1. Identity fraud involves someone obtaining and using another person's personal data like their Social Security number, bank account information, or other identifying details without permission in order to steal money or commit other fraud.
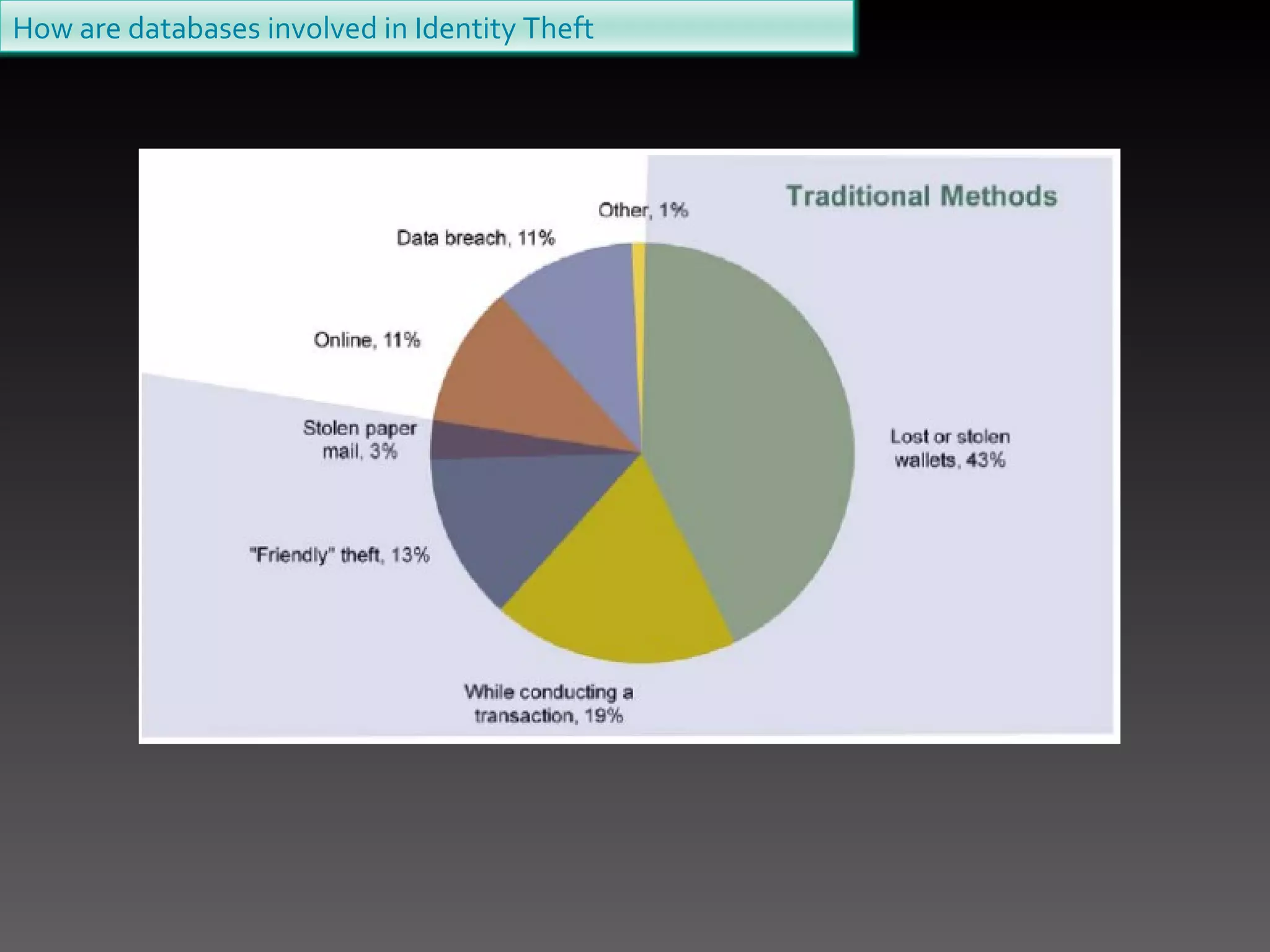
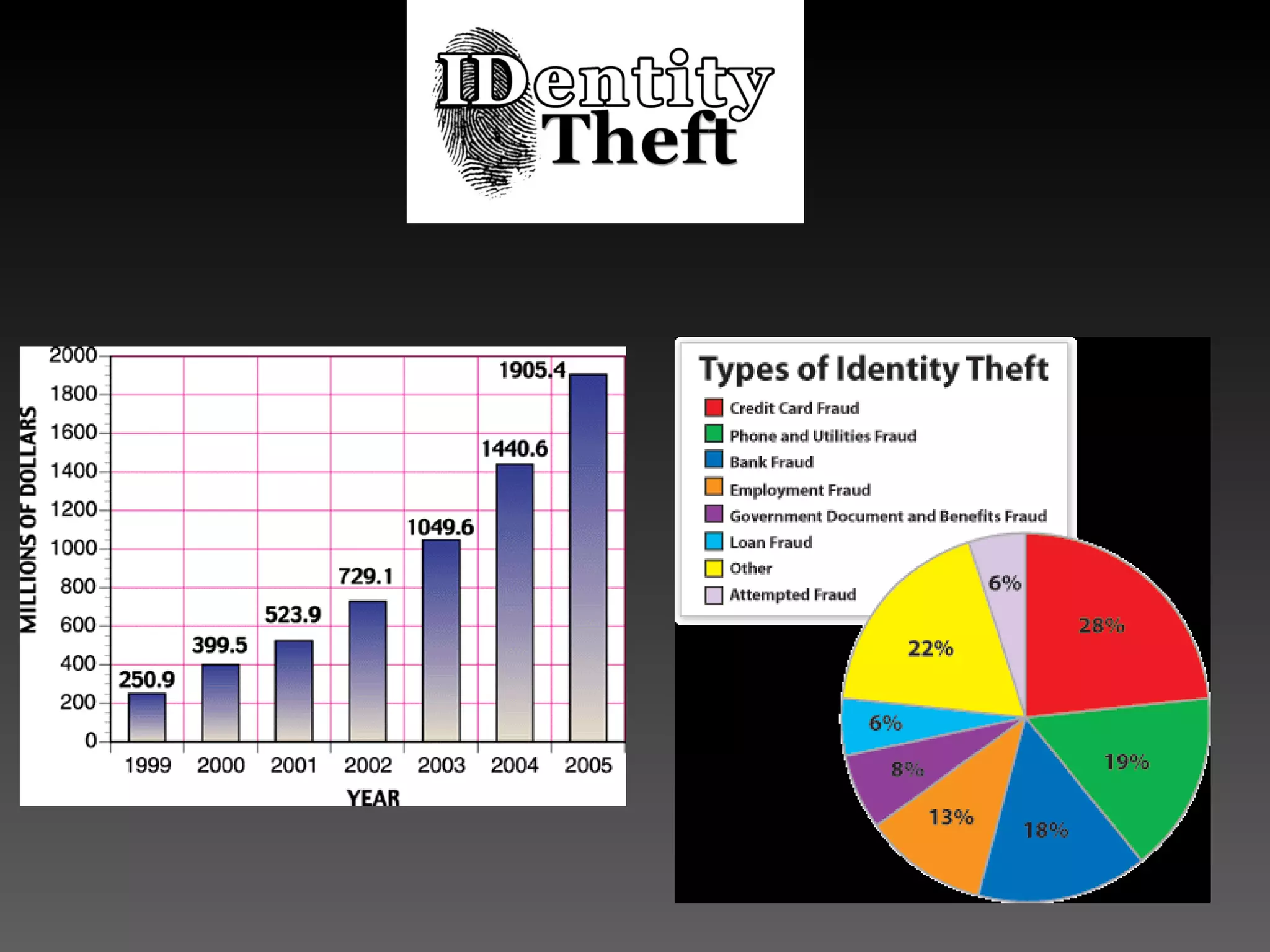
2. Criminals can access personal information stored in databases by hacking, using malware, or researching public records. They use stolen identity details to make purchases, withdrawals, open new accounts, obtain medical services, or apply for loans under the victim's name.
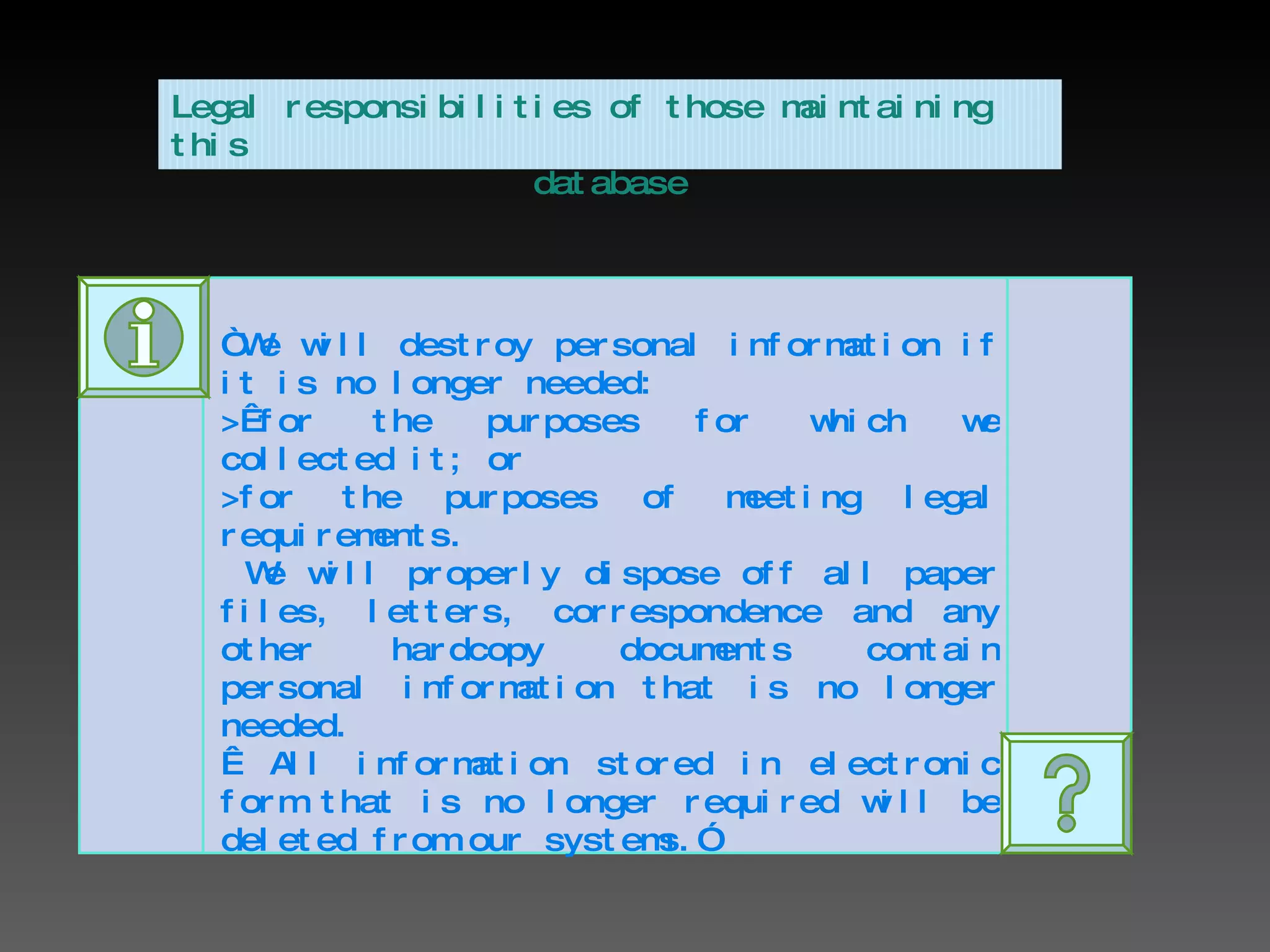
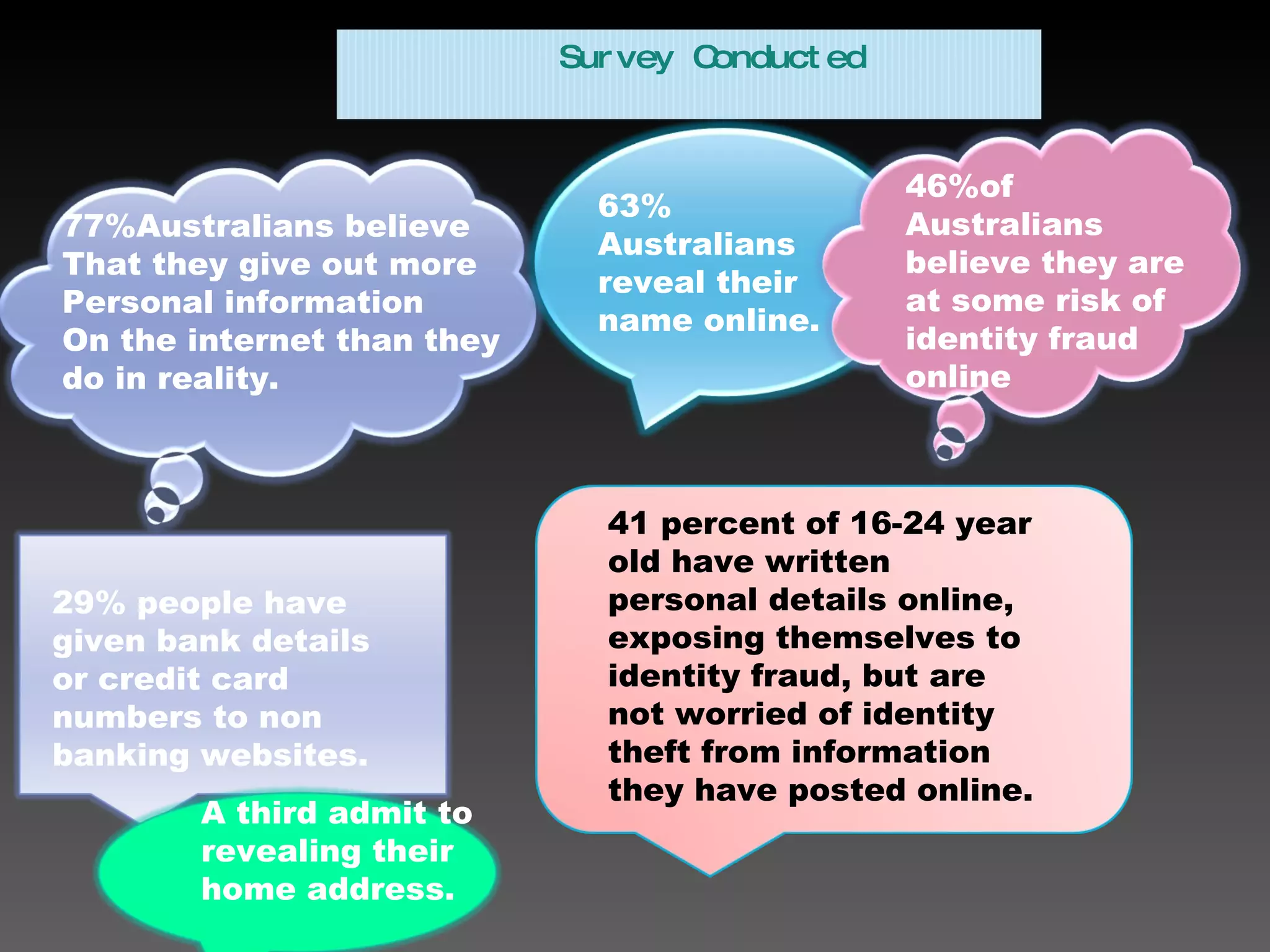
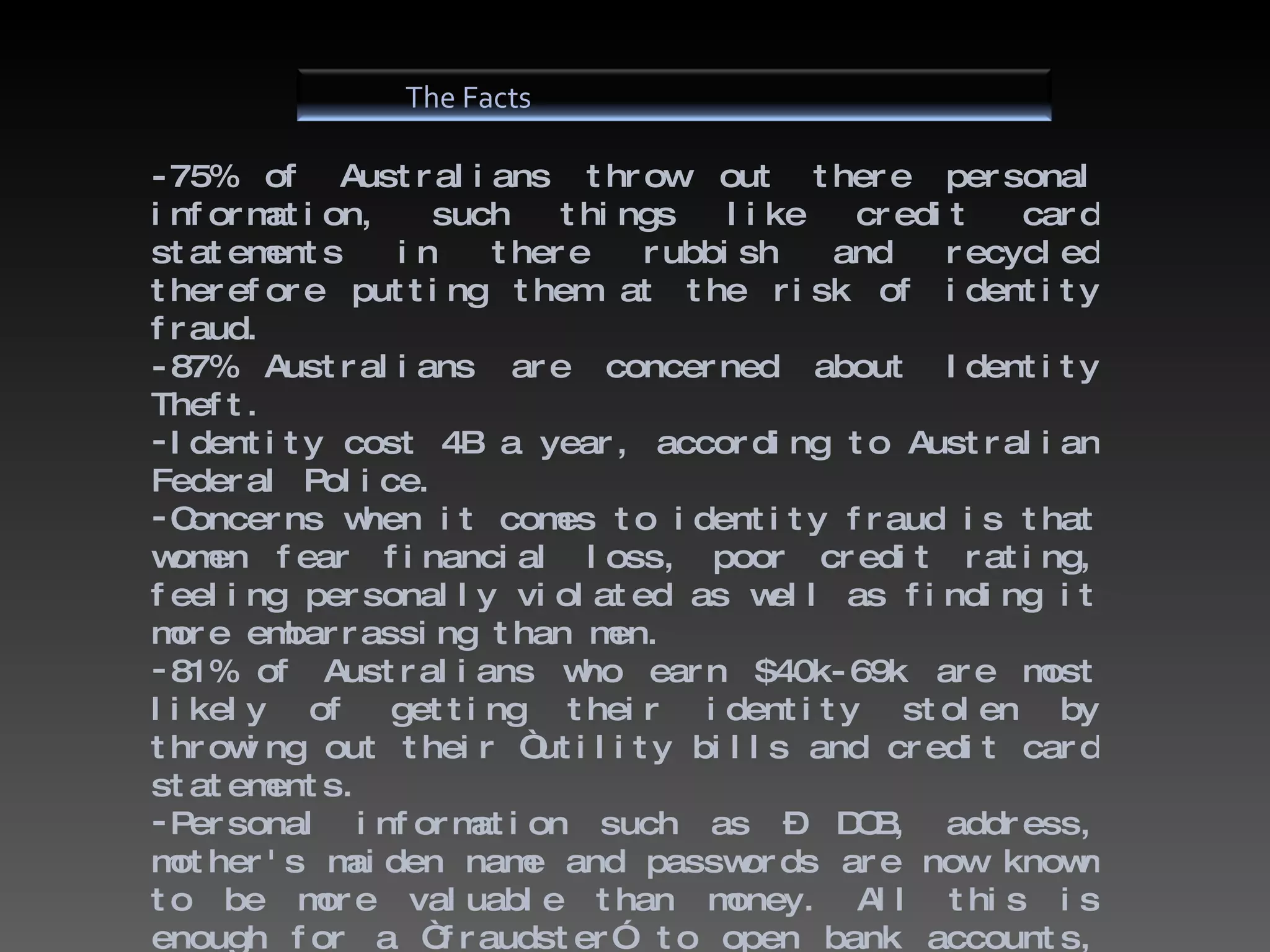
3. Both companies storing personal data and individuals have responsibilities to protect information. Companies must legally secure data and not share it without consent, while individuals should be careful what they reveal online or throw away.