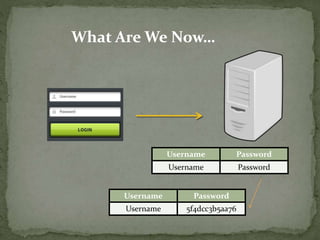
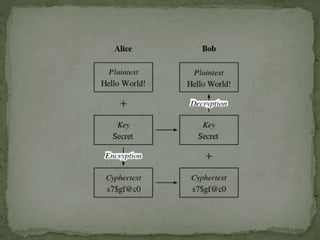
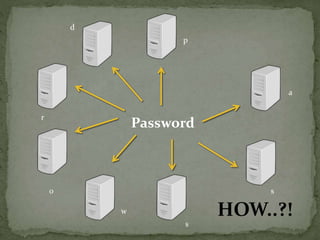
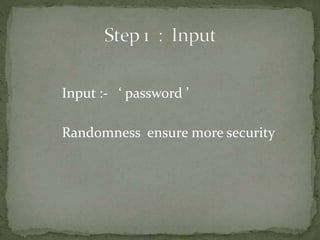
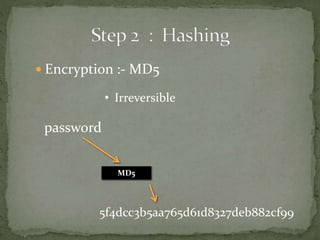
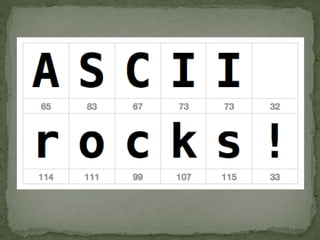
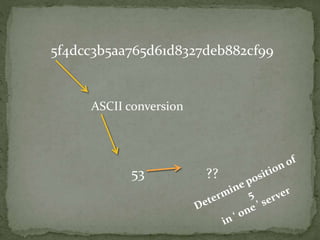
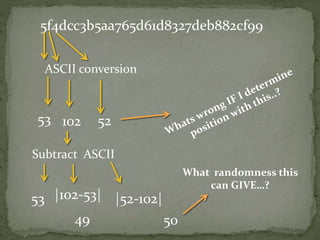
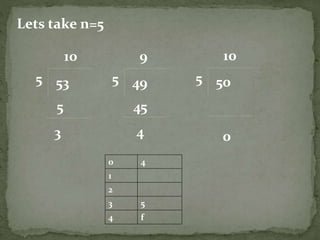
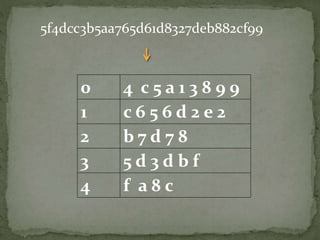
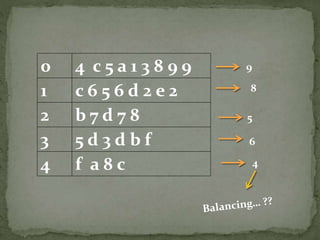
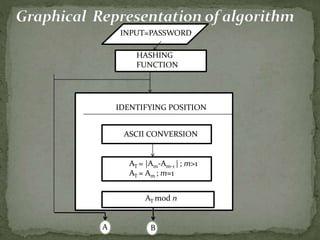
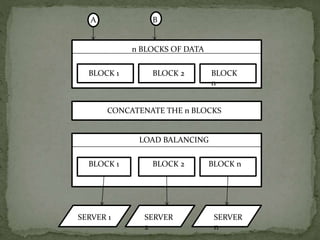
The document outlines a secure password authentication system that incorporates hashing, ASCII conversion, and load balancing across multiple servers to enhance security. It details the process of dividing and storing hashed passwords, ensuring that characters are distributed across several servers without predetermined positions. The proposed system's runtime complexity is discussed, emphasizing that it is primarily influenced by the number of servers, rather than the password length.
















![[1] NIST. Secure Hash Standard, FIPS PUB 180-2, 2002.
[2] A. K. Lenstra. Further Progress in Hashing Cryptanalysis (white paper).
http://cm.bell-labs.com/who/akl/hash.pdf, February 2005.
[3] R. Rivest. The MD5 Message-Digest Algorithm [rfc1321], 1992.
[4] Wang Xiaoyun, Chen Yin ru. Collision Analysis for Every Round Function of the
MD5, 1996.
[5] Wang Xiaoyun. How to Break MD5 and Other Hash Functions, 2005.
[6] Zhao Shaolan, Xing Guobo, Yang Yixian. The Analysis on Amelioration and Security
of MD5, 2005.
[7] L. Dadda, M. Macchetti, and J. Owen. An ASIC design for a high speed
implementation of the hash function SHA-256 (384,512). In ACM Great Lakes
Symposium on VLSI, pages 421–425. ACM, 2004.
[8] L. Dadda, M. Macchetti, and J. Owen. The design of a high speed ASIC unit for the
hash function SHA-256 (384, 512).In DATE 2004, pages 70–75. IEEE Computer
Society, 2004.
[9] R. Lien, T. Grembowski, and K. Gaj. A 1 Gbit/s partially unrolled architecture of
hash functions SHA-1 and SHA-512.In CT-RSA 2004, volume 2964 of LNCS, pages
324–338.Springer, 2004.](https://image.slidesharecdn.com/mltiserver-191125030629/85/High-Secure-Password-Authentication-System-32-320.jpg)

