This document provides an overview of key concepts related to the internet and web development, including:
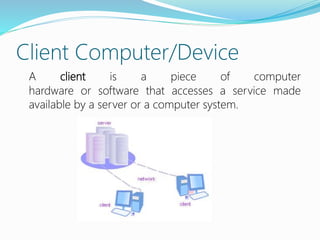
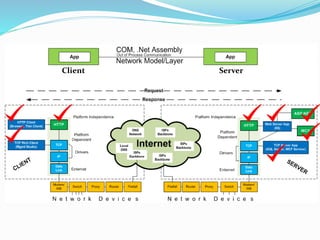
- The difference between client-server communication models like thin clients (browsers) versus thick clients (desktop apps).
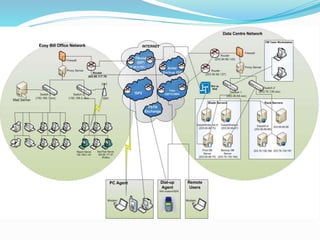
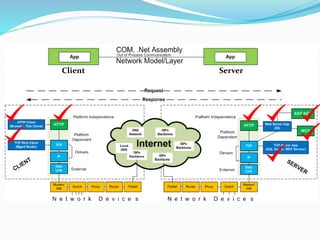
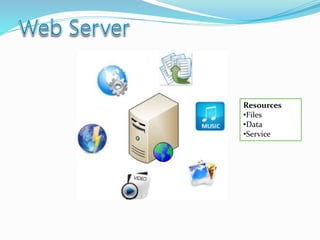
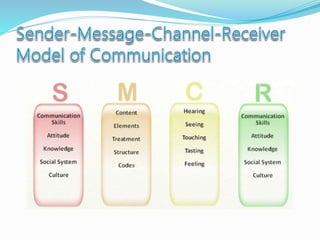
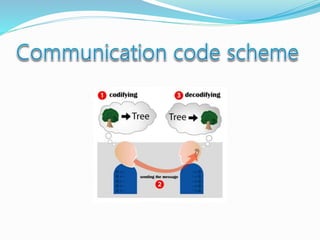
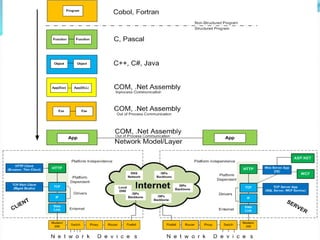
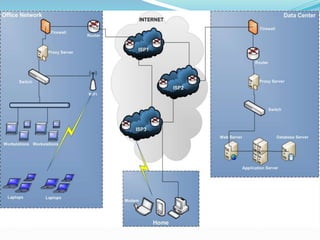
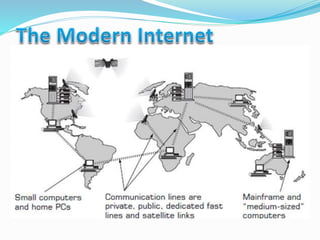
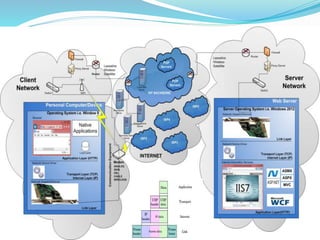
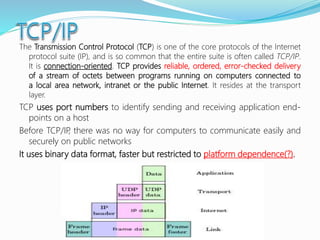
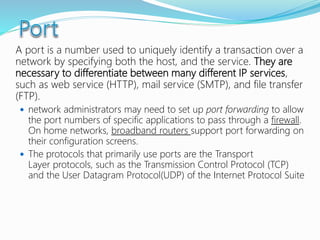
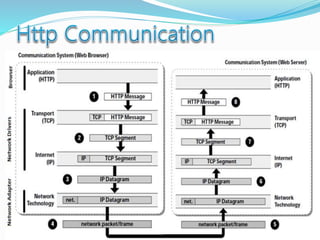
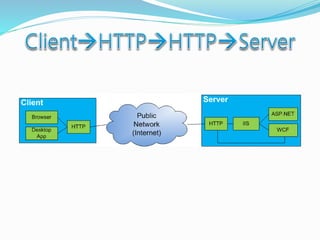
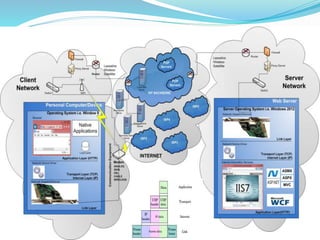
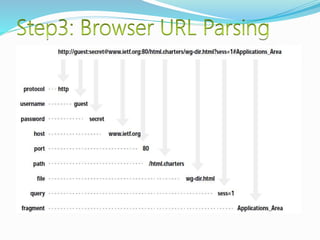
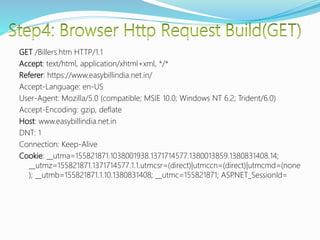
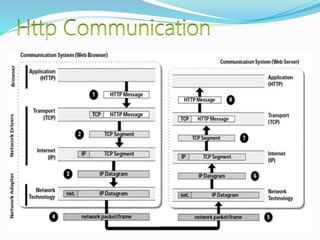
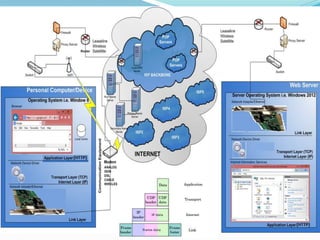
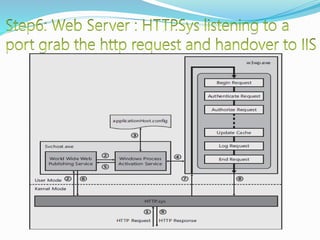
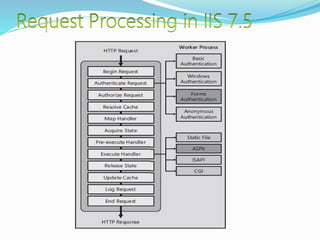
- How communication works between clients and servers over network layers, protocols like HTTP, and network equipment.
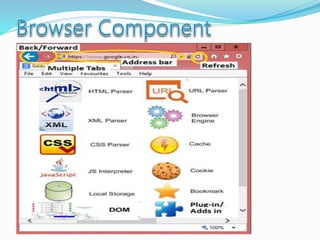
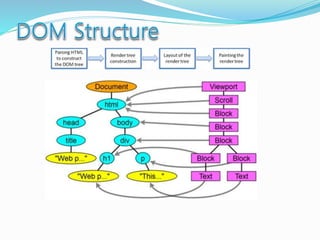
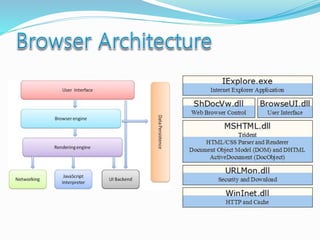
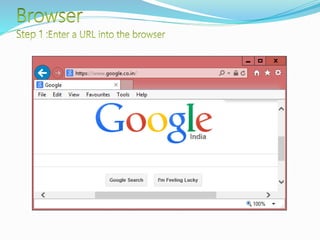
- Key components of web browsers like the user interface, rendering engine, and storage mechanisms.
- The role of plug-ins in enabling customization and extending functionality of applications.
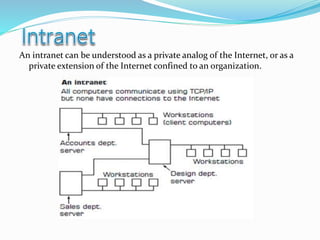
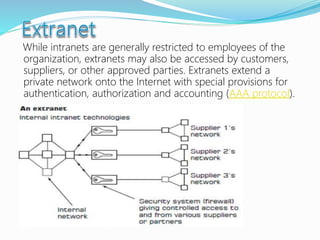
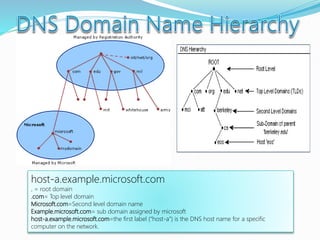
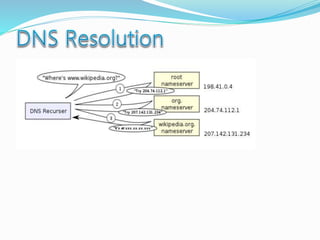
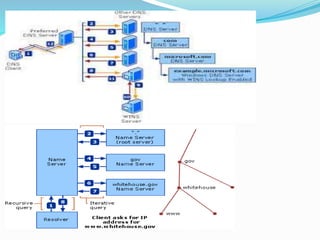
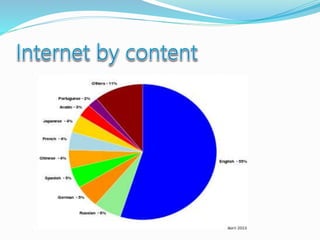
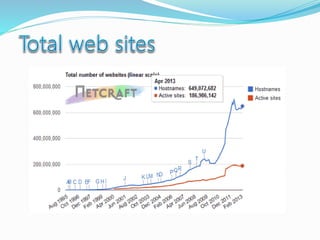
- Definitions of networks like intranets and extranets, and how the global Internet system is structured with domains and DNS.









































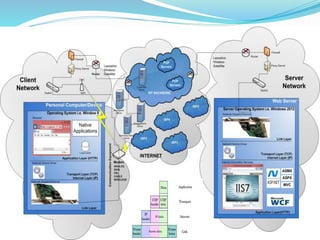




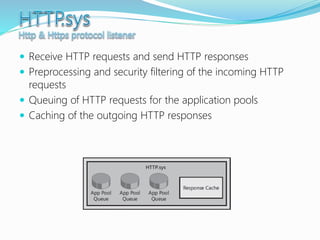
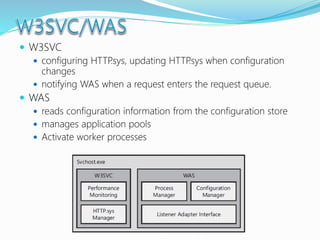
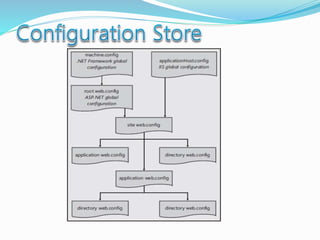
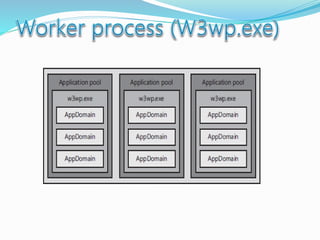
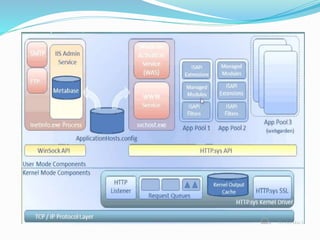
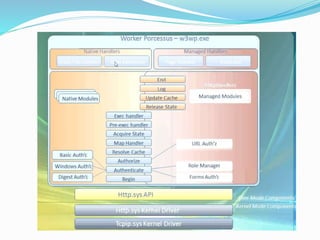

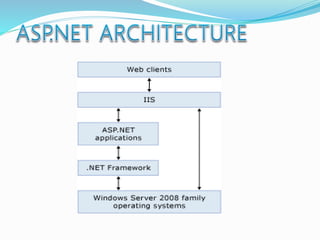
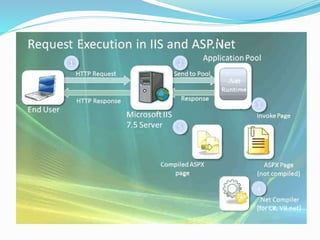





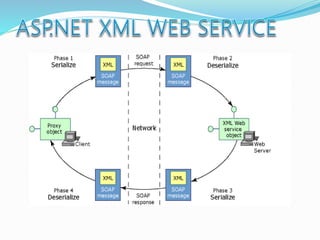


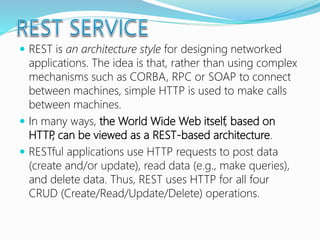

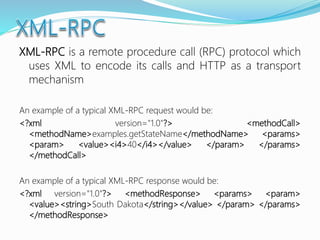


















![The majority of web application attacks occur through cross-site scripting (XSS)
and SQL injection attacks[5] which typically result from flawed coding, and
failure to sanitize input to and output from the web application. These are
ranked in the 2009 CWE/SANS Top 25 Most Dangerous Programming
Errors.[6]According the security vendor Cenzic, the top vulnerabilities in March
2012 include:[7]
Cross Site Scripting, 37%
SQL Injection, 16%
PHP Injection,
Javascript Injection,
Path Disclosure, 5%
Denial of Service, 5%
Code Execution, 4%
Memory Corruption, 4%
Cross Site Request Forgery, 4%
Information Disclosure, 3%
Arbitrary File, 3%
Local File Include, 2%
Remote File Include, 1%
Overflow 1%
Other, 15%](https://image.slidesharecdn.com/howthewebworks-180420075012/85/How-does-the-web-or-internet-work-125-320.jpg)