subnetting schemes
route to arbitrary [address, mask] combinations using VLSMs (Variable
Length Subnet Mask)
• Security
• Type of Service Routing
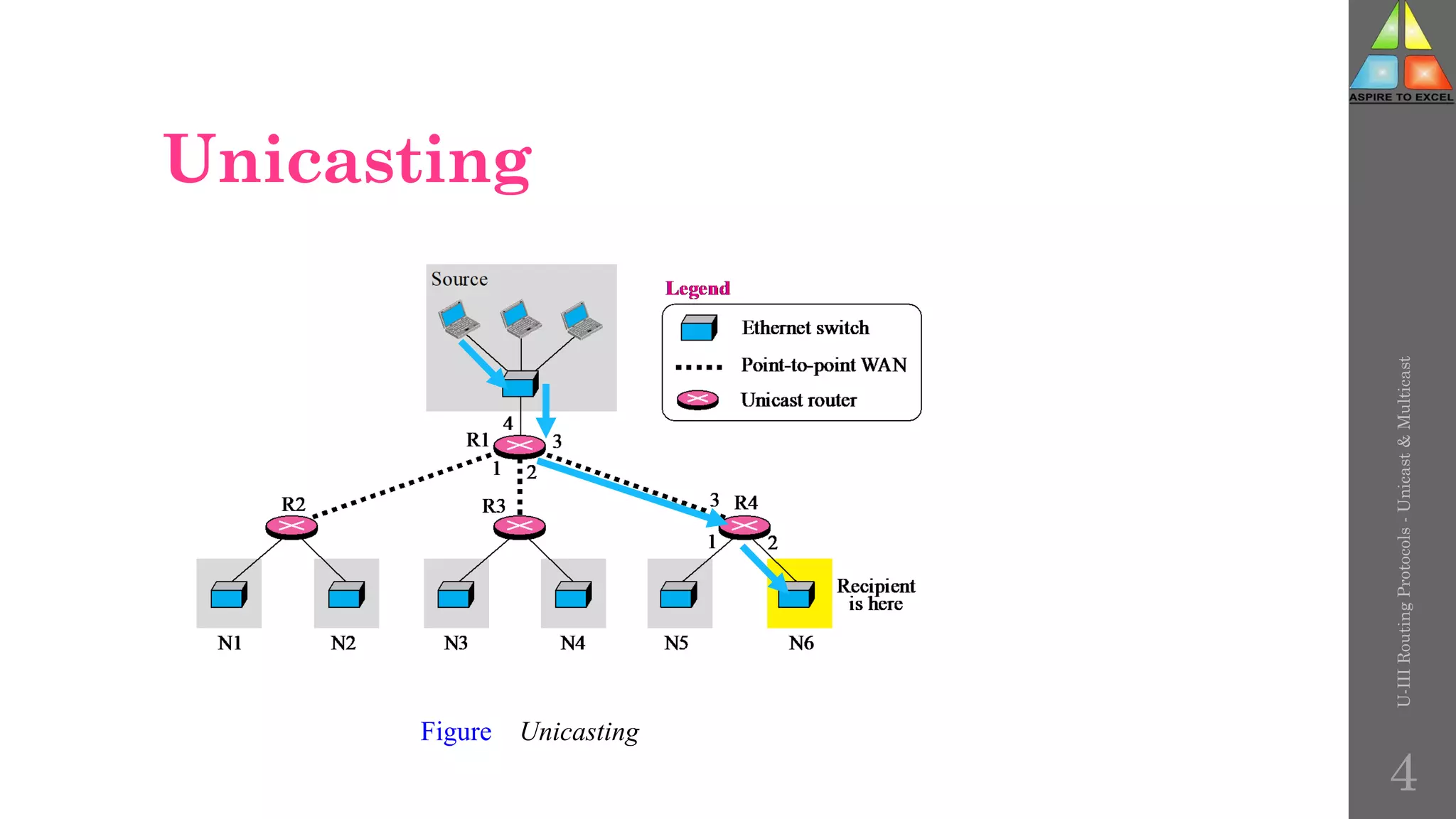
U-III
Routing
Protocols
-
Unicast
&
Multicast
46](https://image.slidesharecdn.com/unit-3routing-230429054921-86531a55/75/Routing-Protocols-46-2048.jpg)






















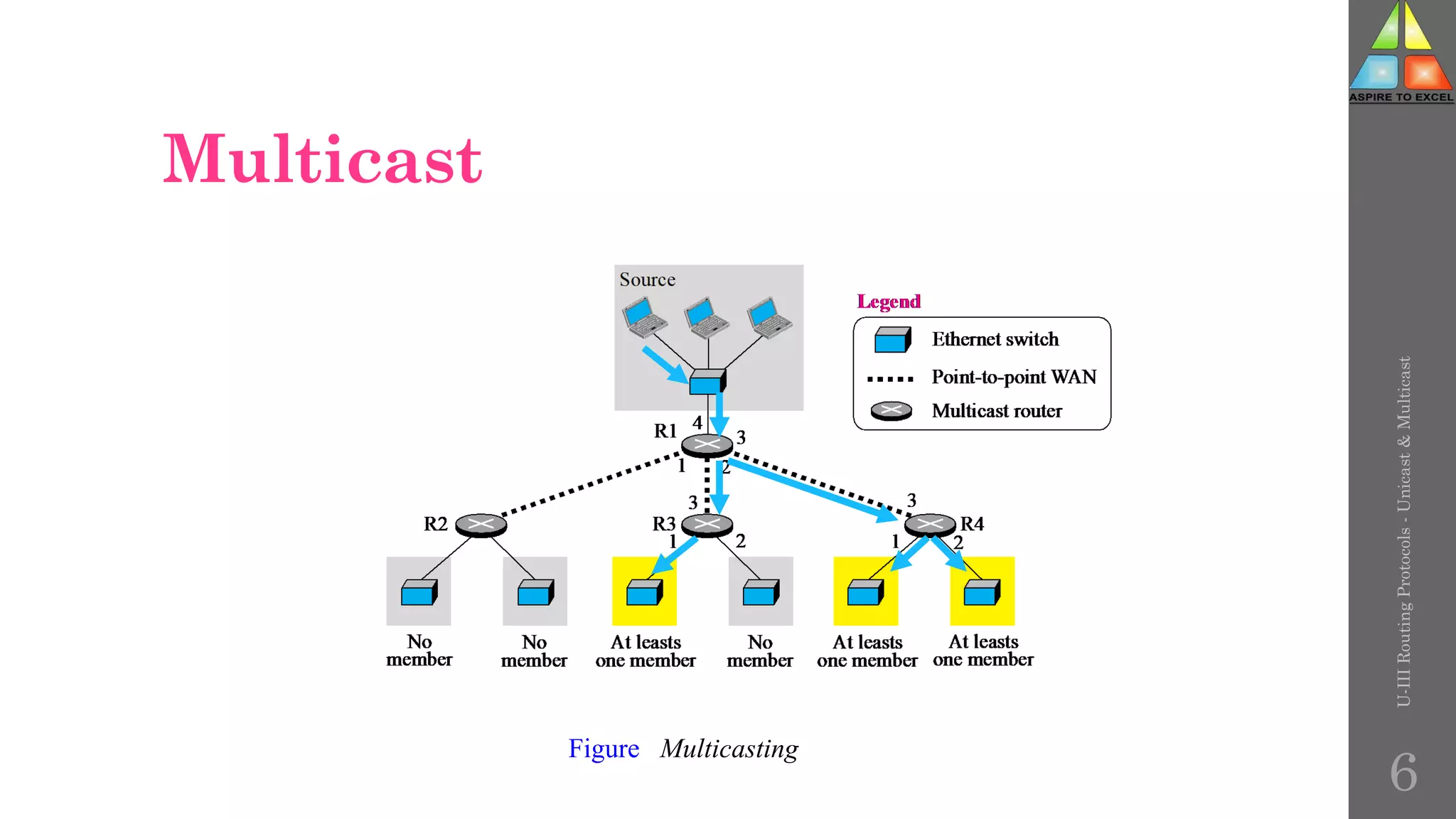
![Membership query message format
U-III
Routing
Protocols
-
Unicast
&
Multicast
111
Field Definition
Type = 0x11 IGMP query.
Max resp. code Maximum response code (in seconds). This field specifies the maximum time allowed before sending a responding
report.
Group address Multicast group address. This address is 0.0.0.0 for general queries.
S S flag. This flag indicates that processing by routers is being suppressed.
QRV Querier Robustness Value. This value affects timers and the number of retries.
QQIC Query Interval Code of the Querier (in seconds). This field specifies the query interval used by the querier.
No. of sources [N] Number of sources present in the query. This number is nonzero for a group-and-source query.
Source address [1...N] Address of the source(s).](https://image.slidesharecdn.com/unit-3routing-230429054921-86531a55/75/Routing-Protocols-111-2048.jpg)