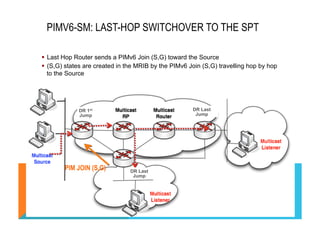
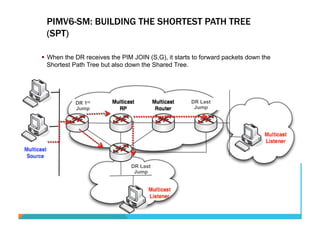
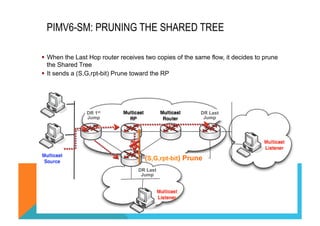
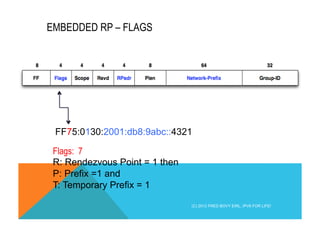
This document provides an overview and agenda for a course on Introduction to IPv6 for Service Providers. The course covers IPv6 essentials such as addressing, operations, applications/services, routing protocols, and transition strategies. It discusses the rationale for adopting IPv6 including the depletion of IPv4 addresses and the need to support the growing number of internet-connected devices. The document outlines some of the key limitations of IPv4 like fragmentation and the issues with long-term reliance on Network Address Translation (NAT) to overcome the address space depletion.






![TYPOGRAPHIC CONVENTIONS
Convention Type of Information
Italic Font
Book titles.
Word or characters that require special attention.
Variable names or placeholders for information you
must supply, for example:
Enter the following command:
ifstat [-z] {-a interface}
Interface is the name of the interface for which you
want to view statistics.
Monospaced font!
Command names, daemon names, and option names.
Information displayed on the system console or other
computer monitors.
The contents of files.
Bold monospaced font!
Words or characters you type, for example:
Enter the following command:
options httpd.enable on!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-7-320.jpg)





















![REPRESENTATION (RFC 4291)
§ X:X:X:X:X:X:X:X
§ X is a Hexa field on 16 bits
§ Consecutive 0 are represented by :: but this can be used only once in the
address
§ 2000:1::0102:1234:4222
§ FF01:0:0:0:0:0:0:1 or FF01::1
§ 0:0:0:0:0:0:0:0 or ::
§ In an URL, the address is surrounded by [ ]
§ http://[2001:1:4::11]:8080/index.html](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-32-320.jpg)












![sa13-72c(config-if)#do show ipv6
int gig0/2
GigabitEthernet0/2 is up, line
protocol is up
§ IPv6 is enabled, link-local address is
FE80::20B:60FF:FEB4:9C1A
No Virtual link-local address(es):
§ Stateless address autoconfig enabled
Global unicast address(es):
§ 2000:1::20B:60FF:FEB4:9C1A, subnet is
2000:1::/64 [EUI/CAL/PRE]
§ Valid lifetime 2591911 preferred lifetime
604711
Hosts use stateless autoconfig for
addresses
Joined group address(es):
§ FF02::1
§ FF02::2
§ FF02::1:FFB4:9C1A
§ MTU is 1500 bytes
§ ICMP error messages limited to one every 100 milliseconds
§ ICMP redirects are enabled
§ ICMP unreachables are sent
§ ND DAD is enabled, number of DAD attempts: 1
§ ND reachable time is 30000 milliseconds (using 23319)
§ ND advertised reachable time is 0 (unspecified)
§ ND advertised retransmit interval is 0 (unspecified)
§ ND router advertisements are sent every 200 seconds
§ ND router advertisements live for 1800 seconds
§ ND advertised default router preference is Medium
CISCO IPV6 INTERFACE
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-51-320.jpg)









![IPV6 HEADER
Ethernet II, Src: ca:02:42:76:00:08 (ca:02:42:76:00:08), Dst: IPv6mcast_00:01:00:02
(33:33:00:01:00:02)
Destination: IPv6mcast_00:01:00:02 (33:33:00:01:00:02)
Source: ca:02:42:76:00:08 (ca:02:42:76:00:08)
Type: IPv6 (0x86dd)
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6" possible: 6]
.... 1110 0000 .... .... .... .... .... = Traffic class: 0x000000e0
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel: 0x00000000
Payload length: 56
Next header: UDP (0x11)
Hop limit: 255
Source: fe80::38b1:e73c:c0f0:4442 (fe80::38b1:e73c:c0f0:4442)
Destination: ff02::1:2 (ff02::1:2)
User Datagram Protocol, Src Port: dhcpv6-client (546), Dst Port: dhcpv6-server (547)
Source port: dhcpv6-client (546)
Destination port: dhcpv6-server (547)
Length: 56
Checksum: 0x86f0 [validation disabled]
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-71-320.jpg)












![ICMPV6 INFORMATION MESSAGE
§ pingv6
§ Echo Request
§ Echo Reply
sa13-72c>ping 2000:1::100!
Type escape sequence to abort.!
Sending 5, 100-byte ICMP Echos to 2000:1::100, timeout is 2 seconds:!
!!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/4 ms!
sa13-72c>!
Apr 21 05:56:54: ICMPv6: Sent echo request, Src=2000:1::20B:60FF:FEB4:9C1A, Dst=2000:1::100!
Apr 21 05:56:54: ICMPv6: Received echo reply, Src=2000:1::100, Dst=2000:1::20B:60FF:FEB4:9C1A!
Apr 21 05:56:54: ICMPv6: Sent echo request, Src=2000:1::20B:60FF:FEB4:9C1A, Dst=2000:1::100!
Apr 21 05:56:54: ICMPv6: Received echo reply, Src=2000:1::100, Dst=2000:1::20B:60FF:FEB4:9C1A!
Apr 21 05:56:54: ICMPv6: Sent echo request, Src=2000:1::20B:60FF:FEB4:9C1A, Dst=2000:1::100!
Apr 21 05:56:54: ICMPv6: Received echo reply, Src=2000:1::100, Dst=2000:1::20B:60FF:FEB4:9C1A!
Apr 21 05:56:54: ICMPv6: Sent echo request, Src=2000:1::20B:60FF:FEB4:9C1A, Dst=2000:1::100!
Apr 21 05:56:54: ICMPv6: Received echo reply, Src=2000:1::100, Dst=2000:1::20B:60FF:FEB4:9C1A!
[SNIP]!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-87-320.jpg)







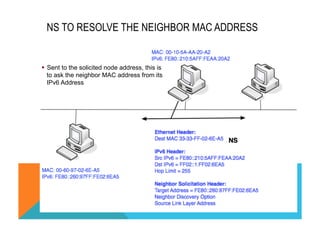


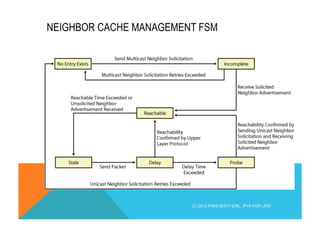




![NEIGHBOR SOLICITATION CAPTURE
§ The Source Layer Address is provided to avoid the request in the other
direction
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6" possible: 6]
.... 1110 0000 .... .... .... .... .... = Traffic class: 0x000000e0
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel: 0x00000000
Payload length: 400
Next header: ICMPv6 (0x3a)
Hop limit: 255
Source: fe80::2027:9779:3775:5cf8 (fe80::2027:9779:3775:5cf8)
Destination: fe80::38b1:e73c:c0f0:4442 (fe80::38b1:e73c:c0f0:4442)
Internet Control Message Protocol v6
Type: 135 (Neighbor solicitation)
Code: 0
Checksum: 0x64e3 [correct]
Target: fe80::38b1:e73c:c0f0:4442 (fe80::38b1:e73c:c0f0:4442)
ICMPv6 Option (Source link-layer address)
Type: Source link-layer address (1)
Length: 8
Link-layer address: ca:03:42:76:00:08
SNIP
The Source Layer Address is
provided to avoid the request
in the other direction](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-106-320.jpg)






![RA CAPTURE
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6"
possible: 6]
.... 0000 0000 .... .... .... .... .... = Traffic class: 0x00000000
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel:
0x00000000
Payload length: 104
Next header: ICMPv6 (0x3a)
Hop limit: 255
Source: fe80::207:cbff:fe3e:b6b3
(fe80::207:cbff:fe3e:b6b3)
Destination: ff02::1 (ff02::1)
Internet Control Message Protocol v6
Type: 134 (Router advertisement)
Code: 0
Checksum: 0xf74b [correct]
Cur hop limit: 64
Flags: 0x00
Router lifetime: 1800
Reachable time: 0
Retrans timer: 0
ICMPv6 Option (Prefix information)
Type: Prefix information (3)
Length: 32
Prefix length: 64
Flags: 0xc0
Valid lifetime: 86400
Preferred lifetime: 86400
Prefix: 2a01:e35:2f26:d340::
ICMPv6 Option (Recursive DNS Server)
Type: Recursive DNS Server (25)
Prefix
Length: 40
Reserved
DNS Servers Address
Lifetime: 600
Recursive DNS Servers: dns3.proxad.net (2a01:e00::2)
Recursive DNS Servers: dns2.proxad.net (2a01:e00::1)
ICMPv6 Option (MTU)
Type: MTU (5)
Length: 8
MTU: 1480
ICMPv6 Option (Source link-layer address)
Type: Source link-layer address (1)
Length: 8
Link-layer address: 00:07:cb:3e:b6:b3
Source
MAC @
MTU
All node link-local
address
Router
Lifetime
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-116-320.jpg)
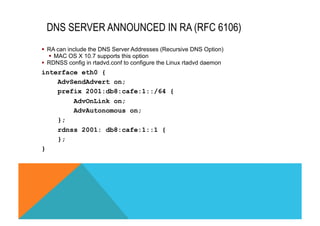


![ALU 7750 RA CONFIGURATION
Prefix
Syntax [no] prefix [ipv6-prefix/prefix-length]
Context config>router>router-advert>if
Description This command configures an IPv6 prefix in the router advertisement
messages. To support multiple IPv6 prefixes, use multiple prefix statements.
No prefix is advertised until explicitly configured using prefix statements.
Default none
Parameters ip-prefix The IP prefix for prefix list entry in dotted decimal notation.
Values ipv4-prefix a.b.c.d (host bits must be 0)
ipv4-prefix-length 0 — 32
ipv6-prefix x:x:x:x:x:x:x:x (eight 16-bit pieces)
x:x:x:x:x:x:d.d.d.d
x: [0 — FFFF]H
d: [0 — 255]D
ipv6-prefix-length 0 — 128
prefix-length Specifies a route must match the most significant bits and
have a prefix length.
Values 1 — 128](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-120-320.jpg)


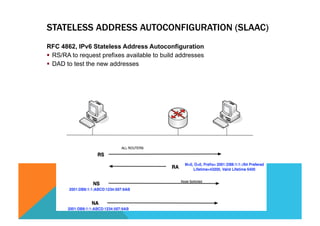


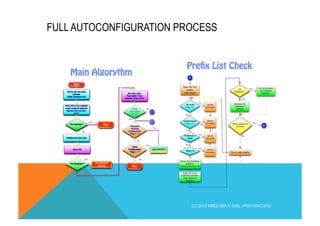
![MAIN ALGO OF AUTOCONFIGURATION PROCESS
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!
Derive the link-local
address
FE80::[Interface ID]
Send NS to the solicited
node multicast address
derived from the link-local
NA received ? Stop
Initialize the link-local
Send RS
RA Received ? Use DHCPv6
and exit
Set Hop Limit,
Reachable Time,
Retrans Timer, MTU
Prefix
Information
present ?
A
B
Managed
Address
Configuration
Flag = 1 ?
Other
Configuration
Flag = 1 ?
Use DHCPv6
Stop
Yes
No
Yes
No
Yes
No
Yes
No
Yes
No
Start](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-129-320.jpg)
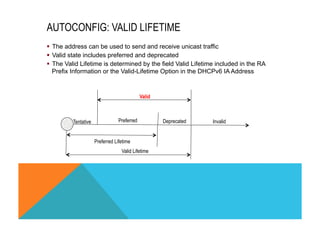
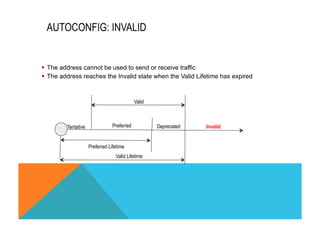
![RA PREFIX OPTION
ipv6 nd prefix <prefix/mask>[Valid]
[Preferred][no-advertise| off-link | no-autoconfig]
A
Take the first
prefix
information
On-Link
Flag = 0 ?
Ignore
the prefix
Autonomous
Flag = 0 ?
No
No
Derive the Stateless
address
Prefixe:[interface ID]
Send NS to the
matching solicited
node multicast
address
NA
Received ?
Other prefixes to
process
Yes
Initialise the
Stateless
address
Go to next prefix
B
No
No
Yes Do not initialize
the stateless
address
Preferred > Yes
Valid
Valid = 0
Ignore
the prefix
Ignore
the prefix
Ignore
the prefix
No
Yes
Yes
Yes](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-134-320.jpg)








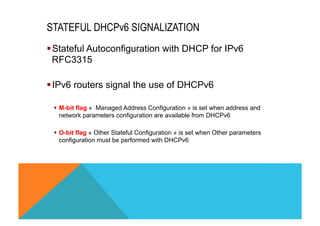
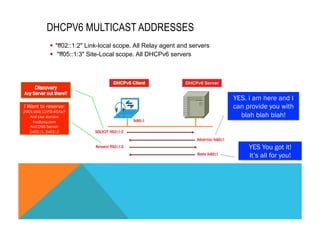
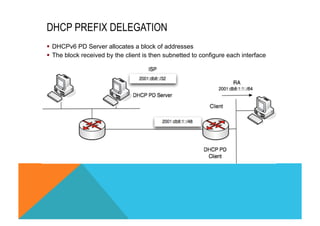
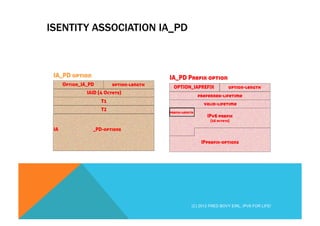
![DHCP MOST IMPORTANT TERMINOLOGY
DHCP = Unique IDentifier
http://tools.ietf.org/html/rfc3315#section-9
DHCP Client or Server has its DUID. It is based on the LL Address, the Vendor, the enterprise, the Time… What I
have seen the Most for the moment was Link Layer (LL or MAC Address).
Veryy important as DHCP uses multicast to communicate with ALL DHCP nodes. DUID is the used to fins the right
node.
IA = Identity Association
http://tools.ietf.org/html/rfc3315#section-10
Each IA must be associated with exactly one interface. Each Interface May have multiple prefixes but will have ONE
IA. This is a logic construct that can be used for a group of interfaces which play the same role.
« Each address in an IA has a preferred lifetime and a valid lifetime, as defined in RFC 2462 [17]. The lifetimes are
transmitted from the DHCP server to the client in the IA option. The lifetimes apply to the use of IPv6
addresses, as described in section 5.5.4 of RFC 2462. » From RFC 3315 Section 10.
IMPORTANT: When theses timers need to be changed, it is from the Server, the source! Changing the routers
timers has no effects.](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-146-320.jpg)



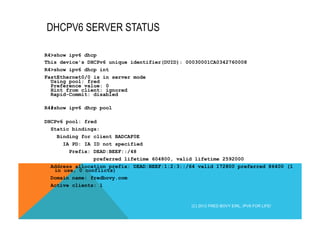
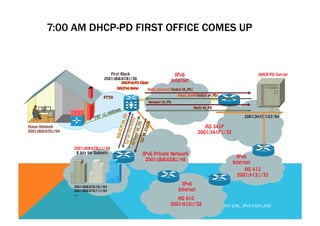
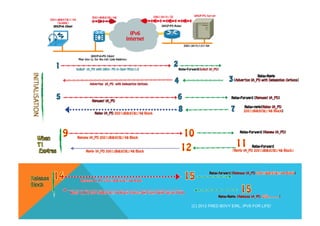
![DHCPv6 SOLICIT (1)
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6" possible: 6]
.... 1110 0000 .... .... .... .... .... = Traffic class: 0x000000e0
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel: 0x00000000
Payload length: 56
Nxt header: UDP (0x11)
Hop limit: 255
Source: fe80::38b1:e73c:c0f0:4442 (fe80::38b1:e73c:c0f0:4442)
Destination: ff02::12 (ff02::1:2)
User Datagram Protocol, Src Port: dhcpv6-client (546), Dst Port: dhcpv6-server (547)
Source port: dhcpv6-client (546)
Destination port: dhcpv6-server (547)
Length: 56
Checksum: 0x86f0 [validation disabled]
Link-Local All Servers and Relays
dhcpv6-client: 546
dhcpv6-server: 547
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-151-320.jpg)


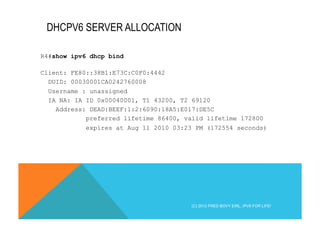
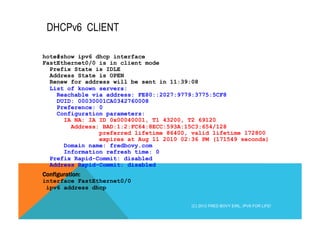












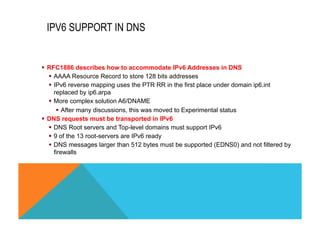






![DNS REQUEST TRANSPORTED IN IPV6
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6" possible
.... 0000 0000 .... .... .... .... .... = Traffic class: 0x00000000
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel: 0x00000000
Payload length: 145
Next header: UDP (0x11)
Hop limit: 255
Source: fe80::61e:64ff:feec:73a9 (fe80::61e:64ff:feec:73a9)
Destination: ff02::fb (ff02::fb)
User Datagram Protocol, Src Port: mdns (5353), Dst Port: mdns (5353)
Source port: mdns (5353)
Destination port: mdns (5353)
Length: 145
Checksum: 0x5753 [validation disabled]
Domain Name System (response)
mDNSv6
Link-local Multicast destination
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-188-320.jpg)

![DNS CAPTURE
Internet Protocol Version 6
0110 .... = Version: 6
[0110 .... = This field makes the filter "ip.version == 6" possible: 6]
.... 0000 0000 .... .... .... .... .... = Traffic class: 0x00000000
.... .... .... 0000 0000 0000 0000 0000 = Flowlabel: 0x00000000
Payload length: 145
Next header: UDP (0x11)
Hop limit: 255
Source: fe80::61e:64ff:feec:73a9 (fe80::61e:64ff:feec:73a9)
Destination: ff02::fb (ff02::fb)
User Datagram Protocol, Src Port: mdns (5353), Dst Port: mdns (5353)
Source port: mdns (5353)
Destination port: mdns (5353)
Length: 145
Checksum: 0x5753 [validation disabled]
Domain Name System (response)
[Request In: 788]
[Time: -404.306754000 seconds]
Transaction ID: 0x0000
Flags: 0x8400 (Standard query response, No error)
Questions: 0
Answer RRs: 1
Authority RRs: 0
Additional RRs: 3
Answers
power-mac-g5-de-fred-bovy-6.local: type A, class IN, cache flush, addr 192.168.0.15
Name: power-mac-g5-de-fred-bovy-6.local
Type: A (Host address)
.000 0000 0000 0001 = Class: IN (0x0001)
1... .... .... .... = Cache flush: True
Time to live: 2 minutes
Data length: 4
Addr: 192.168.0.15
mDNSv6 multicast address
MDNS port 5353
(C) 2012 FRED BOVY EIRL. IPV6 FOR LIFE!](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-190-320.jpg)





























































![ROBUSTNESS
§ This is the basis for the computation of many parameters
§ MLD is robust to [Variable Robustness] – 1 packet loss
§ Default: 2. MLD has no problem losing one MLD packet
Host A Host B
State Change
R
FE80::
1
FF02::
1](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-294-320.jpg)



























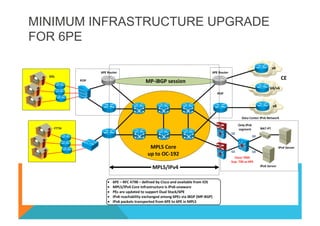

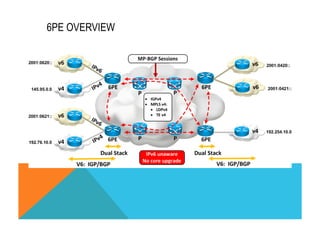
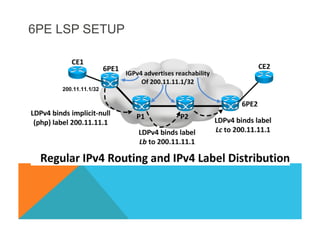
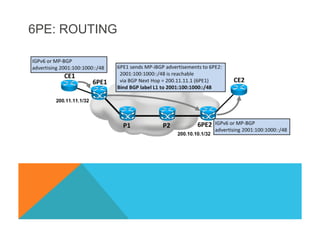
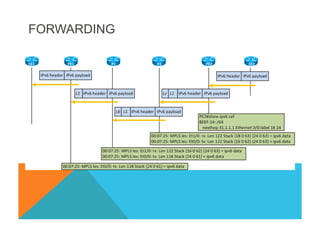

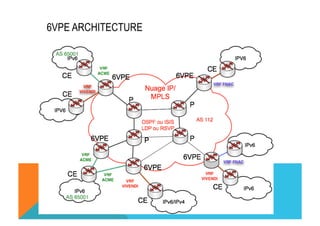
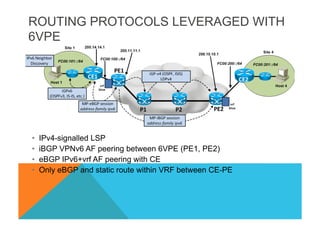
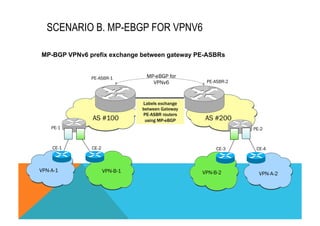
![VPNv4 6VPE
RD 2 bytes:6 bytes
TYPE:VALUE
2 bytes:6 bytes
TYPE:VALUE
RT
(extended community)
2 bytes:6 bytes
TYPE:VALUE
2 bytes:6 bytes
TYPE:VALUE
VPN address 8 bytes:4 bytes
RD:IPv4-address
[8 bytes]16 bytes
[RD]IPv6-address
MP_REACH-NLRI AFI=1
SAFI=128
AFI=2
SAFI=128
NLRI <length, IPv4-prefix,label> <length, IPv4-prefix,label>
VRF (Virtual Routing &
1 VRF = 1 RIB + 1 FIB MP-VRF
forwarding instance)
Nexthop 0:IPv4-address [0]::FFFF:IPv4-address
[0]:IPv6-address
[0]:IPv6-LL-address
Peering IPv4-address IPv4-address, IPv6-address
IPv6-LL--address
6VPE: THE TECHNOLOGY](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-343-320.jpg)
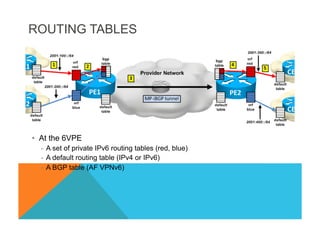
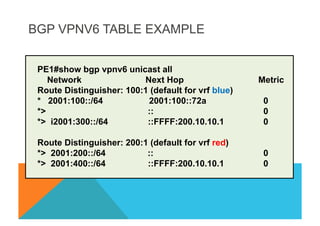
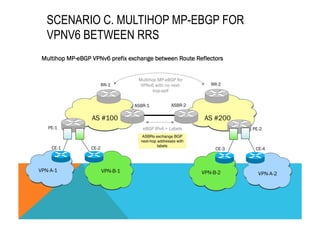
![ROUTING TABLES: EXAMPLES
PE1#show ipv6 route vrf blue
IPv6 Routing Table -blue -7 entries
C 2001:100::/64 [0/0]
via Ethernet4/0, directly connected
B 2001:300::/64 [200/0]
via 200.10.10.1%Default-IP-Routing-Table, indirectly connected
PE1#show ipv6 route vrf red
IPv6 Routing Table - red - 10 entries
C 2001:200::/64 [0/0]
via Ethernet0/0, directly connected
B 2001:400::/64 [200/0]
via 200.10.10.1%Default-IP-Routing-Table, indirectly connected
PE1#show ip route
200.10.10.0/32 is subnetted, 1 subnets
i L1 200.10.10.1 [115/30] via 40.1.1.3, Ethernet1/0
31.0.0.0/24 is subnetted, 1 subnets
i L1 31.1.1.0 [115/30] via 40.1.1.3, Ethernet1/0
200.11.11.0/32 is subnetted, 1 subnets
C 200.11.11.1 is directly connected, Loopback0](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-346-320.jpg)





































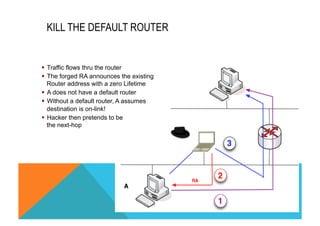

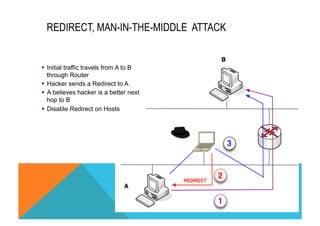

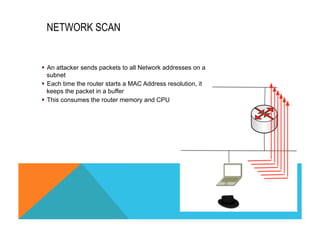


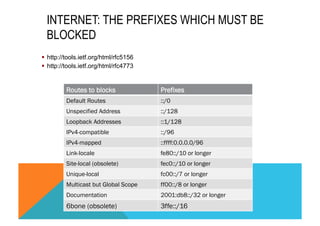







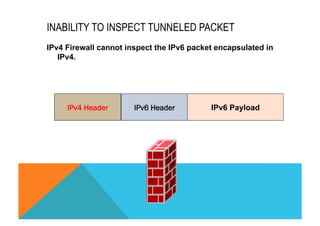

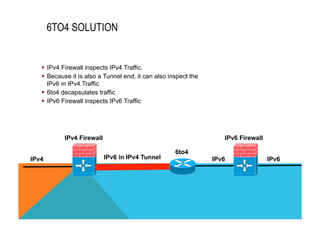












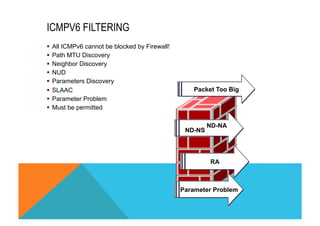
![CISCO IOS FIREWALL FOR IPV6
Fragmented packet inspection
§ The fragment header is used to trigger fragment processing.
§ Cisco IOS Firewall virtual fragment reassembly (VFR) examines out-of-sequence
fragments and switches the packets into correct order, examines the number of
fragments from a single IP given a unique identifier (Denial of Service [DoS] attack), and
performs virtual reassembly to move packets to upper-layer protocols.
IPv6 DoS attack mitigation
§ Mitigation mechanisms have been implemented in the same fashion as for IPv4
implementation, including SYN half-open connections.
Tunneled packet inspection
§ Tunneled IPv6 packets terminated at a Cisco IOS firewall router can be inspected by the
Cisco IOS Firewall for IPv6.
Stateful packet inspection
§ The feature provides stateful packet inspection of TCP, UDP, Internet Control Message
Protocol version 6 (ICMPv6), and FTP sessions.](https://image.slidesharecdn.com/fb-ipv6sparchimanv1-140923195440-phpapp01/85/Fb-i-pv6-sparchimanv1-0-435-320.jpg)